10 Examples of Vishing and How to Prevent Them
Discover 10 examples of vishing threats and learn strategies to prevent them. Enhance your security with our expert guidance.
Voice phishing, or vishing, is no longer about clumsy robocalls with broken English. Today’s attackers use AI-powered voices, spoofed caller IDs, and multi-channel pressure. Their aim is trick people into handing over money, data, or system access.
The FBI reports that tens of millions lost each year to vishing scams. According to Keepnet’s Vishing Response Report, 70% of organizations still fall for vishing attempts.
If you’ve ever asked, “what is an example of vishing?” or “how to protect yourself from vishing?”, this article is for you.
Below, we’ll cover 10 modern examples of vishing attacks (2023–2025) and the vishing protection tips you can use to stop them.
What is Vishing? (Quick Refresher)
Vishing (or voice phishing) is a social engineering scam that uses phone calls or VoIP. The goal is to trick people into giving away sensitive data like passwords, MFA codes, or banking details. Vishing is different from email phishing. It uses the urgency and authority of a real voice, making it harder to resist.
Common goals of vishing fraud include:
- Stealing money via wire transfers or payment changes.
- Gaining credentials to access systems.
- Extracting personal data for identity theft.
Think of it this way: if phishing is the “email scam,” then vishing is the phone call scam. But more personal, immediate, and often more dangerous. For further details, check out our blog on What is Vishing: Definition, Detection and Protection.
10 Modern and Classic Examples of Vishing Attacks
Voice phishing comes in many forms. It includes classic scams like fake bank calls or tax authority calls. It also includes modern attacks that use AI deepfake voices and multi-channel fraud.
Both styles use the same trick. They create urgency and authority over the phone. This pressures victims to share sensitive data or send money.
Understanding modern and classic examples of vishing attacks is the first step. This helps you spot them quickly and build strong defenses:
Example 1: Bank Fraud Calls
Scammers pose as your bank’s fraud department and warn of “suspicious activity.” You might get calls from unknown numbers or a urgent voice message. They pressure you to reveal PINs, MFA codes, login credentials, or account numbers to “secure” the account.
How to Prevent It: Hang up and ignore the voice message. Call your bank back using the number on your card or official app. Never share PINs, codes, or login credentials over the phone, real banks don’t ask for them.
Example 2: Government & Tax Authority Scams
Criminals pretend to be government agencies like the IRS, HMRC, or local tax offices. They demand immediate payment to avoid fines or legal issues.

How to Prevent It: Authorities never demand urgent payment by phone. Verify claims using the official website or hotline.
Example 3: Tech Support Vishing
Attackers pose as IT support, claiming a device is infected or an account is compromised. They push for remote access software installation or credential disclosure.
How to Prevent It: Legitimate IT teams do not cold-call. Never install software from unsolicited calls.
Example 4: Prize & Reward Scams
Scammers make random phone calls and say you won a prize.
Then they demand fees or your data.
They may spoof caller ID.
They give a fake phone number.
They also send text links that lead to phishing attacks.
These push you to share account info or even social security numbers to “verify” the win.
How to Prevent It: If it sounds too good to be true, it is. Don’t pay, click, or share social security numbers. Hang up and verify on the organization’s official site using a known, verified phone number.
Example 5: Fake Customer Service Hotlines
This is a common type of vishing. Threat actors plant fake hotlines via ads/SEO or phishing emails. Calling them triggers a voice phishing social engineering attack for logins, codes, or gift cards. Sometimes followed by received calls, using details from dumpster diving to sound legit.

How to Prevent it: Use only numbers from the official site/app or saved contacts. Never share credentials or pay with gift cards, hang up and call a verified number.
Example 6: AI Deepfake Voice Attacks
An AI deepfake voice attack happens when a scammer copies the voice of a boss, manager, or family member. They call with urgent instructions.
They might send a follow-up text message to "confirm" details. They may pretend to be a bank or tech support to seem trustworthy.
These attacks use classic social engineering tactics. They rely on authority, secrecy, and a false sense of urgency. This pressure makes victims transfer money or share sensitive information, which can lead to identity theft.
How to Prevent It:
- Refuse approvals based on voice alone: hang up and do dual verification. Then callback to known number plus get a written confirmation via email or a secure channel.
