Unmasking the Smishing Triad: A Deep Dive into the China-Based Cyber Fraud Network
Explore the latest Smishing Triad campaign analysis — how this China-linked cybercriminal network runs massive smishing operations, its global impact, recent evolution, economic scale, and practical defenses to protect individuals and organizations.
Smishing is now one of the fastest-growing cybercrime methods, and the Smishing Triad is one of the most dangerous networks behind it. Their operations span dozens of countries, thousands of fake domains, and billions in financial fraud.
What Is the Smishing Triad? (Quick Definition)
The Smishing Triad is a China-linked cybercriminal network that runs large-scale SMS phishing (smishing) campaigns worldwide. These attacks impersonate trusted brands to steal personal data, banking credentials, and one-time passcodes through fake mobile websites.
Origin and Modus Operandi of Smishing Triad
Diving deeper into the origins and workings of the Smishing Triad, it becomes evident that this group has meticulously crafted a unique and effective approach to cybercrime. Originating from China, the group has carved a niche in cyber threats, leveraging innovative techniques and exploiting vulnerabilities to further its malicious agenda.
Smishing allows the group to cast a wide net, reaching many potential victims and increasing the chances of successful attacks. The messages often contain urgent calls to action, prompting recipients to click on malicious links or provide personal details, ultimately leading to identity theft and financial loss.
What distinguishes the Smishing Triad from other cyber-criminal entities is their exclusive utilization of iMessage as a medium for disseminating scams. This platform, associated with Apple devices, is generally perceived as secure, adding more credibility to the group’s deceptive messages.
The group’s ingenuity doesn’t stop there; they have managed to compromise Apple iCloud accounts, enabling them to send iMessages that appear legitimate and bypassing the usual security protocols. This compromise of iCloud accounts amplifies the reach of their smishing campaigns and poses a significant challenge for cybersecurity experts aiming to curb their activities.
