Cybersecurity Awareness Training: Complete Guide for 2026
Cybersecurity awareness training helps eliminate human error in cyber breaches. Train staff to detect phishing, social engineering, and evolving threats to strengthen your security culture.
Cybersecurity awareness training is the most effective way to close the gap between sophisticated cyber threats and everyday employee behavior. While technology can detect many attacks, it’s human decisions - clicking a link, opening an attachment, ignoring a warning - that often determine whether an incident becomes a breach.
In fact, human error was a contributing factor in 60% of breaches, according to the Verizon DBIR 2025. Yet, there’s a proven path forward: organizations that implemented structured awareness training saw a 4x increase in user reporting of suspicious activity, transforming users from weak points into active defenders.
To get there, businesses must move beyond generic content. This means deploying hands-on threat scenarios like phishing, smishing, and quishing - simulations that mirror actual adversary tactics and develop instinctive responses in your team.
In this blog, we’ll unpack the core of cybersecurity awareness training: how it works, why traditional approaches fail, and what it takes to embed security instincts into your organization’s culture.
What is Cybersecurity Awareness Training?
Cybersecurity awareness training is a structured program designed to help employees recognize, avoid, and report cyber threats. Its core goal is to build a strong security culture where every individual understands their role in protecting the organization.
Rather than relying solely on IT teams, this training empowers employees to act as a human firewall - actively defending against phishing, social engineering, ransomware, and other attacks. Topics typically include phishing simulations, password security, data protection, safe browsing, and incident reporting.
When done right, cybersecurity awareness training turns security from a policy into a shared mindset - embedded across every department.
Why is Cybersecurity Awareness Training Important?
Cybersecurity awareness training is a company-wide initiative that educates employees on how to recognize digital threats and make secure choices during everyday tasks. Unlike technical controls that operate in the background, this training focuses on human behavior - guiding people to think before they click, share, or respond.
It’s designed to form security habits that reduce risky behaviors, promote faster threat reporting, and improve decision-making under pressure. Over time, these habits help build a strong security culture where vigilance and accountability are embedded in day-to-day operations.
Top attack patterns your training must cover in 2026
Cybersecurity awareness training in 2026 must reflect how real attacks reach employees today — not only “classic phishing emails.” Attackers now combine AI, multi-channel social engineering, and identity-based tactics to create urgency and bypass security controls. If your training doesn’t cover the patterns below, employees may still “do everything right” in email and still get compromised through other channels.
1) QR phishing (Quishing)
QR codes are increasingly used to deliver malicious links because people can’t easily preview the destination before opening it. In 2026, employees should treat QR codes the same way they treat links: verify the context, avoid scanning unexpected QR codes, and report suspicious QR prompts instead of testing them “just to see.”
2) Deepfake impersonation (voice and video)
AI-generated voice and video make impersonation far more believable. Attackers can mimic executives, finance leaders, or “IT support” to pressure employees into sending data, approving payments, or sharing credentials. Training should emphasize verification habits: confirm requests via a second channel, use trusted contact methods (not the number in the message), and follow approval workflows even when urgency is high.
3) MFA fatigue and authentication prompt scams
Instead of stealing passwords, attackers increasingly try to trick employees into approving an authentication request they didn’t initiate. This is especially dangerous because the request can look legitimate. The habit to build is simple: if you didn’t start the login, deny it and report it immediately. Training should also explain how attackers trigger these prompts (credential stuffing, session hijacking, social engineering) so employees understand the “why,” not just the rule.
4) Voice social engineering and callback patterns (vishing + “call this number”)
Phone-based pressure works because it’s real-time and emotional. Attackers may call directly, or they may send a message instructing the target to “call back” a number that connects to a fake support line. Training should teach employees to use safe call-back procedures, follow verification scripts, and never share passwords, MFA codes, or allow account changes without validated identity checks.
5) Collaboration app social engineering (Teams/Slack-style lures)
Employees often trust messages that look internal — especially in collaboration tools. Attackers can impersonate a colleague, drop a “shared document” link, request an urgent action, or push a fake policy update. Training should teach employees to pause, verify unusual requests, and be cautious with links, file shares, QR codes, and login prompts delivered via chat.
