Phishing Examples: Real Phishing Attacks by Type, Industry, and Emotion
Explore detailed phishing examples covering fear, urgency, finance, healthcare, and more. Strengthen your cybersecurity awareness by understanding the real types of phishing attacks and learning effective methods to identify and avoid threats.
Phishing attacks remain among the most prevalent cybersecurity threats, responsible for nearly 90% of all data breaches globally. With attackers constantly evolving their methods, understanding real phishing attack examples is essential to protect your organization effectively.
In this comprehensive guide, you’ll explore over 50 real-world phishing examples categorized by emotional triggers such as fear, urgency, and curiosity; targeted industries like finance, healthcare, and technology; and attack methods including email, spear phishing, and business email compromise (BEC). Gain actionable insights to detect threats early and strengthen your defense against phishing attacks.
Top Phishing Examples by Emotional Trigger
Phishing attacks succeed primarily because cybercriminals skillfully exploit human emotions. By triggering specific feelings, such as fear, greed, trust, curiosity, guilt, or urgency, attackers trick victims into sharing sensitive data, clicking malicious links, or downloading harmful attachments. Understanding these emotional phishing triggers can significantly boost your ability to detect and avoid phishing scams.
Fear-Based Phishing Examples
Fear-based phishing attacks rely on panic and anxiety, prompting victims to act quickly without thinking. Typical fear-triggered emails include urgent security alerts, warnings about compromised accounts, or legal threats. For instance, a common scenario is an email claiming your bank account has been hacked, demanding immediate login to verify identity. Users who click the link unknowingly hand over sensitive credentials directly to cybercriminals.
Greed-Based Phishing Examples
Greed is another powerful emotional trigger exploited in phishing. Attackers promise enticing financial gains, special offers, or unexpected rewards to lure their targets. Examples include fake lottery winnings, inheritance claims, or cryptocurrency investment schemes. For instance, a recent phishing scam sent emails claiming recipients had won a sizable prize, requiring a small upfront fee or sensitive banking details to collect it, resulting in significant financial loss.
Trust-Based Phishing Examples
Trust-based phishing leverages established relationships or reputable brands to deceive victims. Cybercriminals mimic trusted entities, such as banks, insurance providers, or widely used platforms like PayPal or Microsoft, using realistic logos, accurate company details, and professional language. An example includes emails appearing from IT departments requesting password changes, tricking employees into handing over login details directly to attackers.
Curiosity-Based Phishing Examples
Curiosity-driven phishing campaigns entice users to click links or attachments by provoking intrigue. Cybercriminals craft engaging subject lines such as “You won’t believe what your colleague said about you,” or “See who viewed your profile.” For example, employees might receive emails referencing internal company announcements or intriguing headlines, leading them to open infected attachments or visit malicious websites, unknowingly infecting their systems with malware.
Guilt-Based Phishing Examples
Guilt can be surprisingly effective in phishing attacks. Attackers create scenarios that pressure users into immediate action out of obligation or remorse. Common examples include fraudulent charity solicitations, fake overdue invoice notices, or supposed legal warnings. One notable campaign involved attackers sending fake emails posing as charities, guilting recipients into donating money or revealing payment information to scammers.

Urgency-Based Phishing Examples
Urgency-based phishing attacks pressure victims by imposing strict time constraints or claiming imminent negative consequences. These attacks exploit the human instinct to respond swiftly under pressure, overriding caution. Typical examples include messages like “Your account will be suspended in 24 hours!” or “Immediate action required: Confirm your details now.” Recently, phishing attacks impersonating Amazon urged customers to urgently confirm their payment information to avoid losing prime membership benefits, resulting in stolen personal and financial data.
By learning to recognize these emotional phishing tactics, individuals and organizations can significantly reduce vulnerabilities and proactively defend against these increasingly sophisticated cyber threats.
Key Phishing Examples by Industry
Phishing attacks often target specific industries due to their valuable data, sensitive operations, or critical financial information. Cybercriminals tailor their phishing emails to incorporate industry-specific terminology, procedures, and common scenarios, thereby significantly enhancing their effectiveness.
Here are real-world phishing examples across prominent industries, helping you identify targeted threats and secure your organization:
Financial Sector Phishing Examples
The financial industry is a prime target for phishing due to its direct access to money and sensitive customer data. Cybercriminals frequently impersonate banks, financial advisors, or investment firms. Examples include emails claiming suspicious account activity or fake transaction alerts prompting immediate login. A recent sophisticated phishing campaign impersonated Wells Fargo, prompting customers to urgently verify their credentials to avoid account suspension, which led to significant financial fraud.
Healthcare Sector Phishing Examples
Healthcare organizations face phishing attacks aimed at obtaining valuable medical records, patient data, or access to internal systems. Attackers commonly pose as health authorities, insurance companies, or internal hospital departments. During the COVID-19 pandemic, attackers sent emails claiming to contain important vaccine appointment details, tricking recipients into clicking malicious links that installed malware and compromised sensitive health information.
Retail Sector Phishing Examples
Phishing in the retail sector often exploits online shoppers and retail employees with fake promotional offers, order confirmations, or shipment notices. Attackers impersonate popular brands, sending convincing emails with malicious links or attachments. For example, attackers recently posed as Amazon, claiming order delivery issues and prompting users to re-enter payment details, resulting in stolen credit card information and personal data. If credit card details are compromised in such attacks, enrolling in credit monitoring services can help detect and alert users to any unauthorized activity.
Education Sector Phishing Examples
Schools, universities, and educational institutions are frequent phishing targets due to large student databases, research data, and widespread use of email systems. Typical phishing examples include fake password reset requests, university system outage alerts, or scholarship application notifications. Recently, a phishing attack targeted university students with fake internship opportunities requiring submission of personal information, leading to identity theft.
Technology Sector Phishing Examples
The technology industry experiences highly sophisticated phishing campaigns aimed at stealing intellectual property, technical credentials, or accessing internal networks. Attackers impersonate trusted tech providers or internal IT support teams. A notable incident involved attackers mimicking Microsoft technical support, emailing IT professionals with fake urgent security updates containing malicious payloads, granting attackers access to critical company resources.
Government and Public Sector Phishing Examples
Government organizations face persistent phishing threats targeting sensitive data, employee credentials, and internal communication systems. Phishing emails frequently impersonate official government agencies, tax authorities, or public service announcements. In one significant campaign, attackers posed as the IRS, emailing employees fraudulent tax refund notices with malicious attachments, compromising sensitive government data and leading to financial losses.
Understanding how phishing threats differ across industries allows organizations to strengthen targeted training, implement preventive measures, and mitigate risk effectively.
Common Phishing Examples by Region
Phishing tactics often vary by region, influenced by local culture, language, current events, and regulatory environments. Attackers frequently customize phishing campaigns to align with regional trends, trusted institutions, and localized fears or interests.
Here are real-world phishing examples by geographical region to help you recognize and mitigate these localized threats effectively:
North America Phishing Examples
North America experiences frequent phishing attacks targeting financial institutions, tax authorities, and major tech companies. A common example is IRS impersonation, especially during tax season, where cybercriminals send emails claiming recipients have pending refunds requiring immediate bank account verification. Similarly, attackers recently impersonated Canadian banks, sending alerts about unauthorized transactions, successfully stealing personal financial information.
Europe Phishing Examples
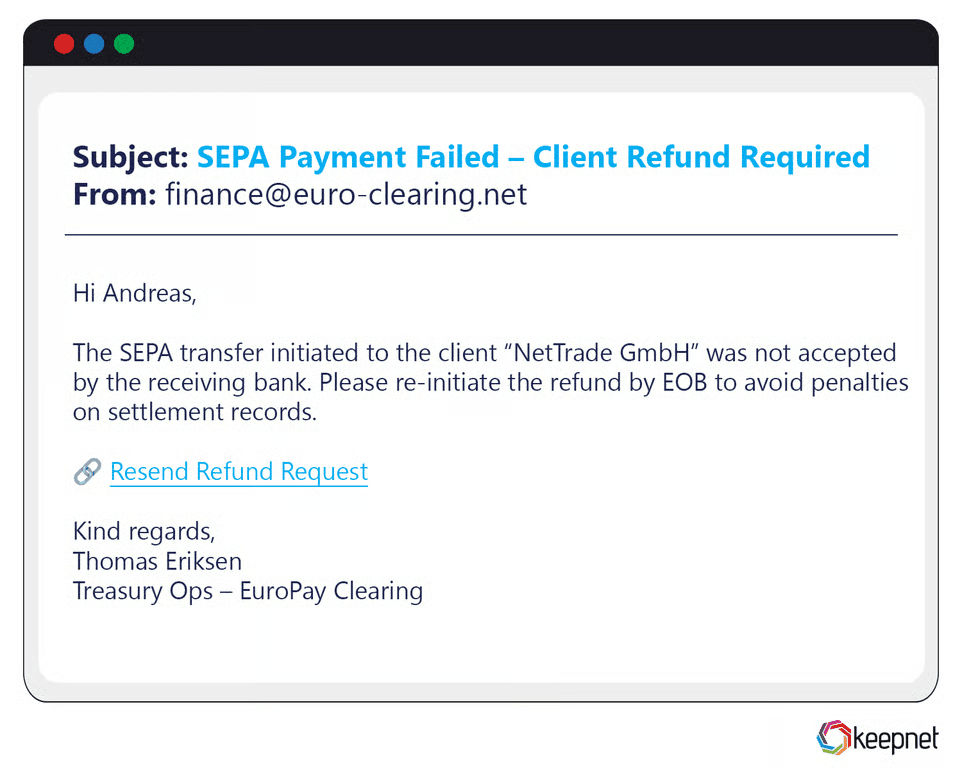
In Europe, phishing campaigns often exploit major political events, GDPR compliance, and regional banking institutions. For instance, phishing emails impersonating the European Central Bank (ECB) claimed that users needed to update personal data due to regulatory changes, redirecting them to fraudulent websites to steal confidential information. Brexit-themed phishing emails also surged, exploiting confusion by promising updates or necessary document submissions.
Asia Phishing Examples
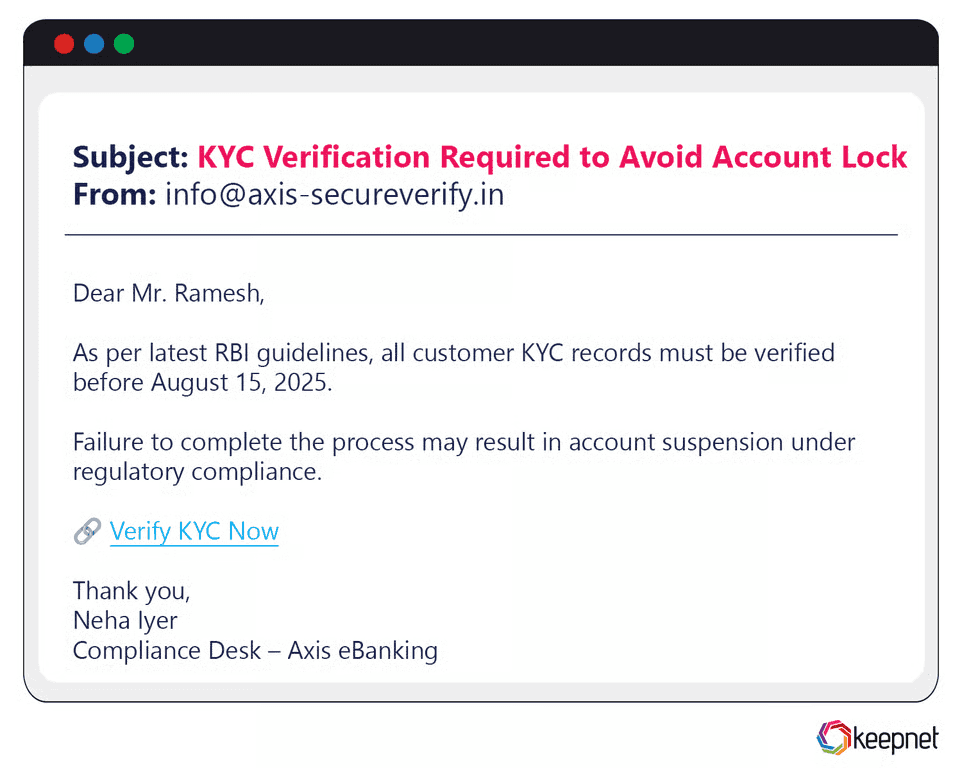
Phishing campaigns in Asia often leverage popular mobile apps, financial services, and e-commerce platforms. Notably, attackers impersonated Alipay and WeChat Pay, two dominant payment systems in China, sending fake payment confirmations or refund alerts to trick users into providing account credentials. Additionally, in India, phishing emails posed as government entities offering COVID-19 vaccination appointments, compromising personal details through malicious links.
