What Is Elicitation in Cybersecurity? A Deep Dive into Subtle Conversations with Purpose
Elicitation is one of the most subtle yet dangerous social engineering tactics in cybersecurity. Through casual conversations, attackers can extract critical details without you even realizing it. In this post, we uncover how elicitation works, the psychology behind it, and the steps you can take to stay protected.
Picture yourself at a bustling networking event, casually chatting with someone who seems genuinely curious about your work. The exchange begins innocently—perhaps a comment about the venue or a compliment on your recent project. You relax, feeling at ease. Then comes an offhand question:
“So, are you guys still relying on that old firewall solution?”
Without a second thought, you respond—and just like that, you’ve unknowingly revealed sensitive details about your organization’s security posture.
This is elicitation in action. In cybersecurity, elicitation refers to the subtle art of extracting information through seemingly harmless conversation. It’s a powerful form of social engineering because it preys not on systems, but on people—the weakest link in the security chain.
And the numbers prove just how effective it is:
- 98% of cyberattacks rely on some form of social engineering rather than technical exploits (Source ).
- Over 95% of successful breaches begin with human error—often in the form of sharing information too freely (IBM Security).
- According to the SANS Institute, three out of four employees admit they have unintentionally shared sensitive information in casual conversations.
These statistics highlight why elicitation is such a formidable threat. Unlike phishing emails or malware, it doesn’t trigger alarms—it works by exploiting trust, curiosity, and social norms. In this blog, we’ll explore what elicitation is, why attackers use it, and what you can do to recognize and resist it.
Defining Elicitation: Conversation with Intent
Elicitation is the strategic, subtle extraction of information through conversation—so seamless that the target often doesn’t realize they’re being manipulated. It’s the art of drawing out valuable data while making the interaction feel completely natural.
- According to Ozan Ucar, CEO of Keepnet, elicitation is “a subtle social engineering tactic where an attacker carefully draws out sensitive information without raising suspicion.”
- The FBI also describes it as a technique to “collect information that is not readily available and do so without raising suspicion that specific facts are being sought.”
Elicitation happens across different formats—face-to-face chatter, phone conversations, even casual emails or small talk online. What matters is the art of steering the conversation, not forcefully grilling the target.
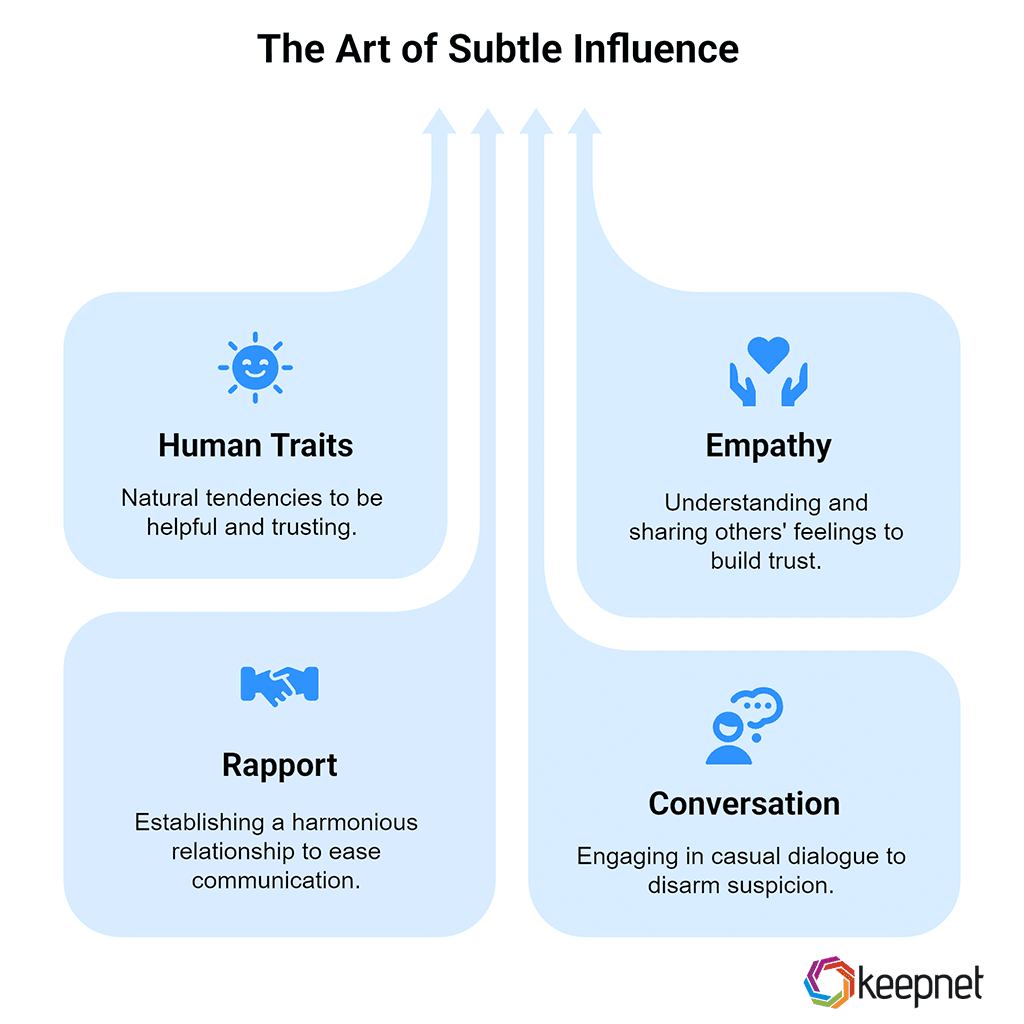
2. Why Elicitation Works: The Subtle Power of Social Psychology
Elicitation works because it taps into natural human traits, our tendency to be helpful, polite, trusting, and eager to share. It’s not force or trickery; it’s empathy, rapport, and conversation that disarm suspicion.
