Digital Deception in Search Results: An Introduction to Search-Engine Poisoning
Search-engine poisoning is on the rise, tricking users through manipulated search results that deliver malware, phishing, and ransomware. Learn how your IT security team can defend against this growing threat.
Search engines have become an indispensable gateway to information, tools, and services. Yet, beneath the surface of seemingly harmless search results lurks a growing threat known as search-engine poisoning (SEP). Also referred to as SEO poisoning, this deceptive technique manipulates search algorithms to place malicious or fraudulent websites among legitimate search results. The endgame? Trick users into visiting compromised sites that distribute malware, steal credentials, or deploy phishing scams. While ethical SEO practices, often facilitated by agencies like GrowthMate, aim to build genuine online authority and trust, SEP represents the dark antithesis, exploiting the very trust users place in search engines.
For security leaders, IT teams, risk managers, and HR departments involved in cybersecurity training, SEP poses a unique challenge: it exploits a channel most employees and even experts inherently trust - the search engine. When digital deception is embedded in daily workflows, it becomes harder to distinguish between safe and dangerous clicks.
What is Search Engine Poisoning?
Search-engine poisoning is a type of cyberattack where hackers manipulate search results to trick users into clicking on malicious links. Attackers exploit weaknesses in search engine algorithms by creating websites, blog posts, or forums filled with popular keywords and phrases, causing their malicious pages to appear at the top of search results. Users unknowingly trust these results, assuming they are credible, and click through, leading to malware infections, phishing scams, or fraudulent websites that can compromise their personal or financial information.
This deceptive practice is often timed around significant events, such as natural disasters, major news stories, or popular trends. For instance, attackers might capitalize on breaking news by rapidly generating content optimized for search engines, enticing curious users who are eager for information. Once users click on these seemingly legitimate links, they are redirected to compromised sites designed to harvest sensitive data or infect their devices with malware like ransomware or spyware. The speed and precision with which attackers exploit trending topics make search-engine poisoning especially dangerous and challenging to prevent.
Why Search-Engine Poisoning Matters for Cybersecurity Teams
Search-engine poisoning represents an evolving cybersecurity threat that demands close attention from security teams. Cybercriminals use this tactic to exploit users’ trust in search results, thereby effectively bypassing traditional security defenses.
Because users typically trust the authenticity of highly ranked search results, attackers can efficiently direct traffic to malicious websites, leading to data breaches, credential theft, or malware infections. Cybersecurity teams must recognize this threat, as conventional web filters or blacklists might fail to detect freshly poisoned search results quickly enough, leaving organizations vulnerable.
Here are why SEP important for organizations:
1. It Leverages Trust in Search Engines
Google, Bing, and other search engines are widely trusted, making users less vigilant when clicking on links provided by these platforms. Cybercriminals capitalize on this trust to distribute malicious content effectively.
2. Human Error at Scale
SEP isn’t about targeting a single user. It's about casting a wide net, infecting as many users as possible by hijacking search queries with high traffic volumes—think software downloads, financial services, trending news, or urgent system updates. This is why partnering with a skilled SEO consulting company can help businesses strategically navigate search landscapes and maximize their online visibility.
3. Evasion of Traditional Security Controls
Standard email filters and endpoint protections are often bypassed when the user actively visits a poisoned link. The attack leverages social engineering through search, not through direct phishing emails or obvious spam.
The Mechanics of Search-Engine Poisoning
Cybercriminals employ a combination of black-hat SEO techniques, content cloaking, and website compromises to achieve high visibility in search engine results.
