What Is Human Risk Management in Cybersecurity? Definition & Benefits
Human Risk Management replaces “train everyone” with “measure behavior, score risk, and intervene.” Learn HRM metrics and quick wins—nudges, simulations, role-based microlearning—to cut phishing, vishing, MFA fatigue, and deepfake fraud.
Human Risk Management (HRM) is a cybersecurity approach that measures, prioritizes, and reduces risk created by human behavior—the clicks, approvals, shares, workarounds, and “just this once” decisions attackers love.
If you’ve ever wondered why your awareness program feels busy but your incidents keep happening, HRM is the missing piece: it turns “people risk” into measurable, manageable cyber risk.
“Human Risk Management isn’t another training checkbox. An HRM is a strategy to turn the human element into a defense layer. With an agentic human risk management platform, phishing simulations, and just-in-time security awareness training, we move from dashboards to measurable behavior change and a strong security culture.”
Human Risk Management definition
Human Risk Management (HRM) is the practice of detecting and measuring human security behaviors, quantifying human cyber risk, and triggering targeted interventions (training, nudges, policy and process changes) to reduce that risk.
In other words: HRM is risk management for people, not a once-a-year training exercise.
Key takeaways
HRM becomes easy to understand when you remember these four rules.
- HRM is not “more awareness training”: HRM uses behavior signals + analytics to focus action where it matters most.
- HRM is continuous: It measures behavior over time and closes the loop with interventions and outcomes.
- HRM is role-based: Finance, HR, IT help desk, executives, customer support—each faces different attack patterns.
- HRM is outcome-driven: It proves impact with metrics leadership actually trusts.
Why Human Risk Management matters now
The “human element” is not a soft topic anymore—it’s a hard statistic.
Verizon’s 2025 DBIR notes that human element involvement in breaches hovered around ~60%, roughly the same as the prior year.
That’s why organizations are moving beyond generic education toward measurable behavior change.
And the threat mix is getting more convincing. Gartner reports that 62% of organizations experienced at least one deepfake attack in the last 12 months (in a Gartner cybersecurity leaders survey), often involving social engineering or automated processes.
HRM exists for one practical reason:
Your biggest exposure is often the moment a person decides. HRM helps you influence that moment—using data.
Human Risk Management vs. Human Resource Management (HRM)
Yes, the acronym is confusing.
Human Resource Management = HR discipline (hiring, payroll, performance).
Human Risk Management (in cybersecurity) = reducing cyber risk created by human behavior using measurement + targeted interventions.
This page is about the second one.
Human Risk Management vs. Security Awareness Training
Security Awareness Training (SAT) is often a component inside HRM—but it’s not the full program.

Security Awareness Training (SAT)
SAT focuses on knowledge and compliance: courses, videos, quizzes, completion rates. That matters, but it can become “checkbox training” if it isn’t connected to risk signals and outcomes.
Human Risk Management (HRM)
HRM asks better questions:
- Who is most exposed (roles + workflows)?
- Who is repeatedly risky (patterns over time)?
- What intervention works for this group?
- Did risk actually go down?
Forrester’s HRM definition explicitly emphasizes measuring behavior and quantifying risk, then initiating policy/training interventions based on that risk
Quick Comparison
HRM and SAT look similar on the surface, but they behave differently in practice.
| Topic | Traditional SAT | Human Risk Management (HRM) |
|---|---|---|
| Goal | Completion + awareness | Measurable risk reduction |
| Targeting | Everyone, same content | Segmented by role + behavior |
| Timing | Calendar-based | Triggered “in the flow of work” |
| KPI | Completion rate | Risk trend, repeat risk, reporting speed |
| Outcome | Knowledge | Behavior change + fewer incidents |
Traditional SAT vs Human Risk Management (HRM)
Human Risk Management vs. Insider Risk Management
Insider Risk programs typically focus on data access misuse, malicious insiders, leakage, and policy enforcement.