For instance, Onur Kolay, cybersecurity analyst at Keepnet, explains how people “underestimate the value of the information they share” and “assume that casual conversations are harmless.” Attackers exploit this by gently guiding the discussion to elicit revealing details—like company processes or personal data—without appearing malicious.
The approach is contrasted against direct questioning, which can immediately raise red flags. Elicitation feels like an innocent chat, even though it’s a calculated dance.
3. Tactics and Techniques Used in Elicitation: The Science of Subtlety
Let’s break down some of the most commonly used tactics in elicitation:
- Assumed Knowledge: The attacker pretends to already know a piece of information, prompting the target to confirm or correct. For example: “You still use [Product X], right?” This invites a correction—“No, we switched to Y”—thus revealing real systems.
- Bracketing: The attacker offers a broad estimate (“Your department’s budget must be between $500k and $2M”), prompting the target to clarify the actual figure.
- Quid Pro Quo / Confidential Baiting: The attacker pretends to share “insider” information to induce reciprocity: “I heard your competitor’s working on X—are you too?” The target often responds in kind.
- Deliberate False Statements / Denial of the Obvious: The attacker makes a blatantly wrong claim, hoping the target will correct them and inadvertently reveal the truth.
- Flattery: Compliments disarm targets, encouraging them to share more. It can trigger pride, admiration, or the desire to elaborate.
- Artificial Ignorance: Pretending ignorance (“I’m no cybersecurity expert—how do you guys do secure remote work?”) encourages the target to “teach,” leading them to reveal details.
- Other conversational tools: Active listening, leading/open-ended questions, humor, empathy, and body language can also enhance rapport and facilitate elicitation.
These techniques are not new—they’ve been used for years in espionage, intelligence, and corporate intelligence.
Who’s Vulnerable Elicitation—and When?
Nearly anyone can be a target of elicitation: employees at work, parents picking up their kids, conference attendees, or chatty colleagues. But some situations increase vulnerability:
- Insider knowledge or security clearance: Those with access to sensitive systems or classified info are especially valuable.
- Periods of transition or stress: Organizational change, employee turnover, or financial hardship can make individuals more talkative or careless, especially on platforms like LinkedIn or professional forums.
- Social networks & gaming platforms: Casual interactions—like in-game chat or supposedly low-risk social forums—can become vectors for elicitation.
- High social trust environments: Events like industry mixers or workshops foster a trusting atmosphere that attackers exploit.
According to Keepnet, 71% of new employees fall for social engineering attacks that also include elicitation techniques.
