Vulnerability Management: How to Find, Prioritize, and Fix Security Flaws (The Practical Guide)
Vulnerability management is a continuous loop: discover assets, scan for flaws, prioritize what’s exploitable and exposed, remediate fast, and verify. This guide shows a workflow using CISA KEV, CVSS, and EPSS—plus KPIs and checklists. Now.
Vulnerability management is an ongoing program that discovers vulnerabilities, prioritizes them by real risk, remediates or mitigates, and verifies the fix—then repeats continuously. Done well, it turns ‘endless scanner findings’ into measurable risk reduction — and complements a broader human risk management program.
What vulnerability management is (and what it isn’t)
Vulnerability management is the practice of monitoring and scanning for vulnerabilities, analyzing results, and remediating legitimate vulnerabilities within defined response times, then sharing what you learn so the same weaknesses don’t repeat.
Not the same as a vulnerability assessment or a pentest
- Assessment: a point-in-time snapshot (useful, but it expires fast).
- Pentest: depth over breadth; proves impact on a subset.
- Vulnerability management: a continuous operating process that keeps your environment “patch-current, configuration-tight, and exploit-aware.”
The vulnerability management “alphabet soup” (CVE, NVD, CVSS, EPSS, KEV)
If you work in vulnerability management, you’ll see the same acronyms everywhere—and they often get mixed up. Here’s the clean, practical way to understand the ecosystem.
CVE = the identifier (the “name” of the vulnerability)
CVE (Common Vulnerabilities and Exposures) exists so the security world can talk about the same vulnerability using a single shared ID (for example, CVE-2025-12345). The CVE Program’s mission is to identify, define, and catalog publicly disclosed vulnerabilities, with one CVE Record per vulnerability.
NVD = enrichment + automation data (the “details hub”)
NVD (NIST National Vulnerability Database) is the U.S. government repository that takes CVEs and adds standards-based vulnerability management data designed to support automation. NVD includes things like affected product details, security checklist references, and impact metrics that tools and workflows can consume at scale.
CVSS = the severity framework (the “how bad is it?” score)
CVSS (Common Vulnerability Scoring System) is an open framework for describing vulnerability characteristics and severity in a consistent way. In CVSS v4.0, the metrics are organized into four groups: Base, Threat, Environmental, and Supplemental—so you can express both intrinsic technical severity and context that changes across environments.
EPSS = the likelihood signal (the “how likely is it to be exploited soon?” probability)
EPSS (Exploit Prediction Scoring System) provides a data-driven probability estimate that a vulnerability will be exploited “in the wild” in the next 30 days. It’s designed to help defenders prioritize remediation based on likelihood, not just theoretical severity. EPSS v4 was released on March 17, 2025.
KEV = the “exploited in the wild” shortlist (the “drop everything” list)
KEV (CISA Known Exploited Vulnerabilities Catalog) is CISA’s maintained list of vulnerabilities that are known to be exploited in the wild—a high-confidence signal for prioritization. CISA publishes the catalog in accessible formats (including CSV and JSON), and also provides a GitHub mirror to make consumption easier for defenders and developers.
The vulnerability management lifecycle (a workflow that actually scales)
Here’s the lifecycle that high-performing teams run weekly/daily—without drowning:
1) Build your asset inventory (or scanning will lie)
You can’t manage vulnerabilities on assets you don’t know exist: cloud instances, SaaS admins, VPN gateways, containers, endpoints, shadow IT.
Output: a living asset inventory with owners, criticality, and exposure tags (internet-facing vs internal). Ownership matters here — it’s the same principle used in Human Risk Management Platform to assign accountability and reduce repeat risk.
2) Discover and monitor vulnerabilities continuously
NIST-style guidance emphasizes monitoring/scanning and updating tools as new vulnerabilities emerge.
Coverage checklist
- External attack surface (internet-facing)
- Internal networks
- Endpoints
- Cloud configs + images
- Web apps / APIs
- Identity & misconfigurations (often more exploitable than missing patches)
3) Triage findings (kill noise fast)
Before you prioritize, remove “fake urgency”:
- False positives
- Out-of-scope assets
- Findings already mitigated by compensating controls
- Duplicates caused by multiple scanners
Rule: if your backlog is mostly noise, your program becomes theatre.
