Human Error in Cybersecurity (2026): Causes, Verified Statistics & How to Reduce Risk
Human error remains the top cause of data breaches in 2026. Discover how mistakes like clicking phishing emails and weak passwords expose organizations—and how to reduce this risk.
Human error in cybersecurity means unintentional actions (or skipped steps) that expose systems and data—like clicking a phishing link, reusing passwords, or misconfiguring cloud access.
In 2026, attackers increasingly design campaigns around human behavior (urgency, trust, fatigue), so “people risk” must be managed like any other control—measured, trained, and continuously improved.
Human error in cybersecurity is any unintentional action (or skipped step) that creates an opening for attackers—like clicking a phishing link, reusing passwords, misconfiguring cloud access, or sharing sensitive data with the wrong person. In practice, most “successful breaches” are not purely technical failures; they happen when human behavior, process gaps, and security controls collide.
That’s why leading breach research consistently treats the human element as a major driver of real-world incidents. Verizon’s 2025 Data Breach Investigations Report (DBIR) reports that the human element was a component of 60% of breaches (using a definition designed to better reflect what security awareness and behavior can influence).
And in Verizon’s 2025 DBIR coverage, human involvement remains high—often showing up through a strong overlap between social engineering and credential abuse.
In 2026, security leaders increasingly frame this as a risk-management problem, not just a training problem. Mimecast’s State of Human Risk 2025 describes addressing human risk as an overwhelming priority, emphasizing that many incidents persist “mostly due to human error” even as organizations invest heavily in tools.
Meanwhile, Proofpoint’s 2024 Voice of the CISO findings show that nearly three-quarters of CISOs (74%) identify human error as the most significant vulnerability, reinforcing that “people risk” remains central to breach prevention strategies.
What Is Human Error in Cybersecurity?
Human error occurs when individuals unintentionally make decisions or take actions that result in a security breach. This can be as simple as using a weak password or clicking on a phishing email. These mistakes may seem minor, but they can have a serious impact, putting an entire organization’s data at risk.
With numerous digital tools and platforms available today, employees are often overwhelmed by the number of passwords they must manage and the security protocols they need to follow. This increases the likelihood of making mistakes, such as forgetting to update software or incorrectly configuring security settings.
How Human Mistakes Turn Into Real Breaches (Business Impact)
Human error rarely causes a breach on its own. What usually happens is simple: one small mistake creates an opening, and attackers use that opening to move deeper, steal credentials, or access sensitive data. When you understand the most common “impact paths,” you can design better controls, training, and verification steps—without blaming employees.
Common impact paths (how a mistake becomes a breach)
1) Phishing click → credential theft → account takeover → data exfiltration
An employee clicks a convincing link, enters credentials, or approves a fake MFA prompt. Attackers then log in as a legitimate user, escalate access, and export data quietly—often without triggering alarms.
2) Misdelivery → accidental exposure
A file is shared with the wrong external recipient, a sensitive attachment is sent to “John.Smith@…” instead of “John.Smyth@…”, or a public link is used instead of a restricted one. These incidents are “simple,” but the impact can be severe because data is already outside your control.
3) Misconfiguration → public access to internal data
A cloud storage bucket, collaboration workspace, or admin setting is left open by mistake. Attackers don’t need to “hack” anything; they just find what is exposed and download it.
4) Weak passwords / reuse → credential stuffing → lateral movement
If employees reuse passwords across services, attackers can use leaked credentials from unrelated breaches. Once inside one system, they move laterally to higher-value apps (email, HR, finance, admin consoles).
5) Social engineering on help desk → bypassed verification → privileged access
Under pressure (urgency, authority, empathy), support teams may skip steps. If verification fails, attackers can reset passwords, enroll new MFA methods, or change recovery options.
What this costs the business (beyond “security”)
Human-error-driven incidents often lead to:
- Downtime and productivity loss: IT and security teams shift into incident mode, systems are locked down, and business workflows slow down.
- Regulatory and legal exposure: notifications, audits, contractual penalties, and potential fines, especially when personal data is involved.
- Financial loss: ransomware payments, fraud/wire transfers, recovery services, and increased insurance premiums.
- Reputational damage: customers lose trust, partners demand proof of controls, and future sales cycles become harder.
Key takeaway
Reduce the number of “human opportunities,” and you reduce breach probability.
The goal isn’t perfect people—it’s a safer system: clear processes, strong verification, secure defaults, and training that matches real attack tactics.
Why Does Human Error Happen?
