Cybersecurity Awareness Training for Employees: Complete Guide (2026)
A practical 2026 guide to run cybersecurity awareness training for employees: short monthly modules, real-world scenarios, reinforcement that sticks, and metrics that prove risk reduction (report rate, time-to-report, verification compliance).
Cyber attacks rarely begin with a “highly technical hack.” Most start with a human moment: a rushed click, a helpful reply, a shared password, a fake caller who sounds confident, or a QR code that looks harmless.
That’s why cybersecurity awareness training for employees should not be a once-a-year checkbox. It should be a repeatable behavior program that reduces risky actions and increases safe habits—especially reporting suspicious messages early.
In this guide, you’ll learn how to build a training program that works in real life: what to teach, how often, how to keep employees engaged, and how to measure results.
Key takeaways
- The goal is not “knowledge.” The goal is behavior change: fewer risky actions and faster reporting.
- A strong program uses microlearning + real-life scenarios + reinforcement.
- The best cadence for most organizations is 5–10 minutes monthly plus short reminders.
- Track the right metrics: report rate, time-to-report, risky behavior reduction, and completion.
- You can use videos, podcasts, PPT, and SCORM—as long as you structure it like a program, not random content.
What is cybersecurity awareness training for employees?
Cybersecurity awareness training is a structured learning program that helps employees recognize threats (phishing, smishing, vishing, QR phishing, deepfakes, MFA fatigue), follow safe processes, and respond correctly when something suspicious happens.
It’s not only about “knowing what phishing is.” It’s about what employees do when the pressure is real:
- Do they verify before acting?
- Do they report quickly?
- Do they follow the process even when someone sounds urgent?
- A good program makes safe actions feel natural, easy, and automatic.
Free Deepfake Phishing Simulation
One-time, zero-cost deepfake simulation
Why most employee awareness training fails
Many cyber security awareness training programs fail because they are built like a lecture:

- too long
- too generic
- too rare (once per year)
- measured only by completion rate
- not connected to real threats employees actually see
Employees forget what they don’t practice. That’s normal human behavior. Your job is to design training that fits how humans learn: short sessions, repetition, realism, and reinforcement.
The outcomes you should target (not just “completion”)
Before choosing content, decide what outcomes you want. Here are practical, measurable outcomes:
1) Increase reporting behavior
Employees should report suspicious messages (email, SMS, calls, QR, chat apps) instead of ignoring them or clicking.
2) Reduce risky actions
Fewer link clicks, fewer credential shares, fewer unsafe installs, fewer “urgent” compliance mistakes.
3) Improve verification discipline
Employees should verify requests (payment changes, password resets, MFA requests, data sharing) using the company’s approved method.
4) Improve response speed
The time between receiving a suspicious message and reporting it should go down.
The training topics employees actually need in 2026
You don’t need 100 topics. You need the right topics, repeated at the right cadence.
Core monthly topics (high impact)
- Phishing fundamentals (modern examples)
- Smishing (SMS scams)
- Vishing (phone-based social engineering)
- QR phishing (quishing)
- Business email compromise (invoice / payment changes)
- MFA fatigue and push notification scams
- Password habits + passphrases + password managers
- Safe file sharing and cloud permissions
- Remote work and device hygiene
- Data handling basics (PII, customer info, confidential docs)
Advanced topics (quarterly or role-based)
- Deepfake voice and impersonation
- Social engineering on messaging apps
- Executive impersonation and urgent approval scams
- Supply chain / vendor request verification
- Privileged access and admin account safety (for IT)
Want a full topic calendar with examples + rollout tips?