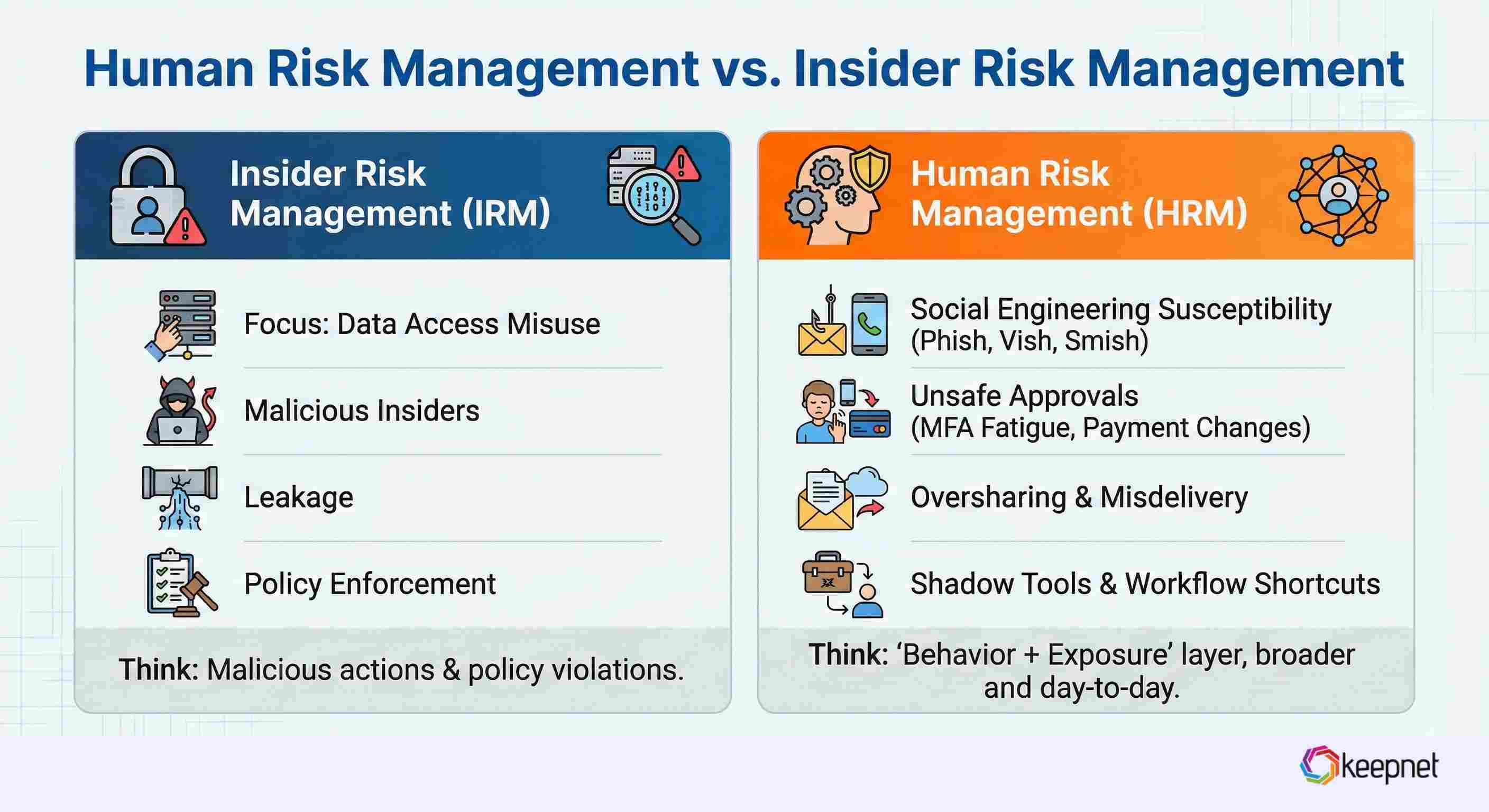
Human Risk Management is broader and more “day-to-day”:
- social engineering susceptibility (phish, vish, smish)
- unsafe approvals (MFA fatigue, payment changes)
- oversharing and misdelivery
- shadow tools and workflow shortcuts
Think of HRM as the “behavior + exposure” layer that complements your technical controls.