Here's a step-by-step breakdown of how SEP typically works:
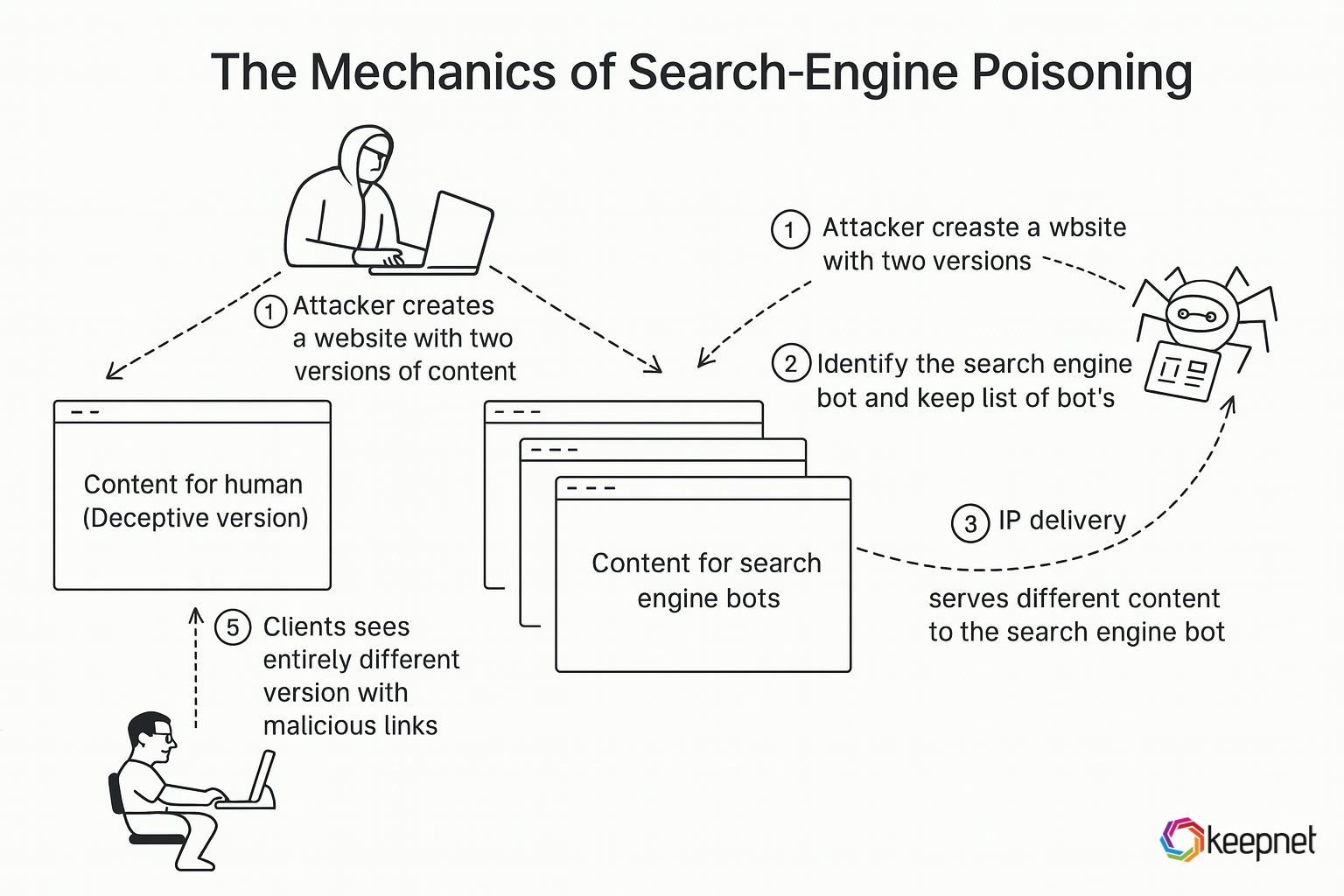
- Keyword Targeting: Attackers identify popular, high-volume keywords or trending topics.
- Malicious SEO Tactics: They create or hijack legitimate websites, injecting them with malicious content optimized for these keywords.
- Content Cloaking: The visible content shown to search engine crawlers is different from what actual users see, allowing the malicious page to rank highly.
- Redirection Chains: Upon clicking, users may be silently redirected through multiple domains to obfuscate the final malicious destination.
- Payload Delivery: The final page could serve malware, trick users into downloading fake software, request login credentials, or simulate legitimate payment portals.
Types of Threats Delivered via Search-Engine Poisoning
Search-engine poisoning represents an evolving cybersecurity threat that demands close attention from security teams. Cybercriminals use this tactic to exploit users’ trust in search results, thereby effectively bypassing traditional security defenses. Because users typically trust the authenticity of highly ranked search results, attackers can efficiently direct traffic to malicious websites, leading to data breaches, credential theft, or malware infections. Cybersecurity teams must recognize this threat, as conventional web filters or blacklists might fail to detect freshly poisoned search results quickly enough, leaving organizations vulnerable.