Middle East Phishing Examples
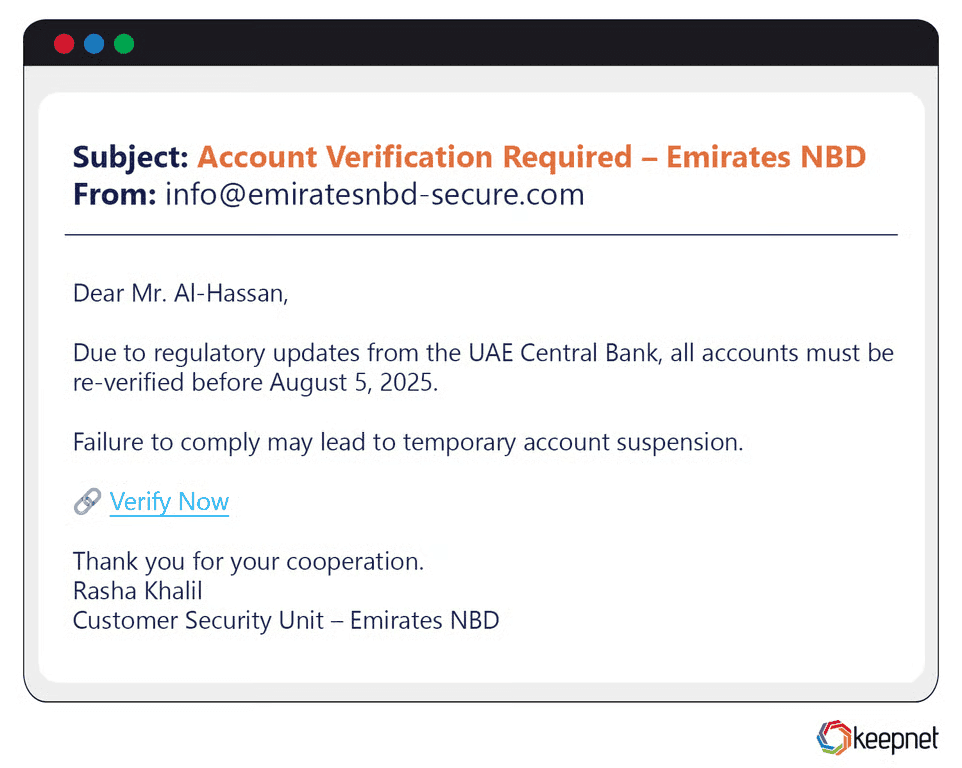
Phishing attacks in the Middle East frequently target governmental institutions, regional banks, and oil and gas enterprises. Cybercriminals have impersonated local banks in Saudi Arabia and the UAE, sending customers fake security alerts requesting urgent account verification, leading to significant financial losses. Attackers also exploited geopolitical tensions, sending phishing emails containing malicious attachments disguised as urgent news updates or security advisories.
Global/Localized Phishing Campaigns
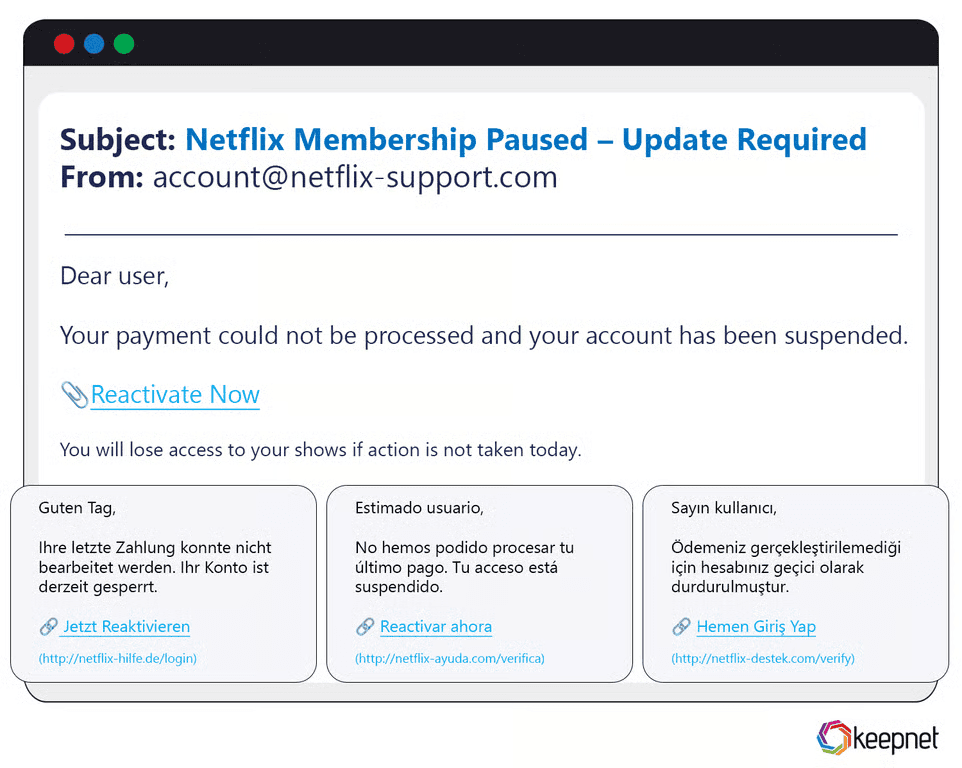
Global phishing campaigns adapt their messages and tactics to appear authentic in multiple regions simultaneously. For example, large-scale attacks impersonating global brands like Microsoft, Apple, and Netflix circulate worldwide in multiple languages. During the FIFA World Cup and Olympics, attackers launched global phishing scams offering fake ticket sales or exclusive streaming access, successfully capturing user credentials and financial information from victims worldwide.
Recognizing regional phishing trends enables organizations to deliver effective, localized cybersecurity awareness training and strengthen defenses against culturally tailored phishing threats.
2026 Phishing Scam Examples by Brand
Cybercriminals frequently impersonate trusted global brands due to their widespread use, recognizable logos, and large user bases. These phishing attacks exploit users’ trust, convincing them to willingly share sensitive credentials, payment details, or personal information.
Understanding common brand-based phishing examples helps individuals and businesses stay vigilant and protect their valuable data.
Google Phishing Examples
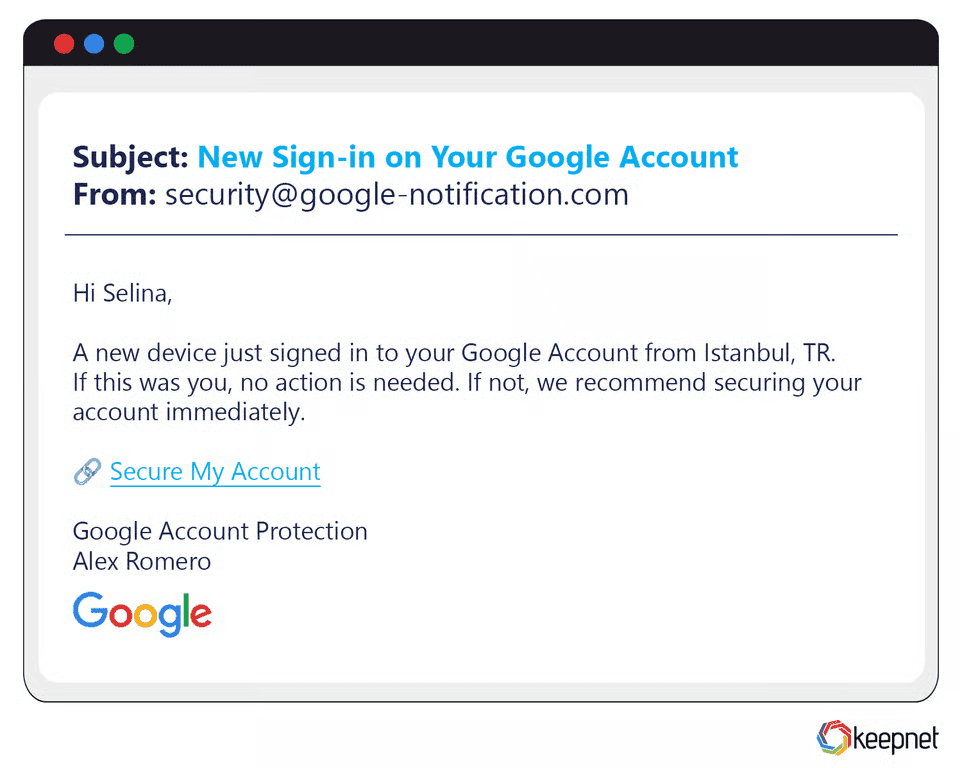
Google, due to its popularity in email, cloud services, and user accounts, is a frequent target of phishing attacks. Attackers often send realistic-looking Google account security alerts claiming unauthorized logins, prompting immediate password resets via malicious links. Another prevalent example includes fake Google Drive invitations that direct users to phishing sites to harvest login credentials, compromising both personal and business data.
PayPal Phishing Examples
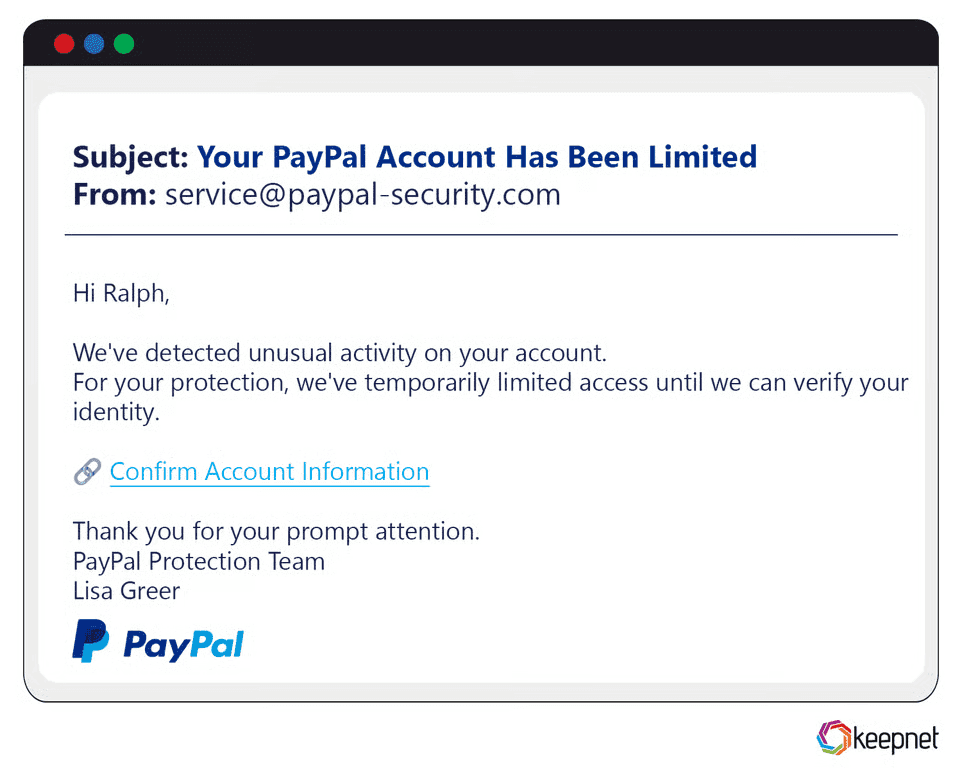
PayPal phishing emails commonly involve fake transaction notifications, warnings about suspicious account activity, or account suspension threats. Attackers mimic PayPal’s official email layout, prompting users to verify accounts urgently. A notorious PayPal phishing campaign involved emails claiming recipients made an unauthorized large purchase, tricking users into clicking links that captured financial information and login details.
Microsoft/Outlook Phishing Examples
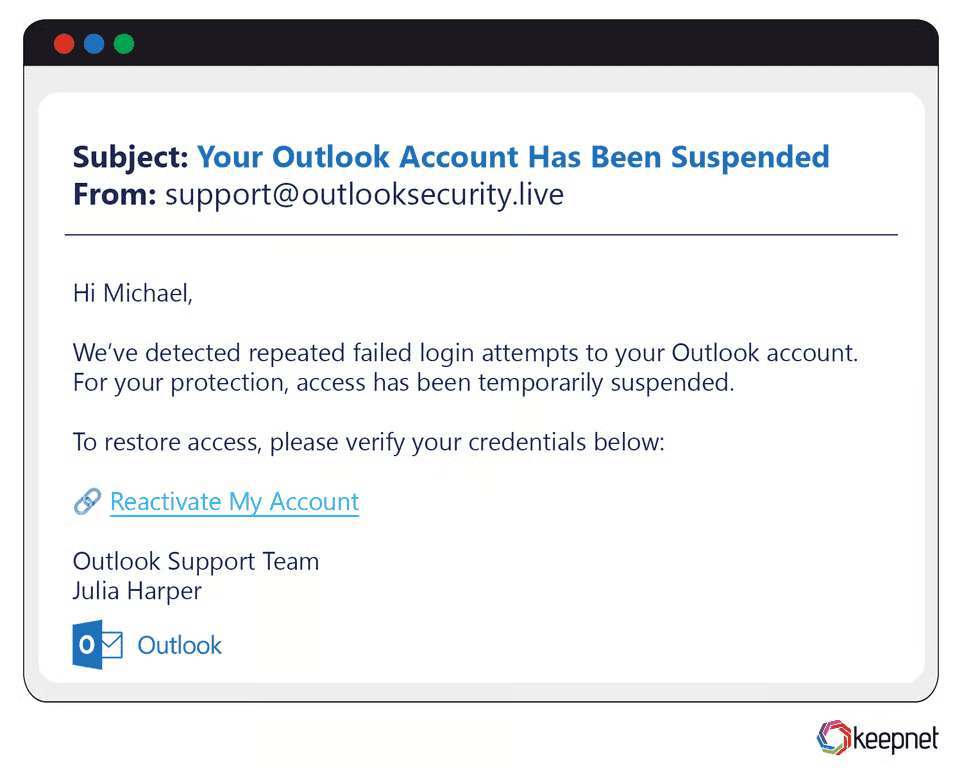
Phishing campaigns targeting Microsoft and Outlook users typically involve fake email alerts regarding mailbox storage limits, password expirations, or mandatory security updates. Recently, attackers impersonated Microsoft IT support, sending convincing emails claiming Outlook accounts were due for mandatory upgrades, directing victims to fraudulent login pages, leading to significant credential theft and subsequent data breaches.