We maintain a dedicated pillar guide that lists 50 Security Awareness Training Topics (with practical examples, metrics, and planning guidance). Use it when you’re building a full annual program or role-based tracks:
Read: Security Awareness Training Topics (CISO Playbook)
The behavior-change loop that actually works: teach → practice → reinforce → improve
A cybersecurity awareness program works best when it’s run as a monthly loop, not a one-time course. Use this simple cycle to turn knowledge into habits:
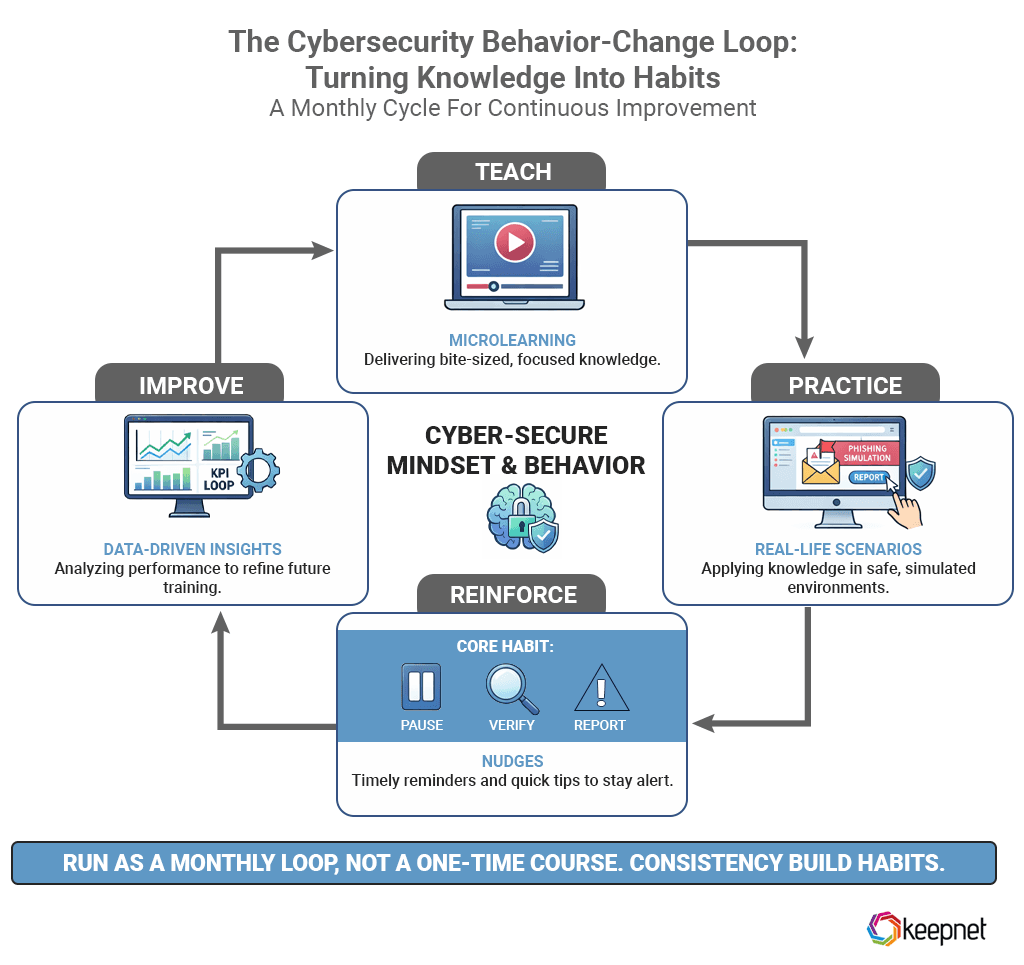
1) Teach (microlearning: 5–10 minutes)
Deliver one small lesson at a time (one threat + one safe action). Keep it short enough that employees complete it without fatigue.
2) Practice (real-life scenarios)
Follow the lesson with short, realistic scenarios—stories and examples that feel like daily work. This is where employees learn what “good behavior” looks like under pressure.
3) Reinforce (nudges: 30–90 seconds)
Most behavior change happens between courses, not during them. Use lightweight reinforcement such as Slack/Teams reminders, quick “what to do next time” messages after a risky action, posters, or short prompts that repeat your desired habit.