Human error in cybersecurity isn’t just about carelessness. It usually stems from a few key factors. One of the biggest reasons is pressure and distractions. Tight deadlines, multiple tasks, or constant notifications can easily lead to someone overlooking critical security steps. Another big factor is a lack of awareness. Many employees aren’t trained well enough to spot phishing emails or understand the importance of basic security practices. Decision-based errors also play a role, where someone makes a mistake based on incomplete or incorrect information. For instance, an employee might delay an important software update, not realizing how critical it is, or fall for a well-disguised phishing scam.
Common Examples of Human Error in Cybersecurity
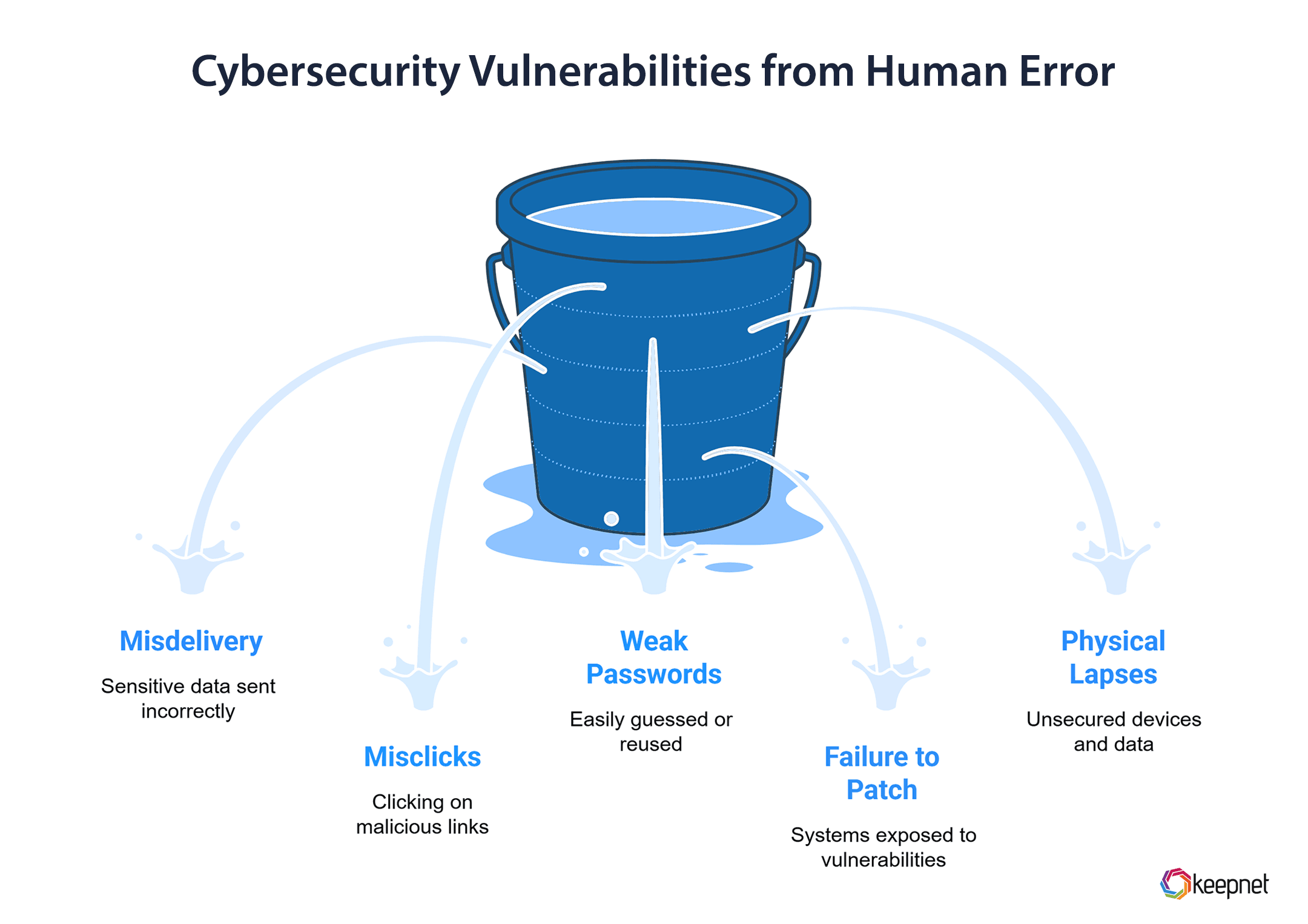
Here are some of the most common ways human error shows up in cybersecurity:
- Misdelivery: This happens when sensitive information is accidentally sent to the wrong person, like emailing a confidential document to an unintended recipient.
- Misclicks: Clicking on a malicious link in an email or downloading a harmful attachment is a common mistake, often made when employees are rushed.
