Privileged Access Management (PAM)
Privileged Access Management (PAM) is a cybersecurity framework designed to protect sensitive systems by controlling and monitoring access to high-level accounts. Learn how PAM works, why it matters, and how to implement it effectively.
Privileged Access Management (PAM) is how you control, monitor, and secure the most powerful accounts in your environment—the admin, root, and service identities attackers love. If you’ve ever asked “what is privileged access management” or looked for a clear privileged access management definition, think of it as a security layer that sits between people (and machines) and your crown jewels. In PAM in cyber security, a privileged access manager brokers access, enforces least privilege, and records what happens during elevated sessions, turning risky “all-access” keys into time-bound, auditable permissions.
The benefits of privileged access management show up fast: fewer pathways for privilege escalation, stronger protection against privileged access abuse, and cleaner compliance through detailed logs and session recordings. A modern privileged access management system can rotate credentials automatically, issue just-in-time access, inject passwords without revealing them to users, and flag suspicious behavior in real time. In short, PAM cybersecurity reduces blast radius, speeds investigations, and gives security teams confidence that powerful accounts aren’t a blind spot.
6% of security incidents in 2025 were linked to compromised privileged identities, according to the 2025 Verizon Data Breach Investigations Report.
Cybercriminals frequently target privileged accounts to gain access to an organization’s most sensitive data and critical systems. A single compromised administrator account can lead to devastating financial, operational, and reputational damage.
This guide breaks down the essentials, Privileged Access Management: definition, benefits & best practices, so you can pick the right privileged access management solutions and shape a practical PAM strategy. We’ll cover how PAM differs from traditional identity access controls, where it fits across cloud, on-prem, and even PAM for OT environments, and the habits that make programs stick: least privilege by default, strong approvals, session monitoring, risk-based policies, and regular PAM audit and risk assessment. By the end, you’ll know how to evaluate a solution and roll out best practices that actually work at enterprise scale.
What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is the security framework for controlling and monitoring the most powerful identities in your environment—admin, root, service, and break-glass accounts. If you’re looking for a clear privileged access management definition, think of PAM as a broker that stands between users (and machines) and your crown-jewel systems, reducing the risk of privileged access abuse. In PAM in cyber security, the goal is to limit who can use elevated privileges, for how long, and under what conditions—so a single compromised account can’t bypass traditional controls.
A modern privileged access management system (often called a privileged access manager) centralizes credentials, issues just-in-time access, records privileged session management, and automates password rotation. These capabilities support least privilege, streamline audits, and make investigations faster. Whether you’re evaluating privileged access management solutions for cloud, on-prem, or PAM for OT environments, the core outcomes are the same: tighter control, better visibility, and a smaller blast radius.
How PAM safeguards privileged accounts:
Control access: Limit use of privileged accounts to authorized personnel with policy, approvals, and MFA.
Monitor activity: Track and record sessions to detect and respond to unauthorized actions in real time.
Rotate credentials: Enforce strong password policies, automatic rotation, and credential checkout/injection.
These controls anchor an effective PAM strategy and answer the practical question, “what is PAM in cyber security?”—it’s how you make powerful access safe, auditable, and temporary.
Why Is Privileged Access Management Critical in Today’s Threat Landscape?
Privileged Access Management sits at the heart of modern cybersecurity because it controls the identities with the most power—admin, root, and service accounts. When attackers get privileged keys, they can turn small footholds into full-blown breaches. PAM changes that equation. By brokering access, enforcing least privilege, and recording what happens during elevated sessions, a privileged access management system shrinks risk, strengthens compliance, and builds day-to-day resilience. Those are the core privileged access management benefits security leaders look for.
- Mitigating insider threat: Not every incident starts outside your walls. Insider error and misuse are costly—industry research (e.g., Ponemon) pegs average annual insider-threat losses in the multi-million range. PAM reduces this risk by limiting who can touch sensitive systems, for how long, and under what approvals. Features like privileged session management, MFA, and just-in-time access create auditable trails, while real-time alerts in PAM platforms help teams spot privileged access abuse as it happens. The result: stronger accountability and faster investigations, backed by clean evidence for PAM audit and risk assessment.