The Smishing Triad’s adeptness at exploiting technological vulnerabilities and its innovative approach to smishing demonstrate high sophistication and adaptability. Their ability to infiltrate secure communication channels like iMessage and compromise iCloud accounts highlights the evolving nature of cyber threats and the necessity for continuous advancements in cybersecurity measures.
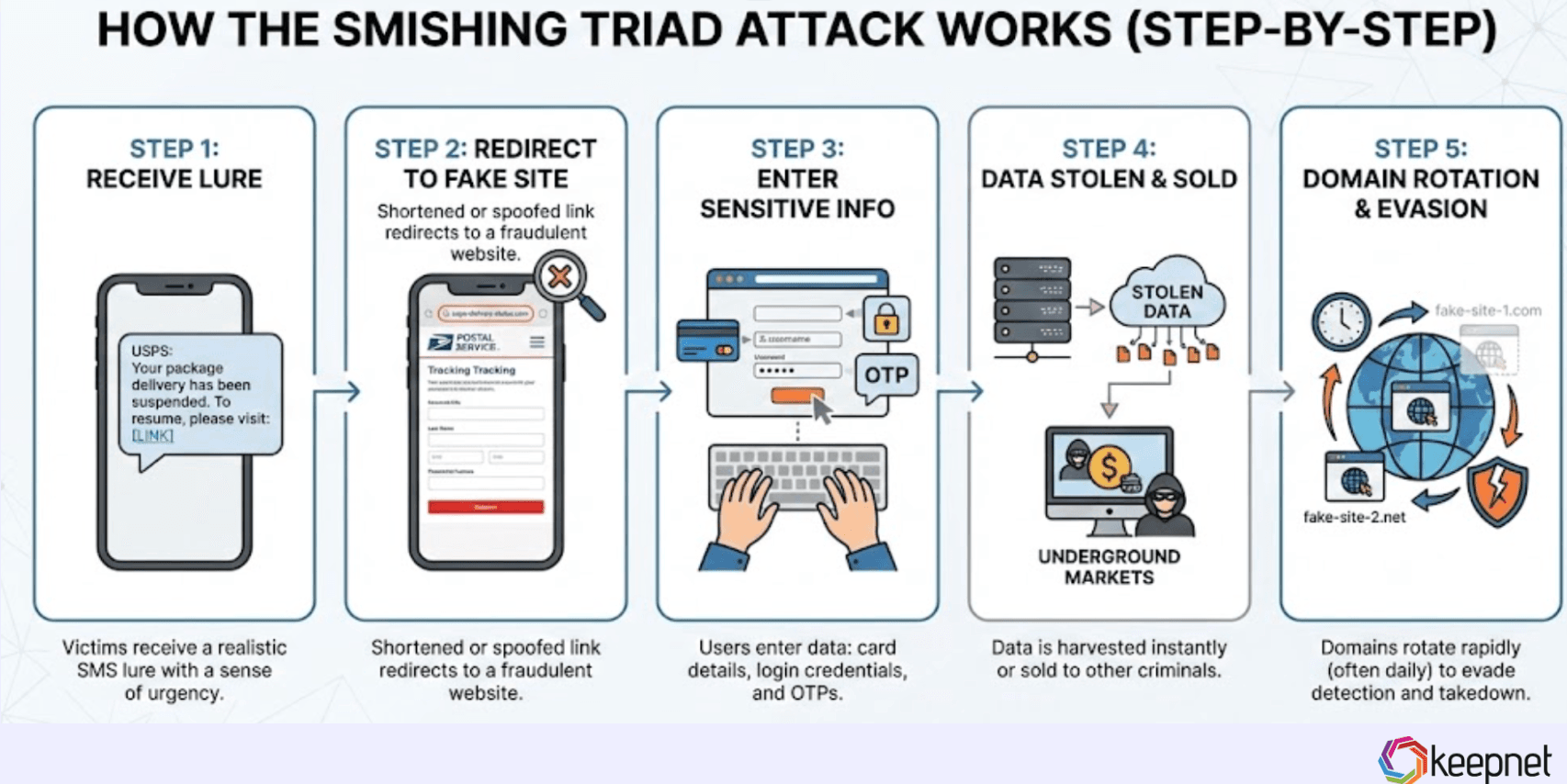
How the Smishing Triad Attack Works (Step-by-Step)
Smishing Triad campaigns follow a repeatable fraud pipeline:
- Victims receive a realistic SMS lure
- A shortened or spoofed link redirects to a fake site
- Users enter sensitive information (card data, login, OTP)
- Data is stolen instantly or sold on underground markets
- Domains rotate rapidly to evade takedown efforts
With its roots in China, the Smishing Triad has emerged as a formidable player in the cybercrime landscape. Their specialized use of smishing, coupled with their exploitation of iMessage and iCloud accounts, underscores the multifaceted nature of their operations and the pressing need for heightened awareness and robust security solutions to counteract such threats.
Real Smishing Triad Text Message Examples
Smishing Triad messages often use urgency and fear. Common lures include:
- “Your package is awaiting delivery. Confirm your address now.”
- “Unpaid toll fee detected. Pay immediately to avoid penalties.”
- “Bank security alert: Verify your account within 30 minutes.”
- “Your mobile payment has been suspended. Reactivate now.”
Check our guide, to see more Smishing examples.
Impersonation and Targets of Smishing Triad
In their pursuit of illicit gains, the Smishing Triad has demonstrated a remarkable ability to impersonate a wide array of postal and delivery services across the globe. This impersonation tactic is a cornerstone of their strategy, enabling them to gain the trust of unsuspecting individuals and thereby facilitate their fraudulent activities.
