What is Role-Based Security Awareness Training, and How Can It Be Customized and Adapted?
With cyber risks up in 2025, businesses need smarter solutions. Learn how role-based security training delivers 30% better results than general programs—reducing risks by 45%, improving compliance, and strengthening defenses.
A one-size-fits-all approach to security awareness training is no longer effective as cyber threats evolve. Research shows that role-specific awareness programs are 30% more effective than general programs (DergiPark, 2023). Generic training often fails to address the unique threats faced by different professions, limiting its effectiveness in real-world scenarios.
Additionally, organizations that invest in role-based security awareness training (RBSAT) see measurable improvements. For example, tailored programs have helped reduce data breaches by up to 45% in certain industries and increased compliance rates, proving that customized training is effective and cost-efficient.
This blog explores Role-Based Security Awareness Training’s benefits, customization strategies, and best practices for effective implementation, showing how tailored programs lead to stronger defenses and smarter cybersecurity practices.
What is Role Based Cyber Security Awareness Training?
Role-based security awareness training is a program that teaches each employee the risks and safe behaviors tied to their job. Finance learns invoice and payment fraud; developers, secure coding and secrets handling; HR, PII and phishing; IT, privileged access and MFA abuse; leaders, policy and risk decisions. Content is short, practical, and job-relevant, using targeted simulations, microlearning, and checklists to turn guidance into daily habits.
To put it in place, map business processes to risks, group staff by role, set clear learning paths, run realistic tests, and track role-level KPIs like click rate, report rate, and policy exceptions. Update modules as roles, tools, and threats change so training stays useful, measurable, and compliant—and reduces risk where it matters most.
Why is Role-Based Security Awareness Training Important?
Different employees encounter different cybersecurity threats. A finance team member is likely to face business email compromise (BEC) scams, while an executive is a prime target for whaling attacks. Legal professionals must protect confidential client data, and IT personnel must be aware of credential-stuffing attacks. Role-Based Security Awareness Training (RBSAT) ensures each team member receives relevant, impactful training that strengthens the organization's defense.
Organizations with effective security awareness training programs are 8.3 times less likely to appear on public data breach lists annually compared to general statistics. This highlights the importance of customized training, allowing different professional groups to take better precautions against specific threats.
Role-based security awareness training is essential because different job roles face unique cybersecurity risks. Tailoring training to specific roles improves both awareness and response, leading to better protection against cyber threats.
Real-world examples highlight advantage of implementing role based security awareness training various industries:
- Role-based security awareness training tailored to cultural contexts achieves 40% higher participation rates than general programs.
- Using role-specific, culturally relevant scenarios increases engagement and retention. Security training delivered by CEOs raised compliance rates by 25%, showing the impact of culture and leadership’s role in security (Kazdal & Rakipoglu, 2020). This demonstrates that in environments where hierarchical communication is prevalent, cybersecurity training led by senior executives has a greater impact.
- In Scandinavian countries, interactive workshops where employees shared role-specific security challenges improved knowledge retention by 20% (Gentontop, 2023).
- Language adaptation including role-specific terminology and culturally relevant expressions, increasing awareness by 30% (Linguistic Adaptation Journal, 2022).
- Cross-cultural teams developing role-based training ensure that content respects and integrates cultural nuances, boosting engagement and compliance. Gamified, role-based cybersecurity program increased global participation rates by 30%, by customizing challenges to regional threats relevant to specific roles. (Netexpat, 2024)
These results demonstrate that customizing cybersecurity training to each profession’s needs helps organizations reduce data breaches, safeguard sensitive information, and build a stronger security culture.
Targeted Cyber Threats: Why Role Specific Cybersecurity Awareness Matters
Different professions face unique cybersecurity threats. Below are key job roles and the cyber threats they face, emphasizing the importance of customized security training in mitigating these risks.