- Contact the financial institution or the company’s technical support using numbers from the official website. Do not those provided in the call or any text message.
- Set passphrases or code words. Require two people to approve payments. Train teams to spot social engineering tricks. This way, a vishing scammer cannot rush the process.
Example 7: Robocall Vishing Scams
Automated robocalls claim to be from banks, telecom providers, or government bodies. Victims are asked to “press 1” and then provide details.
How to Prevent It: Use call-blocking tools to filter robocalls. Hang up and verify directly with the provider.
Example 8: Internal Business Impersonation (CEO Fraud)
Criminals impersonate CEOs, CFOs, or managers, ordering employees to transfer funds or change payroll info.

How to Prevent It: Enforce dual approvals for financial requests and clear no-phone transaction policies.
Example 9: E-Commerce Refund Scams
This type of scam is an e-commerce refund vishing call. A caller poses as a retailer or courier’s “refund department,” claims there’s an overcharge. And asks you to “confirm” details. They’ll try to rush you into reading out account numbers or credit card numbers to process a fake refund.
How to Prevent It: Ignore the instructions in the call. Check the refund status yourself in the retailer’s official app or on their website. Don’t share account numbers or credit card numbers with anyone who contacted you out of the blue. Hang up and reach support using the number listed on the company’s site.
Example 10: Multi-Channel Vishing Attacks
Scammers combine phishing emails + follow-up phone calls. The email primes the victim, while the call “verifies” the request, making the scam feel more authentic.
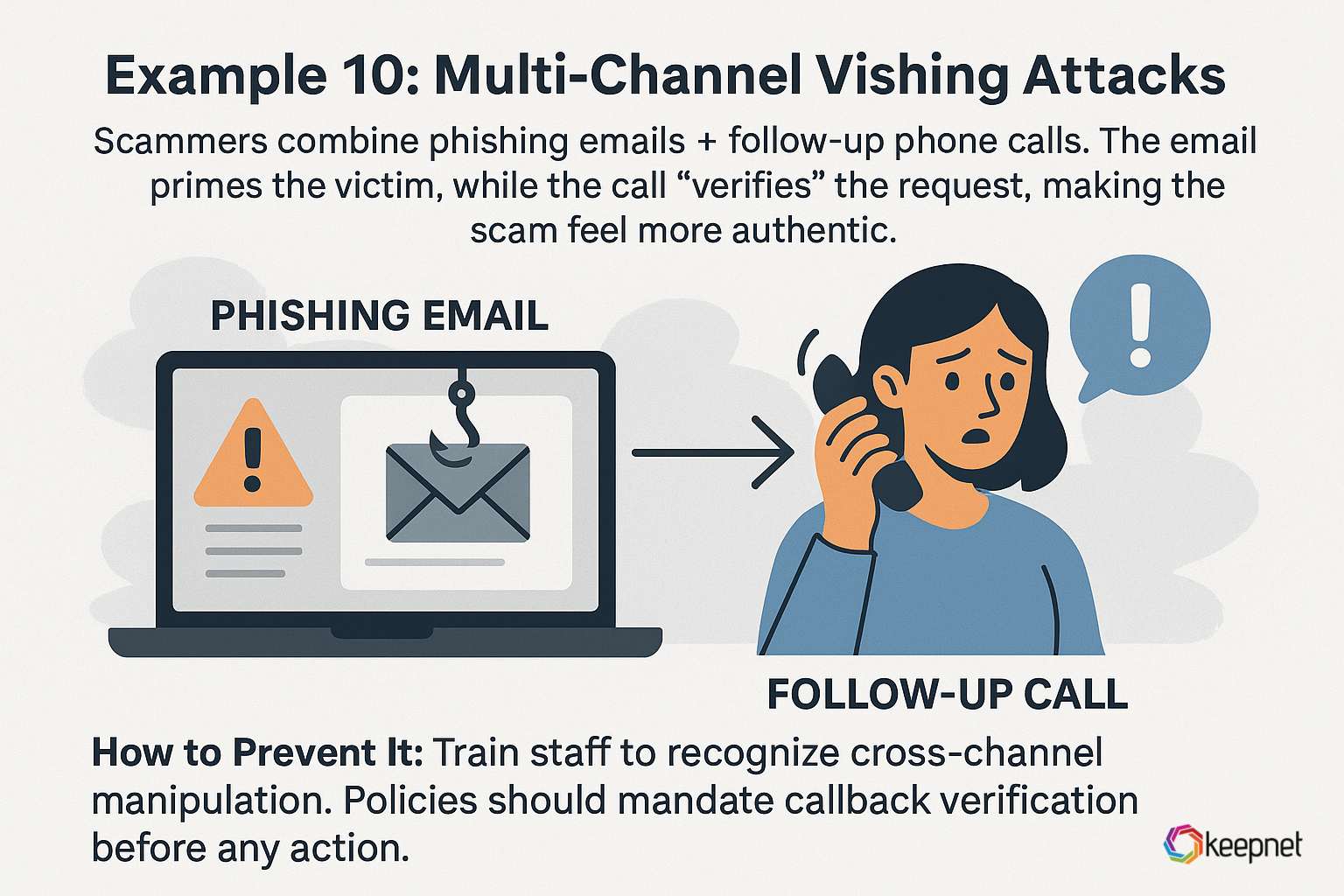
How to Prevent It: Train staff to recognize cross-channel manipulation. Policies should mandate callback verification before any action.
How to Protect Yourself from Vishing Attacks
Whether you’re facing classic bank scams or modern AI-powered vishing attacks, these rules apply:
- Don’t trust caller ID, it can be spoofed.
- Never share passwords, MFA codes, or financial details by phone.
- Hang up and call back using official numbers.
- Use anti-vishing tools and call-blocking apps.
- Report suspicious calls to your IT/security team or national fraud hotlines.
- Train regularly with vishing spam examples so your team recognizes the tactics fast.
The Role of User Education
Education is a cornerstone of vishing prevention. Regular training helps employees stay alert to evolving attack methods.
Running Vishing Simulations
Vishing Simulations provide practical, hands-on experience in identifying and handling vishing attempts. These exercises reveal potential vulnerabilities and strengthen organizational defenses.