- Reducing attack surface: Privileged accounts are prime targets. A well-run PAM strategy enforces least privilege, removes standing admin rights, rotates credentials automatically, and injects passwords without exposing them to users. That means fewer pathways for lateral movement, ransomware, and data exfiltration—and a much smaller blast radius if a single endpoint is compromised. In practice, the privileged access manager becomes a policy gate, turning “always-on” power into short, scoped, and monitored access.
- Ensuring compliance and trust: Regulations like GDPR, HIPAA, PCI DSS, and SOX expect tight control over who can access sensitive data and when. Privileged access management solutions help you prove it—with centralized vaulting, role-based policies, session recordings, and immutable logs. Beyond passing audits, this visibility reassures customers and partners that you handle privileged operations responsibly. In short, if you’re asking what is PAM in cyber security and why it matters now—the answer is simple: it’s the most effective way to keep powerful access safe, compliant, and fully accountable.
Key Statistics, Trends on Privileged Access Managament
Here are some privileged access management statistics and trends that organizations must be aware of:
- 74% of data breaches involve the abuse of privileged credentials (Source).
- 33% of security incidents in 2024 were linked to compromised privileged identities, up from 28% in 2023 (Source).
- 89% of privilege misuse cases are financially motivated (Source).
- 82% of insider misuse-related data breaches took over a week to detect (Source).
- The global PAM market was valued at $3.6 billion in 2024 and is projected to grow at a 23.3% CAGR from 2025 to 2034 (Source).
- 43% revenue increase in Q1 2025, reaching nearly $318 million (Source).
- Legacy PAM solutions are insufficient for complex cloud environments, leading to a shift toward automated and consolidated PAM approaches (Source).
Key Components of an Effective Privileged Access Management Strategy
An effective Privileged Access Management strategy is built on a foundation of proactive control, visibility, and accountability. By implementing the following core components, organizations can significantly enhance their ability to manage and protect privileged accounts, reduce attack surfaces, and maintain regulatory compliance.