- Accountants and Finance Professionals face phishing attacks and fraudulent transactions. Cybercriminals use fake emails to steal credentials and initiate unauthorized transactions. According to PwC, financial institutions are over 30% more likely to be targeted by cyberattacks than other companies.
- Academics and researchers are prime targets for intellectual property theft and phishing scams. Cybercriminals target universities because they store large amounts of personal and research data, making them valuable targets. In 2023, 85% of UK higher education institutions reported experiencing breaches or attacks (gov.uk).
- Engineers and technical staff face cyber espionage and malware threats. In 2023, a Tesla data breach caused by two former employees leaked sensitive engineering data, impacting over 75,000 individuals (The Verge). Security awareness training is essential, as 90% of data breaches are caused by human error—a risk that can be significantly reduced with proper training.
- Legal professionals handle sensitive client data, making them prime targets for cyberattacks and social engineering scams. A Solicitors Regulation Authority (SRA) report found that 75% of law firms have been targeted, with £4 million stolen in 23 cases (Cyber Resillience Center). Strong security awareness training is crucial to safeguarding legal documents and client funds.
- Journalists and media workers are frequently targeted for surveillance and misinformation attacks. Investigations have revealed that Pegasus spyware has been used to monitor the communications of over 180 journalists across 20 countries, highlighting the pervasive threat to press freedom (CPJ).
- Healthcare workers handle sensitive medical data, making them prime targets for ransomware attacks and data breaches. In 2024, 67% of healthcare organizations experienced ransomware attacks—the highest rate in four years (Statista). Security awareness training plays a crucial role in reducing these risks by helping staff identify phishing attempts, follow data protection protocols, and respond effectively to cyber threats, ultimately strengthening the healthcare sector’s defenses.
Key Benefits of Role Based Security Awareness Training
Role-Based Security Awareness Training ensures employees receive targeted, relevant training, improving both security resilience and business continuity. Below are the key business and security benefits of implementing RBSAT in your organization.
Business Benefits
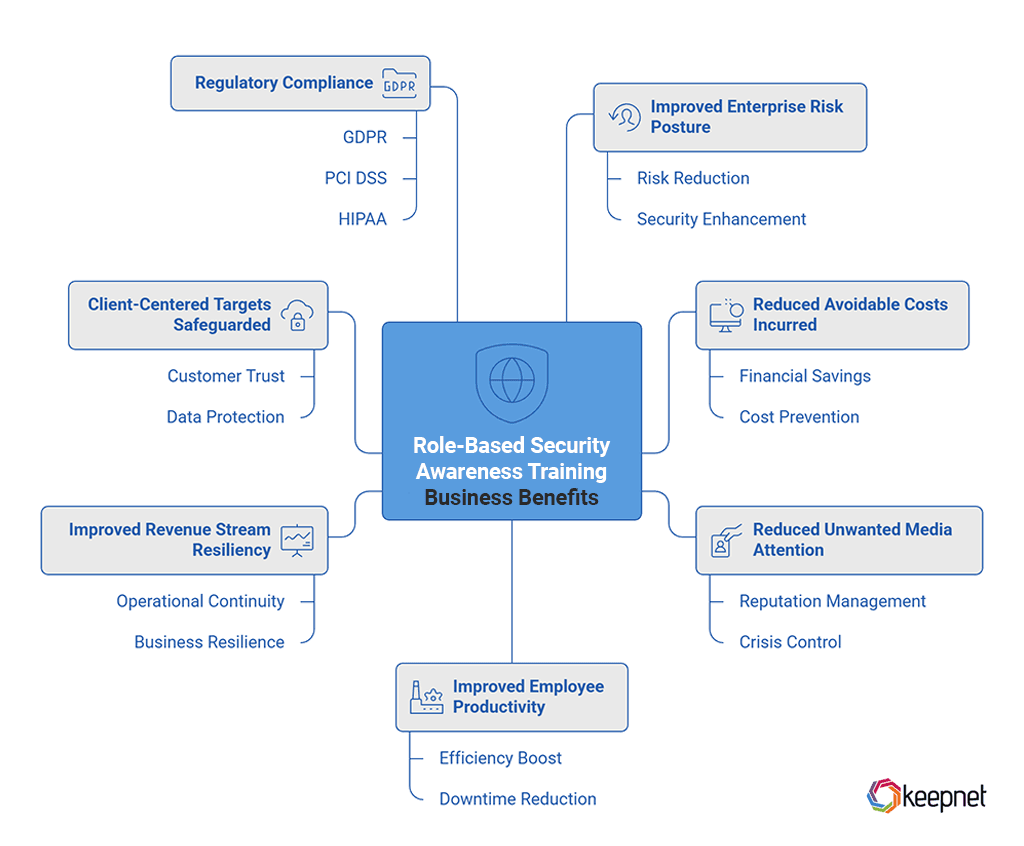
Implementing Role-Based Security Awareness Training not only strengthens cybersecurity but also helps businesses reduce costs, protect their reputation, and ensure operational continuity. Key benefits include:
- Improved Enterprise Risk Posture – Reduces human-related security risks.