4) Prioritize using a risk formula (not just CVSS)
The NIST RA-5 control statement explicitly calls for scanning, analyzing results, and remediating based on risk and response times.
A practical prioritization model that works:
Risk Priority = Exploit Signal × Exposure × Business Impact
Exploit signal (highest weight)
- In KEV (known exploited) → top priority.
- High EPSS (higher probability in next 30 days) → next.
To reduce risk beyond technical exploits, run phishing simulation and security awareness training software in parallel — attackers often choose the easiest path.
Exposure
- Internet-facing, VPN, email/security gateways, identity systems, remote management
Business impact
- Crown-jewel systems, regulated data, revenue paths, production uptime
Where CVSS fits
CVSS is still useful—especially when combined with Threat/Environmental metrics—but don’t let “10.0 everywhere” hijack your roadmap.
5) Remediate or mitigate (and be honest about the difference)
Remediation = remove the vulnerability (patch, upgrade, config fix, code fix).
Mitigation = reduce exploitability/impact (WAF rule, disable feature, segmentation, hardening) when patching isn’t immediate.
Patch management is a core part of this: enterprise patch management includes identifying, prioritizing, acquiring, installing, and verifying patches across the organization.
6) Verify the fix (and prevent regression)
Verification is where mature teams separate themselves:
- Rescan the asset
- Confirm version/config state
- Watch for drift (especially in cloud/IaC)
7) Report and improve (make it measurable)
If leadership can’t see progress, the program loses funding. If engineers can’t see impact, it loses adoption.
Prioritization playbook: the “3 queues” method (simple, fast, effective)
Queue 1: “Must fix now”
- Any vulnerability on CISA KEV affecting your environment
- Actively exploited vulnerabilities from threat intel / incident response findings
Queue 2: “Likely to be exploited”
- High EPSS items on exposed or critical assets (probability focus)
Queue 3: “Engineering hygiene”
Everything else, prioritized by business context + CVSS severity framework.
This approach prevents the classic failure mode: teams spending weeks patching “high CVSS” issues that aren’t being exploited while attackers use yesterday’s KEV entry to break in.
Vulnerability management best practices
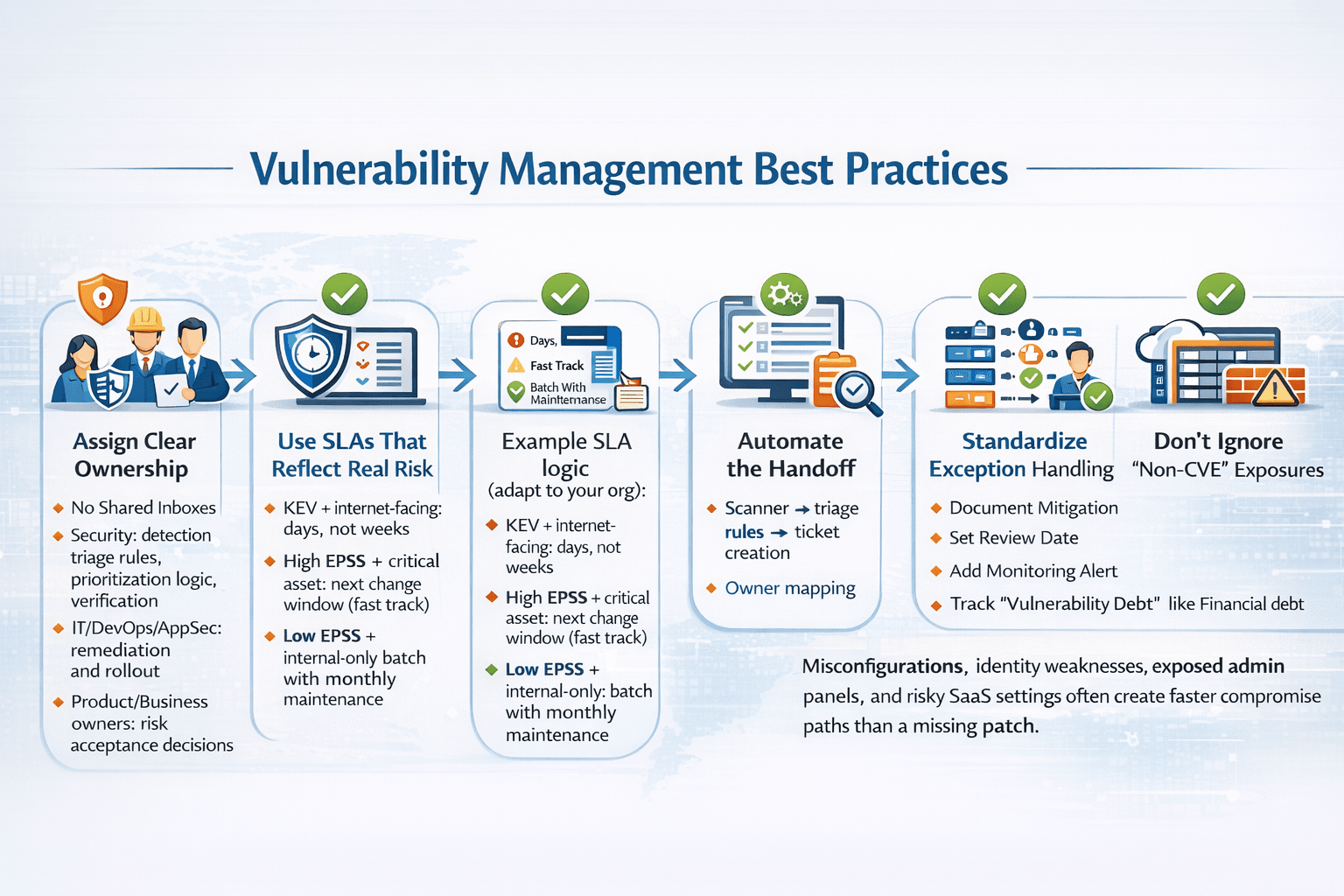
Assign clear ownership (no shared inboxes)