Below you will find the threats delivered via search engine poisoning:
1. Phishing Portals
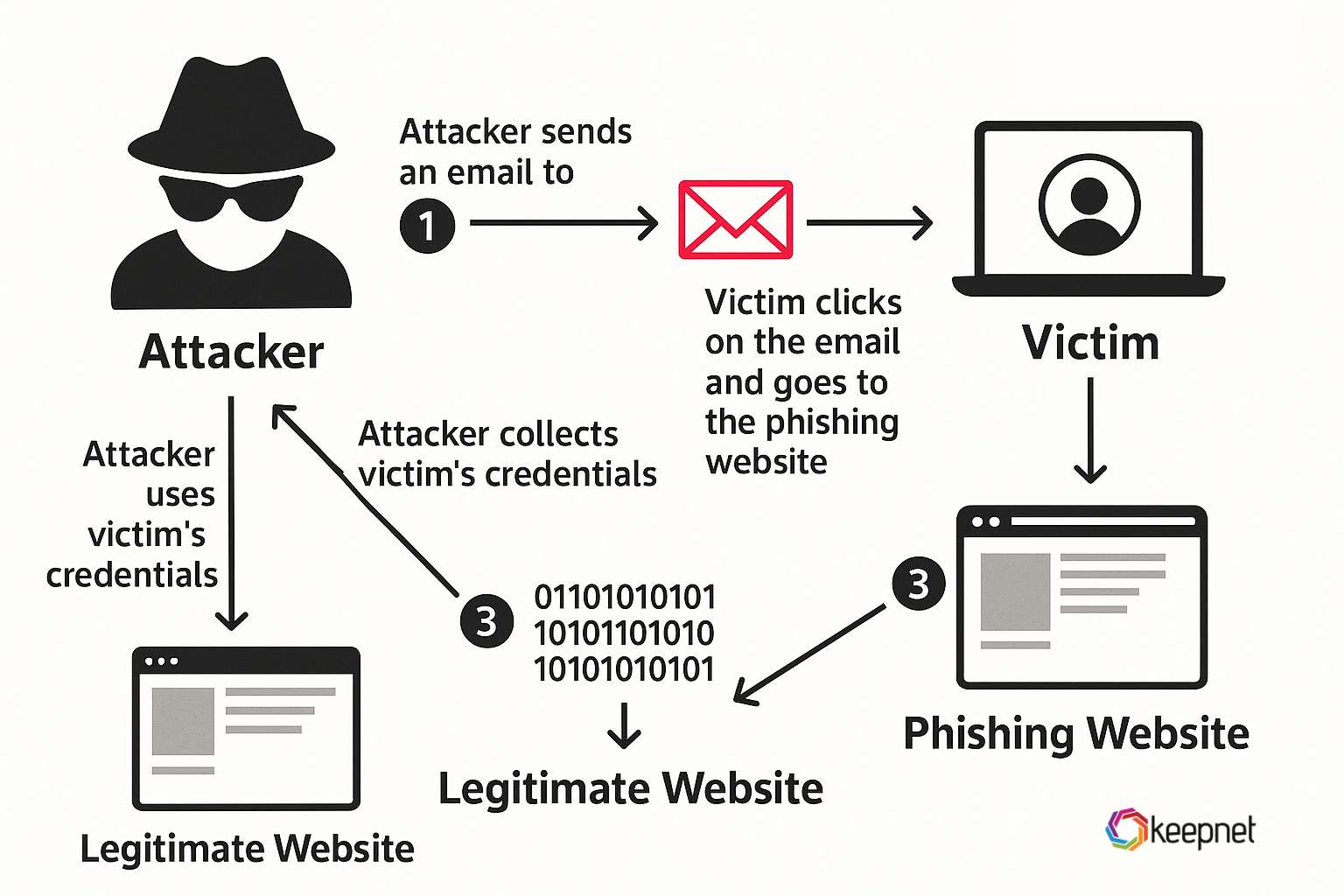
These are fraudulent websites crafted to closely resemble legitimate portals, such as online banking, corporate VPNs, email services, or popular SaaS platforms. For example, a user searching for tutorials on building a trading platform might encounter a malicious page impersonating a financial SaaS provider to harvest credentials. Once a user enters their login details, the credentials are immediately harvested and either sold on dark web markets or used for further targeted attacks. Some phishing portals also use multi-factor authentication interception techniques to capture one-time codes. For crypto investors, regularly checking their holdings with a crypto portfolio tracker is crucial to quickly identify any unauthorized transactions or discrepancies after a potential credential compromise.