How Human Risk Management works
A good HRM program is simple, repeatable, and measurable. It usually follows a closed loop:
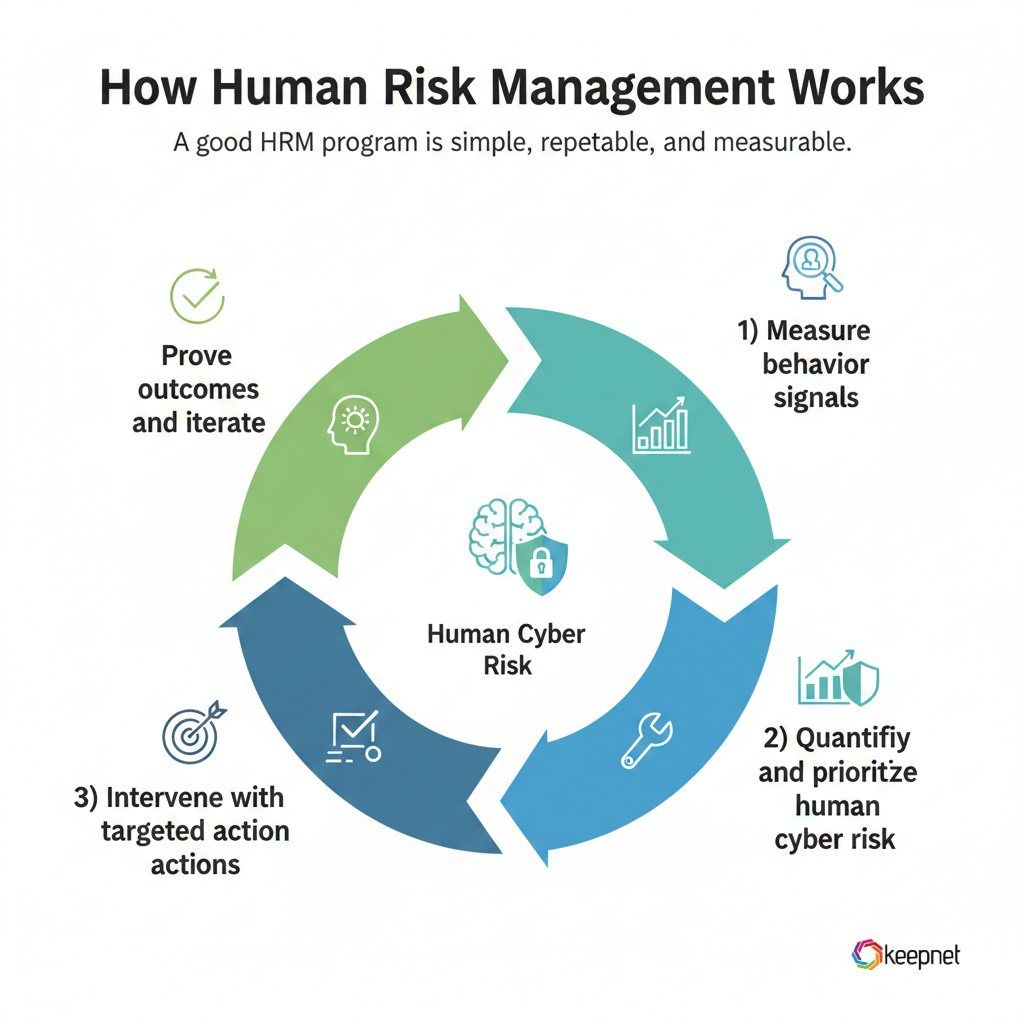
1) Measure behavior signals
You collect signals like simulation outcomes, reporting patterns, repeat behaviors, risky actions by workflow, and role-based exposure. This is where HRM moves from opinions (“people are the problem”) to evidence (“these three workflows are creating repeated risk”).
2) Quantify and prioritize human cyber risk
You translate signals into a practical risk view: risk by user, team, role, region, or job function. This helps you avoid wasting time on low-risk groups while high-risk workflows stay unchanged.
3) Intervene with targeted actions
Interventions should match the risk pattern, not your content calendar:
- microlearning for a role and scenario
- just-in-time training & nudges after risky behavior
- multi channel phishing simulations that mirror current attacker tactics
- process improvements that reduce security friction
This “measure → intervene” logic matches Forrester’s HRM framing.
4) Prove outcomes and iterate
You track whether risk trends move in the right direction, and whether the intervention reduced repeated risk. The goal is not perfection—it’s a measurable downward trend.
Benefits of Human Risk Management (what leaders care about)
HRM pays off when it creates outcomes you can show to the board, auditors, and operational teams.