Amazon Phishing Examples
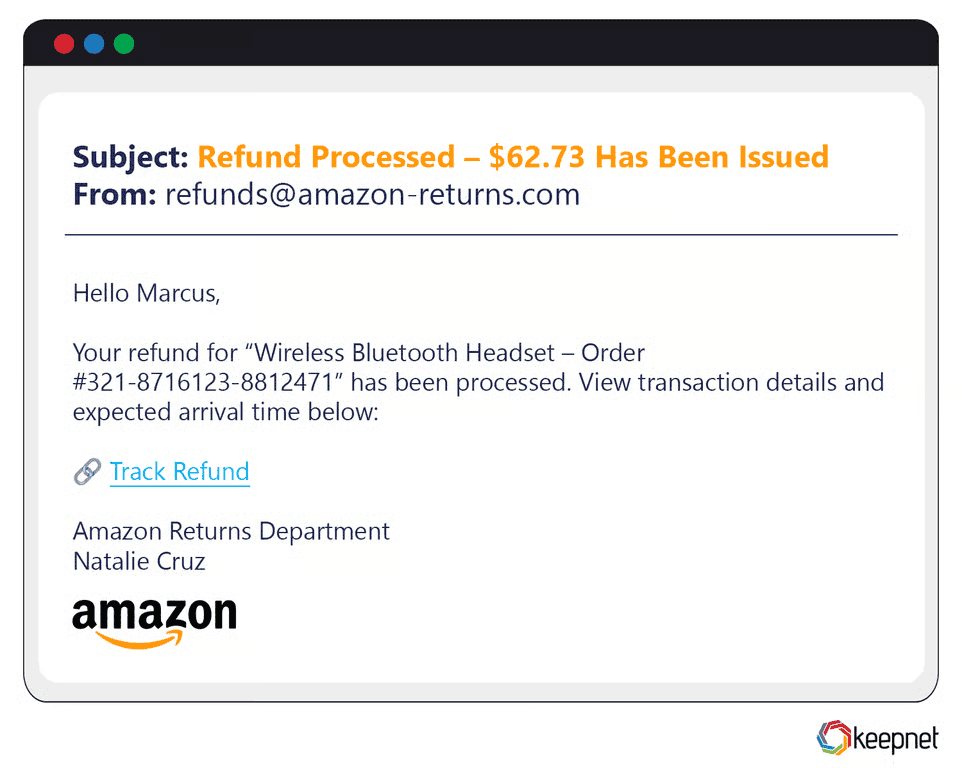
Amazon phishing attacks frequently exploit consumer trust through emails about order confirmations, delivery problems, or account verification requests. A common phishing example includes fake Amazon Prime renewal notifications urging users to confirm payment details. During peak shopping periods, attackers also send realistic-looking delivery tracking emails linking to malicious websites, resulting in stolen payment details and personal information.
Apple/iCloud Phishing Examples
Apple and iCloud phishing emails typically inform users of suspicious account activities, unauthorized device logins, or imminent account deactivation. Attackers convincingly mimic Apple’s branding, directing victims to fraudulent login pages. A prominent campaign involved fake iCloud breach notifications urging immediate password changes, successfully harvesting user credentials and enabling account takeovers.
Dropbox Phishing Examples
Dropbox phishing scams often utilize fake file-sharing invitations or urgent document notifications. Users receive seemingly legitimate emails indicating someone shared an important file, requiring immediate login. Clicking links redirects victims to fraudulent Dropbox login pages designed to capture usernames and passwords. Such attacks can result in significant data leaks, especially affecting sensitive business files and personal documents.
Being aware of how cybercriminals impersonate these trusted brands empowers users to spot phishing scams more easily, strengthening their defense against identity theft, financial losses, and potential data breaches.
Common Phishing Examples by Language
Phishing attacks frequently target victims by leveraging their native languages, increasing credibility and effectiveness. Cybercriminals customize their tactics, messaging styles, and cultural references to appear authentic. Recognizing phishing examples across different languages empowers users globally to detect threats and avoid falling victim.
English Phishing Examples
English remains the most common language for phishing globally, used extensively to target both individuals and businesses. Typical examples include fake password reset requests, banking alerts, and false shipping notifications from major brands. Recent widespread campaigns featured convincing Amazon and Microsoft impersonations, successfully stealing user credentials through sophisticated English-language emails.
Spanish Phishing Examples

Spanish-language phishing emails frequently exploit banking, government notifications, or popular retail offers, especially in Spain and Latin America. Attackers recently targeted Spanish-speaking users with fake tax-refund emails, pretending to be government authorities requiring personal data submissions. Another popular example includes fraudulent Netflix subscription alerts, tricking users into providing financial information.
French Phishing Examples
French-language phishing campaigns often mimic national institutions, banks, and widely used services, particularly across France and French-speaking African nations. Common examples include fraudulent banking notifications or false parcel delivery alerts requiring payment confirmations. A notable recent scam involved fake emails impersonating French telecom providers, successfully tricking users into entering login details and payment data.
German Phishing Examples
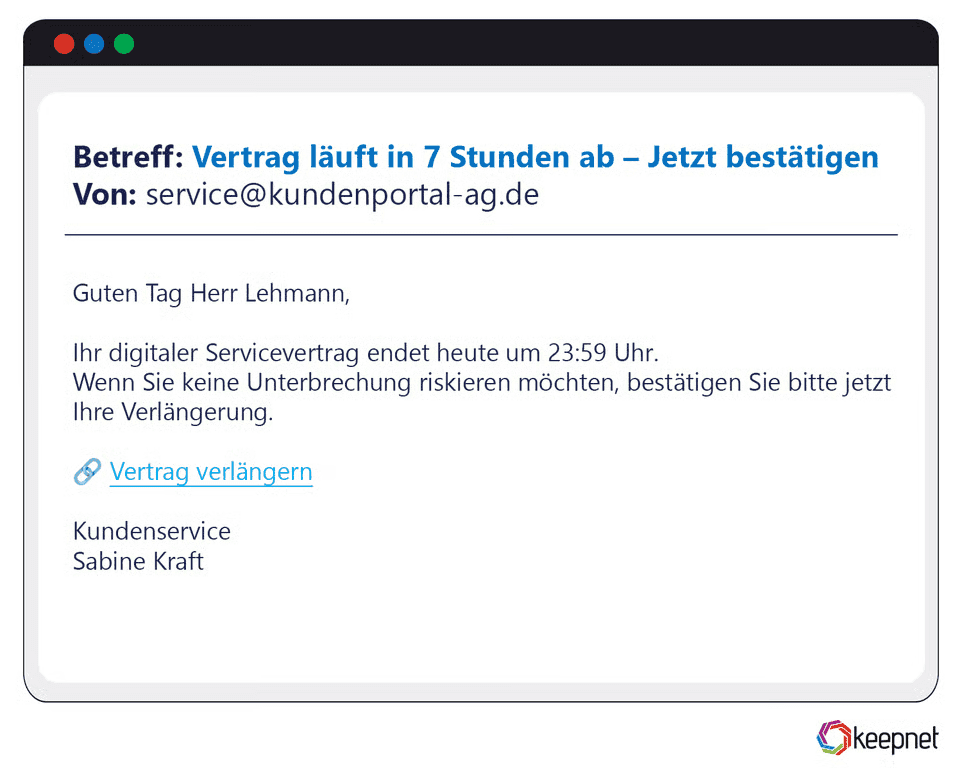
German phishing attacks usually impersonate reputable financial institutions, utility companies, and national services, exploiting user trust within Germany, Austria, and Switzerland. A recent phishing campaign involved fake emails from Deutsche Post, claiming failed parcel deliveries and requesting personal information via malicious links, effectively harvesting user credentials and sensitive data.
Arabic Phishing Attack Examples
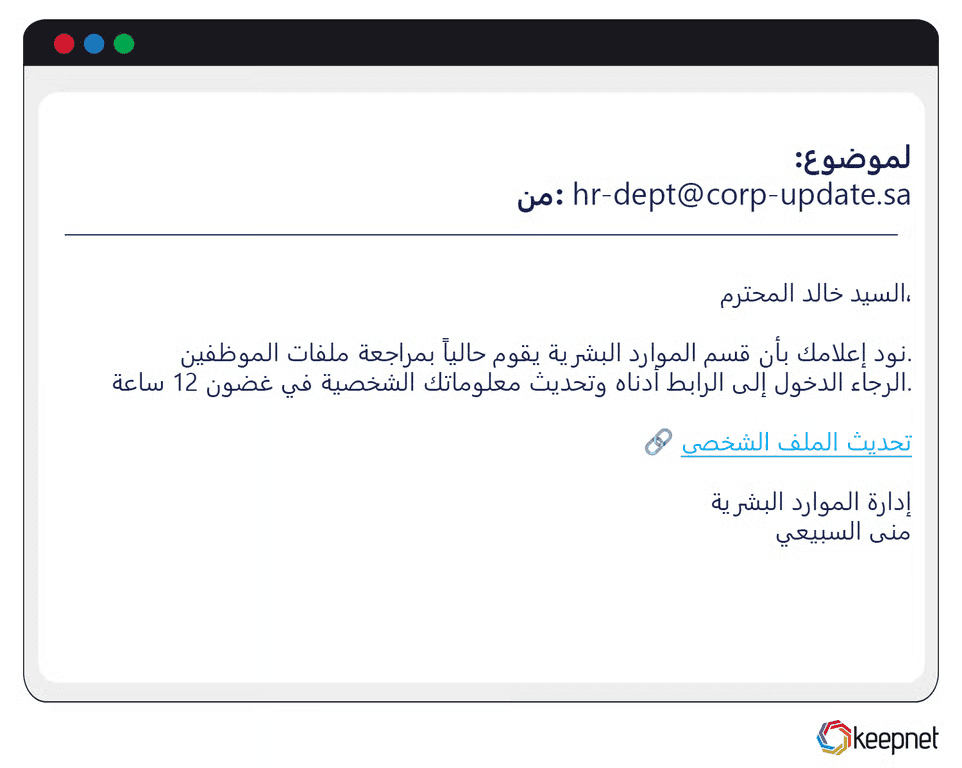
Arabic phishing scams often exploit regional political events, religious occasions, or prominent government services. For instance, attackers recently impersonated Saudi and Emirati banks, sending customers fake security alerts demanding immediate account verification. During Ramadan, cybercriminals targeted Arabic-speaking users with fraudulent charity donation requests, successfully deceiving users into handing over sensitive financial details.
Other Multilingual Phishing Campaigns
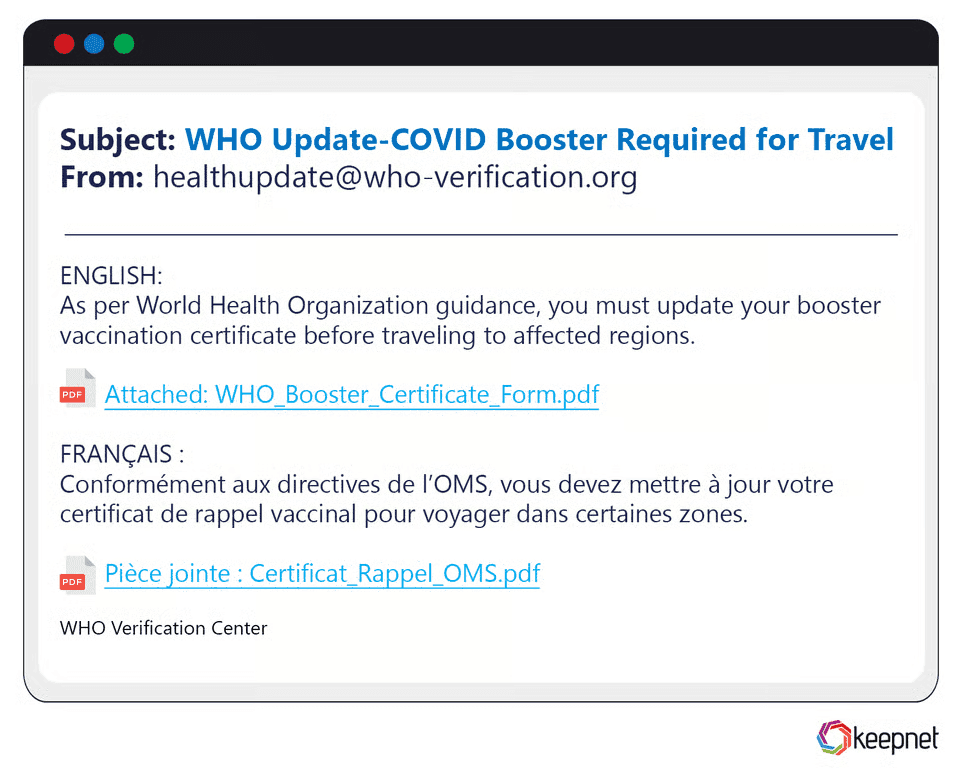
Multilingual phishing campaigns are increasingly common as attackers target diverse, global audiences. Recent notable examples include phishing emails leveraging multiple languages simultaneously, impersonating international organizations like WHO or Interpol. These attacks, often exploiting global crises or health emergencies, convince users worldwide to disclose sensitive personal and financial data through realistic multilingual phishing content.