One habit to reinforce consistently:
Pause → Verify → Report
4) Improve (KPI loop)
Review results every month and adjust the next topic based on real performance. Go beyond completion rates and track behavior outcomes like reporting rate, time-to-report, and risk reduction over time.
Want the full step-by-step blueprint (role/risk-based tailoring, nudging strategy, and KPI-driven iteration)? Check deeper guide here: How to Create a Security Awareness Program
How often should you train employees?
Most organizations get the best results by combining a core training cycle with short, repeated reinforcement.
Recommended cadence (works for most teams)
- Every 6–12 months: one comprehensive awareness module to reset baseline knowledge and align everyone on policies and modern threats.
- Quarterly (minimum): short refreshers focused on the most common mistakes you see internally.
- Monthly (ideal): microlearning and/or simulations to keep awareness “top of mind” and turn safe actions into habits.
- After incidents or major threat shifts: fast, targeted training when something changes (new scam wave, policy update, tooling change, real incident).
Match the frequency to risk (so training doesn’t feel like spam)
Not everyone needs the same intensity. High-risk groups (e.g., finance, executives, IT admins) typically need more frequent touchpoints, while low-risk groups can follow a lighter schedule—as long as reporting behavior stays strong.
A practical schedule you can run all year
- Onboarding: assign essential training immediately when someone joins (so new hires don’t become your biggest blind spot).
- Ongoing: one short monthly module (5–10 minutes) + one reminder/nudge.
- Remediation: targeted training only for employees who fail simulations (fast feedback, specific to the mistake).
If you want the full breakdown (business size, industry, regulations, and a sample monthly calendar), link to our detailed guide here:
How Often Should Employees Receive Cyber Security Awareness Training?
How to use employee awareness training modules effectively
In modern organizations, employees don’t need long courses—they need short, repeatable modules that build habits over time. The most effective programs combine microlearning + realistic scenarios + reinforcement, delivered in a consistent cadence.
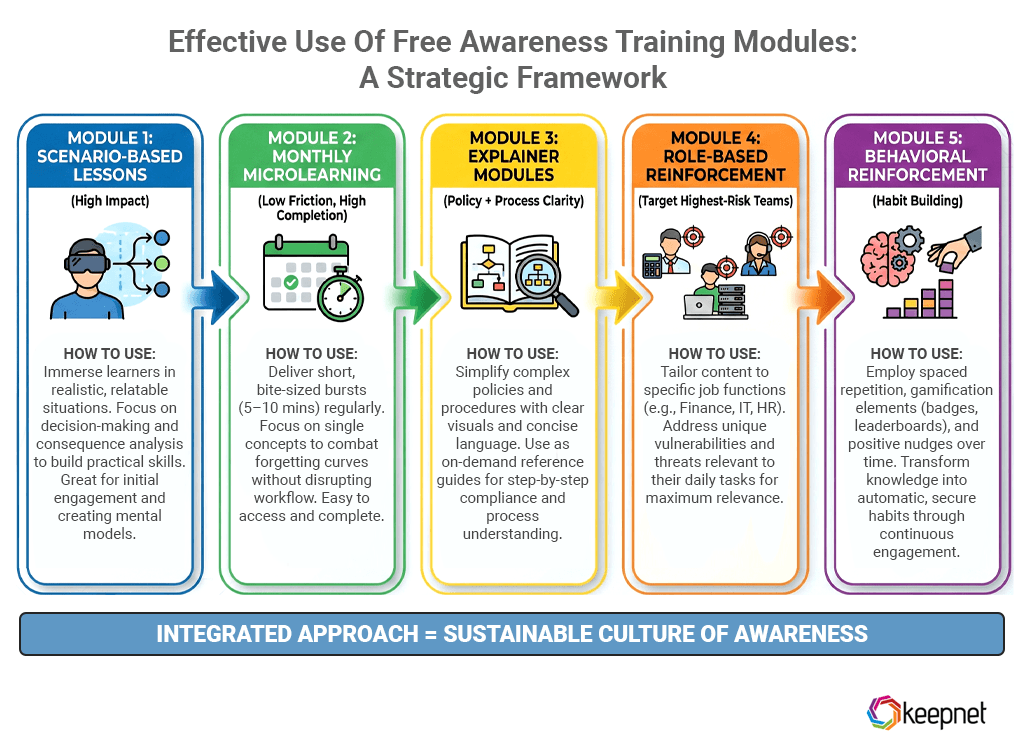
Module 1: Scenario-based lessons (high impact)
Purpose: Teach decision-making under pressure (urgent requests, impersonation, payment changes, credential prompts).
