How to Create an AI-Powered Security Awareness Training Program
Discover how to create a hyper-personalized, AI-powered security awareness program that aligns with regional compliance, role-specific risks, and employee behavior—using adaptive tools to build a proactive and security-conscious culture across your organization.
Researchers from Stanford University and a leading cybersecurity organization found that 88% of data breaches are caused by employee mistakes, showing how much impact human error have on cybersecurity outcomes. Clearly, traditional training methods are no longer enough. Organizations need smarter, adaptive approaches that reflect the complexity of modern digital workplaces.
That’s where AI-powered security awareness programs come in. These systems personalize training based on user behavior, job roles, geographic location, regulatory requirements, and even cultural and personality traits.
In this blog, we’ll break down how to create a dynamic, hyper-personalized security awareness program using AI to protect your organization at every level.
Why an AI-Powered Security Awareness Training Program Works Better in 2025
Traditional programs treat everyone the same. In 2025, attackers don’t, so your training can’t either. An AI-powered approach adapts to each role, behavior pattern, and threat surface in real time. The result is training that’s shorter, smarter, and measurably safer.
Risk scoring per role & behavior
AI aggregates real signals, phishing simulation campaign outcomes, real-world incident data, reporting speed, policy breaches, and even tool usage patterns—then weights them by role criticality. A finance approver who hesitates on vendor changes is a different risk from a field technician who scans QR codes all day. Dynamic scores create clear tiers (low/medium/high) so you can prioritize who needs what, when.
Personalized content & cadence (voice/SMS/QR/MFA-fatigue simulations)
No more one-size-fits-all modules. The system picks scenarios by channel and tactic: voice vishing for service desks, Smishing and QR for frontline teams, MFA-fatigue for admins, executive whaling for leadership. It also adjusts frequency, tightening the cadence after a fail, easing off after proven resilience—so people get the minimum effective dose instead of endless training.
Nudges & micro-interventions
Behavior change happens between courses. Lightweight, in-the-flow nudges, contextual banners, just-in-time tooltips, Slack/Teams reminders, or brief “try this instead” prompts after a risky click—close the gap between knowing and doing. These micro-interventions are short, timely, and specific to the user’s recent behavior, which makes them far more likely to stick.
KPI loop (time-to-remediate, risk reduction, culture lift)
AI turns training into a measurable control. Track time-to-remediate (how fast risky users recover), risk reduction (movement between risk tiers over weeks), and culture lift (reporting rates, phishing-resilience scores, secure-by-default actions). The program learns from these KPIs, automatically updating scenarios and cadence—creating a closed feedback loop that compounds improvements month after month.
AI-Powered Hyper-Personalized Security Awareness Program
A hyper-personalized security awareness program uses AI to continuously adjust training content based on employee behavior, risk levels, and organizational context. Instead of generic, repetitive modules, each user receives training that is timely, relevant, and specific to their responsibilities and risks. This approach not only reduces training fatigue but also builds stronger security habits that last.
Let’s break down the steps to create this program.
Step 1: Define Your Organization’s Region & Compliance Needs
If your organization operates in multiple locations, each region likely falls under different regulatory requirements and faces unique cyber threats. Your security awareness program must reflect these differences.