6) AI-personalized spearphishing and social proof manipulation
Modern lures feel more “human” because they reference real names, vendors, projects, or recent events. Attackers exploit authority, urgency, secrecy, and emotional triggers (“I need this today,” “Don’t loop anyone else in,” “It’s confidential”). Your program should teach employees to recognize these manipulation patterns and use a report-first mindset when something feels off.
The goal of covering these patterns is practical: increase reporting behavior, reduce repeated mistakes, and help employees respond consistently under pressure — regardless of the channel the attacker uses.
Looking for a ready list of topics to build your training calendar? See: Security Awareness Training Topics (2026).
What Are the Benefits of Cybersecurity Awareness Training?
Most cyberattacks don’t start with code - they start with people. Whether it’s a misclick on a phishing email or a password reused across accounts, human behavior remains the easiest entry point for attackers. This is exactly where cybersecurity awareness training delivers value: by turning your workforce into a critical layer of defense.
Benefits for Individuals
- Improved Threat Recognition and Response: Employees become skilled at identifying phishing attempts, malicious links, and other deceptive tactics. This helps them act before a mistake becomes a security incident.
- Stronger Cyber Hygiene Habits: From managing passwords to avoiding unsecured networks, cybersecurity training reinforces daily habits that minimize risk—at work and beyond.
- Lower Exposure to Personal Risk: As staff gain awareness, they’re less likely to fall for scams or accidentally leak sensitive data—benefiting both their personal and professional lives.
Benefits for Organizations
- Fewer Breaches from Human Mistakes: Well-trained employees are less likely to click malicious links, share sensitive data, or fall for impersonation attempts—reducing avoidable security incidents.
- Faster Threat Detection and Response: Awareness training encourages staff to recognize and report threats early, giving your security team valuable time to investigate and contain issues before they escalate.
- A Unified Security Culture: Security awareness becomes a shared responsibility. Employees across departments understand common threats and take consistent action to protect systems and data.
- Greater Confidence and Clarity During Incidents: Employees respond faster and more effectively when something goes wrong. Training gives them the clarity to act decisively - reducing confusion and delays.
By embedding cybersecurity awareness training into your operations, you’re not just educating staff - you’re building an environment where secure behavior is second nature, and every individual contributes to a stronger, breach-resistant business.
Core Elements of Cybersecurity Awareness Training

Effective training sharpens decision-making, strengthens instincts, and focuses on actions employees take in their actual roles. From frontline staff to senior executives, security awareness programs should be role-based - reflecting the specific risks and responsibilities of each user group.
Below are the foundational elements every security awareness training program should address.
| Core Element | What It Covers |
|---|---|
| Recognizing Cyber Threats | Helps users identify threats like malware, ransomware, and unauthorized access before they escalate. |
| Password Management | Guides users on creating strong, unique passwords, avoiding reuse, and applying multi-factor authentication effectively. |
| Phishing and Social Engineering | Builds awareness of deceptive tactics used in phishing attacks and social engineering, including impersonation and urgency tricks. |
| Software Updates and Patching | Emphasizes the importance of timely patching and updates to prevent exploitation of known vulnerabilities. |
Table 1: Core elements of effective security awareness training
For deeper insight into tailoring this training by department, seniority, or risk level, read the Keepnet blog on Role-Based Security Awareness Training.
Implementing an Effective Awareness Program
Running cybersecurity awareness training once a year isn’t enough. To reduce human risk effectively, your program must be continuous, tailored, and actionable. A successful cybersecurity awareness training program not only educates - it changes behavior over time. This requires aligning content to real threats, using engaging delivery methods, and tracking progress to ensure it’s working.

1. Define Role-Based Objectives
Tailor training content to different roles and risk levels. Executives, IT staff, and frontline employees face different cyber threats, and your program should reflect that. A marketing associate might need phishing recognition, while a sysadmin should be drilled on credential threats. Aligning content to job-specific risks increases relevance and impact.
2. Deliver Engaging, Interactive Content
Ditch the slide decks. Use phishing simulations, gamified modules, microlearning, and video-based lessons to keep employees engaged and improve retention. Interactive content keeps learners focused and helps them apply knowledge in real scenarios. The more realistic the training, the stronger the behavioral change.