Best for: All employees, especially non-technical roles.
How to use: 1–2 short scenarios per month, followed by one clear “what to do next time” action.
Module 2: Monthly microlearning (low friction, high completion)
Purpose: Maintain awareness with minimal fatigue.
Best for: Organization-wide monthly cadence.
How to use: 5–10 minutes once per month, each module focused on one threat + one safe action.
Module 3: Explainer modules (policy + process clarity)
Purpose: Clarify “how we do it here” (verification steps, reporting routes, handling sensitive data).
Best for: New hires, distributed teams, global workforces.
How to use: Use during onboarding and as an annual refresher (or when processes change).
Module 4: Role-based reinforcement (target the highest-risk teams)
Purpose: Reduce the highest-cost mistakes by focusing on role-specific scams.
Examples:
- Finance: invoice fraud, payment changes, supplier impersonation
- HR: payroll changes, employee data requests
- IT: MFA fatigue, password reset social engineering, admin account protection
How to use: Quarterly assignments for high-risk roles, with short follow-up checks.
Module 5: Behavioral reinforcement (habit building)
Purpose: Make safe behavior automatic, not optional.
How to use: Pair every module with a simple rule employees remember: Pause → Verify → Report
Format options: short prompts, quick reminders in Teams/Slack, posters, or manager talking points.
Where these modules should live (professional delivery)
To keep training measurable and audit-ready, deliver modules through:
- LMS (SCORM) for completion tracking and reporting
- Internal training portal/intranet for on-demand access
- New-hire onboarding workflow so new employees aren’t a blind spot
Looking for a complete library of free materials (videos, podcasts, PPT decks, and SCORM packages)? Visit our Free Security Awareness Training page.
PPT and SCORM Awareness Training: when employees training needs LMS tracking
Many organizations need proof of completion for compliance or HR reporting. That’s where PPT and SCORM help.
When to use PPT
- You run live sessions (monthly security briefings)
- You want managers to deliver training in a team meeting
- You want quick internal enablement
When to use SCORM
You use an LMS and need completion tracking
- You want a consistent training experience across regions
- You need audit-friendly records
Best practice: Use SCORM for tracking, and use videos for engagement and realism. Together they work better.
How to deliver security awareness training at scale (without manual effort)
Designing the right training is only half the job. The real security awareness training challenge is operational: rolling out the right modules to the right people, in the right language, on the right schedule—then proving it worked. When training depends on spreadsheets, reminders, and manual follow-ups, programs usually stall after the first few months.
Here’s what “manual effort” looks like in most organizations (and why it breaks):
- Scheduling chaos: different teams, time zones, and shift workers require different delivery windows—plus constant changes as people join, move roles, or leave.
- Localization gaps: global teams need training in their language and cultural context, not just a translated PDF.
- Tracking overload: chasing completions, exporting lists, and merging reports becomes a monthly admin project.
- Reporting pain: leaders don’t want “completion rate.” They want metrics like reporting rate, time-to-report, and risk reduction—without you building dashboards by hand.