Understanding phishing across different languages significantly enhances users’ ability to identify and avoid these culturally adapted cyber threats, effectively reducing global phishing risks.
Phishing Attack Examples by Difficulty Level
Phishing attacks vary widely in complexity, ranging from basic scams that almost anyone can recognize to advanced, highly targeted campaigns capable of deceiving even cybersecurity professionals. Understanding phishing threats by their difficulty level helps users and organizations calibrate their cybersecurity training programs, effectively addressing varying levels of sophistication.
Basic Phishing Examples
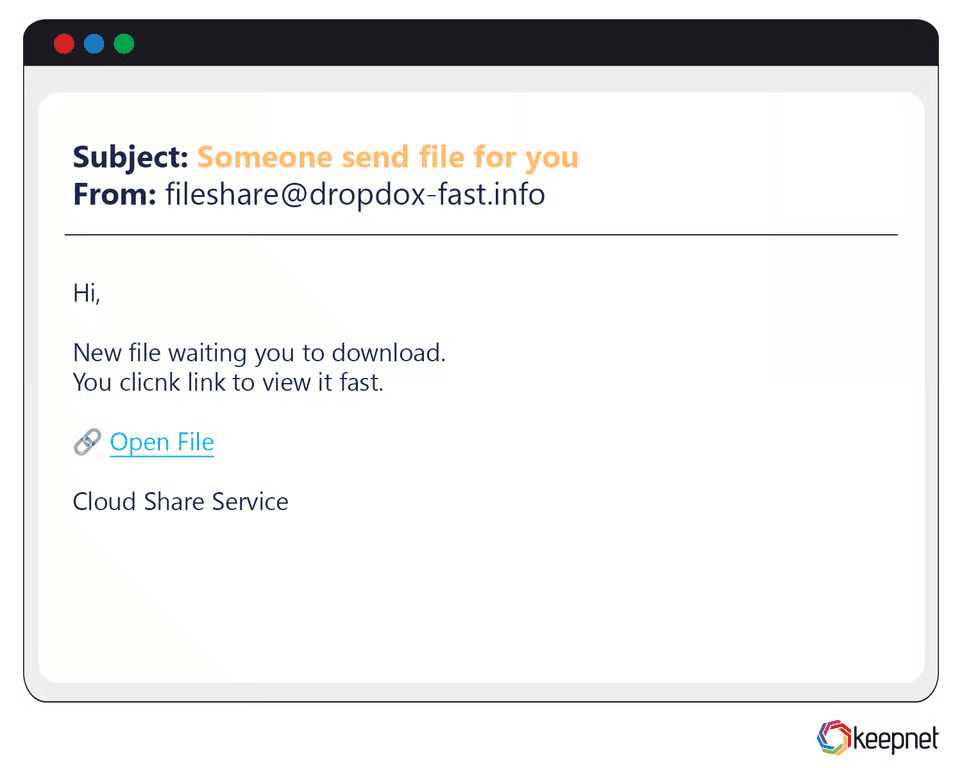
Basic phishing attacks are typically broad, generic, and easy to identify. They often contain noticeable spelling errors, poor grammar, or suspicious sender addresses. Common examples include emails claiming you've won a lottery, received an inheritance from an unknown relative, or requiring urgent account verification with obviously fake links. Despite their simplicity, these basic scams still trick thousands of less experienced users annually.
Intermediate Phishing Examples
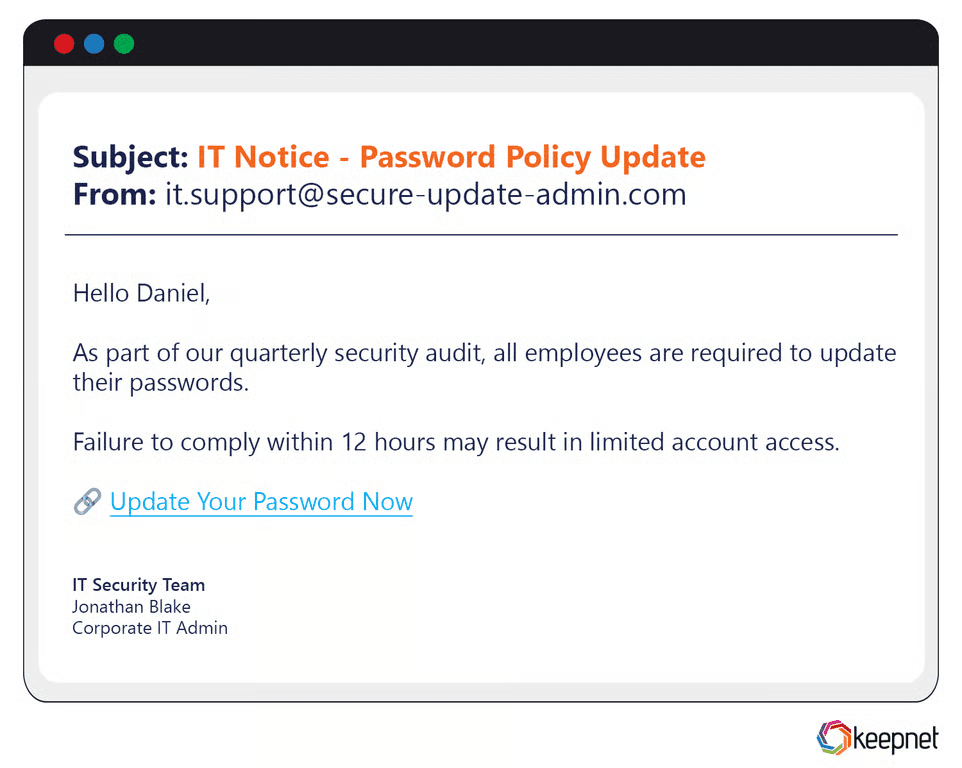
Intermediate phishing scams demonstrate a higher level of sophistication. Attackers use accurate logos, legitimate-looking email templates, and more convincing scenarios, such as fake delivery notifications or credible account security alerts. An example includes phishing emails mimicking popular services like Netflix or Spotify, claiming payment issues, prompting users to re-enter payment details through convincingly designed fake webpages, leading to compromised financial information.
Advanced Phishing Scam Examples
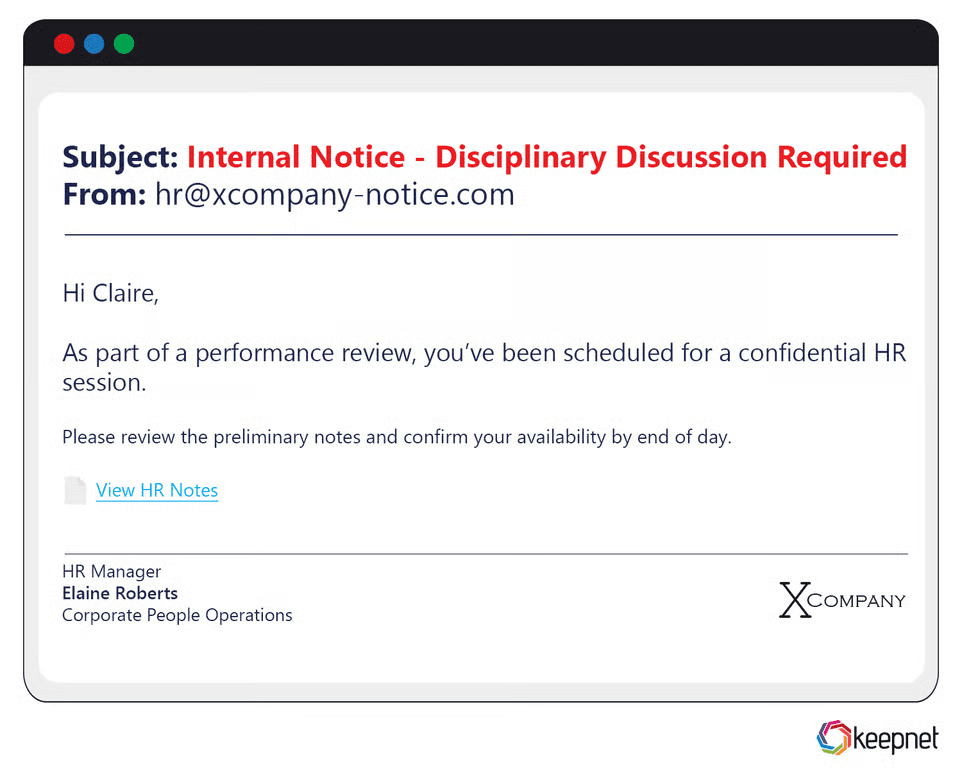
Advanced phishing attacks carefully mimic trusted brands or internal communications, often employing personalized details or contextually relevant scenarios. Cybercriminals might include the recipient’s actual name, reference recent interactions, or accurately replicate internal communication styles. For instance, a notable advanced phishing campaign involved attackers impersonating an employee’s manager, referencing a recent business event, and requesting the recipient urgently review a confidential document embedded with malware.
Highly Targeted Phishing Examples
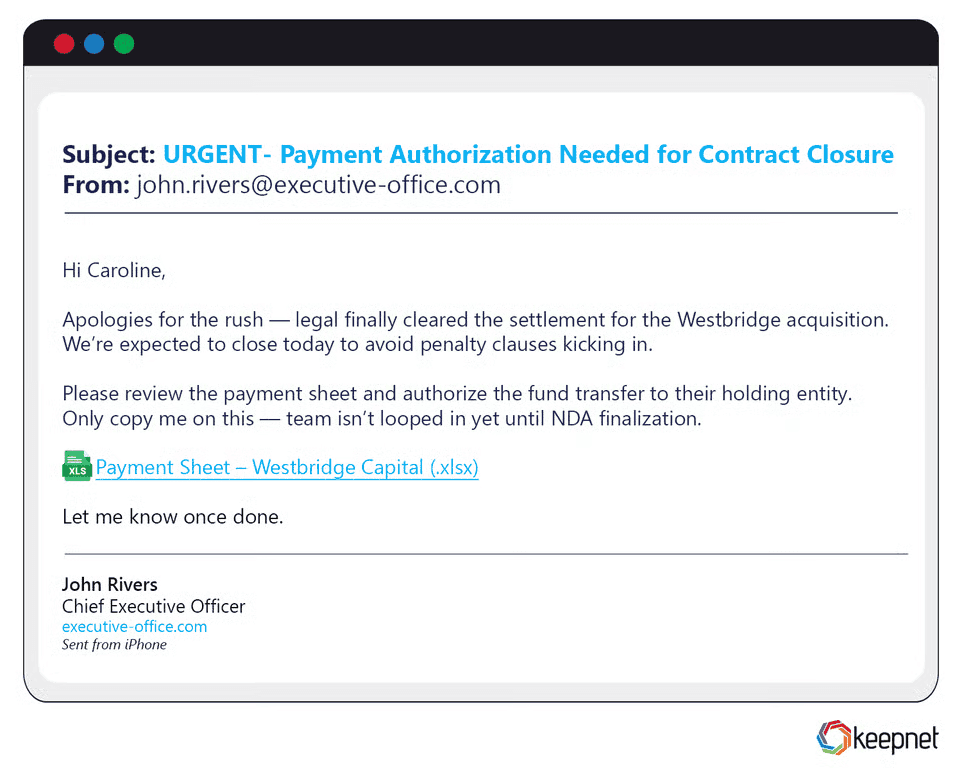
Highly targeted phishing, or spear phishing, involves meticulous research and precise customization. Attackers gather detailed personal or organizational information, crafting messages specifically tailored to high-value targets such as executives, IT administrators, or finance directors. For example, attackers recently targeted a company's CFO with a carefully crafted email seemingly from the CEO referencing a real upcoming merger, requesting confidential financial documents. This sophisticated spear phishing attack successfully led to unauthorized disclosure of sensitive corporate information and financial losses.
Recognizing phishing attempts at every difficulty level enables users and organizations to effectively tailor cybersecurity training, significantly enhancing their ability to identify threats and minimize potential damage.
Top Phishing Examples by Delivery Vector
Phishing attacks are delivered through various vectors—each using different tactics to deceive users. While some phishing emails rely on malicious attachments, others embed harmful links, multimedia content, or even fake applications. Understanding phishing delivery methods helps organizations create more targeted defenses and empower users to identify red flags effectively.