- Weak Passwords: Using easily guessable passwords, reusing the same password for multiple accounts, or storing passwords insecurely are all examples of password-related human errors.
- Failure to Patch: Many breaches occur because employees or IT teams don’t install critical security updates in time, leaving systems exposed to vulnerabilities.
- Physical Security Lapses: Leaving devices unlocked or unattended, or failing to securely store physical copies of sensitive data, can also lead to breaches.
Human Error Types in Cybersecurity
Human error is a critical vulnerability in cybersecurity, but not all mistakes are the same. By categorizing errors into skill-based (routine slips) and decision-based (judgment lapses), and knowledge-based human errors organizations can tailor strategies to address root causes. Let’s break down the types of human error:
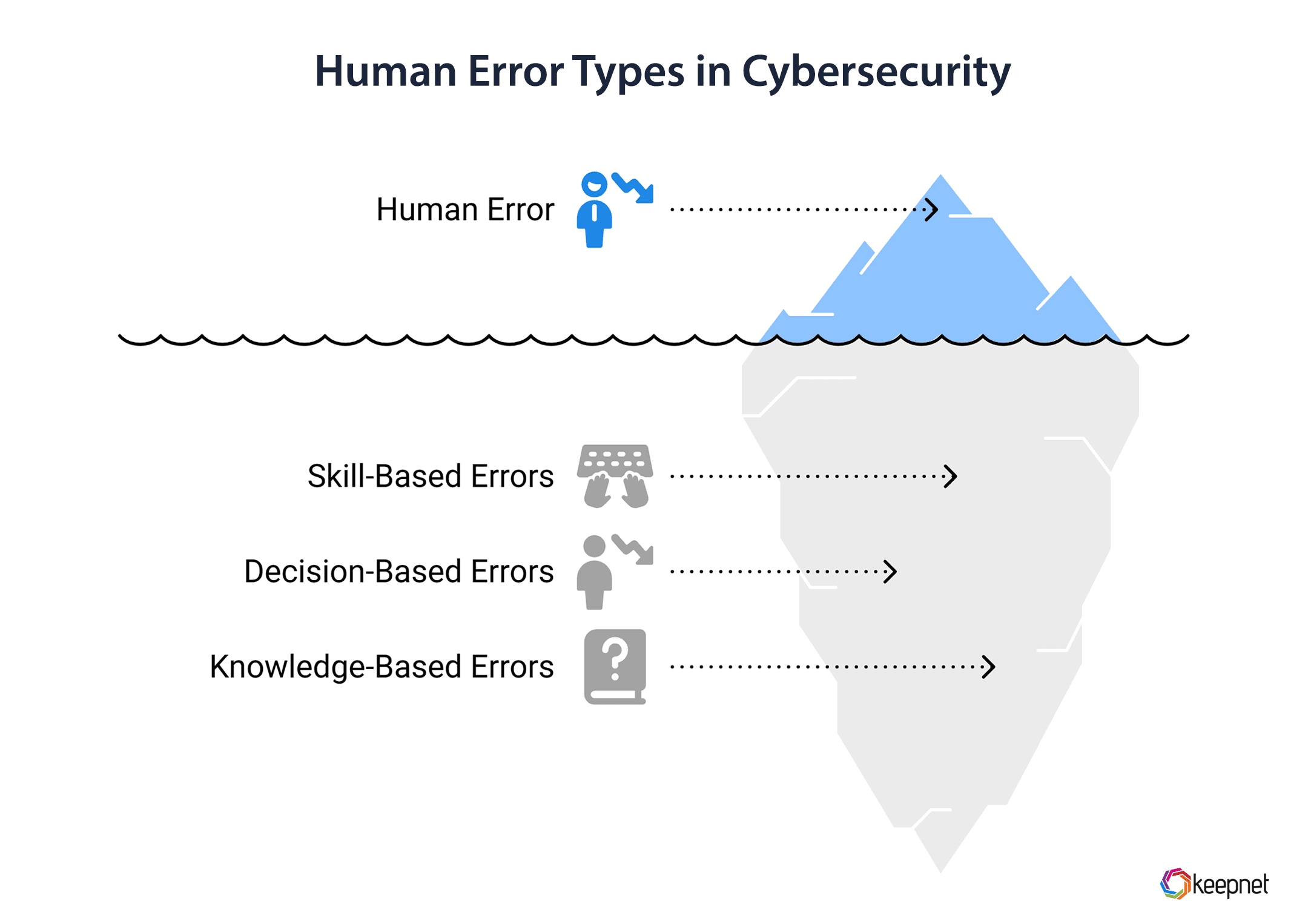
1. Skill-Based Errors: The "Oops" Moments
These occur during routine tasks, often due to distraction, fatigue, or haste. Even trained individuals make these mistakes.