- Reduced Avoidable Costs Incurred – Prevents financial losses from cyber attacks.
- Reduced Unwanted Media Attention – Helps mitigate reputation damage from security breaches.
- Improved Employee Productivity – Minimizes downtime caused by security incidents.
- Improved Revenue Stream Resiliency – Ensures critical business operations remain unaffected by cyber threats.
- Client-Centered Targets Safeguarded – Enhances customer trust by securing their data.
- Regulatory Compliance – Helps meet industry regulations like GDPR, PCI DSS, and HIPAA.
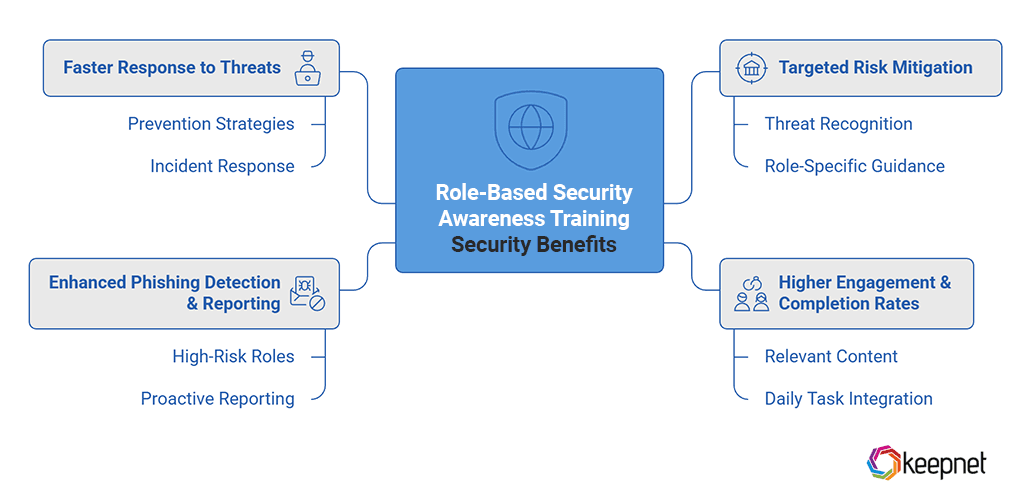
Security Benefits
A role-based approach to security training ensures employees receive relevant guidance on the threats they face daily. This not only improves threat recognition but also enhances overall organizational resilience. Key benefits include:
- Targeted Risk Mitigation – Employees learn to recognize threats specific to their roles.
- Higher Engagement & Training Completion Rates – Employees engage more with training tailored to their daily tasks.
- Enhanced Phishing Detection & Reporting – Employees in high-risk roles become proactive in reporting suspicious activity.
- Faster Response to Threats – Employees understand their role in preventing and responding to cyber incidents.
Why Does Customization in Security Awareness Training Lead to Higher Engagement?