3. Integrate into Daily Workflows
Training should be part of the culture, not a one-time event. Embed security awareness training into onboarding, monthly check-ins, and ongoing team communications. Use tools like Slack reminders or monthly security tips to maintain visibility. This makes secure thinking a routine part of daily operations.
4. Measure Effectiveness and Improve
Track metrics like training completion, phishing click rates, and incident reporting. Use this data to refine your program and close gaps. Set clear KPIs tied to business risk, such as reduced phishing response time. Review results quarterly to adapt and optimize.
5. Keep It Continuous and Current
Cyber threats evolve, so your program should too. Regularly update modules, rotate scenarios, and share real incident lessons to keep content relevant. Leverage recent threat intelligence to make training timely. Ongoing refreshers help prevent user fatigue and keep awareness sharp.
By combining role-specific content, interactive delivery, and continuous improvement, a well-executed cybersecurity awareness training program becomes one of the most powerful tools in reducing human-driven security risks.
Tools that operationalize cybersecurity awareness training at scale (2026)
A strong cybersecurity awareness program often fails for one reason: it becomes manual. Spreadsheets, chasing completions, inconsistent reminders, and reporting that takes days to compile will eventually slow the program down. In 2026, the goal is to run awareness continuously and measure behavior change over time — not just deliver a course once a year.
At a high level, a platform that can operationalize training at scale should help you:
- Automate delivery: onboarding assignments, reminders, recurring microlearning schedules, and targeted remediation for repeat failures
- Run realistic phishing simulations: scenarios that reflect how employees are targeted today (email plus SMS/voice/QR/MFA-style prompts where applicable)
- Measure outcomes, not only completion: reporting rate, time-to-report, repeat failures, and risk trends by department/role
- Support scale and governance: localization, integrations (SSO/LMS/SCORM if needed), and audit-ready reporting
For a detailed checklist, read: How to Choose Security Awareness Training for Your Team
For a vendor-roundup view of leading options in 2026, read: Top Security Awareness Training Solutions for 2026
If you want to see how this looks in a real platform (automation + simulations + reporting), explore: Keepnet Security Awareness Training Software
Tailoring Security Awareness Training to Different Audiences
Not all users face the same risks—or learn the same way. A one-size-fits-all approach to cybersecurity awareness training leaves gaps that attackers can exploit. To truly reduce human risk, training must be customized by role, responsibility, and risk exposure across the organization.
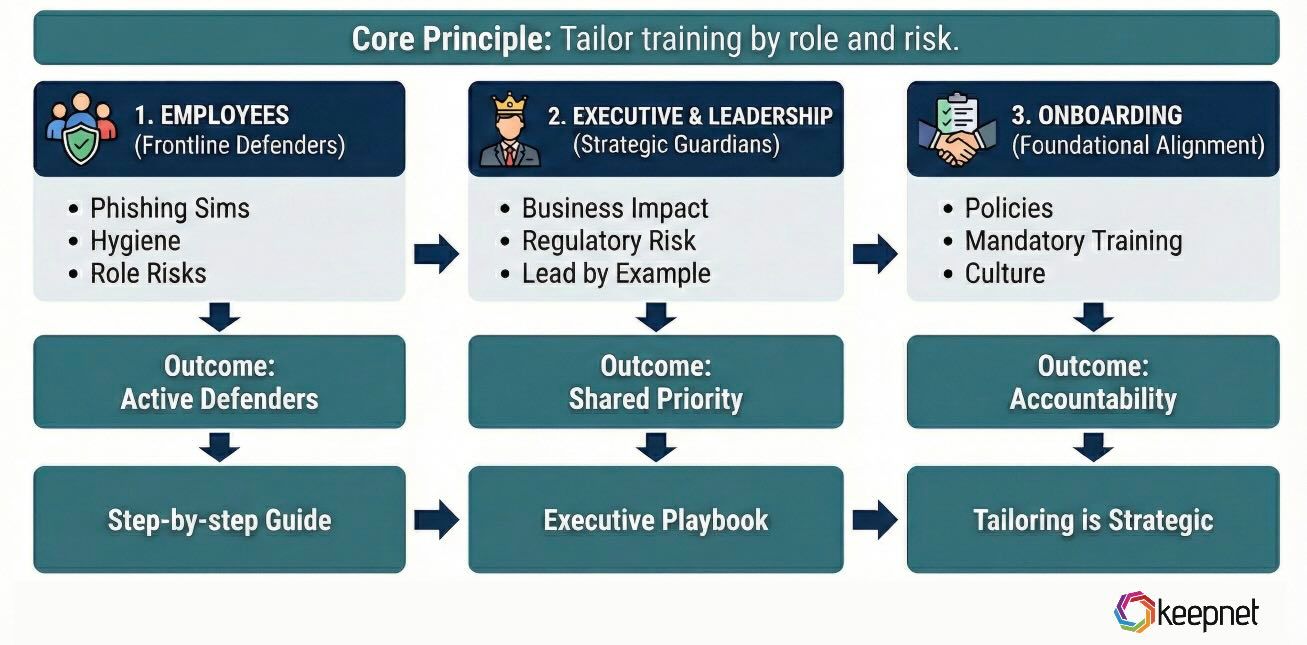
Cybersecurity Awareness Training for Employees
Frontline staff are often the first targets of phishing, malware, and social engineering. They interact daily with email, cloud apps, and customer data—making them high-impact security touchpoints.