Attachment-Based Phishing Attack Examples
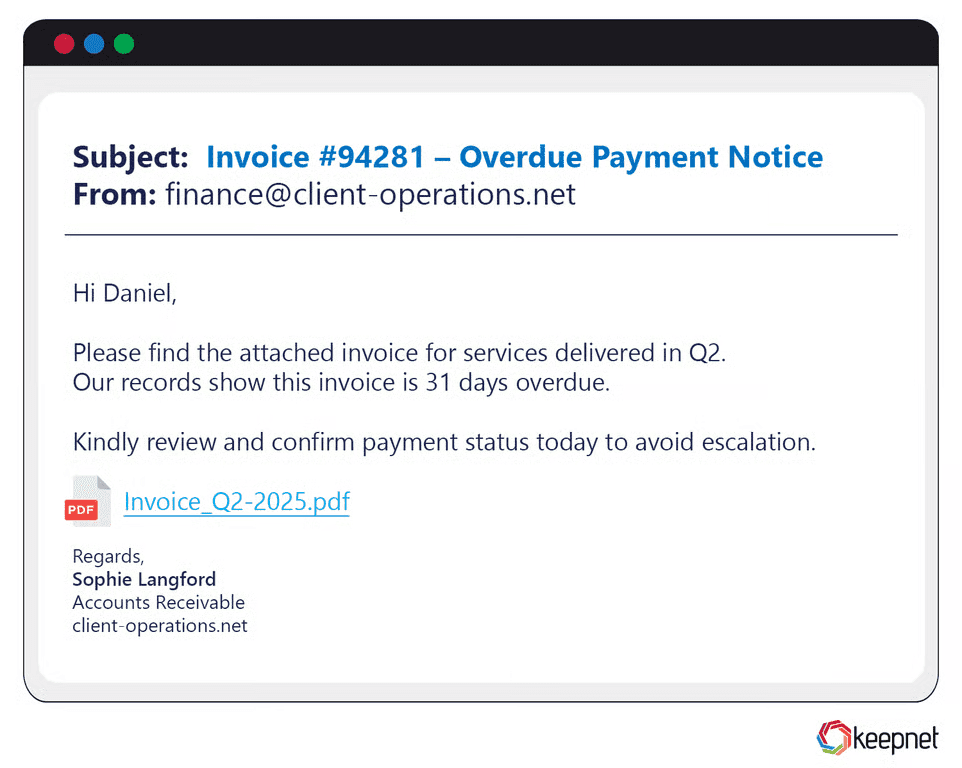
Attachment-based phishing attacks are among the oldest yet still highly effective tactics. Cybercriminals send emails containing infected files—often disguised as invoices, resumes, or company reports. These attachments, typically in PDF, Word, or Excel format, contain embedded malware or scripts that activate upon opening. For example, attackers have sent fake HR policy documents with macro-enabled Word files. Once opened, they execute malicious code, granting attackers access to the victim’s system.
Link-Based Phishing Fraud Examples
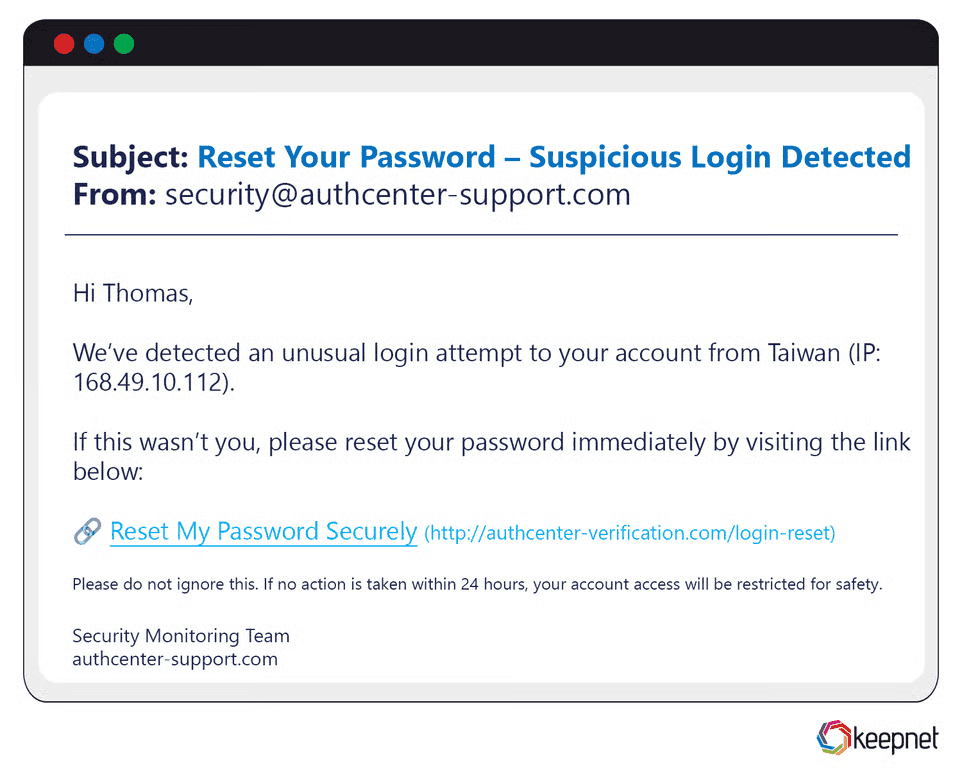
Link-based phishing is one of the most common and scalable attack vectors. These emails contain URLs that redirect users to fake websites mimicking login portals for services like Office 365, Google Workspace, or banking platforms. Once victims enter their credentials, attackers harvest them instantly. A common example is a fake “reset your password” email from a popular service, with a convincing look-alike link that steals login information.
Embedded Media Phishing Examples
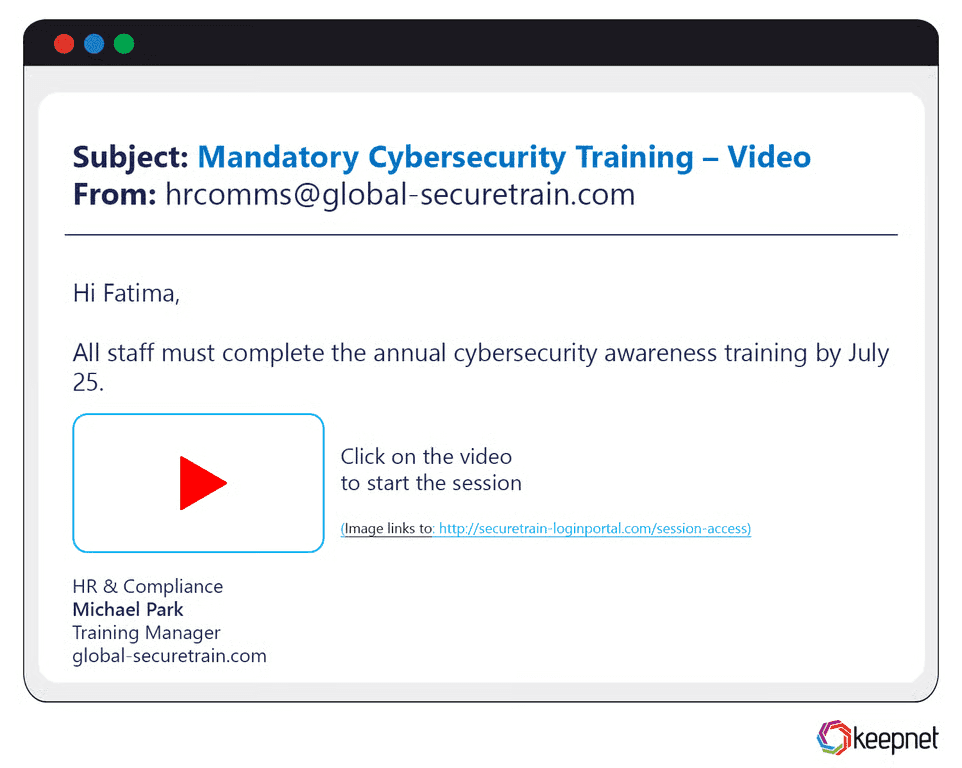
Some phishing campaigns use embedded media such as images, videos, or HTML buttons that look like real interface elements but link to malicious content. These emails may contain clickable banners (“Track your shipment” or “View invoice”) that redirect to phishing sites. One recent campaign embedded a fake “play” button in an email claiming to contain a video message from HR, tricking users into entering credentials on a spoofed page after clicking the media.
Fake Application-Based Phishing Fraud Examples
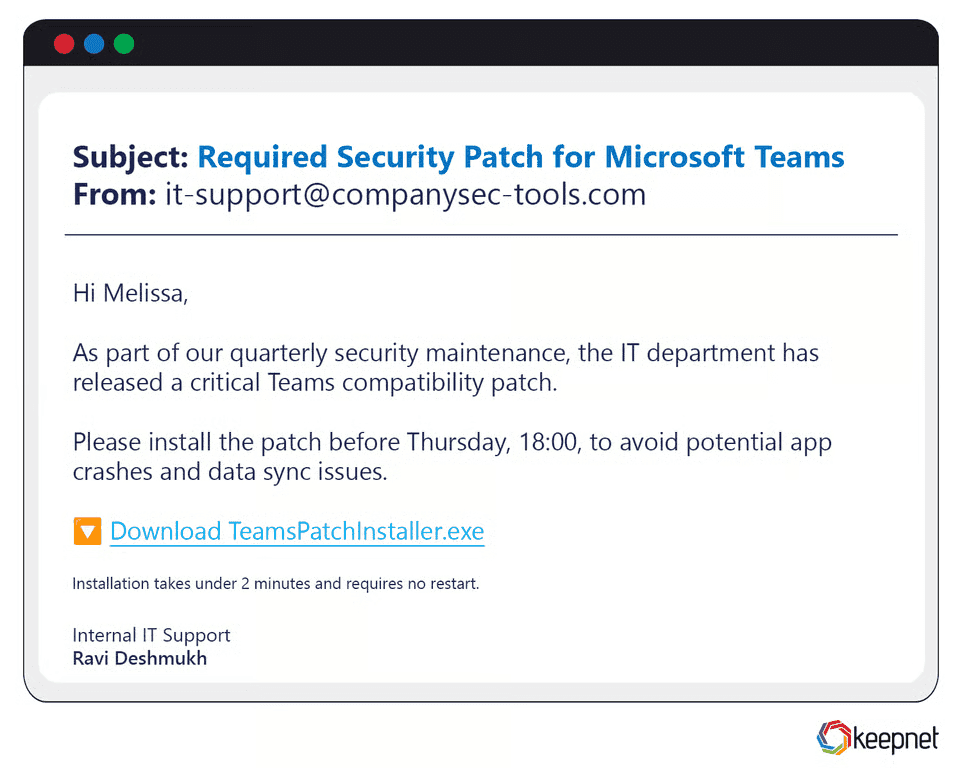
Fake application phishing involves malicious software disguised as legitimate apps. These are often sent via email or promoted on phishing websites. In corporate environments, attackers may send fake IT tools or updates disguised as productivity apps. One notable example involved an attacker posing as internal IT support, emailing employees a link to install a “security patch” that was, in fact, spyware. Once installed, it silently captured keystrokes and login details.
Recognizing how phishing threats are delivered—whether through attachments, links, embedded content, or malicious apps—helps users stay vigilant and avoid falling for increasingly sophisticated scams. Security awareness programs should focus on educating employees about these diverse delivery methods to reduce risk organization-wide.
Phishing Attack Samples by Timing
Attackers love a good schedule. By tying their scams to predictable dates—tax season, the holiday rush, or end-of-year reporting—they increase the odds that victims will “click first, think later.” Knowing these timing cues can help security teams schedule just-in-time reminders and tighten controls when risk naturally spikes.
Holiday-Themed Phishing Examples
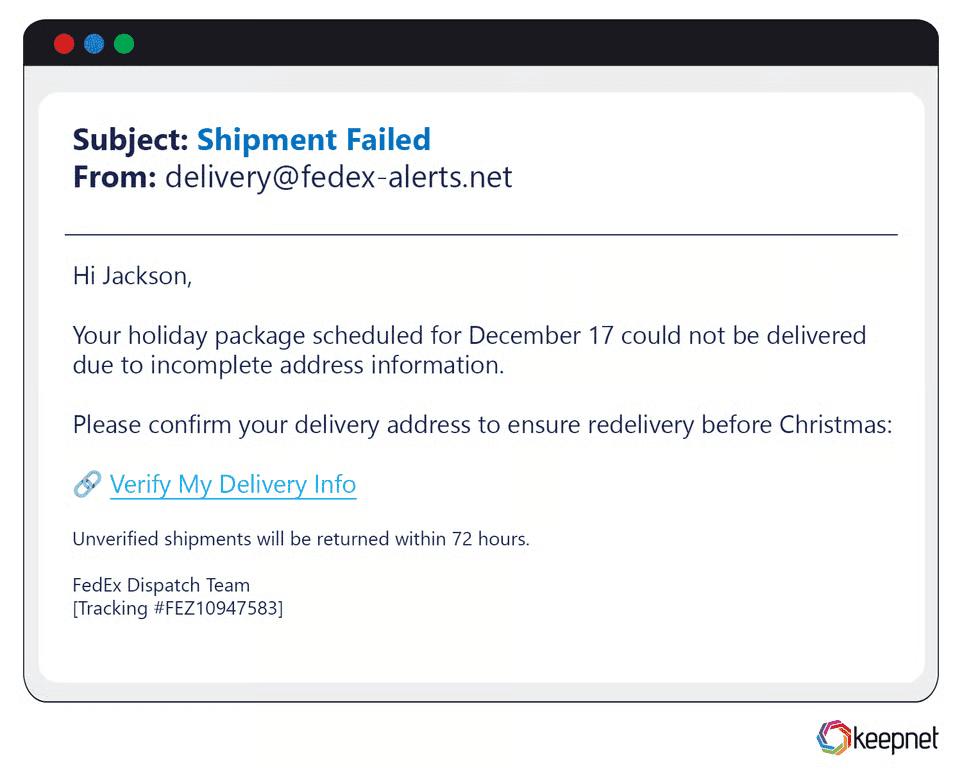
During November–December, inboxes overflow with “exclusive deals,” “gift-card surprises,” and “shipping update” emails. A recent campaign spoofed FedEx tracking notices, tricking shoppers into entering credit-card details on a look-alike site. Long-tail keywords attackers use include “holiday delivery scam email” and “Black Friday coupon malware.”
