Most Common Examples of Malware Attacks You may Encounter in 2025
This blog post outlines effective ways to protect your organization from malware attacks. Discover how to use phishing simulations, improve employee awareness, and apply best practices to strengthen your defenses against growing cyber threats.
In 2025, malware attacks are no longer just an occasional nuisance; they’ve become an everyday threat to both individuals and organizations.
Every click, download, or plug-in poses a risk of introducing a digital parasite into your system. As common malware attacks become more sophisticated, it’s essential to stay informed about the most dangerous types of malware and how they operate.
Let's take a closer look at the most recent malware attacks that have left a lasting mark on the cybersecurity landscape. Understanding them is the first step in protecting yourself and your business.
What Does Malware Mean?
We talk about malware attacks a lot, but what exactly is it? At its core, malware—short for “malicious software”—is designed to infiltrate, damage, or gain unauthorized access to systems. It can steal sensitive data, spy on users, or lock you out of your own network. And just like a biological virus, it’s highly contagious—once it’s in, it can spread fast and quietly.
Malware comes in many forms, and each type of malware has its unique way of sneaking into your systems. Whether it’s a Trojan virus attack pretending to be legitimate software or a rootkit attack that grants hackers hidden control over your devices, knowing what you’re up against is significant.
What Are the Different Types of Malware?
To defend against the most dangerous malware attacks, you first need to know what you're up against. Each type of malware operates differently, and understanding these distinctions can be the key to stopping an attack before it causes real damage. Below are the most common malware attacks that have been keeping security teams on high alert:
Some of these cyber security threats are designed to steal sensitive data, while others aim to disrupt systems, spy on users, or lock you out entirely. In the next sections, we’ll take a closer look at what these different types of malware do, how they work, and why they’re so dangerous.
Viruses (NEW)
Think of a virus as the classic bad guy in the malware world. It attaches itself to legitimate files, often spreading through infected downloads, emails, or external drives. Once a virus gets into your system and is activated (usually by the user opening the infected file), it can replicate, corrupt, or delete data, making your systems unstable or unusable.
Unlike other types of malware, viruses typically require user action to spread—such as sharing infected files or opening compromised email attachments. While many viruses are designed to disrupt your system, others can create backdoors for further attacks. Keeping your software up to date and scanning for viruses regularly is essential to protect against these common malware attacks.
Trojan (NEW)
A Trojan virus attack is one of the trickiest forms of malware because it pretends to be something legitimate, often tricking users into letting it in. It might present itself as a software update, a useful tool, or even a harmless PDF file.
However, once installed, it opens a backdoor, granting cybercriminals unauthorized access to your system. This allows hackers to steal sensitive data, install additional malware, or even gain complete control of your device.
Trojans are especially dangerous because they don’t just infect your system—they pave the way for future attacks by giving hackers a foothold in your network. Be cautious with downloads and ensure email security training is in place to avoid Trojan-laced attachments.
Botnet (NEW)
Botnets are like sleeper agents in the world of malware. Once your device is infected, it becomes part of a larger network of compromised devices (called "bots" or "zombies") controlled by a hacker, often without your knowledge. These botnets are used for large-scale attacks, like Distributed Denial of Service (DDoS) attacks, which can disrupt websites and services. The scariest part? Your device could be involved in these attacks without you even knowing. Phishing attacks and compromised devices often form the foundation of these botnets.
Rootkit (NEW)
A rootkit attack is highly dangerous type of malware because it embeds deeply into a system, allowing cybercriminals undetected control over a device for long periods. Rootkits often operate without leaving obvious signs of infection, making them hard to detect and remove. Once in place, they allow attackers to manipulate the system, steal data, and disable security software.
Their ability to stay hidden means they can go unnoticed until significant damage is done. Regular security audits and anti-rootkit tools are essential defenses against a rootkit attack.
Spyware (NEW)
As its name suggests, spyware is designed to secretly monitor your activities without your knowledge. It tracks everything from keystrokes to passwords and sensitive information, often operating quietly in the background. Spyware is typically bundled with legitimate software or downloaded from malicious sites. Although it can slow down your system, its primary danger is the silent theft of your data. Using anti-spyware tools and regularly scanning devices can help detect and remove it before major harm is done.
Adware (NEW)
Adware may not be as destructive as other forms of malware, but it’s intrusive and can significantly slow down your device. It floods your screen with unwanted ads and can even redirect your browser to risky websites.
While its primary goal is generating revenue for its creators through ads, adware can track your browsing habits and expose you to more serious threats.
Adware often opens the door to more dangerous malware. Removing adware as soon as detected is crucial to protecting your privacy.
Ransomware (NEW)
Ransomware is the heavyweight of malware, causing massive financial and operational damage. Once it infects your system, it encrypts your files and demands a ransom, typically in cryptocurrency, for the decryption key.
Ransomware has shifted from targeting individuals to businesses, hospitals, and government agencies.
Modern campaigns, like Clop and Darkside, often use Ransomware-as-a-Service (RaaS) models, making them more accessible to attackers.