Effective employee training should:
- Emphasize each employee’s responsibility in safeguarding company data.
- Include realistic simulations of phishing, smishing, and malware attacks.
- Reinforce daily cyber hygiene habits like secure browsing, password management, and device security.
- Evolve regularly with emerging threats and role-specific risk scenarios.
When employees understand the threat landscape and how their actions matter, they shift from being vulnerable endpoints to active defenders.
Need a step-by-step rollout plan for employees (including cadence, onboarding, and a 30–60–90 day structure)? Read: Cyber Security Awareness Training for Employees (2026 Guide).
Executive and Leadership Cybersecurity Training
Executives are prime targets for whaling and spear phishing due to their access to sensitive data and decision-making authority. Leadership training must focus on business impact- not just technical risk.
Leadership-focused training should:
- Highlight strategic threats such as business email compromise (BEC) and data exfiltration.
- Show the reputational and regulatory consequences of executive-level breaches.
- Emphasize leading by example in compliance, reporting, and secure communication.
Security awareness at the top signals to the rest of the organization that cybersecurity is a shared, strategic priority.
If you’re training senior leaders, keep it short, scenario-based, and focused on decision-making under pressure. For a dedicated executive playbook, read: Security Awareness Training for Executives: Protect Leaders from Cyber Threats.
Onboarding: Embedding Awareness from Day One
New hires are especially vulnerable, often unfamiliar with internal systems and protocols. Integrating cybersecurity awareness training into onboarding ensures early alignment with company-wide security practices.
Effective onboarding integration should:
- Introduce basic security policies, acceptable use standards, and reporting procedures.
- Include mandatory training on phishing awareness, password rules, and safe data handling.
- Reinforce the company’s commitment to a security-first culture from the start.
Tailoring training by audience isn’t a nice-to-have—it’s a strategic necessity. When security awareness programs reflect the real threats employees face in their specific roles, they’re far more likely to change behavior, close security gaps, and build a culture of accountability from the ground up.
If your goal is to prove impact (not just completion), use a KPI-driven approach. For practical metrics and how to measure program effectiveness, read: Security Awareness Program Metrics.
Keeping Pace with Regulatory Changes and Compliance
Cybersecurity threats evolve rapidly and so do the regulations designed to stop them. As attackers adopt new tools and tactics, regulators respond with updated compliance standards. That’s why cybersecurity awareness training must remain dynamic. Keeping your workforce informed on both emerging threats and shifting compliance requirements is critical to reducing risk, maintaining trust, and ensuring operational continuity.
Update Training to Reflect Emerging Threats
Refresh training content regularly to cover current attack vectors like QR code phishing, deepfake-based social engineering, and multi-factor bypass techniques. Training must help employees recognize the methods threat actors are using today not last year.
Integrate New Compliance Requirements
Align security awareness training with the latest standards such as GDPR, ISO 27001, NIS2, or industry-specific mandates. Educate staff on how compliance affects their daily tasks - from how they handle sensitive data to how and when they report incidents.
Deliver Ongoing Awareness, Not One-Time Lessons
Use bite-sized updates, interactive threat briefings, and periodic simulations to keep awareness sharp. A continuous approach reinforces that cybersecurity is not a one-off event - it’s a sustained organizational behavior.