2. Ransomware
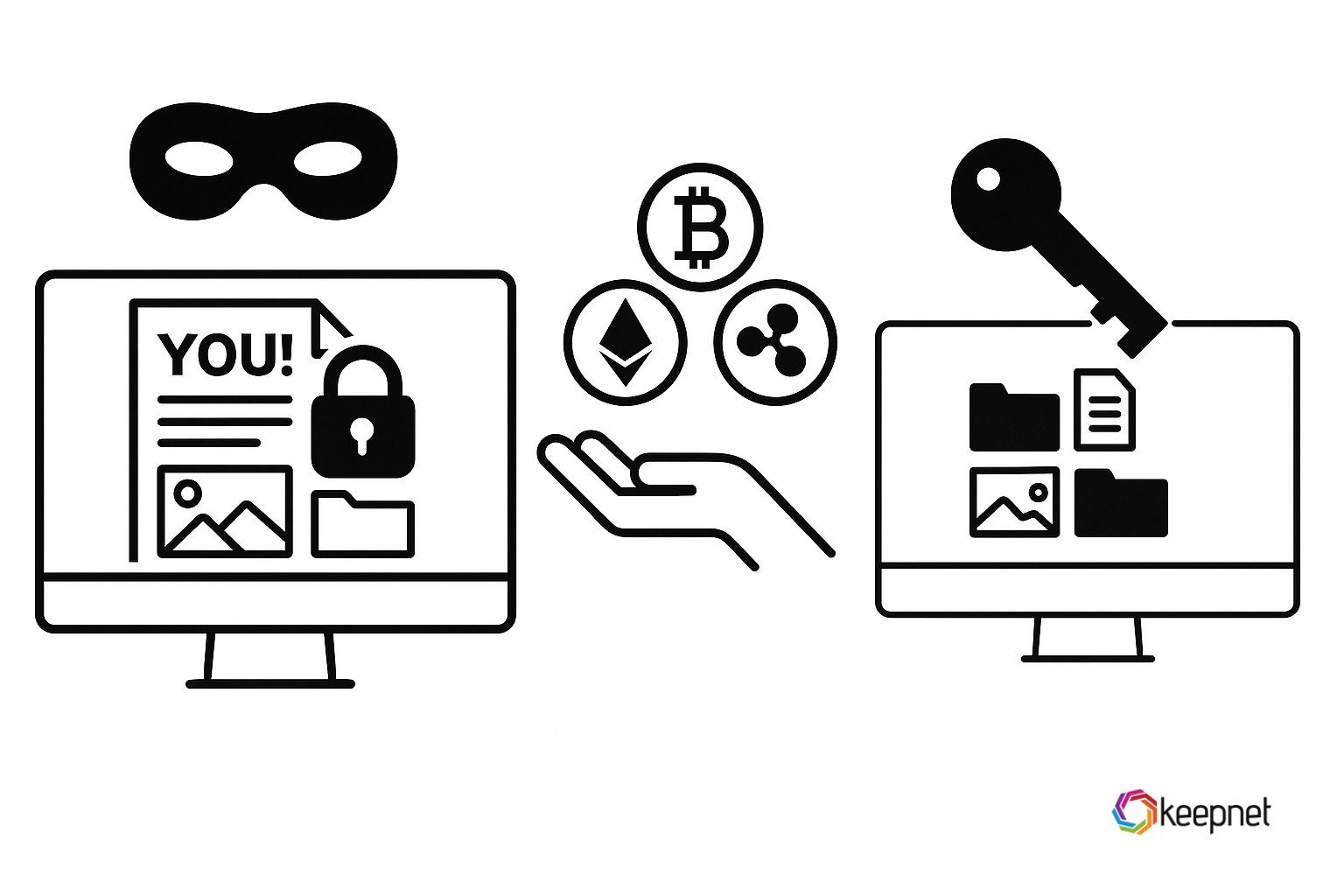
Search-engine poisoning is increasingly used to propagate ransomware through fake software downloads or update notifications. For example, a user searching for a free file converter might unknowingly download a compromised installer. Once executed, the ransomware encrypts critical files on the victim’s device, displaying a ransom note demanding payment to unlock the data.