| Capability | What to check |
|---|---|
| Global Brand Impersonation (Postal & Delivery) | Smishing Triad frequently impersonates trusted postal and delivery brands to exploit user trust and drive clicks to fake tracking/payment pages. |
| Commonly Impersonated Services | Watch for lures referencing major carriers such as Royal Mail (UK), USPS (US), Correos (Spain), PostNord (Sweden), Poste Italiane (Italy), Poczta Polska (Poland), J&T Express (Indonesia), and New Zealand Post. |
| High-Trust Messaging Strategy | Messages create urgency using delivery failures, pending packages, address confirmation, or small fee/payment prompts to increase click-through rates. |
| Expansion to E-commerce Targets | Beyond logistics brands, campaigns also target online shopping and e-commerce ecosystems to reach high-volume consumer transactions. |
| Web Injection / Malicious Code Attempts | Some operations attempt to inject malicious code into online shopping sites (or compromise third-party scripts) to intercept customer transaction data. |
| Data Interception During Checkout | Look for signs of credential theft, payment card skimming, session hijacking, and exfiltration of personal data during login or checkout flows. |
| Stolen Data Monetization | Collected credentials and card data may be used for account takeover, identity theft, fraudulent purchases, and resale on underground markets. |
| Business Impact and Risk Scope | Impersonation increases customer support load, reputational damage, fraud losses, and regulatory exposure—especially for retail, logistics, and payment-heavy sectors. |
Impersonation and Targets of Smishing Triad
The multifaceted impersonation tactics and targeting strategies employed by the Smishing Triad reveal the depth of their operations and the potential risks posed to individuals and businesses worldwide. The need for vigilance, enhanced security measures, and consumer awareness has never been more critical in the face of such sophisticated and evolving cyber threats.
Fraud-as-a-Service Network
Delving further into the intricate web woven by the Smishing Triad, we uncover a sophisticated Fraud-as-a-Service Network that is the backbone of their expansive operations. This network is a testament to the group’s entrepreneurial spirit in cybercrime and a glaring indication of the multifaceted nature of modern digital threats.
| Capability | What to check |
|---|---|
| Smishing Kits Sold on Telegram | Smishing toolkits are advertised and distributed in encrypted Telegram groups, enabling low-skill actors to launch SMS phishing campaigns. |
| Pre-Built Scripts & Activation Codes | Kits include message templates, scam scripts, and activation mechanisms that streamline setup and execution of smishing campaigns. |
| Cybercriminal Collaboration Ecosystem | The network collaborates with other threat actors to share tactics, infrastructure, and resources, increasing attack sophistication and reach. |
| Cybercrime-as-a-Service Infrastructure | Infrastructure supports broader criminal services (e.g., phishing platforms and stolen data markets) that make cybercrime easier to scale. |
| Subscription-Based Business Model | Smishing kits are sold via tiered subscriptions, turning fraud operations into repeatable, commercial-style services. |
| Low Barrier to Entry | Entry pricing (reported around $200/month) lowers the barrier for new criminals and accelerates the spread of smishing operations. |
| Commodification of Smishing Attacks | Fraud is packaged as a service, allowing rapid replication of attacks and consistent monetization across regions and industries. |
| Expanded Global Threat Impact | This model increases attack volume and geographic reach, raising risk for consumers, enterprises, banks, and public-sector organizations. |
Fraud-as-a-Service Network (Smishing Triad Overview)
The Smishing Triad’s establishment of a Fraud-as-a-Service Network, their collaboration with other cyber entities, and the provision of cybercrime-as-a-service infrastructure underscore the depth and complexity of their operations. The sale of smishing kits and the detailed pricing structure further illuminate the group’s strategic approach to expanding its reach and influence in the cybercriminal landscape. The revelations about this network serve as a stark reminder of the evolving nature of cyber threats and the imperative for continuous advancements in cybersecurity measures.
Key Statistics on the Smishing Triad

Here is a compilation of 20 statistics about the Smishing Triad, a China-linked cybercrime group known for large-scale SMS phishing campaigns. These are drawn from various cybersecurity reports and analyses as of early 2026.
- The Smishing Triad has been linked to over 194,000 malicious domains used in global phishing operations since January 1, 2024.
- The group has earned more than $1 billion through scams over the last three years.
- Approximately 195,000 domains have been traced to the Smishing Triad since January 2024.
- The operation involves thousands of malicious actors, including dozens of active, high-level participants.
- The Smishing Triad has been active since at least 2023, with criminal affiliate partners operating in multiple countries.
- Their campaigns have targeted at least 121 countries and numerous industries.
- The group sends up to 100,000 smishing texts daily.
- Portions of their infrastructure generated over 1,000,000 phishing page visits within a 20-day period.
- In January 2024, a USPS smishing campaign targeted over 180,000 U.S. residents.
- Approximately 25,000 phishing domains are active during any 8-day period.
- Smishing campaigns maintain an average success rate of approximately 5%.
- Some domains receive over 500 visits per week.