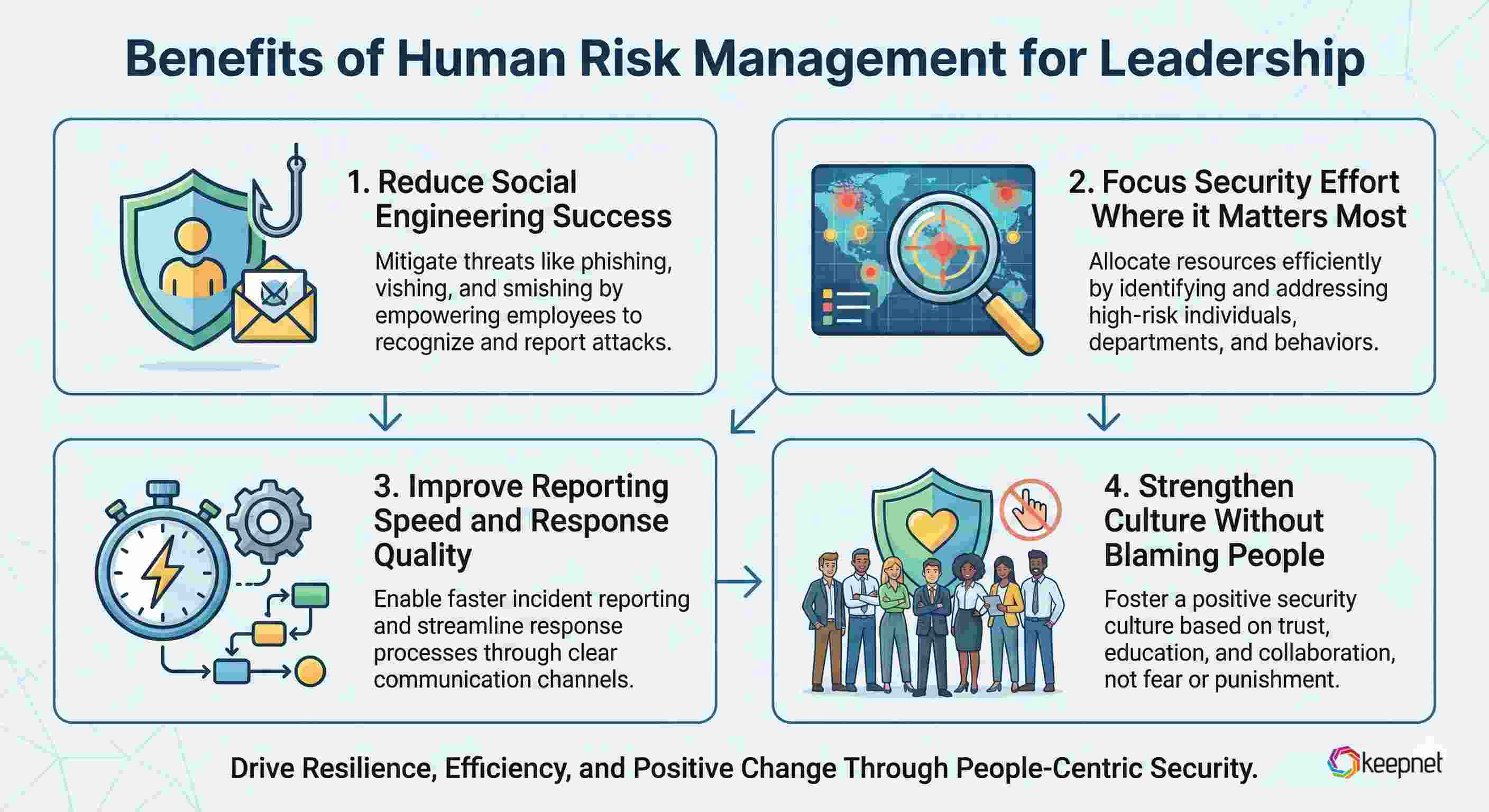
Reduce social engineering success
HRM helps reduce successful phishing, smishing, vishing, and deepfake-driven fraud attempts by targeting the roles and behaviors attackers actually exploit.
Focus security effort where it matters most
Instead of treating all employees as equal risk, HRM prioritizes based on real exposure and observed behavior—so your team spends time where it reduces risk fastest.
Improve reporting speed and response quality
Better reporting behavior means faster containment. HRM trains “what to do next” and reinforces it through nudges and repeated practice.