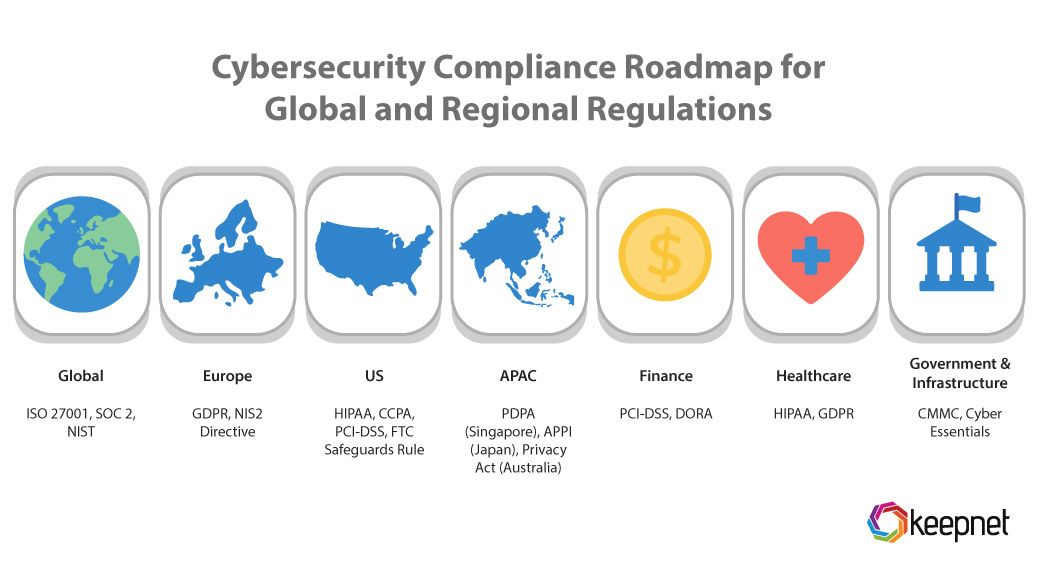
Examples of Compliance Requirements:
- Global: ISO 27001, SOC 2, NIST
- Europe: GDPR, NIS2 Directive
- US: HIPAA, CCPA, PCI-DSS, FTC Safeguards Rule
- APAC: PDPA (Singapore), APPI (Japan), Privacy Act (Australia)
- Finance: PCI-DSS, DORA
- Healthcare: HIPAA, GDPR
- Government & Infrastructure: CMMC, Cyber Essentials
Impact on Training
Training content should be tailored to match regional laws, helping employees understand local data protection obligations. This not only supports compliance but also makes the training more relevant and actionable.
Tools like the Keepnet Security Awareness Training simplify this process by automatically assigning region-specific modules based on location and industry.
Step 2: Industry & Business Unit Mapping
Every industry comes with its own set of cybersecurity risks and compliance requirements. A healthcare organization, for example, must protect sensitive patient data, while a SaaS provider might focus more on cloud security and customer credentials. To make training relevant, your program must reflect these differences across both industry and internal business units.
What to do:
Start by identifying the industry your organization operates in and the departments that make up your structure. Each sector—whether Finance, Healthcare, Retail, or SaaS—faces unique threats like ransomware, BEC, or data theft. Similarly, departments such as IT & Security, HR, Finance, Sales, Customer Support, Engineering, and Operations have different exposure levels and responsibilities. Check out this blog to see how our role based security awareness training works.
Impact on Training:
With Keepnet Security Awareness Training, you can assign industry-specific modules (e.g., BEC for finance teams, ransomware for healthcare) and tailor content for each department’s risk profile. Regulated sectors also receive targeted compliance training.
Step 3: Department & Role-Specific Training
Not every employee faces the same threats. A generic training program can miss the mark. To increase relevance and engagement, training should be customized based on departmental functions and job roles.
What to do:
Review the structure of your organization and categorize employees by department and role. Identify the specific security risks tied to each. This helps ensure each employee receives training that aligns with their day-to-day responsibilities and risk exposure.
Role-specific focus areas to consider:
- IT & Security: Incident response, secure coding, zero trust
- Finance: Invoice fraud, phishing, business email compromise (BEC)
- HR: Insider threats, employee data protection
- Customer Support: PII handling, phishing recognition
- Engineering: Secure DevOps, API security
Impact on Training
With tools like the Phishing Simulator, you can deliver targeted simulations to help employees recognize and respond to threats specific to their roles.
Explore Keepnet’s article on Adaptive Phishing Simulations to see how role-based simulations enhance employee response and reduce phishing risk.
Step 4: Behavioral Risk Scoring & Adaptation
Not all employees have the same level of risk. Some are more likely to click on phishing emails or ignore basic security practices. AI can help by tracking these behaviors and adapting training based on individual risk levels.
What to do:
Use behavioral data—such as phishing click rates, incident reporting history, and password habits—to identify high- and low-risk users. Then, adjust training intensity accordingly.
Examples of high-risk behaviors to monitor:
- Clicking on malicious links or attachments in phishing emails
- Failing to report suspicious emails or incidents
- Reusing weak or compromised passwords
- Accessing sensitive data through unsecured devices or networks
- Ignoring software or security update notifications
How AI Adjusts Training Based on Risk Levels
Employees identified as high-risk are enrolled in more frequent, interactive training sessions using tools like the Quishing Simulator. This helps reinforce critical skills and reduce their susceptibility to threats. In contrast, low-risk users receive occasional refresher modules to maintain awareness without overwhelming them. As employee behaviors evolve, the AI dynamically updates both the content and frequency of training, ensuring that each user continues to receive the appropriate level of engagement.
You can benchmark employee risk levels using Phishing Risk Score Trend Across Industries.