A scalable operating model: automate the “delivery + measurement” layer
To scale without burning time, treat awareness as a system that runs continuously in the background:
- Auto-assign training by role and lifecycle: onboarding assignment on day 1, monthly microlearning for everyone, and targeted remediation only for people who fail simulations.
- Deliver training where employees already are: email for office staff, but also mobile-friendly delivery for frontline and distributed teams.
- Apply localization by default: assign training language automatically for multilingual regions so employees don’t disengage at the first screen.
- Centralize measurement: one place to track completion, progress, and behavior metrics over time—without exports and manual reporting cycles.
What “no manual effort” should look like (your checklist)
If you’re evaluating tooling or improving your operational setup, aim for these capabilities:
- Automated enrollment and reminders (so you’re not chasing people)
- Role-based learning paths (so content matches risk)
- Multi-language training support (so global teams don’t get left behind)
- LMS compatibility / SCORM support when needed (so training fits your existing ecosystem)
- Reporting that shows outcomes (not just completions): reporting rate, time-to-report, repeat failures, and progress by department
If you want this program to run without spreadsheet admin work, you’ll need a platform that automates assignment, reminders, localization, and outcome reporting. Explore Keepnet’s Security Awareness Training platform (includes role-based learning paths, multi-channel simulations, and behavior metrics).
Alternatively, try free security awareness training.
A simple 30–60–90 day cybersecurity awareness rollout plan for employees
This plan is designed to help you launch fast, build momentum, and then optimize based on real behavior—not guesswork. Keep each monthly touchpoint short, consistent, and measurable.
Days 1–30: Launch and set a baseline
Goal: Establish the program, teach the “one must-do action,” and measure where you are today.
- Assign one short core module (5–10 minutes) to all employees (ideal for onboarding + organization-wide baseline).
- Teach one non-negotiable action: how to report suspicious messages (email, SMS, calls, QR codes, chat apps).
- Run a baseline knowledge check (5 questions) to identify the top gaps (e.g., MFA fatigue, invoice fraud, QR phishing).
- Set clear expectations with one simple rule: “If you’re unsure, report it.”
- Make reporting easy (one button, one mailbox, one workflow). If reporting is hard, training won’t stick.
- Capture baseline KPIs you’ll compare against later: completion rate, quiz pass rate, report rate, time-to-report (if available).
Days 31–60: Reinforce with realism and repetition
Goal: Turn “knowledge” into “decision-making under pressure.”
- Add scenario-based learning (2–3 short scenarios) focused on realistic situations employees face: urgent approvals, impersonation, invoice/payment change requests, credential/MFA prompts
- Share one internal example (sanitized) to make the risk feel real (what happened, what the red flags were, what the correct response should be).
- Repeat the verification rule in the exact same wording across channels: “If money, credentials, or sensitive data is requested → verify via an approved channel.”
- Add one reinforcement nudge (30–60 seconds) to keep the habit top-of-mind: a short Teams/Slack message, a manager talking point, a one-slide reminder
- Measure improvement month-over-month: report rate, risky actions, time-to-report.
Days 61–90: Segment by role and optimize the program
Goal: Reduce the biggest risks by targeting the teams that attackers target most.
- Create role-based assignments (short, specific modules that match real threats): Finance: invoice fraud + payment change verification; HR Department: payroll changes + employee data request; IT/Admins: MFA fatigue + password reset social engineering + privileged access hygiene
- Add one behavior-focused module that reinforces a single habit (e.g., verify-before-action, report-first culture).
- Review performance and adjust your monthly calendar based on what employees actually struggle with: Which departments report least? Which scam type appears most often? Where do employees hesitate (verification steps, escalation path, policy confusion)?
- Set the next-quarter plan using the data: keep what’s working; remove low-impact topics; double down on the behaviors that reduce incidents
Optional (high impact): What to communicate to employees in one sentence
Use one consistent message across email, intranet, and manager briefings:
Pause → Verify → Report.