Security training for employees is most effective when it aligns with employees' daily tasks. When training feels relevant, employees engage more and retain information better. Job-specific scenarios make learning more impactful. For example:
- Healthcare workers respond better to scenarios about patient data breaches.
- Finance teams benefit more from phishing simulations on invoice fraud.
A National Institute of Standards and Technology (NIST) study found that segmented phishing training reduces successful attacks by 38%, compared to 16% with generic training. This proves that customized security training significantly enhances threat recognition and response.
For deeper insights, read Why CISOs Need Segmentation for a Security Behavior and Culture Program.
What Are Keepnet's Role Based Security Awareness Training?
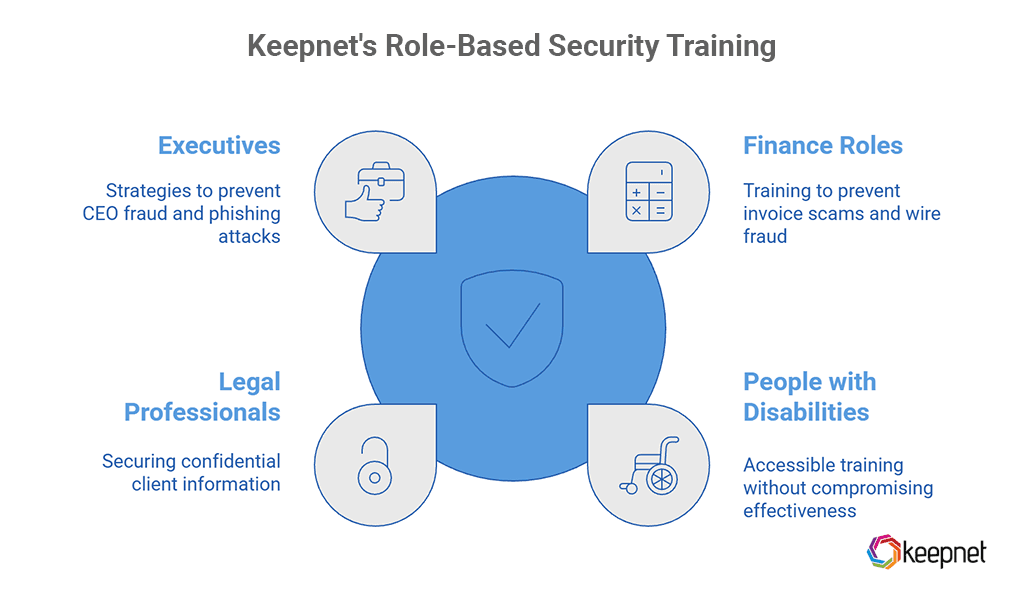
Different job roles face unique cybersecurity threats, requiring specialized training to address their specific risks. Keepnet offers targeted security awareness training designed to equip employees with the knowledge and skills needed to defend against the threats they encounter daily. Below are some key role-based training programs offered by Keepnet:
- Security Awareness for Finance Roles – Teaches financial teams to spot and prevent invoice scams and wire fraud.
- Security Awareness Training for People with Disabilities – Ensures accessible security training without compromising effectiveness.
- Security Awareness Training for Legal Professionals – Helps lawyers and legal teams secure confidential client information.
- Security Awareness Training for Executives – Equips leaders with strategies to prevent CEO fraud and targeted phishing attacks.
What Are the Best Methods for Customizing and Adapting Security Awareness Training for Different Roles?
To build an effective, role-based security awareness training program, organizations should implement the following strategies:
- Identify Job-Specific Cyber Threats – Conduct a detailed risk assessment to determine the most relevant threats for each role, ensuring training addresses real-world risks employees face daily.
- Use Targeted Training Materials – Develop customized content, including interactive exercises, case studies, and industry-specific attack scenarios, to enhance engagement and improve retention.
