What Is DLL Hijacking? (DLL Search Order Hijacking Explained)
DLL hijacking happens when a Windows app loads the wrong DLL—often from a user-writable folder—letting attackers run code inside a trusted process. This guide explains the main variations (search order, sideloading, phantom DLL), plus detection and prevention checklists.
DLL hijacking is a Windows attack technique where an attacker causes an application to load a malicious Dynamic-Link Library (DLL) instead of the legitimate one. In many cases, this works because the application loads a DLL without a fully qualified path, so Windows searches a set of locations in a defined order—and attackers aim to control one of those locations
MITRE ATT&CK describes this as DLL Search Order Hijacking (sub-technique T1574.001 under “Hijack Execution Flow”), where adversaries place a trojan DLL in a directory that gets searched before the legitimate library’s location.
DLL Hijacking Definition
DLL hijacking is an attack that executes code by placing a malicious DLL where a Windows program will load it first due to the DLL search order or related loading behavior (Mitre)
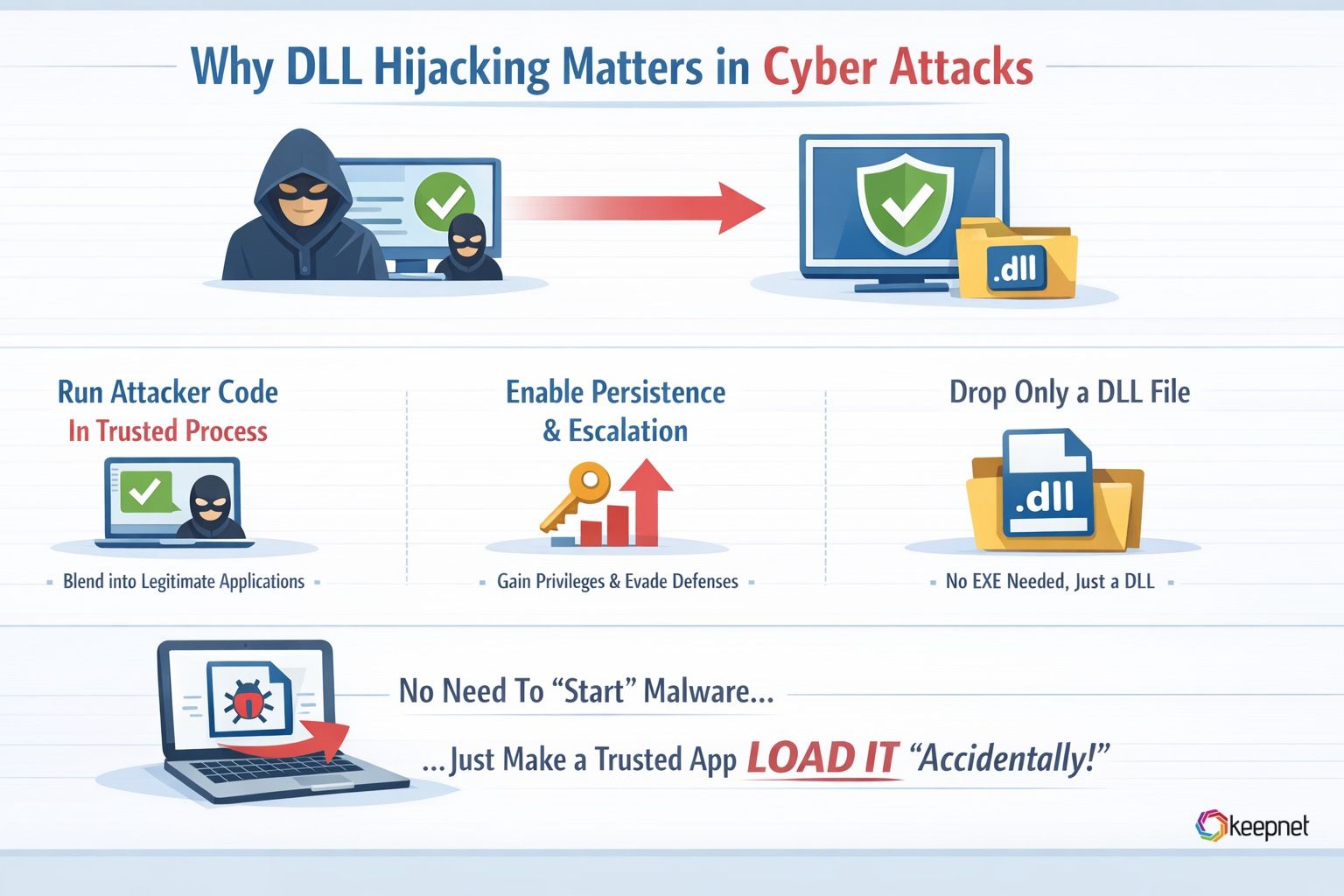
DLL hijacking is popular because it can:
- Run attacker code inside a trusted, legitimate process (often blending in)
- Support persistence, privilege escalation, or defense evasion
- Work even when the attacker can’t drop an EXE—only a DLL into a writable folder
Think of it like this: the attacker doesn’t need to “start” malware— they just need to make a trusted app “accidentally” load it.