How to measure cybersecurity awareness training effectiveness
Completion rates are useful for tracking participation, but they don’t prove that employee risk is going down. A practical employee program should be measured by whether people report faster, make fewer risky decisions, and follow verification steps under pressure.
The metrics you should track (in this order)
1) Reporting rate (most important): Track how often employees report suspicious messages (email, SMS, calls, QR codes, or chat requests). If reporting is rising over time, your program is building a safer reflex.
2) Time-to-report: Measure how quickly employees report after receiving something suspicious. Faster reporting usually means faster containment and less damage.
3) Risky action reduction: Track whether risky behaviors decrease over time (e.g., clicking unsafe links in tests, sharing credentials, approving urgent payment changes without verification, or falling for impersonation attempts).
4) Verification compliance (role-based): For high-risk teams, measure whether employees follow your verification process:
- Finance: payment change and supplier verification
- HR: payroll change and employee data requests
- IT/Admins: identity checks for resets, MFA fatigue handling, admin account hygiene
5) Completion and short quiz results (supporting metrics): Use completion rate and short quizzes (2–5 questions) to confirm coverage and spot knowledge gaps—but treat them as supporting indicators, not the main success metric.
Use a monthly feedback loop
Review results monthly, then choose the next topic based on what employees struggle with most. This is how training becomes a program that improves over time—not a static course.
For a deeper KPI framework (what to measure, how to interpret results, and how to build a metrics-driven awareness program), see:
Metrics for Evaluating Security Awareness Efforts
Common mistakes to avoid in employee cybersecurity awareness training
1) Training that is too long (and too rare)
Long, annual courses create fatigue and low recall. Employees don’t remember what they don’t practice.
Better approach: deliver short modules (5–10 minutes) on a consistent cadence, then repeat the key action you want employees to take.
2) Generic training with no workplace relevance
If examples don’t match real workflows, employees disconnect. Generic “phishing examples” won’t help when someone is facing an invoice change request, an HR data request, a fake IT call, or a QR code in the office.
Better approach: use scenarios that reflect your environment—finance approvals, HR processes, vendor requests, support interactions, remote work, and the channels employees actually use.
3) No reinforcement between lessons
Behavior doesn’t change from a single course. Without reinforcement, awareness decays and old habits return.
Better approach: pair each module with a lightweight nudge that repeats one rule:
Pause → Verify → Report
Use quick reminders in Teams/Slack, manager talking points, posters, or short follow-up prompts after risky actions.
4) Measuring the wrong thing
If you only measure completion, you’ll optimize for “finishing training,” not for reducing human risk.
Better approach: prioritize behavior outcomes such as:
- reporting rate
- time-to-report
- risky action reduction
- verification compliance (especially for finance/HR/IT)
Turn employee training into measurable risk reduction (at scale)
This guide explains how to run an employee cybersecurity awareness program: short modules, realistic scenarios, consistent reinforcement, and KPIs like reporting rate and time-to-report. The challenge for most organizations is not the idea—it’s executing it consistently across roles, regions, and channels.
Keepnet helps you run this program as a repeatable system:
- Security Awareness Training: Deliver short, role-based modules (onboarding + monthly microlearning) with consistent reinforcement to build safer habits.
- Phishing Simulator: Practice real-world decision-making through simulations (so employees learn what to do under pressure—then improve over time
If you want to implement the 30–60–90 day approach in this article with measurable outcomes, explore Keepnet Cyber Security Awareness Training Software or request a demo.
Note: Keepnet has been named a go-to vendor for stopping deepfake and AI disinformation attacks by Gartner for consecutive years.
Further Reading
- Cybersecurity Awareness Training: Complete Guide for 2026
- Security Awareness Training Topics (2026)
- How to Create a Security Awareness Program
- How Often Should Employees Receive Cyber Security Awareness Training?
- What Are the Metrics for Evaluating Security Awareness Efforts?
- Security Awareness Training Platform
Editor's Note: This blog was updated on February 23, 2026.