Step 5: Work Mode & Security Risks
Employees don’t all work in the same environment. Office-based, remote, and hybrid work models each present different cybersecurity challenges that should be reflected in the training program.
What to do:
Identify how each team operates—whether they work from the office, remotely, or in a hybrid setup. Then, tailor the training content to address the specific risks tied to those environments.
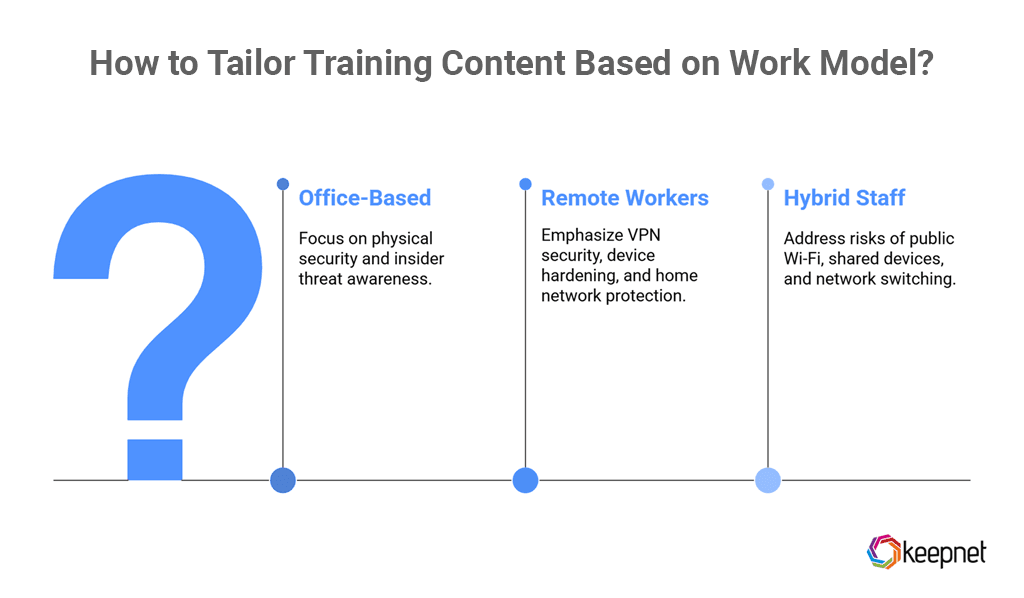
Work models and associated risks:
- Office-Based: Physical security issues, insider threats
- Remote Workers: VPN security, device hardening, home network exposure
- Hybrid Staff: Public Wi-Fi use, shared devices, network switching
Impact on Training
Assign targeted modules based on work mode. For example, remote staff can be trained using the Smishing Simulator or Vishing Simulator to raise awareness around non-email-based phishing attacks, which are common outside the traditional office setting.
For a detailed guide on securing employees in remote and hybrid setups, read Keepnet’s blog on How Can You Ensure Remote Work Security for Your Team?
Step 6: AI-Powered Personalization Based on Employee Profiles
Not all employees have the same technical background or experience level. To keep training relevant and effective, AI should adjust the content based on each user's skill level and time in the organization.
What to do:
Segment your workforce by technical proficiency—beginner, intermediate, expert—and by experience level, such as new hires versus long-term staff. Then, assign training paths that match their current knowledge and responsibilities.