Strengthen culture without blaming people
HRM isn’t about “employees are the problem.” It’s about making secure behavior the easiest behavior by reducing friction and improving workflows (a theme emphasized in Gartner’s PIPE framework for security behavior and culture programs).
Human Risk Management metrics (what to track)
HRM metrics work best when you group them into leading indicators (predict risk) and outcomes (prove results).
Leading indicators (behavior risk)
These help you act before incidents happen.
- Repeat-risk behaviors (same risky action repeating)
- Role exposure (e.g., Finance approvals, HR onboarding, IT help desk verification)
- MFA fatigue patterns (unsafe approvals under prompt pressure)
- QR and mobile susceptibility patterns (scan behavior)
- Vishing/callback verification discipline
Response indicators (security operations value)
These show how humans support detection and response.
- Time to report suspicious events
- Report quality (actionable details)
- Time to contain after a user report
Outcome indicators (business impact)
These prove HRM is working.
- Fewer successful social engineering incidents
- Fewer credential-related compromises
- Reduced preventable errors (misdelivery, oversharing, unsafe sharing settings)
Human Risk Management examples: what HRM protects against
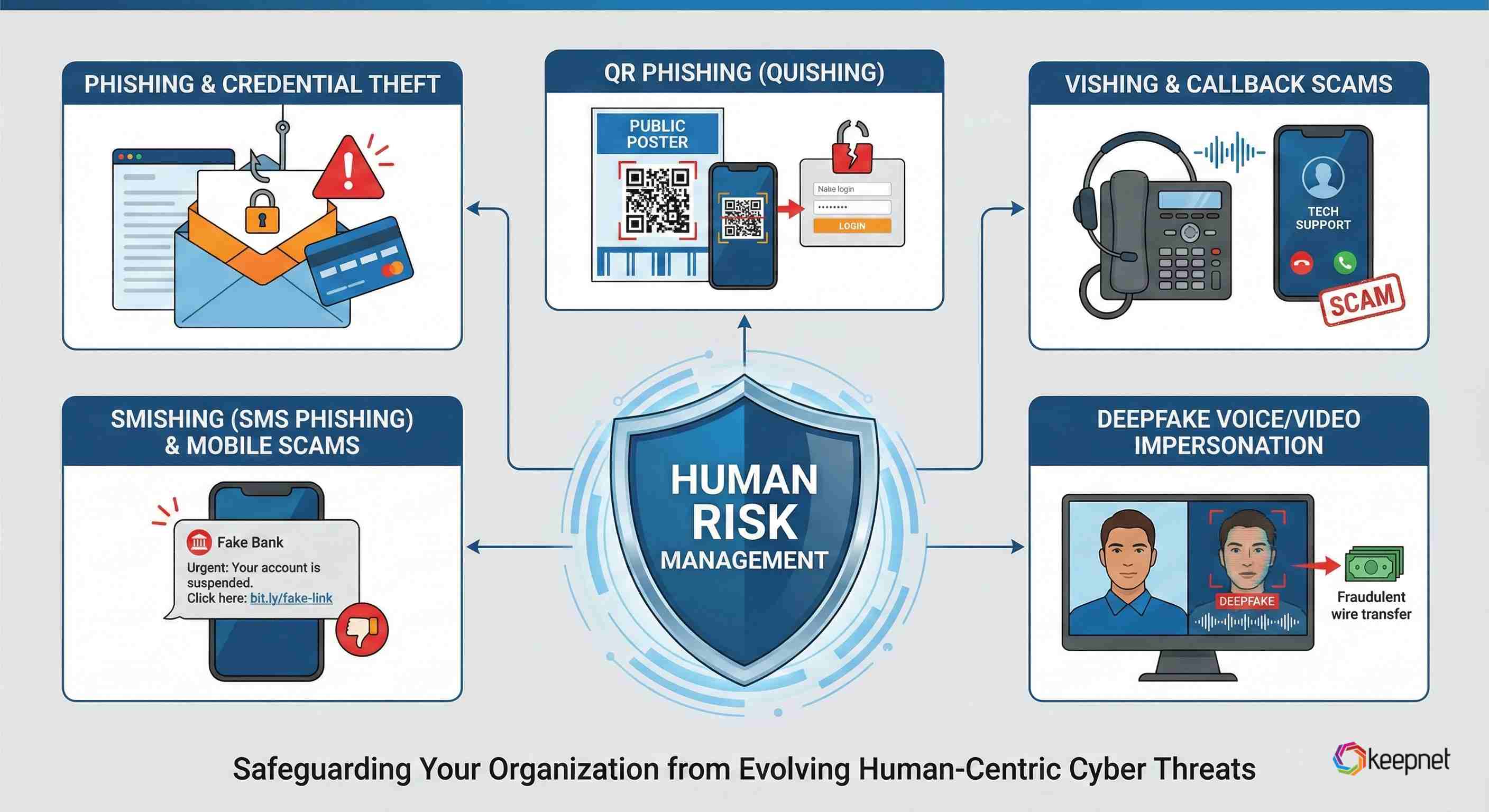
HRM is easiest to grasp through scenarios. Here are common HRM use cases.