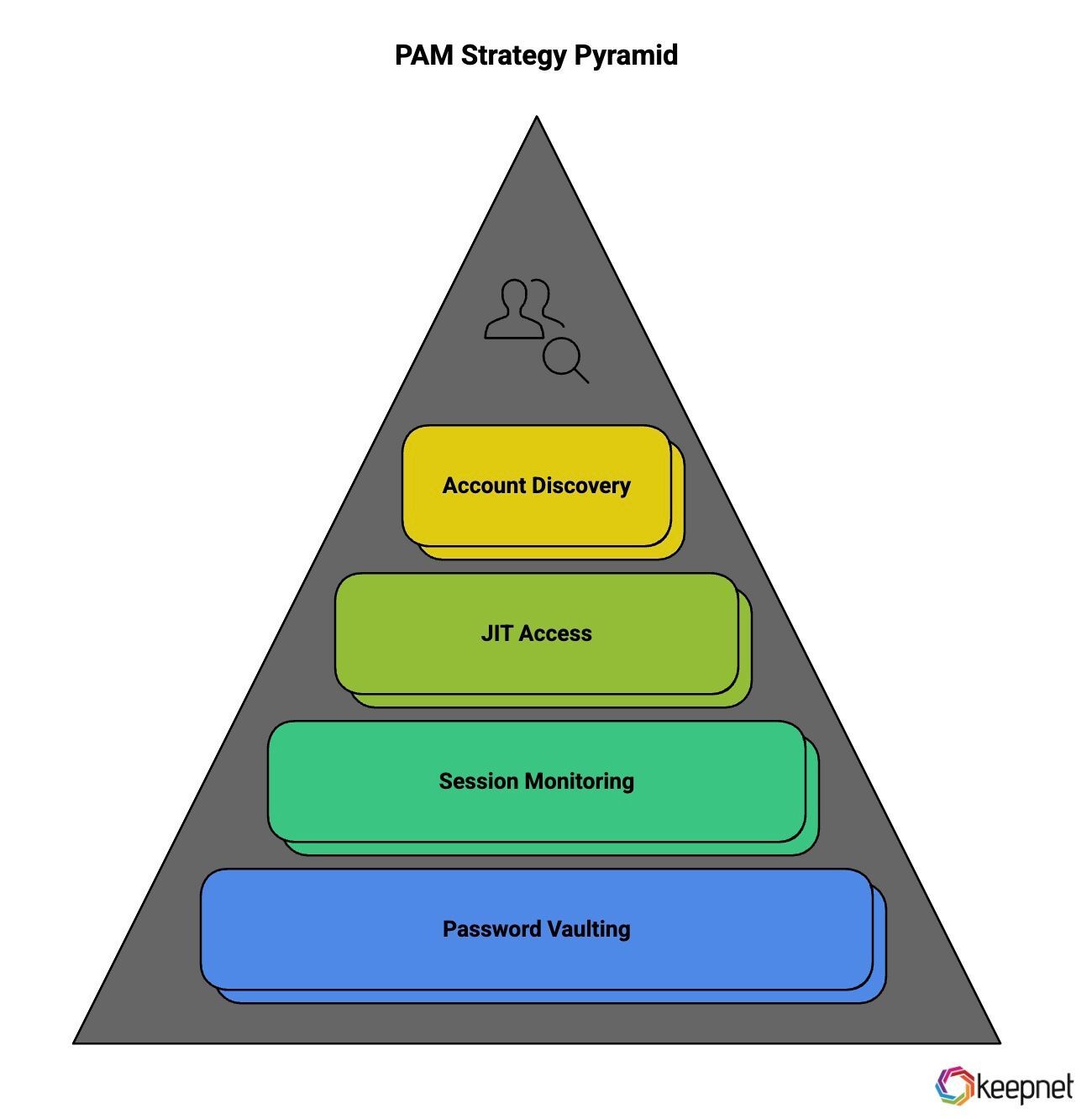
1. Password Vaulting
At the core of any PAM strategy is password vaulting, which ensures that privileged credentials are securely stored, encrypted, and rotated on a regular basis.
This practice helps prevent unauthorized access and limits the risk of credential theft. Modern vaulting solutions also support password check-in/check-out procedures and session initiation directly from the vault, further enhancing operational security.
2. Session Monitoring and Recording
Effective PAM solutions offer real-time session monitoring and full session recording to provide visibility into privileged user activities.
This capability enables security teams to detect suspicious behavior, investigate incidents more efficiently, and maintain accountability through detailed audit trails. Session playback also supports forensic analysis and ensures compliance with industry regulations.
3. Just-in-Time (JIT) Access
JIT access grants temporary, time-bound access to privileged accounts only when needed, significantly reducing the window of opportunity for misuse.
By eliminating standing privileges, organizations minimize attack surfaces and limit exposure to internal and external threats. This approach aligns with the principle of least privilege and enhances operational agility.
4. Privileged Account Discovery
Before securing privileged accounts, organizations must first identify them. Privileged account discovery tools scan across networks, endpoints, cloud platforms, and applications to locate unmanaged or orphaned accounts that pose hidden risks.
Once discovered, these accounts can be brought under centralized management and secured in line with PAM policies.
Best Practices for Implementing PAM
Implementing Privileged Access Management successfully requires more than just deploying technology—it demands a strategic approach that aligns with your organization’s security objectives and operational workflows.

Below are industry-recognized best practices designed to strengthen your PAM framework, improve accountability, and reduce the risk of privilege misuse.
1. Start with an Audit
Begin by conducting a comprehensive audit of all privileged accounts, credentials, and entitlements across your environment. This includes on-premises infrastructure, cloud platforms, SaaS applications, and DevOps pipelines.