Real-World Impacts: Why It Matters in Cybersecurity
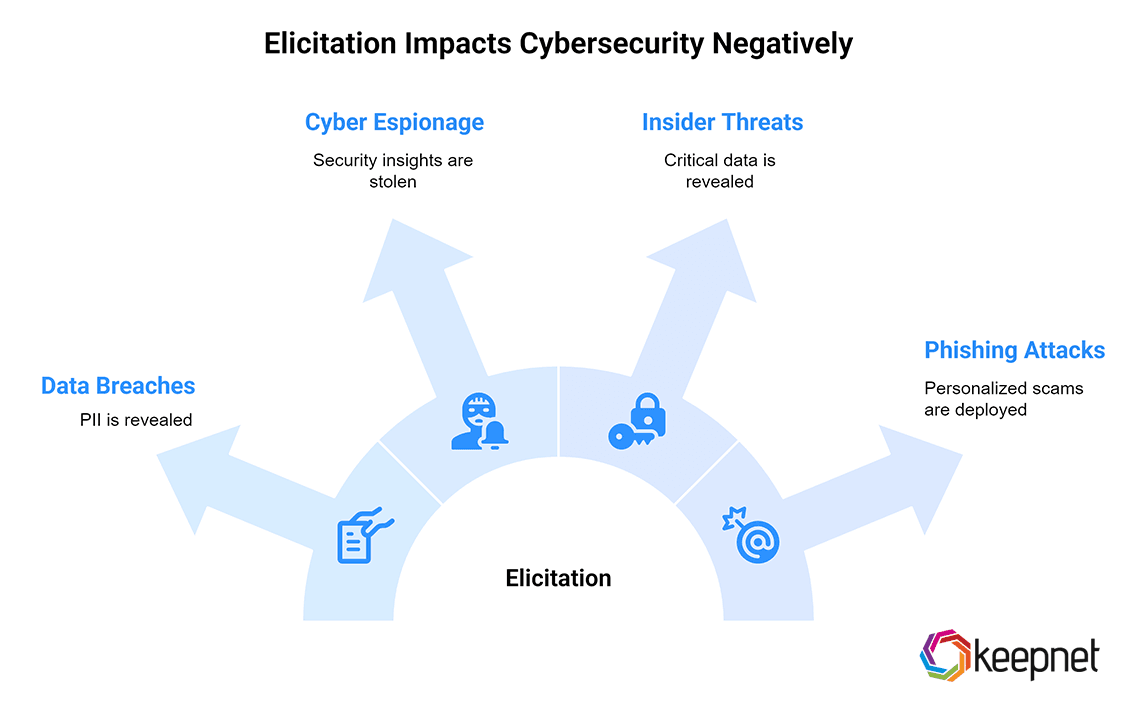
Elicitation is more than small talk—it can lead to:
- Data breaches: Revealing PII (names, birthdays, job roles) helps attackers impersonate victims or bypass authentication.
- Cyber espionage: Insights into security tools, vendor choices, or project roadmaps can be used to craft targeted attacks or steal competitive advantage.
- Insider threats: Recruited or coerced insiders can be led to reveal critical data via elicitation.
- Customized phishing/social engineering: Elicited details fuel threateningly personalized scams or spear-phishing campaigns.
Elicitation is especially dangerous because it’s low-tech and human-centered—hard for security systems to detect and easy to deploy.
Ethical Elicitation: When Conversation Is Constructive
Elicitation isn’t inherently malicious. Ethical professionals—in user research, penetration testing, or hiring—also use it ethically:
- Set clear goals: Know what info you need and be transparent about the context.
- Build rapport appropriately: Use pretext or role-play honestly—e.g., testers pretending to be HR in simulated vishing exercises.
- Ensure no one feels deceived: Ethical elicitation leaves participants feeling positive, not manipulated.
Ethical elicitation has its place, but only within well-defined, consensual frameworks.
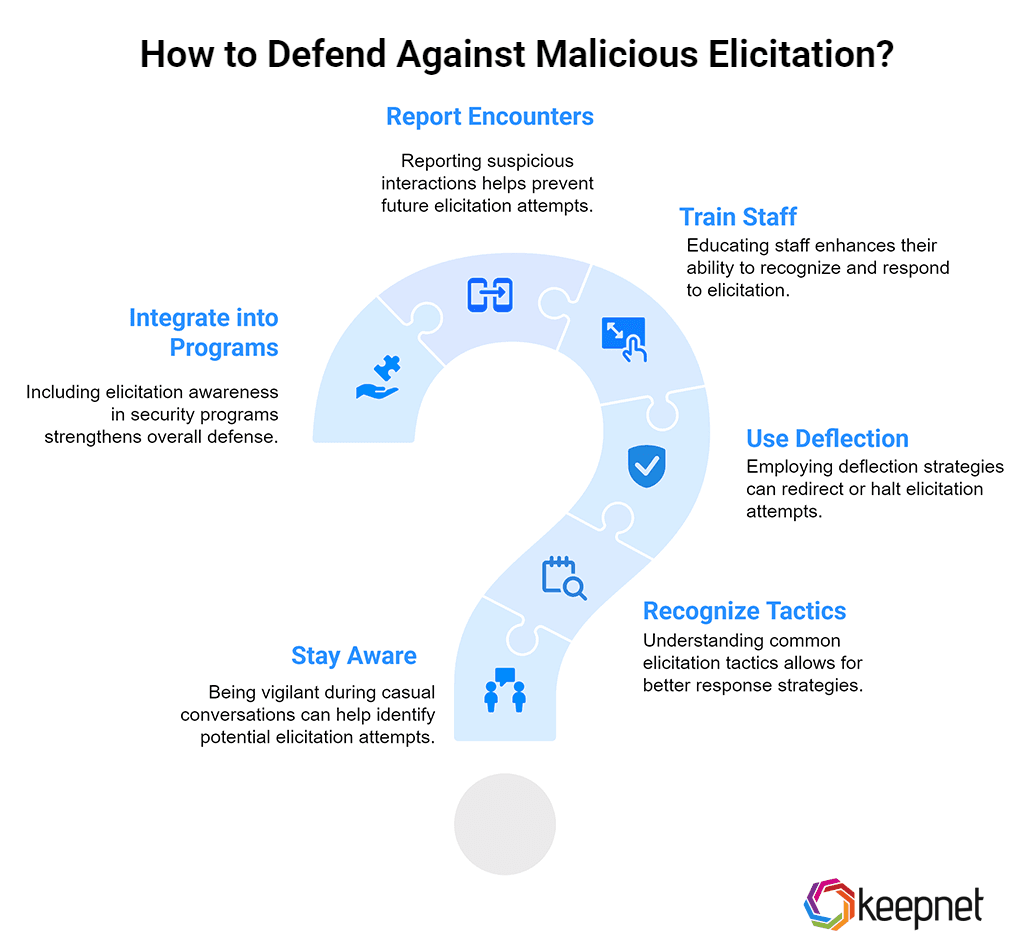
How to Defend Against Malicious Elicitation
Here’s how you can protect yourself and your organization:
- Stay aware, especially during casual conversations. Pause when you feel “too comfortable” around strangers asking seemingly innocent questions.
- Recognize common tactics: Assumed knowledge, bracketing, false statements—question them before responding.
- Use deflection strategies:
- Change the subject or answer vaguely (“That’s not something I’m sure about”).
- Ask back: “Why do you ask?”
- State limitations: “I’d need to check with my supervisor.”
- Refer to public sources instead of volunteering specifics.
- Train staff to identify and respond to elicitation attempts, especially in high-risk roles or during company transitions.
- Report suspicious encounters, even on platforms like LinkedIn—something that fewer than half of targets currently do.
- Integrate into security programs: Elicitation awareness should be part of social engineering and insider-threat mitigation training.