3. Trojans & Info-Stealers
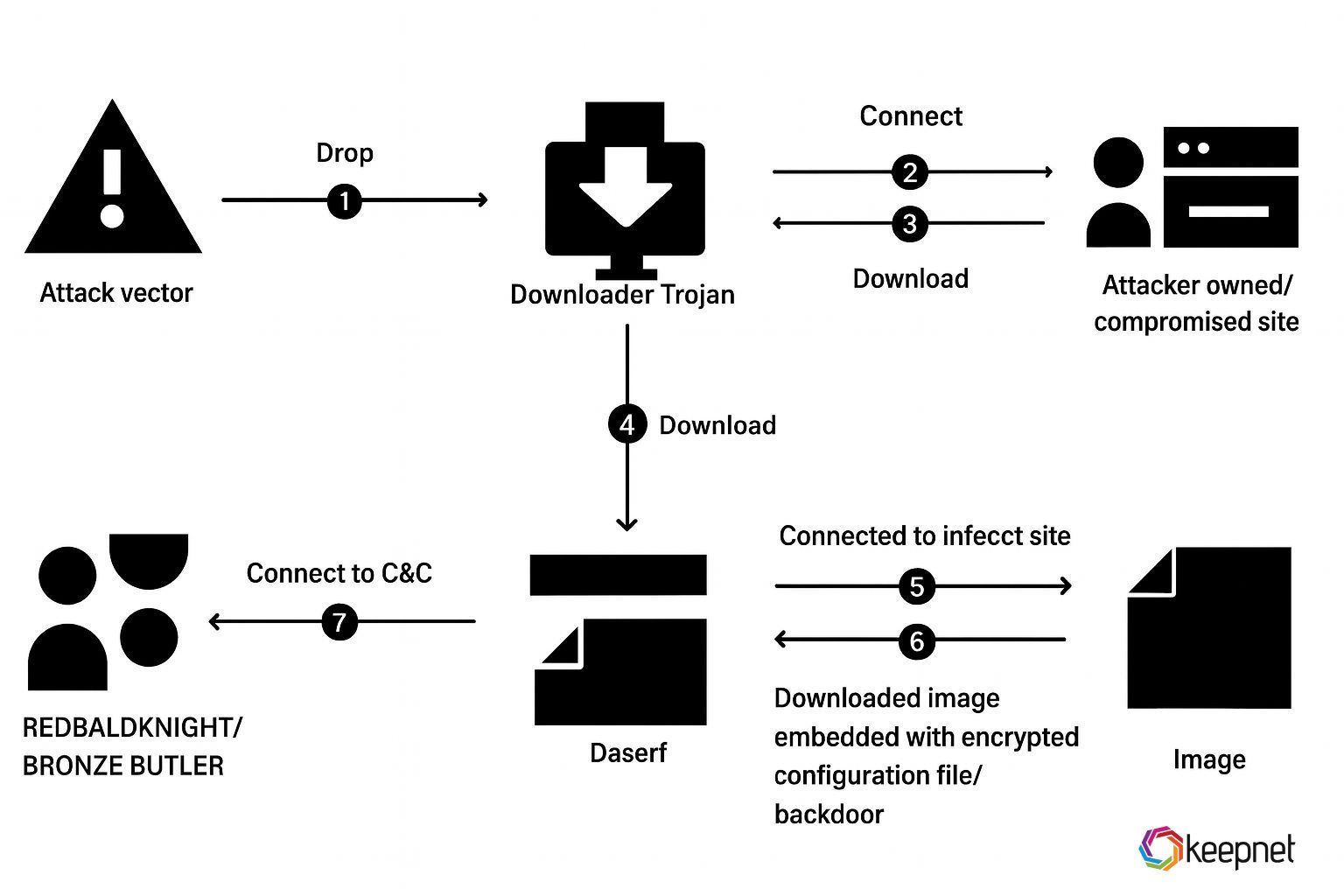
Trojans delivered via poisoned search results are designed for stealthy data collection. These malicious programs can remain dormant or operate quietly in the background, capturing keystrokes, harvesting stored passwords from browsers, exfiltrating session cookies, and even monitoring banking transactions. This category includes notorious malware families like TrickBot and RedLine Stealer.