Effectively combating vishing requires a combination of awareness, technology, and proactive measures. Organizations must focus on educating employees, implementing robust verification processes, and using tools to monitor and prevent suspicious activities. By staying informed about evolving tactics, businesses can build resilience against vishing threats and reduce human risk factors.
VoIP phone system is a cost-effective communication tool that offers flexibility and advanced features like call routing. However, it also provides anonymity for attackers, enabling them to mask their identities and spoof numbers. This makes fraudulent calls harder to trace and increases the risk of exploitation.
Use tools or apps that detect and block spoofed numbers to reduce exposure to fraudulent calls. For instance, using a reliable call center software not only streamlines communication but also acts as a frontline defense against vishing attacks by verifying callers, detecting spoofed numbers, enabling real-time monitoring, and reinforcing employee training through integrated simulations.
Consider using a multi-level auto attendant system for small businesses to help screen and direct calls effectively, reducing the risk of fraudulent or unwanted calls reaching your team.
Check our guide to learn how to run vishing simulations step by step.
Keepnet Human Risk Management Platform
Preventing vishing requires a layered approach, combining employee education, strict communication protocols, and the right tools. Solutions like the Keepnet Human Risk Management Platform offer comprehensive support to identify, mitigate, and respond to vishing attempts effectively.
This platform provides a centralized hub for monitoring human risk factors, empowering organizations to track vulnerabilities and implement targeted security awarenes training. Tools such as the Keepnet Phishing Simulator and Vishing Simulation help employees build practical, hands-on skills to recognize and stop vishing attempts.
By integrating these solutions into your cybersecurity strategy, you can bolster organizational resilience, reduce risks, and create a culture of vigilance against social engineering attacks.
Conclusion
These 10 examples of vishing prove how attackers exploit both old tricks (bank and tax scams) and modern tactics (AI voices, multi-channel attacks). The best defense is a mix of awareness, clear policies, and regular vishing simulations.
Ready to see how your team would handle a real vishing attempt?
Book a demo of Keepnet’s Vishing Simulator and Security Awareness Training to build resilience against today’s most dangerous phone-based attacks.
Editor’s Note: This blog post was updated on February 9, 2026.