Summary
Elicitation = the art of subtly extracting confidential or sensitive information via conversation that seems innocent.
Effectiveness stems from:
- Leveraging human trust, rapport, and psychology.
- Being low-tech and hard to detect.
Common techniques:
- Assumed knowledge, bracketing, flattery, false statements, artificial ignorance, quid pro quo.
Defensive steps:
- Awareness, conversation strategies, training, reporting, and organizational vigilance.
Elicitation is a powerful tool—capable of swinging conversations in silent, damaging directions. But with awareness, training, and skepticism, both individuals and organizations can hold the line.
How Keepnet Helps Against Elicitation Attacks
Elicitation thrives in silence and subtlety — which is why awareness and resilience are the strongest defenses. Keepnet Human Risk Management Platform equips organizations to counter these hidden threats through a multi-layered approach:
- Security Awareness Training: Engaging, scenario-based modules teach employees how elicitation works, what subtle conversational traps look like, and how to deflect without raising suspicion.
- Phishing & Vishing Simulations: Realistic simulations, including phone-based elicitation simulations, allow employees to experience these tactics in a safe environment — making them more likely to recognize and resist them in the real world.
- Instant Training Nudges: If someone falls for a simulated elicitation attempt, Keepnet delivers immediate, bite-sized learning moments to reinforce the lesson while the experience is fresh.
- Behavioral Analytics & Reporting: Organizations gain visibility into who is most vulnerable to elicitation, track progress over time, and take proactive steps to reduce human risk.
By embedding elicitation awareness into everyday training and security culture, Keepnet helps organizations move from reactive defense to proactive resilience.
References
- FBI’s official description: social-engineer.org & FBI
- Elicitation techniques breakdown: TestPros (2020)
- Three top techniques: Hackcontrol blog
- Physical/strategic risks and insider vulnerability (BTAC, Mar 2025)
- Ethical elicitation guidance: Social-Engineer.com (Mar 2025)
- Defense strategies: Security Through Education & Valkyrie cybersecurity blog
Editor’s note: This blog was updated December 1, 2025