- One identified threat actor can send up to 2,000,000 smishing messages daily.
- The group could potentially target up to 60,000,000 victims per month or 720,000,000 per year.
- Around 200,000 domains have been used by the group in recent years.
- The crime group has amassed more than 1 million victims across 120 countries.
- They have stolen between 12.7 million and 115 million credit cards in the U.S. alone.
- Roughly 90,000 fraudulent domains impersonated toll services, and over 28,000 impersonated the US Postal Service.
- From January 1, 2024, to June 2025, 136,933 root domains were registered by the Smishing Triad, totaling 194,345 fully qualified domain names.
Read our guide to learn key Smishing statistics in 2026.
Challenges in Combating Smishing Triad
Addressing the challenges in combating cybercrime, particularly those posed by groups like the Smishing Triad, unveils a complex landscape marked by jurisdictional hurdles and the need for international cooperation. The transnational nature of such cyber threats necessitates a unified approach, where difficulties in disrupting activities by actors in foreign jurisdictions are addressed through regulatory harmonization and mutual legal assistance.
One of the primary challenges in combating the Smishing Triad activities stems from their origin in China. The geographical and jurisdictional boundaries present significant obstacles in pursuing and disrupting the operations of such foreign-based cyber-criminal entities. The differences in legal frameworks, enforcement mechanisms, and the availability of resources across countries can impede timely and effective responses to emerging threats.
The Smishing Triad’s ability to operate across borders, exploiting vulnerabilities and targeting victims worldwide, highlights the need for a cohesive and harmonized international approach to cybersecurity. Regulatory harmonization is pivotal in establishing common standards and protocols for addressing cybercrime, thereby facilitating cooperation and information sharing among nations. A harmonized regulatory environment can foster a more conducive atmosphere for joint efforts in investigating and combating cyber threats, regardless of their origin.
Equally important is the establishment of mutual legal assistance agreements abroad. Such agreements are instrumental in enabling cross-border collaboration and support in legal matters related to cybercrime. They provide a framework for extradition, evidence sharing, and joint investigations, thereby enhancing the capacity of nations to respond to and mitigate the impact of transnational cyber-criminal activities.
The challenges the Smishing Triad and similar entities pose underscore the urgency of addressing the gaps in international cybersecurity frameworks. The importance of overcoming jurisdictional barriers, fostering regulatory harmonization, and establishing mutual legal assistance cannot be overstated. These elements are foundational in building a resilient and united front against the ever-evolving and increasingly sophisticated landscape of cyber threats.
The journey to combatting cybercrime is fraught with challenges, but the path forward is clear. The international community must come together, transcending boundaries and differences, to forge a united and robust defense against the activities of groups like the Smishing Triad. Pursuing regulatory harmonization and mutual legal assistance abroad is a necessity and a cornerstone in safeguarding the digital realm against the multifaceted challenges of the modern cybercrime era.
How to Protect Against Smishing Triad Attacks
To reduce smishing risk, organizations should implement layered defenses:
- Security awareness training focused on mobile phishing
- Smishing simulations to test real employee behavior
- Mobile threat detection and SMS filtering
- Incident reporting workflows for suspicious texts
- Role-based microlearning for high-risk teams (finance, HR, IT support)
Final Thoughts: Smishing Triad Shows Why Mobile Phishing Is the Next Major Threat
The Smishing Triad represents the industrialization of SMS phishing—global, scalable, and extremely profitable.
Organizations must move beyond awareness posters and adopt modern Human Risk Management strategies that include:
- Smishing Simulation
- Behavioral Microlearning
- Real-Time Risk Analytics
- Multi-channel phishing defense
Keepnet helps enterprises stop smishing, vishing, quishing, and AI-driven phishing attacks through the Human Risk Management Platform.
Explore Smishing Simulator Further
Are you ready to fortify your organization’s defenses against smishing attacks? We invite you to explore the capabilities of our Smishing Simulator in more detail. Request a demo or sign up for a free trial on our website to experience how our solution can empower your business to stay ahead of evolving cyber threats. Don’t miss the opportunity to safeguard your organization and build a resilient cybersecurity culture with Keepnet’s innovative solutions.
Editor's Note: This blog was updated on February 9, 2026.