Examples:
- Accidental Data Exposure: Sending sensitive files to the wrong email recipient or uploading data to public cloud storage
- Physical Security Lapses: Leaving devices unlocked in public spaces or misplacing unencrypted USB drives.
- Misconfigurations: Overlooking security settings (e.g., leaving cloud storage “public” due to rushed setup).
- Typos in Critical Fields: Mistyping a URL and landing on a phishing site.
Mitigation Strategies of Skill-Based Human Errors:
- Automate Repetitive Tasks: Use tools to auto-patch software, encrypt data, or verify email recipients.
- Checklists & Double-Checks: Implement protocols for configuring systems or sharing sensitive data.
- Physical Safeguards: Require auto-lock features on devices and secure disposal of hardware.
2. Decision-Based Errors: The "I Thought It Was Fine" Mistakes
These stem from poor judgment, lack of awareness, or cognitive biases. They often reflect gaps in knowledge or training. Examples:
- Falling for Phishing/Social Engineering Attack: Clicking malicious links or sharing credentials due to urgency or trust.
- Weak/Reused Passwords: Prioritizing convenience over security.
- Ignoring Updates: Delaying patches because “it’s not urgent.”
- Bypassing Security Protocols: Disabling multi-factor authentication (MFA) for convenience.
Mitigation Strategies:
- Targeted Awareness Training: Simulate phishing attacks and teach employees to recognize red flags (e.g., urgency, mismatched URLs).
- Enforce Policies: Mandate MFA, password managers, and least-privilege access.
- Cultivate Security Culture: Reward proactive behavior (e.g., reporting suspicious emails).
3. Knowledge-Based Errors: The "I Didn’t Know" Factor
These occur when individuals lack the expertise to handle complex or unfamiliar scenarios. Examples:
- Misconfiguring firewalls due to unfamiliarity with tools.
- Failing to recognize novel attack vectors (e.g., zero-day exploits).
Mitigation:
- Continuous Learning: Provide advanced training for IT teams.
- Expert Support: Partner with cybersecurity consultants for audits and guidance.
2026 Human Error in Cybersecurity: What the Data Really Says (with sources)
Before you compare “human error” numbers, one caution: reports define the human factor differently (e.g., whether malicious insiders are included, whether credential abuse is counted, and how “error” is categorized). Verizon even revised its “human element” calculation to remove malicious privilege misuse so the metric better reflects what awareness and behavior change can influence.
The human element still drives most breaches (and it’s consistent year to year)
- Verizon DBIR 2024: The human element was a component of 68% of breaches (using the revised definition).
- Verizon DBIR 2025: Human involvement remained roughly the same, hovering around 60%.
- Verizon also notes that human-driven breaches often involve credential abuse and social actions (like phishing)—the “people layer” and the “identity layer” are tightly linked.
“Errors” are a major breach pattern—not a rare edge case
Verizon reports breaches involving Errors reached 28% in 2024, noting that errors may be more prevalent than incident-response narratives typically suggest (because broader breach-notification contributors reveal more of these cases).
CISOs still rank human error as the #1 security weakness
In Proofpoint’s global survey of CISOs, 74% identified human error as their organization’s most significant vulnerability—and many also flagged negligent employees as a key concern over the next two years.
Why “human error” keeps showing up: fatigue, distraction, and executive impersonation
Research on workplace mistakes consistently ties risky actions to cognitive load and fatigue—especially under pressure and in hybrid work. Tessian’s Psychology of Human Error report found:
- 52% of employees said they fell for a phishing email where the attacker impersonated a senior executive (up from 41% previously reported).
- 40% admitted sending a work email to the wrong person in the last 12 months.
- 36% believed they made a mistake at work that compromised security in the last 12 months.
2026 trendline: “human risk” is expanding beyond email
Mimecast’s 2025 reporting emphasizes that human risk has surpassed technology gaps as the biggest cybersecurity challenge—and highlights growing concern around collaboration tools, with many organizations expecting the risk (and impact) to continue.
Additional Facts and Statistics on Human Error in Cybersecurity
Let's dive into statistics, trends and facts on human error in information security 2026:
- 95% of cybersecurity issues involve a human element.
- 26% of employees fell for a phishing email at work.
- 17% of employees accidentally emailed the wrong external party.
- 49% of breaches were due to personal information being sent to the wrong recipient.
- 33% of breaches involved accidental disclosure or publication of personal data.