How DLL Hijacking Works (The Simple Flow)
- A program starts and tries to load someLibrary.dll (often via LoadLibrary-style behavior) without specifying a full path.
- Windows searches for that DLL in a well-defined order (application directory, system directories, current directory, PATH, etc., depending on settings).
- If the attacker can place a malicious DLL with the expected name in a location searched early (commonly a user-writable directory), Windows loads it.
- The malicious DLL runs code as soon as it’s loaded (e.g., in DllMain), gaining execution inside the target process.
DLL Hijacking Variations
DLL hijacking comes in several forms, but all variations exploit how Windows applications locate and load DLL files during execution.
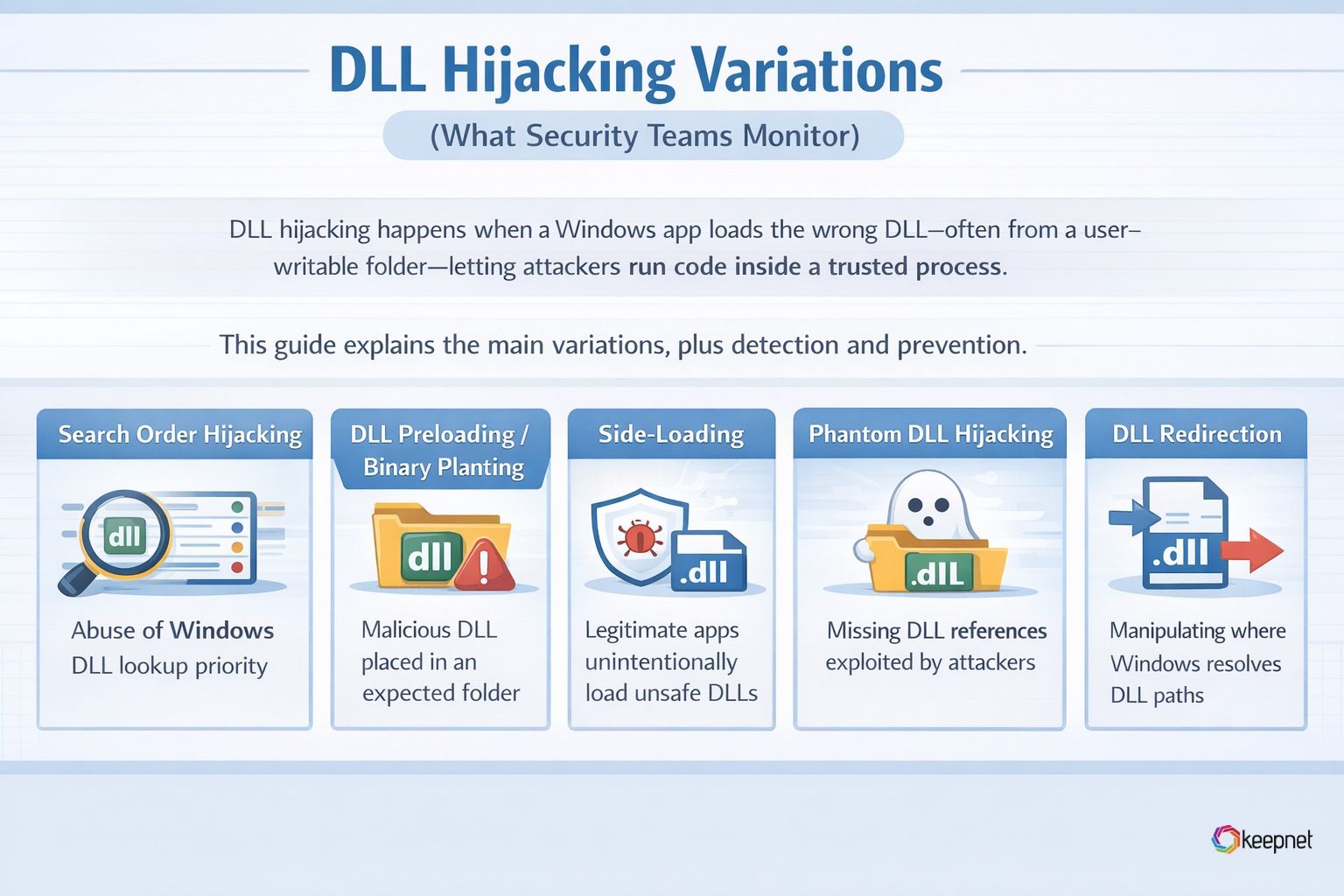
1) DLL Search Order Hijacking (Classic)
This is the “main” concept: Windows loads the attacker DLL because its location is searched before the legitimate DLL location.
