What Is a Firewall? How Does It Help Cybersecurity?
A firewall is a hardware/software security control that filters network traffic using rules. It improves cybersecurity by reducing attack surface, blocking unauthorized connections, enforcing segmentation, and providing visibility through logs.
A firewall is one of the oldest ideas in cybersecurity—and still one of the most useful. Not because it “stops hackers” by itself, but because it forces traffic to follow rules.
If you want a mental model that sticks:
A firewall is a bouncer + guest list for network connections. It decides which traffic gets in, which traffic gets out, and which traffic is suspicious enough to block or inspect more deeply.
NIST describes firewalls as devices or programs that control network traffic flow between networks or hosts with differing security postures.
Firewall Definition
Firewall (definition): A security control (hardware/software/cloud service) that monitors and filters inbound and outbound network traffic using rules—allowing legitimate communication and blocking unauthorized or risky connections.
A firewall protects cybersecurity by reducing exposure and enforcing traffic rules between devices, networks, and the internet. But it works best when it’s part of a broader program like security awareness training.
How a Firewall Works
At a high level, every network connection has “labels” (metadata) like:
- source/destination IP address
- port number (e.g., 443 for HTTPS)
- protocol (TCP/UDP)
- in advanced firewalls: application identity, user identity, and content signals
A firewall compares those labels against a policy (rules) and then:
- allows the connection
- blocks it
- inspects it (more deeply) before deciding
Firewalls are commonly used as boundary protection devices—controls that mediate communications at the “edge” of a system or network.
What Threats Does a Firewall Actually Help With?
A well-configured firewall helps with cybersecurity in five practical ways:
1) Reduces your attack surface
If a service isn’t reachable from the internet, attackers can’t easily exploit it. This is why “close unused ports” is still timeless advice.
2) Blocks known-bad and suspicious traffic patterns
Modern firewalls can spot patterns like scanning, suspicious protocol behavior, or policy violations and stop them early.
3) Enforces segmentation (limits blast radius)
Even if one machine gets compromised, internal firewall rules (or segmentation firewalls) can limit lateral movement. Segmentation reduces the blast radius, but many breaches still begin with stolen credentials — which is why phishing simulation is used to measure how often employees fall for real-world lure
4) Gives visibility (logs you can investigate)
Firewall logs show who tried to connect to what, when, and how often—useful for threat hunting and incident response.
5) Supports compliance and control
Firewalls help demonstrate that access is controlled, monitored, and reviewed—common requirements across security standards.
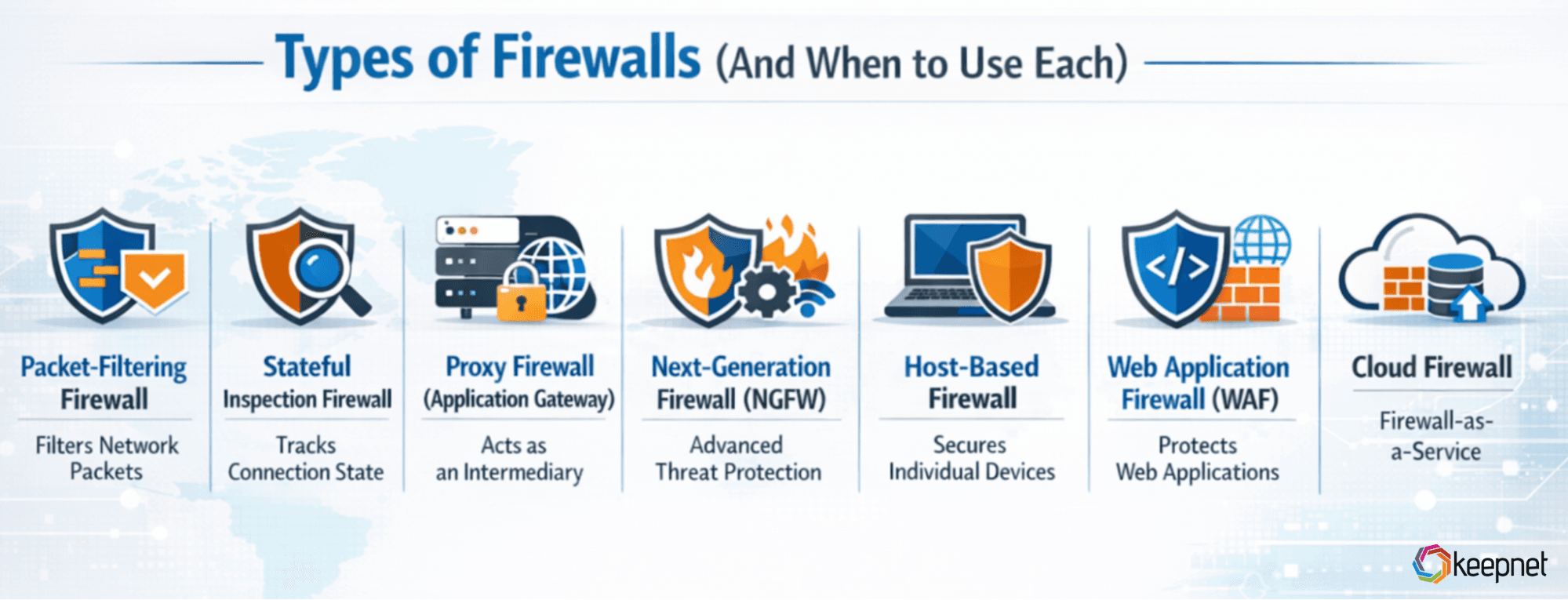
Types of Firewalls (And When to Use Each)
Different firewalls solve different problems. Here’s the clean breakdown.