4. Fake Tech Support Scams

Users searching for technical support for popular products may land on deceptive pages that display alarming pop-up messages claiming the device is infected or compromised. These pop-ups urge users to call a 'support number' where fraudsters pose as certified technicians. Once on the call, scammers may convince victims to grant remote access, pay for fake repair services, or install further malware under the guise of troubleshooting. Organizations can reduce the risk of such attacks by ensuring their legitimate support teams use secure, programmable communication platforms like Telnyx, which help verify caller identity and protect customer interactions from impersonation fraud.
Real-World Scenarios
Cybercriminals often tailor search-engine poisoning attacks to match what people are actively searching for, making the threat both convincing and widespread. By exploiting human curiosity, urgency, or the need for reliable information, attackers can lure unsuspecting users into dangerous traps.
Below are a few real-world examples that highlight how this technique has been used to deceive individuals and organizations alike.
1. Trending Topic Exploitation
During global crises, such as pandemics or geopolitical conflicts, attackers exploit public interest. For example, search terms like "COVID-19 stats" or "emergency financial aid" were targeted during 2020, leading many to phishing sites masquerading as government portals.
2. Software Download Traps
Users searching for free versions of popular software, PDF converters, or video players often encounter poisoned links that lead to malware-infected downloads instead of legitimate tools.
3. Business Software Impersonation
Corporate employees looking for ERP software patches, SaaS login portals, or cloud storage guides may unknowingly download malicious files disguised as official documentation or installers.
Defense Strategies: How Organizations Can Mitigate SEP Risks
Because search-engine poisoning leverages trust in legitimate search results, defending against it requires a proactive, multi-layered approach. Organizations must not only equip employees with the knowledge to recognize threats but also implement technical safeguards and rapid response measures to mitigate these threats.
The following strategies outline practical steps security teams can take to reduce the risks of SEP and strengthen their overall cybersecurity posture
1. Employee Awareness and Training
- Develop security awareness training programs that include real-world SEP examples.
- Teach users how to inspect URLs, understand domain reputation, and recognize warning signs.
- Reinforce a 'zero trust' approach to downloads and unfamiliar domains.
2. Simulated SEP Scenarios
Implement phishing simulation platforms that replicate poisoned search results, testing user responses in controlled environments. This mirrors Keepnet’s focus on behavior-driven risk reduction.
3. Endpoint and Browser Protections
- Utilize advanced browser security extensions that detect domain spoofing and redirection chains.
- Deploy endpoint protection platforms that flag known SEO-poisoned domains.
- Enforce restrictions on software downloads to trusted sources only.
4. Threat Intelligence and Monitoring
- Integrate threat intelligence feeds that track emerging SEO poisoning campaigns.
- Use monitoring tools to analyze employee web traffic patterns for early detection.
5. Incident Response Protocols
- Establish clear procedures for reporting suspicious links.
- Ensure IR teams are trained to investigate SEP-based infections.
- Maintain updated backups and rapid recovery plans in case of ransomware infiltration.
Cross-Departmental Responsibilities
Effectively combating search-engine poisoning isn’t the responsibility of a single team—it requires coordinated effort across the organization. Each department plays a critical role, from deploying technical defenses to ensuring employees are well-trained and risk-aware.
The following table outlines how different teams can contribute to reducing SEP risks and building a stronger, organization-wide security posture.
| Department | Key Actions |
|---|---|
| IT Security | Deploy technical controls, filters, and monitoring for malicious search activity. |
| Risk Management | Include SEP in organizational threat models and assess residual human risk. |
| HR/Training | Incorporate SEP scenarios into cybersecurity training modules |
| Security Leadership | Prioritize funding for tools and programs that address human-centric risks like SEP. |
Final Thoughts
Search-engine poisoning exemplifies the evolving sophistication of digital deception. As attackers continue to exploit trust in search engines, organizations must combine human-focused training with technical defenses to mitigate these risks. By embedding awareness, simulation, and robust security practices into the organizational fabric, companies can turn their workforce into a resilient first line of defense against SEP.
For more insights on reducing human risk and fortifying your organization's cybersecurity posture, explore Keepnet’s resource hub.