Common enabling conditions
- The app loads DLLs without full paths
- A searched directory is user-writable (Downloads, temp folders, app folders with weak permissions, etc.)
2) DLL Preloading / Binary Planting
Microsoft explicitly notes that if an attacker controls a directory on the DLL search path, they can place a malicious copy there—sometimes called a DLL preloading attack or binary planting.
This term often appears in vulnerability reports: “the application is vulnerable to DLL planting.”
3) DLL Side-Loading (Sideloading)
DLL sideloading is often described as placing a benign (sometimes signed) executable together with a malicious DLL in the same directory, so the executable loads the attacker DLL from its own folder.
This variation is popular because it can:
- Leverage a trusted executable to proxy-load the malicious DLL
- Reduce suspicion during execution (legit process name, signed binary)
4) Phantom DLL Hijacking
A particularly sneaky subtype: attackers target DLLs that don’t exist on the system but are referenced by the application. They create a DLL with that missing name in the searched location so it gets loaded.
5) DLL Redirection
MITRE notes adversaries may modify the search order via DLL redirection (e.g., using redirection files or registry settings), causing a program to load a DLL from a different location.
What Makes an App Vulnerable to DLL Hijacking?
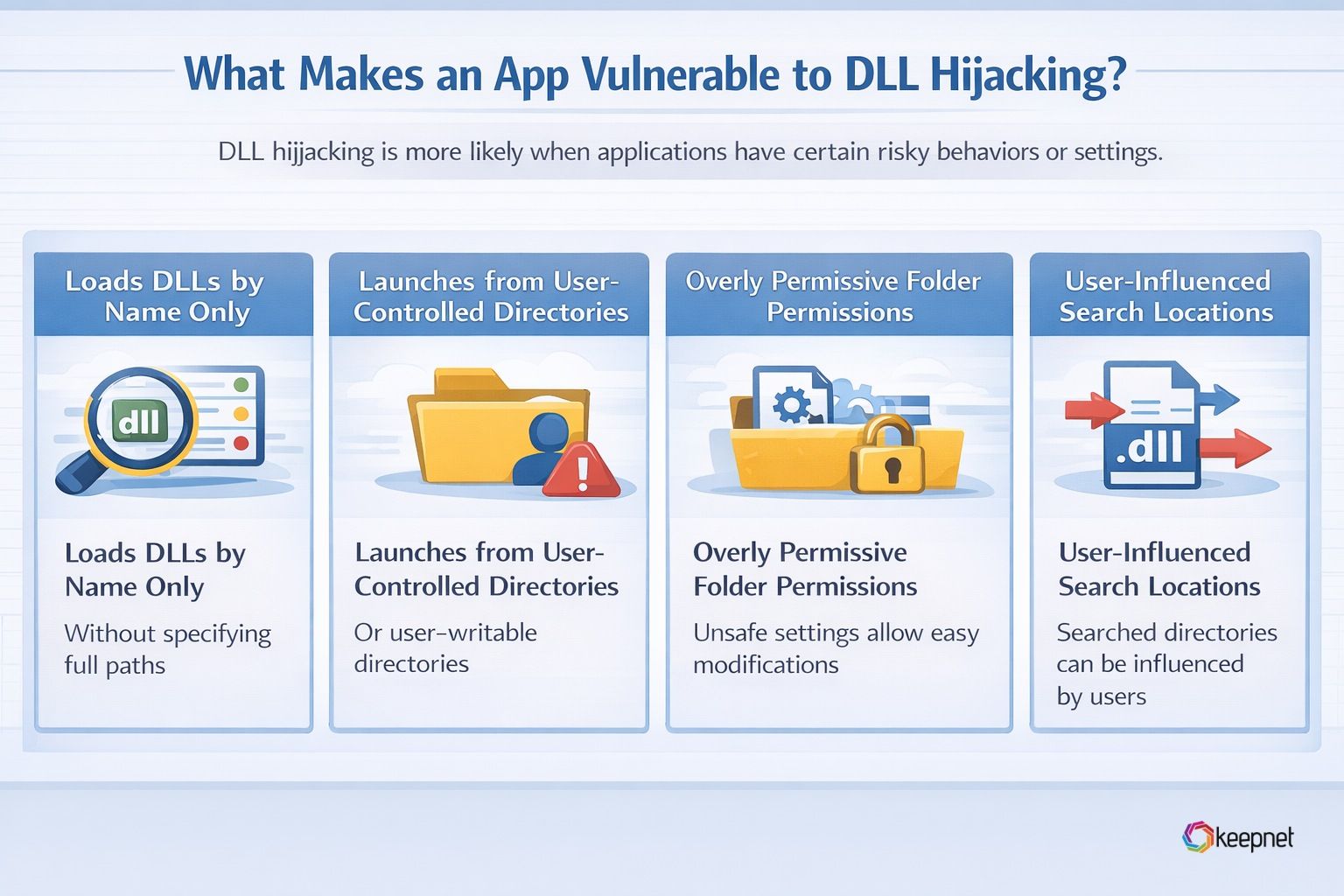
You’ll often find DLL hijacking risk when:
- The app loads DLLs by name only (no absolute path).