1) Packet-Filtering Firewall
The simplest form: checks IPs, ports, and protocols. Fast, but limited context.
2) Stateful Inspection Firewall
Tracks whether traffic is part of an established connection (not just a random packet). This is a major step up from basic filtering.
3) Proxy Firewall (Application Gateway)
Acts like an intermediary. The client talks to the proxy; the proxy talks to the destination—useful for deeper control and inspection.
4) Next-Generation Firewall (NGFW)
NGFWs add deeper capabilities beyond classic firewalling—often including deep packet inspection, identity awareness, and integrated protections.
What NGFWs are best for: modern enterprise networks where you need app/user-aware policy (not just IP/port rules).
5) Host-Based Firewall (Endpoint Firewall)
Runs on the device itself (laptop/server). Great for protecting roaming devices and enforcing rules even off-network.
6) Web Application Firewall (WAF)
A WAF protects web applications by filtering/monitoring HTTP traffic and blocking common web attacks (e.g., SQL injection, XSS).
Simple rule:
- Network firewall protects networks/services broadly
- WAF protects web apps specifically
7) Cloud Firewall / Firewall-as-a-Service
Cloud-native controls that apply policy to cloud workloads, VPC/VNET traffic, and remote users—useful when your “perimeter” is no longer a single office.
Firewall Rules: The 80/20 That Makes or Breaks Security
A firewall’s value comes from its policy quality. These are the rules that separate “we have a firewall” from “the firewall protects us.”
The default stance: deny by default (then allow what you need)
- Start with block all inbound
- allow only required services
- restrict by source IP ranges where possible
Don’t forget outbound control
Many orgs allow all outbound traffic—making data exfiltration and command-and-control easier. Egress filtering can reduce damage when something slips through.
Use “least privilege” for network access
Rules should be specific:
- exact source → exact destination
- exact ports and protocols
- time-based rules for temporary access
- documented exceptions with review dates (a mature practice aligned with boundary protection governance)
What a Firewall Does NOT Do
A firewall is not magic. It won’t automatically stop:
- phishing that steals credentials
- attacks that use legitimate logins
- malware running on an endpoint already inside the network
- every threat hidden inside encrypted traffic (unless you’re doing TLS inspection carefully)
Best way to explain it:
A firewall is a control point—not a full security program.

Firewall Best Practices (2026-Ready Checklist)

1) Patch and upgrade firewall software/firmware
Firewalls are high-value targets. Real-world advisories show that firewall vulnerabilities can be actively exploited and require urgent patching and version verification.
2) Lock down management access
- restrict admin interfaces by IP allowlist/VPN
- require MFA
- disable unused management services
- monitor admin logins
3) Review rules like you review financial access
- remove unused rules
- eliminate “ANY-ANY” rules
- tag rules to owners + business purpose
- set expiry dates for temporary access
4) Turn on logging—but make it usable
Log key decisions (blocked inbound, denied outbound, admin actions) and route them to SIEM/SOC workflows.
5) Segment critical systems
Create “no direct path” zones for:
- backups
- identity systems
- crown-jewel servers
- production environments
6) Test your firewall rules (don’t assume)
Validate with:
- vulnerability scans (internal + external)
- change simulations
- incident drills
CISA emphasizes securing networks through continuous monitoring and risk-based mitigation across network components, which includes edge and boundary controls.
How to Choose the Right Firewall (Fast Buyer’s Guide)
Ask these five questions:
- Where is your perimeter today? (office, cloud, remote, hybrid)
- Do you need app/user awareness? (NGFW benefits)
- Do you run web apps? (add a WAF)
- What’s your visibility requirement? (logs, integrations, response workflow)
- Can you operate it well? (policy management matters more than flashy features)
Conclusion: Firewalls Control Traffic—Phishing & Training Reduce What Slips Through
Firewalls are still essential because they turn network chaos into controlled, enforceable pathways. But the biggest security gains come from how you run them day to day: least-privilege rules, smart segmentation, usable logging, and continuous patching.
At the same time, many real-world breaches don’t “break” the firewall—they go around it. Phishing, social engineering, and MFA fatigue often lead to credential theft, and attackers then walk in using legitimate logins. That’s why firewall hygiene should be paired with phishing-focused prevention and testing: Security Awareness Training to change behavior, and Phishing Simulator to measure and improve resilience over time.
Keepnet has been named a go-to vendor for stopping deepfake and AI disinformation attacks by Gartner.