- Security: detection, triage rules, prioritization logic, verification
- IT/DevOps/AppSec: remediation and rollout
- Product/Business owners: risk acceptance decisions
Use SLAs that reflect real risk
Example SLA logic (adapt to your org):
- KEV + internet-facing: days, not weeks
- High EPSS + critical asset: next change window (fast track)
- Low EPSS + internal-only: batch with monthly maintenance
Automate the handoff
Scanner → triage rules → ticket creation → owner mapping → verification scan → closure.
Standardize exception handling
If something can’t be patched:
- Document mitigation
- Set review date
- Add monitoring alert
- Track “vulnerability debt” like financial debt
Don’t ignore “non-CVE” exposures
Misconfigurations, identity weaknesses, exposed admin panels, and risky SaaS settings often create faster compromise paths than a missing patch.
KPIs that prove your program works (and survive executive questions)
Use metrics that show risk reduction, not just activity.
Core KPIs
- Coverage: % of assets scanned (by environment type)
- MTTR: mean time to remediate (by severity and by KEV/EPSS tier)
- SLA compliance: % closed within policy windows
- Backlog health: total open findings + aging distribution
- Reopen rate: fixes that reappear (drift/rollback indicator)
Because NVD explicitly supports automation of vulnerability management, it’s reasonable to align your reporting pipeline to standardized data (CVE/NVD/CVSS/EPSS/KEV) so your KPIs remain consistent across tools.
Tooling checklist (buy/build decisions without brand bias)
Look for:
- Strong asset discovery (cloud + on-prem + external)
- Low false positives + good evidence
- Integrations (ticketing, CI/CD, EDR)
- Support for standardized vulnerability identifiers and scoring (CVE/NVD/CVSS/EPSS, plus KEV feeds)
- Reporting that matches your KPIs and SLAs
Conclusion: vulnerability management that actually reduces breach risk
The best vulnerability management programs are exploit-informed (KEV), likelihood-aware (EPSS), and context-driven (asset criticality + exposure)—with patch management discipline and verification baked in.
If you want to extend risk reduction beyond technical flaws, pair your vulnerability management program with behavior-focused defenses that reduce human-enabled compromise paths (phishing, vishing, MFA fatigue). Keepnet Human Risk Management Platform helps security teams reduce the human attack surface alongside technical remediation.