- The app is launched from (or searches) user-writable directories
- The app’s folder permissions are too loose (users can write next to the EXE)
- The DLL search order includes locations attackers can influence (like current directory or PATH).
How to Detect DLL Hijacking (High-Signal Clues)
Detection is usually about spotting unexpected DLL loads—especially from weird locations.
Practical detection signals
- A process loads a DLL from Downloads, Temp, user profile paths, or other user-writable directories (when it normally loads from System32 or the app’s install directory).
- A legitimate/signed process suddenly loads a DLL that is:
- unsigned or signed by an unknown publisher
- new/unseen in your environment
- located outside standard library paths
Threat-hunting idea
Start with high-value processes and look for DLL load events that come from non-standard directories. DLL hijacking is explicitly framed as executing malicious payloads by hijacking DLL search order behavior.(CISA)
How to Prevent DLL Hijacking (Developer + Defender Checklist)
DLL hijacking prevention is mostly about controlling where DLLs can be loaded from and removing attacker write access.
For developers (most effective long-term fixes)
1) Use safer DLL loading APIs and flags
Microsoft recommends specifying search behavior using LoadLibraryEx with LOAD_LIBRARY_SEARCH flags, and setting a default process DLL directory policy using SetDefaultDllDirectories.
2) Avoid loading DLLs by relative name only
If you dynamically load, prefer fully qualified paths or restricted search locations. Microsoft’s security guidance calls out the risk when an application loads a DLL without specifying a fully qualified path.
3) Prefer System32 for known system DLLs
Microsoft has also discussed mitigations such as PreferSystem32 that change how the DLL search order is handled when opted in.
For security teams / IT (high-impact operational controls)
1) Fix folder permissions (remove easy planting locations)
- Ensure application install directories are not user-writable
- Watch “shared” folders used for running tools/scripts (common planting hotspots)
2) Reduce risky search locations
Review configurations that may reintroduce unsafe search behavior. Microsoft documents how safe DLL search mode and directory behaviors can be influenced by configuration and APIs like SetDllDirectory.
3) Application control
Use application allowlisting / code integrity policies to prevent untrusted DLLs from loading, especially from user-writable locations.
4) EDR detections focused on module load paths
Tune detections for:
- unsigned DLLs loaded by signed binaries
- uncommon DLL load paths for common apps
What To Do If You Suspect DLL Hijacking (Response Steps)
- Isolate the affected endpoint (if this is a confirmed malicious load).
- Identify the parent process and the exact DLL path that loaded.
- Hash/signature-check the DLL and correlate with other endpoints.
- Remove the planted DLL and fix the write-permission root cause (or it will recur).
- If sideloading is involved, identify the dropped “benign” EXE + DLL pair and trace origin.
CISA’s ATT&CK-focused resources emphasize that hijacking DLL loads can be used for persistence, privilege escalation, and evasion—so treat it as a serious intrusion signal, not just “a weird file.”
Conclusion
DLL hijacking is effective because it abuses normal Windows DLL loading behavior to run malicious code inside a trusted process—often without dropping a standalone executable. The strongest defense is layered:
- Developers: reduce risk at the source by using safer DLL-loading controls (for example, restricted search flags and secure default directories) and avoiding ambiguous “name-only” DLL loads.
- Defenders: harden the environment by fixing writable paths, monitoring unusual module-load locations, and enforcing application control so untrusted DLLs can’t load from user-writable folders.
But technical controls alone aren’t enough—because DLL hijacking usually happens after an initial foothold, often gained through phishing, social engineering, or credential abuse.
That’s why organizations also need a measurable approach to reducing human-driven risk. Keepnet’s Human Risk Management Platform combines phishing simulations (SMS, voice/vishing, QR, MFA-fatigue), Security Awareness Training, and Agentic AI-driven behavioral microlearning that adapts content by role, region, and risk signals—helping teams turn awareness into real behavior change and measurable risk reduction.
Keepnet has been named a go-to vendor for stopping deepfake and AI disinformation attacks by Gartner.