Phishing and credential theft
Employees are tricked into entering credentials on lookalike pages. HRM reduces this by identifying who repeats risky behavior and delivering targeted coaching (not generic reminders).
Smishing (SMS phishing) and mobile scams
Mobile decisions are fast and distracted. HRM addresses mobile behavior with realistic smishing scenarios and just-in-time nudges.
QR phishing (quishing)
QR codes remove the “hover-to-check” safety moment. HRM helps by training QR-specific verification habits and testing QR decision-making in safe simulations.
Vishing and callback scams
Voice scams exploit urgency and helpfulness. HRM focuses on verification behaviors (what must be checked, what must never be shared) and reinforces them for high-exposure teams.
Deepfake voice/video impersonation
Deepfakes escalate “trust attacks.” Gartner notes deepfake attacks are already common for many organizations. HRM reduces risk by training verification behaviors (out-of-band checks, secure approval processes) and by focusing on executive assistants, finance, help desk, and leadership—roles attackers target most.
A practical 90-day Human Risk Management plan
A 90-day plan makes HRM real and helps you avoid “we’ll start next quarter” paralysis.
Days 1–30: Baseline + quick wins
Start with 2–3 high-impact scenarios (phishing-to-login theft, vishing/callback, MFA fatigue). Measure baseline behaviors, identify repeat-risk groups, and deploy short role-based microlearning and nudges.
Days 31–60: Role-based expansion
Expand to more roles and scenarios (smishing, QR phishing, deepfake impersonation). Build segments by role and exposure. Make reporting behavior part of the routine (what good reporting looks like).
Days 61–90: Automation + proof
Automate interventions where possible and show trend lines: repeat risk down, reporting speed up, fewer preventable incidents. This is where HRM earns trust and budget.
How to choose a Human Risk Management platform
A Human Risk Management platform should make HRM easy to run as a program.
HRM platform capabilities to look for
A strong platform typically supports:
- behavior measurement and human risk scoring
- segmentation by role, region, and exposure
- targeted interventions (microlearning, nudges, simulations)
- reporting that proves risk reduction over time
- multi-channel scenario coverage (not “one channel only”)
Vendor questions worth asking
Ask questions that force measurable answers:
- “How do you reduce repeat-risk users?”
- “How do you show behavior change, not just course completion?”
- “Can you tailor scenarios by role and region?”
- “How do you connect HRM signals to incident response workflows?”
- “What does success look like in 90 days?”
Use Keepnet Human Risk Management Platform
The strongest HRM strategy combines three things: a Human Risk Management Platform to measure and prioritize risk, Security Awareness Training to build knowledge and habits, and a Phishing Simulator (plus other channels) to safely practice decisions under pressure.
The strongest Human Risk Management (HRM) platforms combine measurement, practice, and reinforcement—so you can prove risk goes down over time. Keepnet brings these pieces together in one place:
- Human Risk Management Platform: To measure human risk, prioritize high-exposure roles, and track risk trends.
- Security Awareness Training: to build role-based habits with short, relevant microlearning.
- Phishing Simulators: (email, voice, SMS, QR, and MFA-fatigue scenarios) to safely test real-world behavior and trigger coaching in the flow of work.
Keepnet has been named a go-to vendor for stopping deepfake and AI disinformation attacks by Gartner.
If you want to see where your highest human risk sits today—and what to fix first—request a demo and we’ll share a clear 90-day rollout plan.
Editor's note: This article was updated December 30, 2025.