Future Trends in Cybersecurity Awareness Training
The future of cybersecurity isn't merely about defending against threats; it's about harnessing the power of cutting-edge technologies and pedagogies to make training more efficient, engaging, and adaptive. Here's a look into the horizon of Cybersecurity Awareness Training and what trends are expected to shape its future.
Role of Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) have revolutionized many sectors, and cybersecurity training is no exception. Their integration promises a smarter, more efficient training paradigm:
- Dynamic Content Customization: AI can analyze an individual's learning style, pace, and past performance to tailor training materials accordingly.
- Predictive Analysis: ML algorithms can study patterns and predict potential cybersecurity threats, updating training modules in real-time to address them.
- Real-time Feedback: Immediate feedback based on AI analysis can help learners rectify mistakes on the spot, reinforcing cybersecurity awareness more effectively.
- Automated Simulations: AI can create real-time simulations of potential threat scenarios, providing learners practical experience.
Personalized Learning Journeys for Employees
Recognizing that every individual has unique learning needs and roles, the future of training leans towards personalization:
- Role-specific Modules: An IT specialist and a sales representative face different cybersecurity challenges. Tailored training ensures relevance and applicability.
- Adaptive Learning Paths: Depending on performance, training modules can adapt, offering deeper insights into areas where the learner may be struggling and fast-tracking areas of proficiency.
- Feedback-driven Iterations: Continuous feedback loops mean training paths evolve with the learner, ensuring long-term effectiveness and engagement.
Integration of Gamification and Microlearning Techniques
The digital-age learner often has a shorter attention span but a penchant for engagement. Addressing this, the trends of gamification and microlearning are on the rise:
- Engaging Security Awareness Training Games: Gamification turns training into a game with scores, levels, and rewards. This approach makes learning enjoyable and promotes healthy competition and motivation.
- Bite-sized Learning: Microlearning breaks down complex topics into bite-sized modules, making it easier for learners to digest, remember, and apply information.
- Immediate Rewards: Instant gratification through badges, scores, or other digital rewards can reinforce positive behaviors and encourage continuous learning.
The future of cybersecurity awareness training is exciting, with innovations poised to make training more immersive, personalized, and effective. By staying attuned to these trends, organizations can ensure their cybersecurity training initiatives remain top-notch, preparing their teams for the challenges of tomorrow.
Keepnet's Comprehensive Cybersecurity Awareness Training
Keepnet offers a behavior-driven cybersecurity awareness training solution designed to close the human security gap where most attacks begin. Rather than delivering generic content, Keepnet’s Human Risk Management platform aligns training with actual employee actions, organizational risk levels, and the specific attack techniques targeting your industry.
Key capabilities of Keepnet’s awareness training include:
- Personalized learning paths tailored to each employee’s behavior, role, and level of cyber readiness—ensuring relevant, high-impact training across the workforce.
- Access to over 2,100 training assets from 15+ trusted content providers in 36+ languages—ideal for multilingual and geographically dispersed teams.
- Full organizational coverage, helping ensure that every department—from finance to operations—is aligned with your security posture and compliance goals.
- Visual reinforcement tools like posters, infographics, and screensavers to keep essential security practices visible and memorable throughout the workday.
- AI-powered phishing simulations and adaptive testing, including advanced challenges like deepfake recognition—equipping staff to identify and respond to complex threats.
- Smart content customization, using AI to match training topics with your organization’s specific threat exposure and behavioral risk data.
- Short, narrative-based modules that bring cybersecurity principles to life through relatable, scenario-driven stories that drive retention and action.
Whether you’re building a new training program or upgrading an existing one, Keepnet’s cybersecurity awareness platform is built to drive measurable behavior change and long-term risk reduction—at scale.
Explore Keepnet’s Security Awareness Training Platform.
Ready to try it without commitment? Start with the free security awareness training.
Further Reading:
- Cyber Security Awareness Training for Employees (2026)
- Security Awareness Training Topics (2026)
- Security Awareness Training Statistics
- How to Evaluate Your Security Awareness Program’s Effectiveness
- Role-Based Security Awareness Training
- Localization for Security Awareness Training
- Nano Awareness Training
- Deepfake-focused awareness training
Editor's Note: This article was updated on January 6, 2026.