- Implement Hands-On Simulations – Regularly test employees with phishing, social engineering, and ransomware simulations across multiple attack vectors like email, SMS phishing, voice call phishing , QR phishing, and MFA-phishing threats to build practical defense skills.
- Adapt Training Based on Threat Intelligence – Continuously update training modules based on emerging cyber threats, ensuring employees stay prepared for evolving attack tactics.
- Measure Effectiveness and Reinforce Learning – Track training completion rates, phishing simulation results, and employee feedback to refine the program and strengthen long-term security awareness.
To maximize the effectiveness of security awareness training, it should be combined with a phishing simulator to provide employees with real-world attack scenarios. Learn more about this approach in The Role of Adaptive Phishing Simulations in Building a Secure Culture.
Industry Insight: Ozan Ucar, CEO at Keepnet
Understanding how to enhance security awareness training is important for organizations aiming to reduce phishing risks. Ozan Ucar, CEO of Keepnet, shares valuable insights on how role-based training significantly improves engagement and phishing detection rates:
"We have seen over our customer base that when security awareness training adapts to the role, engagement rate increases up to 60% with 95% completion rate, and phishing reporting increases up to 92% in less than a year."
Implementing Role-Based Security Awareness Training
Successfully integrating Role based awareness training requires a structured approach to ensure employees receive targeted and effective cybersecurity education. Here are the key steps:
- Assess Role-Specific Cyber Risks – Identify unique threats based on employees' job responsibilities to ensure training aligns with real-world risks.
- Customize Training Content – Develop role-specific modules that address the security challenges employees face daily.
- Leverage AI-Powered Adaptive Learning – Use technology-driven training that dynamically adjusts content based on user behavior, ensuring personalized learning paths.
- Measure Training Effectiveness – Track engagement levels, phishing report rates, and incident reductions to continuously refine the program.
For a detailed step-by-step guide, read our blog on How to Implement Role-Based Security Awareness Training.
Keepnet’s xHRM: Adaptive Security Awareness Training
Keepnet’s xHRM (Extended Human Risk Management) platform includes adaptive security awareness training and dynamically tailors training content based on an employee’s role, behavior, and risk level. Features include:
- Automated Role-Based Assignments – Employees automatically receive training relevant to their role.
- Behavior-Driven Customization – Training evolves based on past engagement and risk exposure.
- Phishing Simulation Integration – Real-world phishing scenarios reinforce learning.
- Regulatory Compliance Alignment – Helps businesses meet industry and legal requirements effortlessly.
Measuring the Success of Role-Based Training
To ensure Role based security training is effective, organizations should track key outcome-driven metrics that reflect real improvements in security posture:
- Average Phishing Simulation Click Rate – Tracks how well employees identify phishing attempts. Lower click rates indicate improved awareness and reduced risk of successful attacks.
- Average Phishing Simulation Reporting Rate – Measures how often employees report phishing emails. Higher reporting rates show proactive security behavior and improved threat detection.
- Repeat Offenders Rate – Identifies employees who repeatedly fall for phishing attacks. Reducing this number indicates the effectiveness of targeted training in changing risky behavior.
- Regulatory Compliance Achievement – Ensures adherence to industry standards like GDPR, PCI DSS, HIPAA, ISO/IEC 27001, and NIST. Meeting compliance requirements demonstrates alignment with legal and organizational obligations.
For deeper insights into measuring security awareness training effectiveness, read What Are the Metrics for Evaluating Security Awareness Efforts.
Strengthening Security with Role-Based Training
Role based awareness training ensures employees receive targeted, relevant education to defend against daily cyber threats. With Keepnet’s xHRM Adaptive Security Awareness Training, businesses can boost engagement, strengthen defenses, and maintain compliance.
Ready to elevate your security awareness program? Contact Keepnet today and implement role-based training to protect your organization from evolving cyber threats.
Check out the Keepnet Human Risk Management Platform to build a security-aware workforce.
Editor’s Note: This blog was updated on November 6, 2025.