Tax Season Phishing Examples
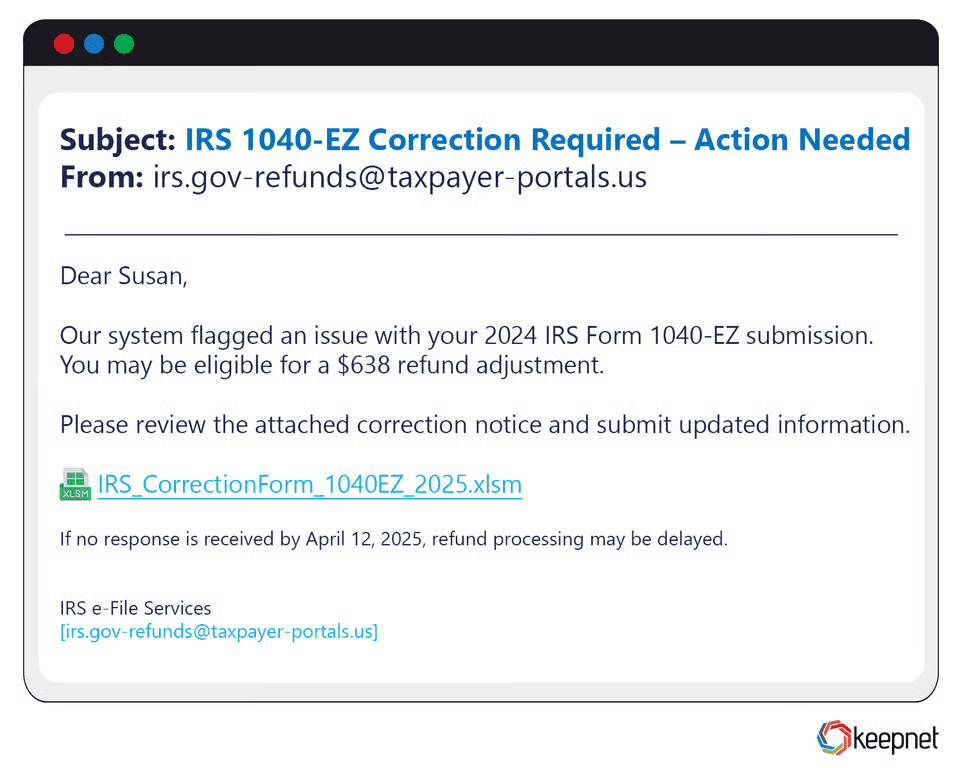
Between January and April, U.S. taxpayers face a blitz of fake IRS refund alerts and W-2 download links. One 2025 scam sent authentic-looking Form 1099 attachments—really a macro-laden spreadsheet that deployed infostealers. Watch for subject lines like “1040 EZ correction required” or “HMRC tax rebate notification” (for UK targets).
Crisis-Based Phishing Examples

Natural disasters, geopolitical conflicts, and public-health emergencies trigger “crisis donation” scams within hours. After a major earthquake in Türkiye, fraudsters circulated bilingual donation pleas with Bitcoin wallets embedded in QR codes. Short-tail hooks such as “urgent relief fund” and “emergency aid payment portal” generated thousands of clicks before takedowns.
Year-End Phishing Campaigns
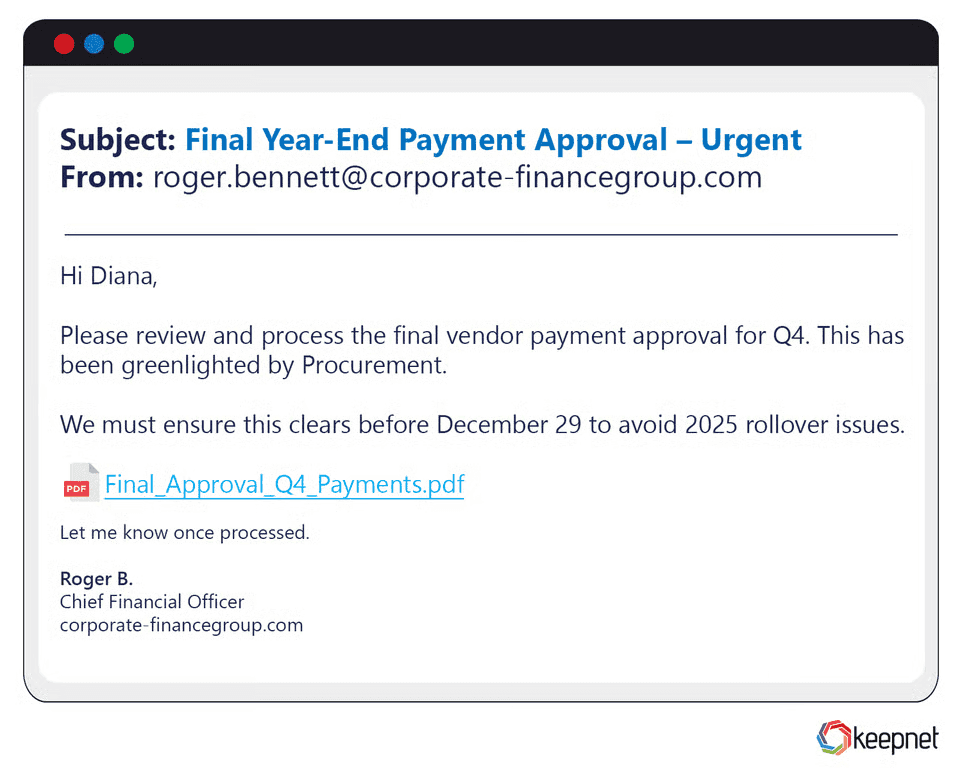
Q4 closeouts mean budget reallocations, bonus calculations, and vendor renewals—prime territory for fake invoice or DocuSign requests. A notable 2024 attack impersonated a CFO, forwarding “final payment approval” PDFs that launched Cobalt Strike beacons. Keywords often leveraged: “year-end invoice phishing”, “enterprise renewal scam.”
Phishing Attack Examples by Holiday or Festive Occasion
Celebrations create distraction—and distracted users are easier marks. Below are common festive-phish themes and real incidents that illustrate how cyber-crooks cash in on holiday cheer.
Valentine’s Day Phishing Examples
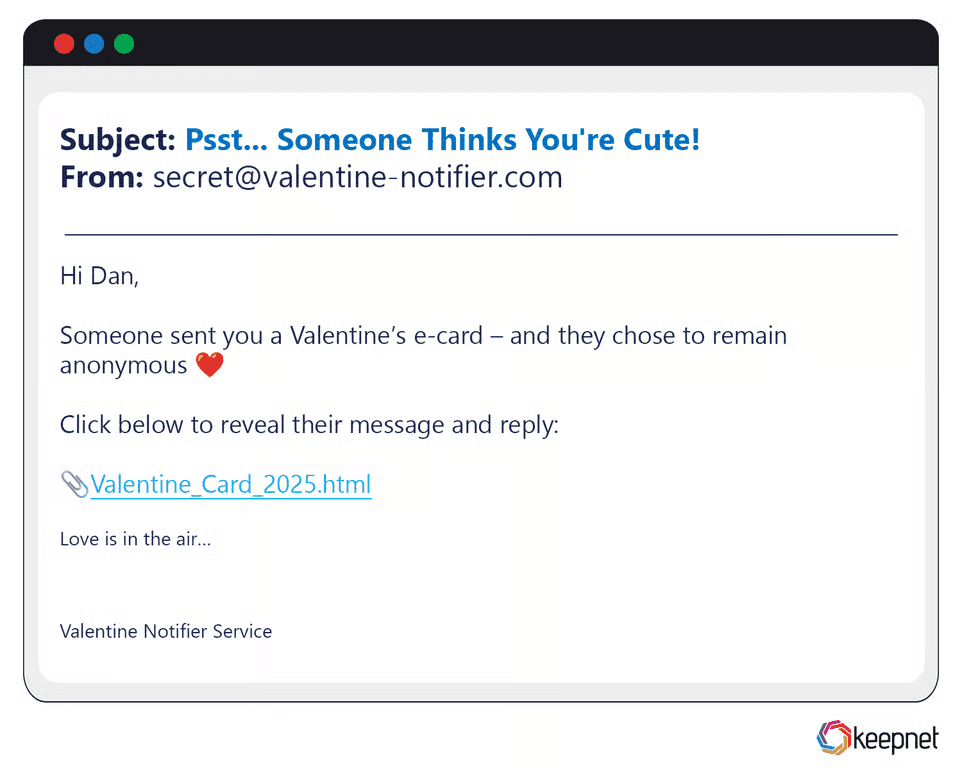
Attackers send “secret admirer e-cards” with malicious .HTML attachments or spoofed flower-delivery confirmations requiring payment updates. In 2025, a campaign targeting dating-app users pushed fake profile-view notifications, harvesting 50 000 passwords.
Black Friday Phishing Examples
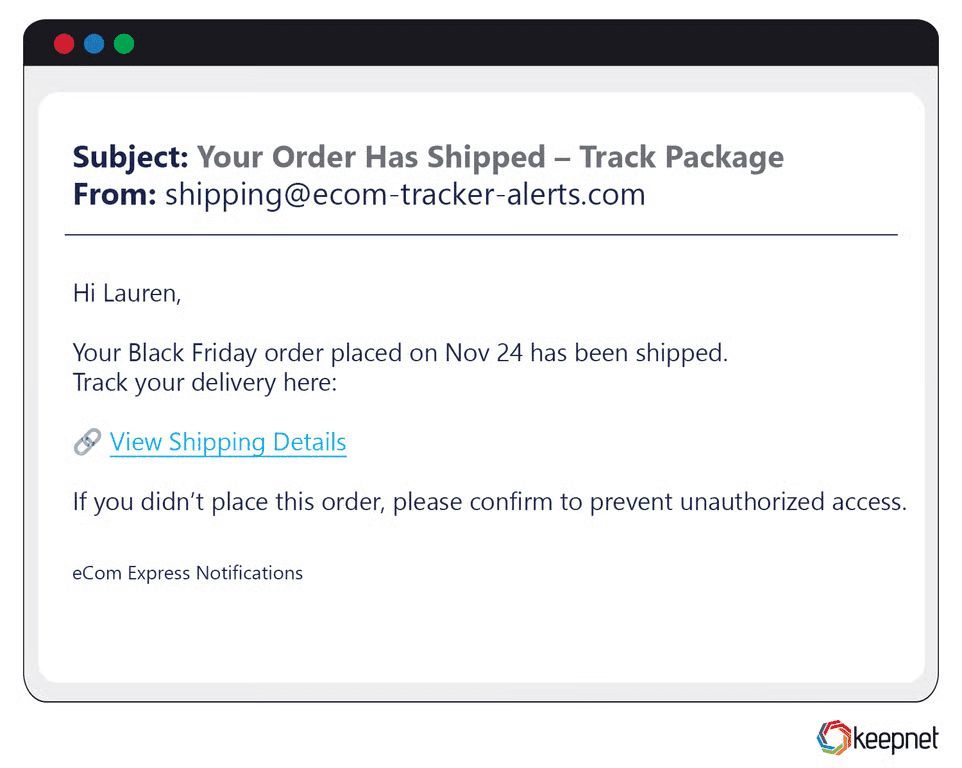
Countdown-timer emails boasting “95% OFF—Today Only!” redirected shoppers to cloned checkout pages for brands like Nike and Zara. SEO-bait subject lines—“black friday mega sale phishing email”, “cyber week coupon scam”—drove high open rates.
Cyber Monday Phishing Examples

Because remote workers shop on company devices, fraudsters blast Microsoft 365 users with fake “order error—re-authenticate” links. One SOC report showed a 3× jump in credential-harvest pages bearing “Cyber Monday deal” banners during the first 12 hours of the sale.