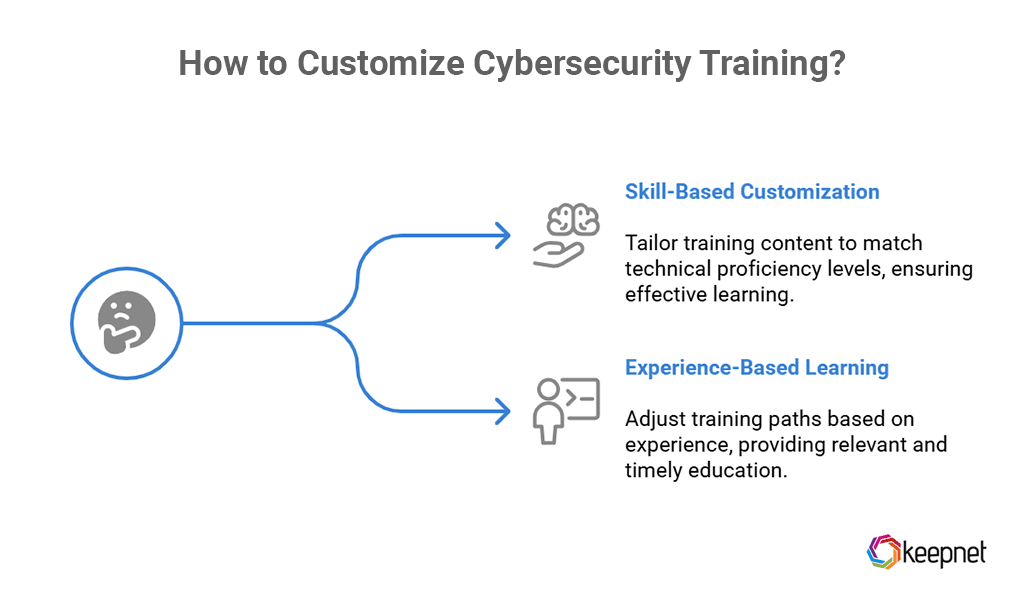
Skill-based customization:
- Beginners: Basic phishing recognition, secure password practices
- Intermediate users: Safe browsing, defending against social engineering
- Experts (e.g., IT teams): Malware analysis, red teaming, secure coding
Experience-based learning paths:
- New hires: Onboarding modules and a structured 30-day foundational plan
- Experienced employees: Periodic refresher courses tailored to previous performance
Impact on Training
Solutions like Security Awareness Training automatically adjust course difficulty, pacing, and content, ensuring each employee receives training suited to their level.
Step 7: Cultural & Personality-Based Adaptation
Employees process information differently based on their cultural background and personality traits. To boost training effectiveness, it’s important to adjust both tone and format to match how people learn and respond to security risks.
What to do:
Assess how your teams typically communicate, make decisions, and respond to authority. Then, tailor your training content to fit these patterns. You can also use behavioral data to align training with individual traits like risk tolerance or learning preference.
Culture-based adjustments:
- Structured, top-down modules work well in hierarchical cultures
- Collaborative exercises are more effective in peer-driven environments
Personality-based adjustments:
- Risk-takers benefit from gamified simulations and real-time challenges
- Analytical users prefer case studies and data-focused content
- Complacent users respond better to frequent nudges and behavioral cues
Impact on Training
Tools like the Email Threat Simulator and Threat Intelligence help deliver training aligned with employee behavior, making content more engaging and actionable.
To dive deeper into adapting training by region and culture, read What is Localization for Security Awareness Training
Step 8: Risky Security Behaviors & Nudging
Even with structured training in place, risky behaviors still occur. That’s where AI-powered nudging comes in—providing real-time prompts that help employees make better security decisions in the moment.
What to do:
Use AI tools to detect risky actions like clicking on phishing links, failing to report suspicious emails, using personal devices for work, or ignoring software updates. When such behavior is identified, send a timely nudge to steer the user toward a safer response.
Examples of corrective nudges:
- “You almost clicked a phishing link. Let’s review why it looked suspicious.”
- “Using personal devices? Make sure they’re encrypted.”
- “Report phishing to help protect your team.”
Examples of positive reinforcement:
- “You were the first to complete training this month, great job!”
- “Excellent work! Your phishing report helped stop a real threat.”
Impact on Training
Real-time nudging reinforces learning, encourages secure habits, and keeps employees engaged beyond scheduled training. Over time, this approach shifts your organization from a reactive posture to a proactive security culture.
For guidance on tailoring nudges to specific roles and risk levels, read Keepnet’s blog on Customizing Nudges for Specific Roles in Security Behavior and Culture Programs.
Building a Modern Security Awareness Program That Works
Traditional security awareness programs often fall short in today’s complex threat landscape. Instead of relying on static content and generic policies, organizations need a smarter, more adaptive approach.
An AI-powered, hyper-personalized program gives you the flexibility to:
- Match training to regional laws and industry regulations
- Assign role-specific content that reflects daily job risks
- Adjust learning paths based on behavior, culture, and personality
- Reinforce secure actions through real-time nudges and feedback
By tailoring training to your workforce and risk profile, you can drive long-term behavior change—and build a proactive security culture that protects your organization from the inside out.
Check this blog if you would like to create a generic security awareness training program.
Explore Keepnet’s Adaptive Security Awareness Training—a behavior-based program tailored to your team's needs, knowledge gaps, and risk level. Access 2,100+ materials in 36+ languages to build a security-aware culture across every department.
Editor’s Note: This article was updated on October 23, 2025.