- 6% of breaches were due to not using BCC in emails.
- 5% of breaches were from misplacing paperwork or storage devices.
- 5% of breaches were from unauthorized verbal disclosures.
- 51% of employees made security mistakes when tired.
- 50% of employees made security mistakes when distracted.
- 50% of misdirected emails were due to pressure to send emails quickly.
- 49% of misdirected emails were due to not paying attention.
- 47% of misdirected emails were due to distraction.
- 42% of misdirected emails were due to fatigue.
- 54% of employees fell for phishing scams because they perceived the email as legitimate. .
- 29% of companies lost a customer or client due to a misdirected email.
- 21% of employees lost their jobs after sending data to the wrong person.
- 35% of employees had to notify customers about data loss due to misdirected emails.
- 44% of employees sent apology emails for data loss incidents caused by misdirected emails.
- 21% of employees did not inform their IT team about email security mistakes.
- 31% of cloud data breaches were attributed to misconfiguration or human error.
- 22% of organizations regarded human error as their topmost concerning threat in 2024.
- 43% of breaches were due to insider threats (both accidental and intentional).
Major Data Breaches Caused by Human Error in 2025
Human error has been responsible for some of the biggest data breaches in recent years. Here are a few high-profile examples of human error that caused data breaches:
PowerSchool Data Breach
- Date: January 2025
- Details: PowerSchool, an edtech company serving over 18,000 schools, experienced a breach when hackers accessed its customer support portal using a single compromised credential. This was likely due to phishing or poor password practices by an employee.
- Impact: Over 62 million students and 9.5 million teachers were affected, with personal data exposed across North America and the UK.
Ubiquiti Networks (Business Email Compromise / executive impersonation)
- Date: 2015 (still a classic “human-process” failure pattern)
- Details: attackers impersonated employees/executives and induced fraudulent wire transfers totaling $46.7M (documented in an SEC filing).
- Why it matters in 2026: the same pattern is now amplified by AI-written lures and voice deepfakes.
Bankers Cooperative Group, Inc. Breach
- Date: Reported January 14, 2025 (attack in August 2024)
- Details: Hackers accessed sensitive customer information through an employee’s email account at Bankers Cooperative Group, Inc., likely via phishing or weak password security.
- Impact: The number of affected individuals is unspecified, but the breach’s significance is noted in financial sector reports.
How Keepnet Helps Reduce Human Error
Human error is predictable. People get rushed, distracted, or socially engineered—especially when attackers combine urgency, authority, and multi-channel lures. The practical goal isn’t “perfect employees.” It’s a repeatable system that helps people make safer decisions in the moment and proves improvement over time.
1) Test real behavior with multi-channel simulations (not theory)
Keepnet helps you uncover where human risk is actually happening by running multichannel phishing simulations across today’s most common social-engineering pathways—smishing (SMS), vishing (voice), quishing (QR), MFA fatigue, callback lures, and deepfake-driven impersonation scenarios.
This approach is designed to measure the real behaviors that lead to breaches (clicking, scanning, replying, sharing codes)—not just course completion.
2) Train with targeted, engaging learning (not one-size-fits-all)
Instead of pushing generic “annual training,” Keepnet supports adaptive security awareness training and engagement techniques like gamification and mobile/SMS delivery to improve participation and retention.
Over time, organizations aim to reduce risky actions through repeated practice, feedback, and reinforcement—results vary by baseline risk, training frequency, and enforcement.
3) Measure improvement with risk scoring and outcome-driven reports
To prove progress, Keepnet provides reporting that explains how key metrics are calculated (including Human Cyber Risk Score and Phishing Risk Score) across simulation types—email phishing, smishing, quishing, vishing, and callback phishing—so you can identify high-risk roles, track trends, and prioritize interventions.
This is critical for CISOs because it turns “awareness” into measurable risk reduction.
4) Close the loop with phishing reporting and faster response
Human error doesn’t stop at prevention—employees also need an easy way to report suspicious content, and security teams need a fast path from report → analysis → action. Keepnet supports phishing incident response workflows and automated analysis capabilities that help teams investigate reported threats more efficiently.
5) Backed by real deployments and external recognition
Keepnet publishes customer stories and case studies showing how organizations improve simulation accuracy and reduce human cyber risk through platform changes and program design.
In addition, Keepnet has been named a go-to vendor for stopping deepfake and AI disinformation attacks by Gartner (noting Gartner’s AI disinformation guidance and the need for behavior-based interventions).
Bottom line: Keepnet is built to help you test → train → measure → respond, so you can reduce employee-driven risk with evidence—not assumptions.
Editor's Note: This article was updated on January 1, 2026.