Christmas & New Year Related Phishing Attacks
Multi-language spear-phish emails mimic DHL, UPS, and local postal services, attaching bogus shipping labels seeded with Emotet. Another trend: “digital holiday card” downloads that sideload infostealers onto corporate laptops just before IT teams leave for vacation.
Easter Phishing Examples
E-commerce-style scams promise free chocolate hampers for taking a “short survey.” Links lead to data-skimming sites asking for name, address, and card number. Seasonal keywords: “Easter giveaway scam”, “spring sale phishing email.”
Halloween Related Phishing Attacks
Phony costume-store promotions embed JavaScript redirects to exploit kits. In 2024, a “Haunted House ticket” PDF attachment installed ransomware across a Midwest university when a student activities coordinator forwarded it internally.
Mapping phishing campaigns to the calendar lets security teams issue perfectly timed advisories—just before employees are most likely to face themed scams—while reinforcing zero-trust behaviors year-round.
Election Phishing Attack Examples
Election years see spikes in “voter registration confirmation email scam” and “campaign donation phishing”. One U.S. campaign cloned state-level election-board sites, requesting driver-license scans “to prevent voter suppression.” Meanwhile, in Nigeria’s 2023 election, SMS smishing offered “instant PVC verification,” harvesting personal data for identity theft.
Concert or Festival Ticket Phishing Examples
Phishers create cloned Ticketmaster checkouts, Instagram ads promising last-minute passes, or emails with malware-stuffed “print-at-home” PDFs. A 2025 “Coachella ticket lottery” scam netted 8000 card numbers in two days. Long-tail keywords exploited: “festival ticket phishing email”, “concert e-ticket malware attachment.”
Phishing Examples by Event
Phishing attacks are highly event-driven. Cybercriminals carefully monitor what people are talking about—taxes, elections, concerts, school starts—and time their scams to match the moment. By blending in with trusted communication around key events, attackers make phishing emails harder to detect and more likely to succeed.
Tax Season Phishing Attacks
Every tax season, phishing emails flood inboxes with subject lines like “Your tax refund is ready” or “Action required: IRS account issue.” Attackers often impersonate government tax authorities such as the IRS, HMRC, or Agencia Tributaria, attaching fake PDFs or linking to spoofed portals. One campaign in the U.S. used a fake W-2 download link to steal employee payroll data—leading to multiple identity theft cases.
Back-to-School Phishing Examples
Back-to-school time is a goldmine for cybercriminals targeting parents, students, and school staff. Common tactics include “new schedule notifications,” fake financial aid alerts, or phishing emails from fake university portals. One real case involved a phishing email to university students claiming their campus Wi-Fi password had expired. Clicking the link led to a fake login page that harvested credentials and spread malware internally.
Major Sporting Event Phishing Examples
From the FIFA World Cup to the Olympics, big sporting events create perfect cover for phishing attacks. Fraudsters craft emails offering last-minute ticket sales, exclusive livestreams, or VIP contest entries. In one high-profile case, attackers cloned UEFA’s branding to trick users into downloading malware disguised as an “official fan app.”
Election Phishing Examples
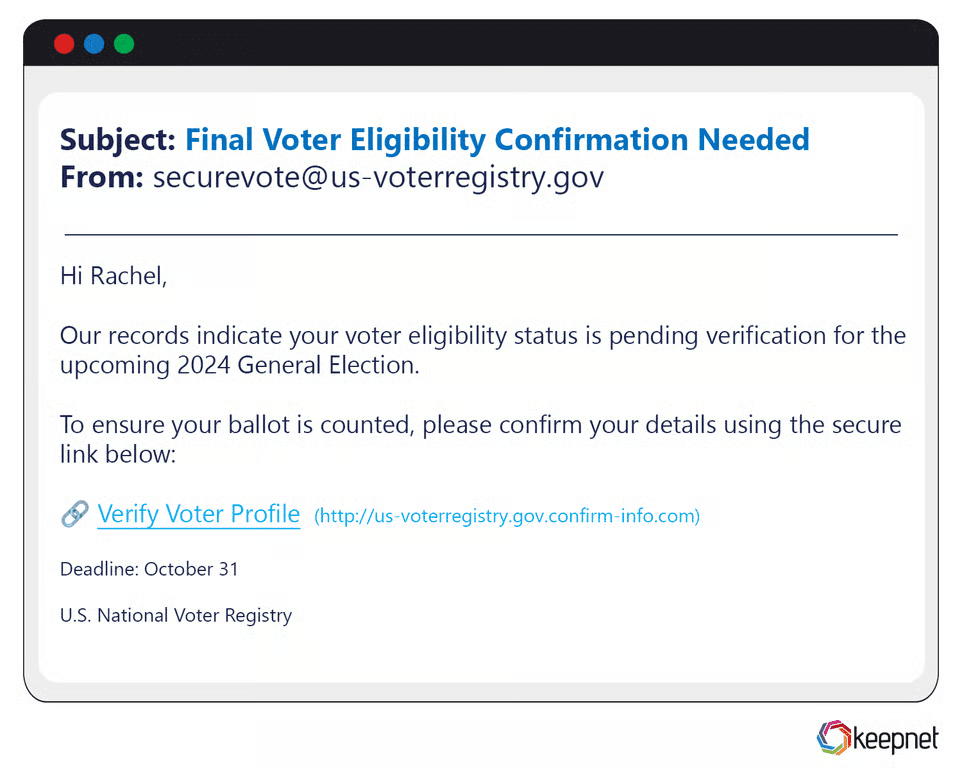
During election periods, attackers exploit voter interest and political tension. Common phishing campaigns mimic voter registration portals, absentee ballot forms, or fundraising emails from major candidates. In a recent U.S. campaign, voters received emails asking them to “confirm their voter ID” by uploading sensitive documents—used later for fraud and identity theft.
Concert or Festival Ticket Phishing Examples
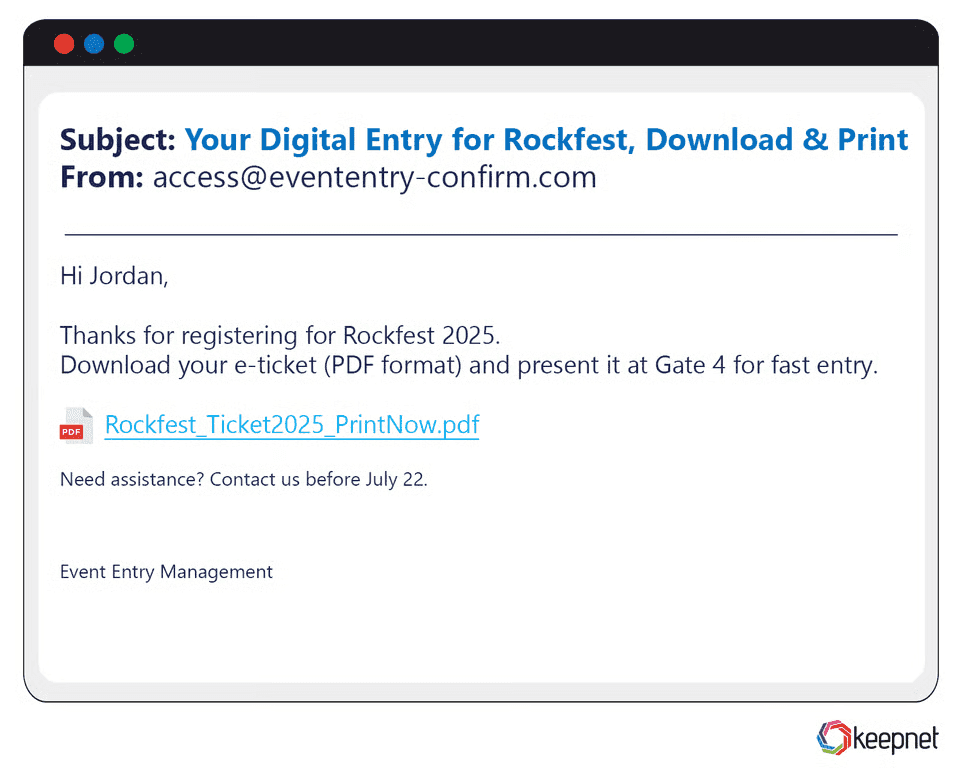
Scammers target music fans with fake ticket confirmations, bogus e-tickets, or spoofed ticketing sites that steal credit card info. A phishing campaign during Coachella sent out emails claiming, “Your weekend pass is ready—just confirm your payment.” The site looked exactly like Ticketmaster but funneled card data directly to attackers.
Phishing Examples by Shopping Seasons
Scammers love shopping seasons because people are in a rush, overwhelmed with emails, and more willing to click. They use discounts, urgency, and fake delivery notifications to trick even the savviest online shoppers.
Black Friday & Cyber Monday Phishing Examples
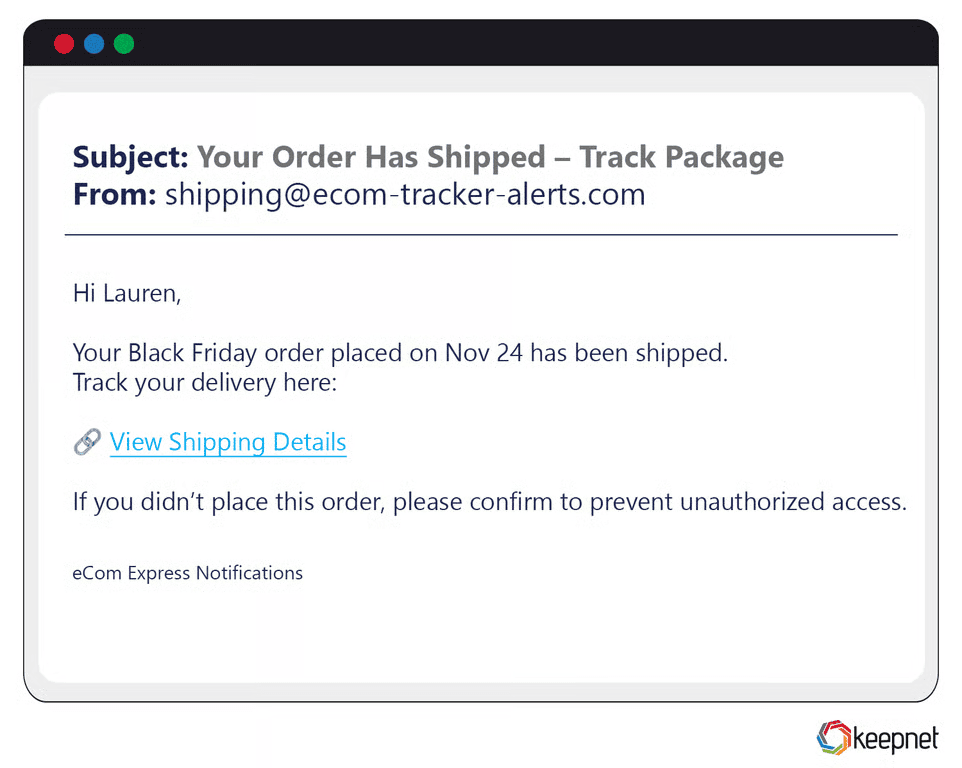

During Black Friday and Cyber Monday, attackers unleash massive campaigns impersonating top brands like Amazon, Walmart, and Target. One scam sent fake order confirmations with tracking links, which redirected users to credential-stealing pages. Another campaign mimicked “One-day 90% off” promo emails with zip attachments laced with ransomware.
Prime Day Phishing Examples
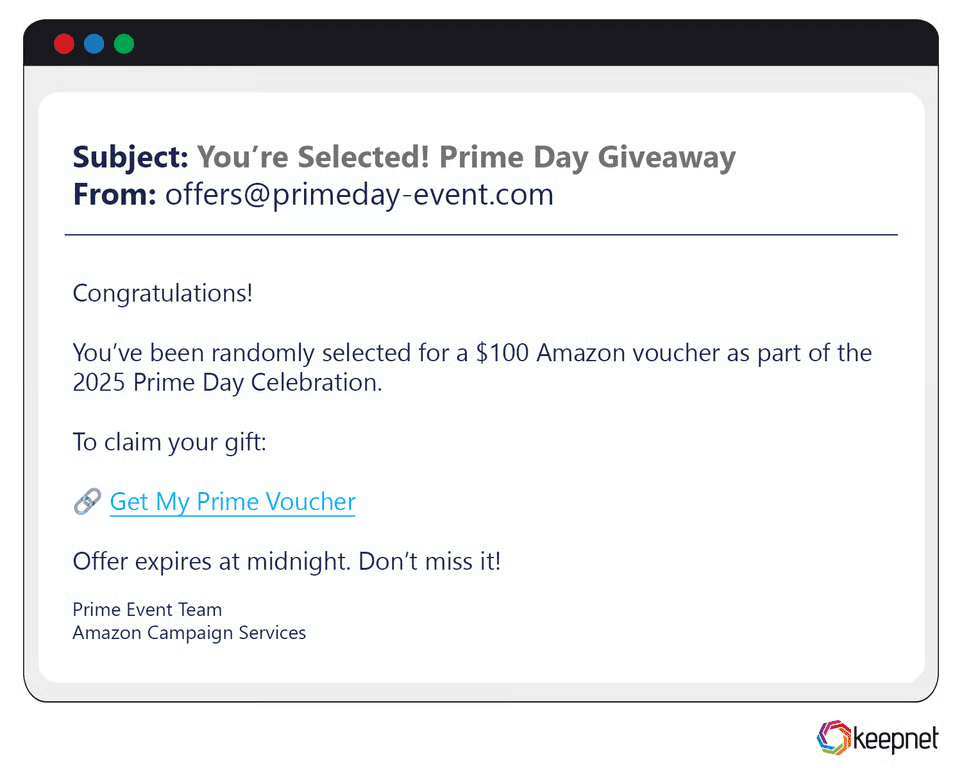
Amazon Prime Day brings a wave of phishing emails disguised as Prime order problems, payment failures, or Prime membership renewals. In one attack, users received emails saying “Your Prime order couldn’t be processed,” and were redirected to a convincing fake Amazon login page.