Without proper backups or cybersecurity measures, victims are left with a painful choice: pay the ransom or lose their data. Ransomware attacks like these are becoming increasingly sophisticated.
CryptoJacking (NEW)
Cryptojacking malware, such as CoinMiner and XMRig-based malware, is designed to stealthily exploit your system’s processing power to mine cryptocurrency without your knowledge.
By running silently in the background and consuming CPU or GPU resources, this malicious software slows down devices, increases energy consumption, and can even cause hardware damage over time—all while generating profits for cybercriminals.
What Is the Most Dangerous Type of Malware?
While all forms of malware are dangerous, ransomware has become the most destructive in recent years. It not only locks you out of your own systems but also threatens to expose sensitive data if a ransom isn’t paid.
Recent attacks like Clop and Darkside show just how devastating ransomware can be, from halting operations to causing massive financial losses.
The introduction of Ransomware-as-a-Service has also escalated the threat level, allowing cybercriminals with little technical knowledge to launch sophisticated attacks by renting ransomware tools from skilled developers. It’s like the dark side of the gig economy.
How Does Malware Infect?
Malware can get into your devices in a few ways. It's like having uninvited guests crash your party, and they can get in through some surprising doors you might not have thought about.
Let's talk about two common ways malware attacks find their way in:

Phishing
Phishing is when you get an email that looks like it’s from a friend or a company you know, asking you to click on a link or download an attachment with malicious intentions.
It's like fishing, but instead of catching fish, hackers are fishing you. The link or attachment is bait. When you bite by clicking or downloading, the malware gets control of your device.
USB
USB drives, those small sticks we use to transfer files, can also be carriers of malware. Here's how: someone might leave a USB drive in a place where you find it, like on a desk or in a parking lot. You plug it into your computer out of curiosity or wanting to return it. But surprise, that USB drive is infected with malware, and just plugging it in can install harmful software on your device without you even knowing. It's like accidentally inviting a thief into your house just because they knocked on your door.
Websites
Sometimes, just visiting a website is enough to get malware. It’s like walking into a spider web without seeing it; suddenly, you’re caught. Some websites are booby-trapped with malware that can download itself onto your device as soon as you visit the page.It’s not always the obvious risky websites, either; even legitimate sites can be hacked and used to spread malware. Be cautious always, and consider getting security awareness training or learning what to do if you click on a phishing link.
Infected Files
Downloading files from the Internet can be like picking up hitchhikers; you might end up with more than you expected.
Malware can hide inside harmless files, such as documents, movies, or games. Once you download and open the file, the malware can attack and infect your device. Always download from trusted sources and update your antivirus software to catch these malicious files.
Network
Malware can also spread through networks, like a cold in a crowded room. If one device on a network gets infected, the malware can use the network connections to spread to other devices.
This is especially dangerous in places with lots of computers connected together, like offices or homes with multiple devices. It’s like the malware is playing tag, and every device is “it” at some point. Keeping your network secure and monitoring for suspicious activity can help prevent the spread of malware.
3 Most Common Examples of Malware Attacks
Let’s take a closer look at the 3 most common malware attacks that have caused significant damage in recent years.
These types of malware are among the most dangerous threats found online today. They can lead to data breaches, financial losses, and major disruptions in both personal and business environments. Understanding how these attacks work is key to protecting yourself from becoming a victim.
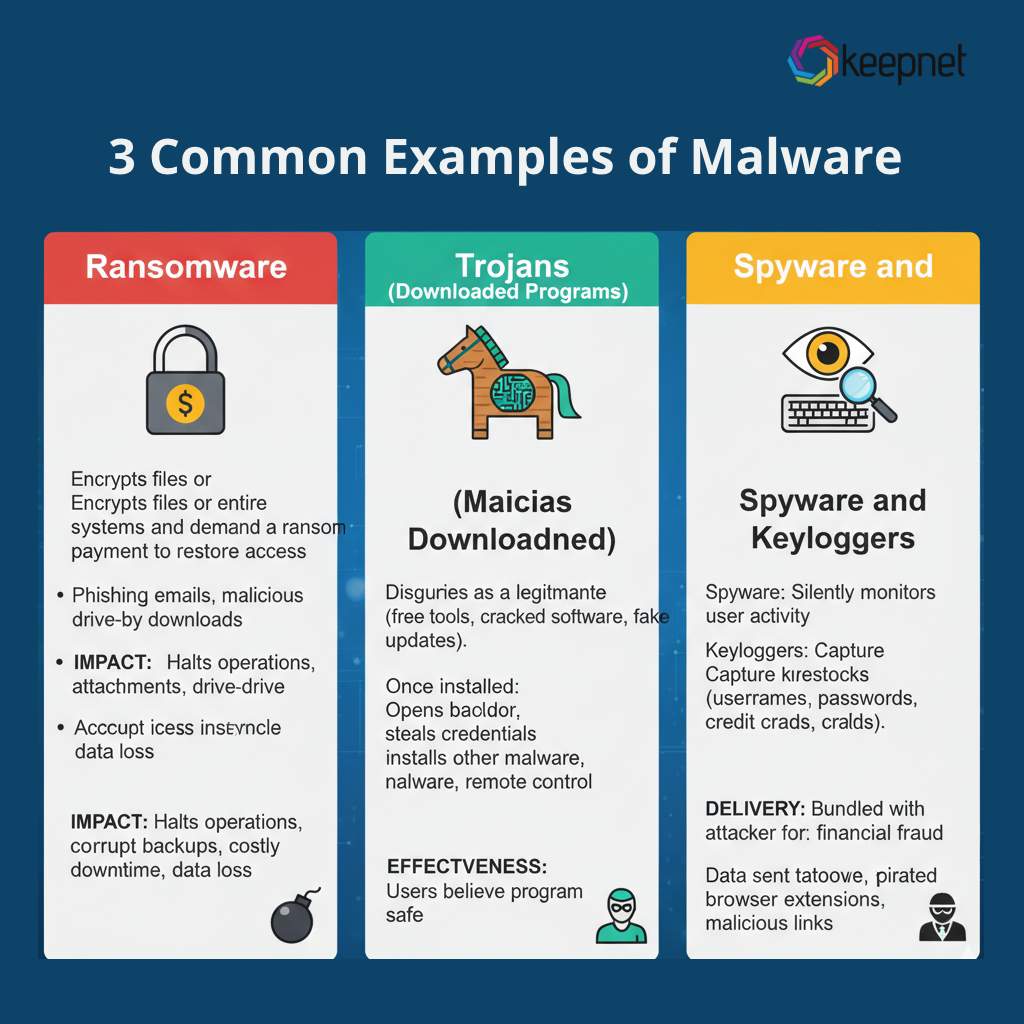