The goal is to identify who has elevated access, whether it’s still needed, and how these privileges are currently managed. This foundational step reveals security gaps and informs the scope of your PAM program.
2. Adopt the Principle of Least Privilege (PoLP)
Limit user access rights to the bare minimum required for their roles and responsibilities. By enforcing PoLP, organizations reduce the potential damage caused by insider threats or compromised credentials. Incorporate Privileged Password Management to monitor and control access to high-value credentials, reducing the risk of lateral movement after a breach.
Regularly review and adjust privileges to ensure they align with evolving job functions and access requirements.
3. Implement Multi-Factor Authentication (MFA)
Strengthen security controls by requiring at least two forms of authentication before granting access to privileged accounts.
MFA adds a critical barrier against unauthorized access, especially in cases where passwords are stolen or leaked. Integrating MFA into your PAM solution ensures that identity verification is both continuous and adaptive.
4. Invest in Robust PAM Tools
Choose PAM tools that integrate seamlessly with your existing IT ecosystem and support scalability, automation, and policy enforcement.
Modern solutions should provide capabilities such as automated credential rotation, real-time activity monitoring, risk scoring, and policy-based access control. Investing in the right tools not only simplifies management but also ensures compliance with regulatory standards.
How Keepnet Strengthens Your Privileged Access Management Strategy
While traditional Privileged Access Management solutions focus on securing access points and credentials, Keepnet Human Risk Management takes your security posture a step further by addressing the human element—often the most exploited vulnerability in cyberattacks.
Keepnet’s platform is uniquely positioned to complement and strengthen your PAM strategy through advanced human risk management, real-time behavior analytics, and automated awareness interventions.
1. Bridging the Gap Between Technology and Human Behavior
PAM systems excel at controlling who gets access to what, but they often lack visibility into why certain actions are taken or how human errors occur. Keepnet’s Human Risk Management Platform identifies risky user behavior—such as credential sharing, phishing link clicks—before they escalate into full-blown security incidents. This feeds directly into PAM policies, enabling more informed decisions around privilege assignments and access controls.
2. Real-Time Threat Response and Insider Risk Mitigation
Insider threats, whether malicious or accidental, are among the most difficult to detect. Keepnet’s behavioral analytics engine monitors user actions through various phishing simulations and correlates them with known threat patterns.
Keepnet triggers automated alerts based on employee behavior and, if integrated, can even prompt your PAM solution to revoke or restrict access in real-time.
3. Security Awareness Training Aligned with PAM Goals
A critical yet overlooked component of a successful PAM strategy is employee awareness education. Keepnet offers targeted security awareness training tailored to privileged users, IT administrators, and developers. Through gamified contents, phishing tests, and real-world scenarios (including deepfake phishing and MFA fatigue simulations), Keepnet ensures that high-risk users understand the importance of secure access practices and are capable of recognizing social engineering threats that target privileged credentials.
4. Automated User Risk Scoring to Prioritize Privileged Account Monitoring
Keepnet assigns dynamic user risk scores to users based on their behavior, training completion status, and incident history. When integrated with your PAM solution, these scores help prioritize which privileged accounts require closer monitoring, temporary access restrictions, or additional authentication layers. This enables security teams to focus their efforts where the risk is highest, optimizing both performance and protection.
5. Seamless Integration Across Security Ecosystems
Keepnet’s platform is designed with interoperability in mind. Whether you’re using BeyondTrust, CyberArk, Thycotic, or other PAM vendors, Keepnet integrates effortlessly through APIs and SIEMs to enrich access logs with human risk insights. This provides a 360-degree view of privileged activity—from technical access records to behavioral context—helping organizations build a smarter, adaptive security model.
In essence, Keepnet doesn’t replace your PAM solution—it enhances it. By weaving human-centric cybersecurity into your access controls, Keepnet empowers organizations to build a truly resilient privileged access environment that is aware, adaptive, and aligned with modern cyber risk realities.
Editor's Note: This blog was updated on August 28, 2025.