Seasonal Sales Phishing Attacks
Seasonal events like summer clearance, Eid sales, Boxing Day offers, and Singles’ Day are often mimicked in phishing emails. Cybercriminals use flashy subject lines like “Final 24 Hours: 80% Off Everything!” to lure clicks. One scam impersonated a popular clothing brand during the winter sales, leading victims to enter payment info on a cloned site.
Phishing Examples by Season
Phishing doesn't take a vacation, if anything, it adapts with the seasons. Here's how attacks evolve across the calendar year:
Winter Phishing Examples
Cold weather brings hot scams. Winter phishing campaigns often exploit holiday shipping updates, gift card offers, and heating bill payment reminders. In one case, attackers impersonated a local utility company during a snowstorm, asking customers to “avoid disconnection” by clicking a malicious payment link.
Spring Phishing Examples
Spring means tax deadlines, spring break, and online deals. Cybercriminals use subject lines like “Claim your spring bonus” or “Get your IRS refund now.” A phishing attack during spring 2024 targeted employees with emails offering “Easter cash-back rewards,” which led to fake bank login pages.
Summer Phishing Examples
During summer, vacation-themed scams thrive. Common attacks include fake hotel booking confirmations, flight cancellation alerts, or fake Airbnb refund emails. One phishing campaign even used fake sunscreen brand giveaways that directed victims to credential-harvesting sites.
Fall/Autumn Phishing Examples
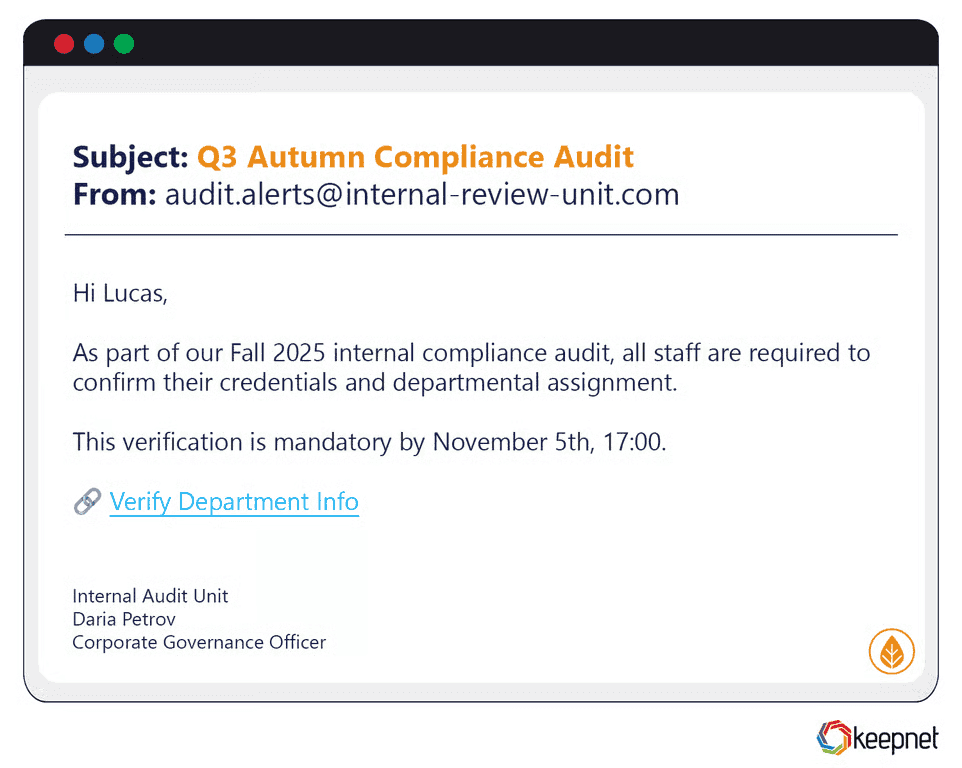
Fall campaigns focus on back-to-school, Halloween costumes, and early holiday shopping. One phishing email posed as a Halloween store offering “buy one, get two free,” but clicking led to a credential-stealing website. Another used fake invoices disguised as school supply orders.
Phishing Examples by Special Observance
Attackers love to hijack meaningful causes and awareness campaigns to build trust and urgency. These campaigns often appear genuine—until it's too late.
Earth Day Phishing Examples
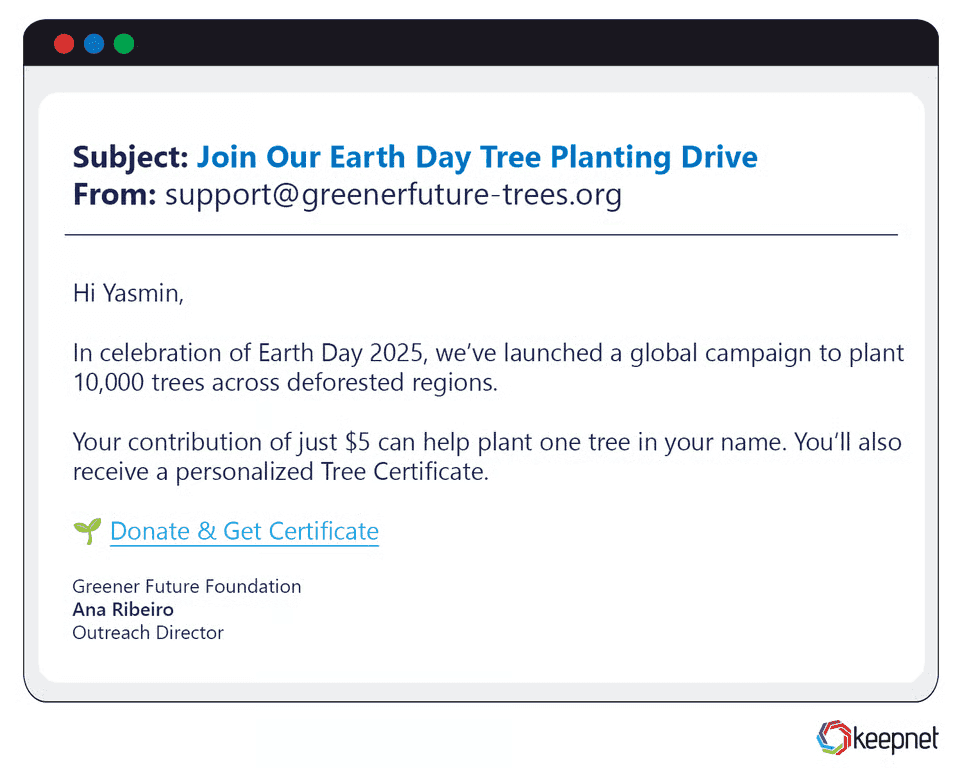
Scammers use Earth Day to push fake eco-campaigns, such as “Plant a tree with one click” or “Join our green donation drive.” These emails often contain links to data harvesting forms or malware-laced PDFs. One attack targeted corporate CSR departments with fake partnership proposals from made-up non-profits.
Cybersecurity Awareness Month Phishing Examples
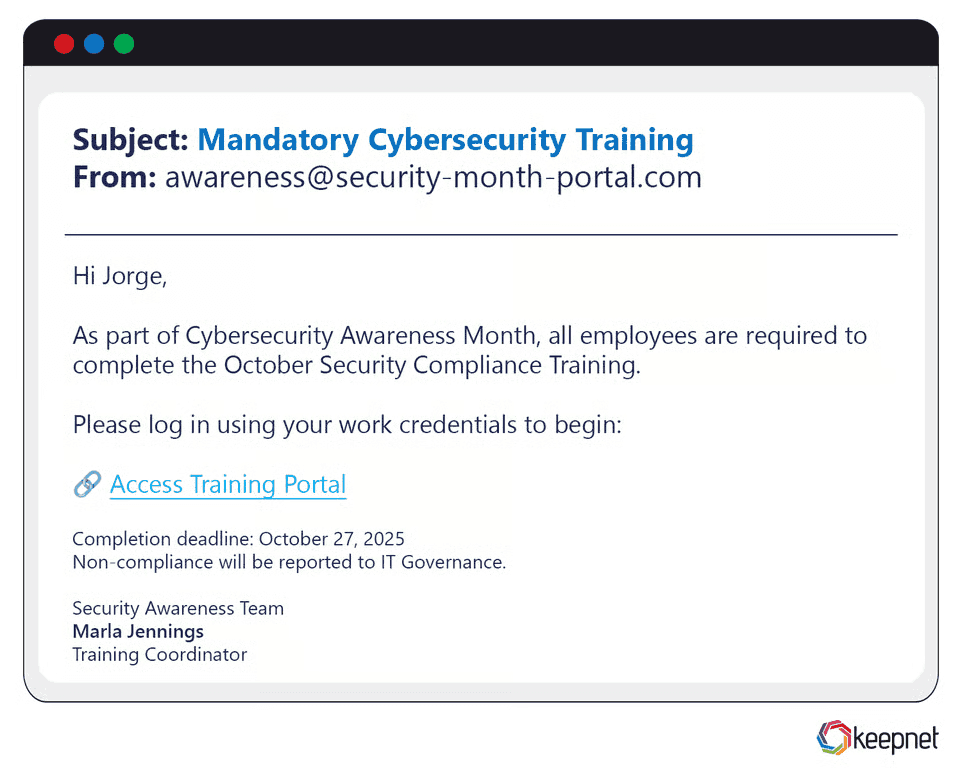
October’s Cybersecurity Awareness Month is ironically a busy time for phishing. Attackers send fake training invitations, spoofed LMS login links, or fake compliance deadlines. In one clever case, employees received an email saying “Complete your phishing simulation now”—but the email was the phish.
Awareness Campaign-Related Phishing Examples
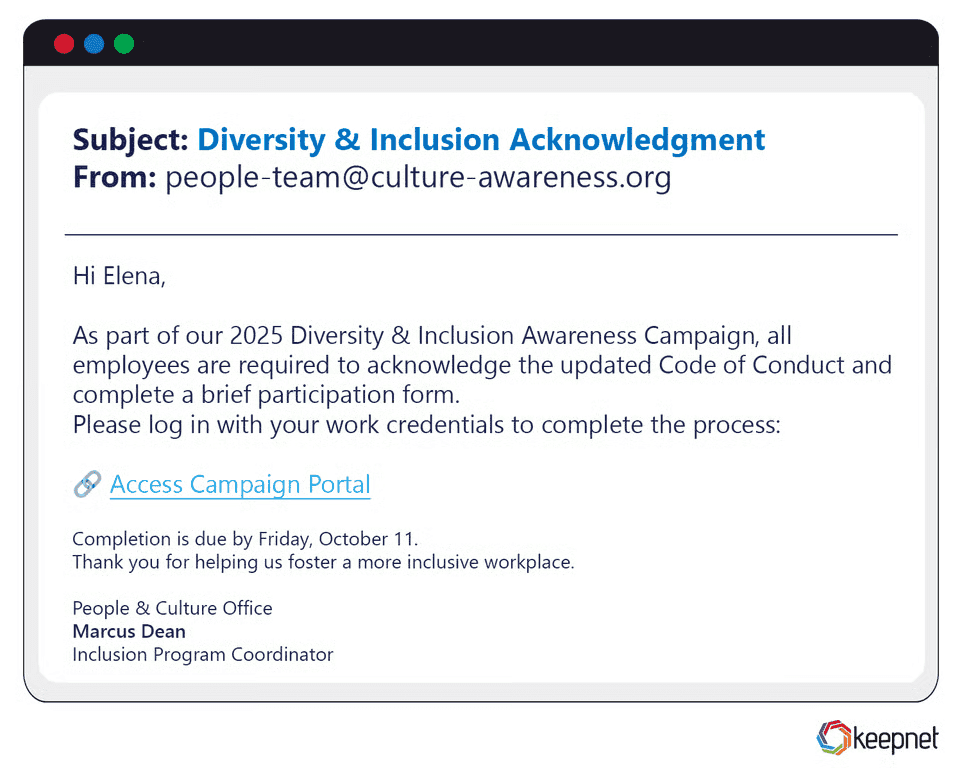
From Breast Cancer Awareness Month to Mental Health Week, scammers exploit empathy and social good. Common tactics include donation request emails, online store sales (“100% of proceeds go to charity”), or fake social media fundraisers. In a 2023 campaign, fraudsters created a fake breast cancer foundation website that stole donor payment information.
Editor's note: This blog post was updated on February 9, 2026.