Let's discuss the 3 most common examples of malware attacks. These are the kinds of digital troublemakers you definitely don't want to encounter on the Internet.
1. Ransomware
Ransomware encrypts files or entire systems and demands a ransom payment to restore access. Attackers often deliver it through phishing emails, malicious attachments, or drive-by downloads. For businesses, ransomware can halt operations, corrupt backups, and lead to costly downtime and data loss.
2. Trojans (Malicious Downloaded Programs)
A Trojan disguises itself as a legitimate program—such as a free tool, cracked software, or even a fake update. Once installed, it can open a backdoor, steal credentials, install other malware, or give attackers remote control of the device. Because users believe the program is safe, Trojans are one of the most effective malware delivery methods.
3. Spyware and Keyloggers
Spyware silently monitors user activity, while keyloggers specifically capture keystrokes such as usernames, passwords, and credit card numbers. This data is then sent to the attacker, who can use it for account takeover, identity theft, or financial fraud. Spyware often comes bundled with pirated software, browser extensions, or malicious links.
Please also check this video below and learn what is malware and the most common malware types.
How to Defend Against Malware Attacks?

Defending against malware attacks requires a multi-layered approach that combines awareness, technology, and proactive measures. Here are a few key ways to protect your systems:
1. Keep Your Software and Systems Updated
Malware often exploits vulnerabilities in outdated software. Regularly updating operating systems, applications, and security patches helps close these gaps.
2. Install Strong Antivirus and Anti-Malware Solutions
Use reputable antivirus and anti-malware tools to detect and block threats before they infiltrate your systems. Regular scans are essential to spot any suspicious activity.
3. Conduct Regular Backups
Backing up critical data regularly ensures that even if ransomware encrypts your files, you won’t lose everything. Use both cloud-based and offline backups for extra security.
4. Provide Security Awareness Training
Human error is often the weakest link in security defenses. Teach your employees how to recognize phishing emails, avoid suspicious downloads, and practice good cyber hygiene. Security awareness training and phishing simulation can significantly reduce the chances of malware infiltrating your systems.
5. Use Firewalls and Network Segmentation
Isolate sensitive areas of your network to prevent malware from spreading. Firewalls can help filter malicious traffic and provide an additional layer of protection.
Watch the video below and learn more about 2025 common malware attacks.
Protect Your Organization from Malware Attacks with Keepnet’s Security Solutions
To safeguard your organization from a wide range of cyber threats, Keepnet Human Risk Management Platformoffers a comprehensive suite of educational and training tools. These solutions help your workforce recognize and respond to evolving digital threats.
Keepnet’s phishing simulators train employees to spot and avoid phishing attacks—one of the most common entry points for security breaches.
Additionally, our threat intelligence resources keep you updated on the latest cyber risks, helping you stay ahead of potential attackers.
Beyond phishing, Keepnet provides thorough security awareness training that covers a variety of threats, such as social engineering tactics.
This training empowers your employees to act as the first line of defense by recognizing suspicious activity and responding appropriately. Keepnet’s security awareness training can increase employee awareness and lead to a reduction of up to 90% in high-risk security behaviors, significantly lowering the chances of human error resulting in costly security breaches.
Don't wait for an attack to exploit a vulnerability.
Start your free trial today and arm your team with the cybersecurity knowledge they need to protect your organization from the evolving digital landscape.
Let Keepnet’s security awareness solutions be the foundation of your defense strategy.
Watch the video below to learn more about Keepnet's Human Risk Management platform.
Editor's Note: This article was updated on November 13, 2025.