Security Awareness Isn’t Dead—But It’s Not Enough
Old-school security awareness training fails to change behavior, leaving organizations vulnerable to evolving threats. Discover how a behavior-driven security culture with adaptive learning, nudging, and AI-driven interventions can significantly reduce cyber risk.
Organizations have long used security awareness training to educate employees about cyber threats like phishing and insider attacks. Gartner’s 2024 recognition of Security Awareness Computer-Based Training (CBT) helped formalize these efforts, making training more structured.
However, the cyber skills gap is growing. According to the World Economic Forum (2025) (WEF, 2025), it increased by 8% in 2024, with two out of three organizations struggling to find skilled security professionals. Worse, only 14% of companies feel confident they have the right people to handle today’s threats.
With social engineering attacks still a major cause of breaches, awareness alone isn’t enough. This blog explores why traditional security awareness falls short and how organizations can build a behavior-driven security culture to reduce risk.
Who Thinks That Security Awareness Doesn’t Work?
Despite years of security awareness training, social engineering attacks remain a major cause of breaches. Gartner data shows that from 2013 to 2021, the percentage of breaches linked to social engineering has hovered around 20%, with no significant decline.
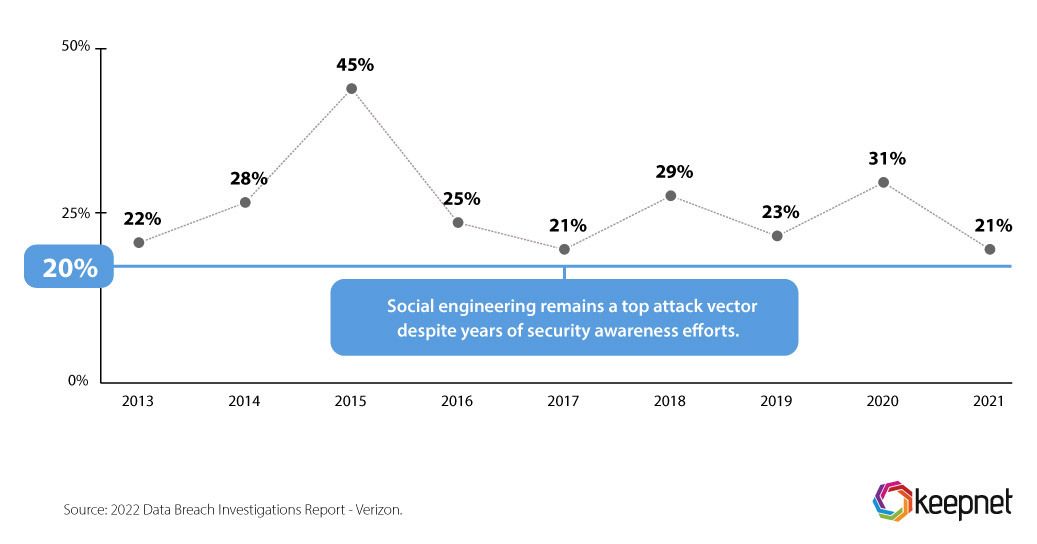
However, this doesn’t mean security awareness programs don’t work. Instead, it highlights how attackers have adapted, using AI, machine learning, and advanced social engineering tactics across email, SMS, voice calls, and social media to bypass traditional defenses.
The bigger issue is that awareness alone doesn’t change behavior. A Gartner survey found that 69% of employees admitted to bypassing security policies in the past year, and 74% would do so if it helped them meet business goals (Gartner, 2022).
This proves that simply educating employees isn’t enough. Organizations need a behavior-driven security culture that goes beyond training, reinforcing secure habits and integrating security into daily workflows. This is where a Security Behavior and Culture Program (SBCP) comes in, focusing on sustained behavior change rather than one-time training. Learn more about SBCPs here: What is a Security Behavior and Culture Program (SBCP)?.
Has Security Awareness Failed?
Security awareness isn’t dead—but outdated approaches are. Organizations must move beyond basic training and adopt a Security Behavior and Culture Program (SBCP) within a human cyber risk management framework to drive real behavior change.
Why Traditional Security Awareness Falls Short
Traditional security awareness training helps employees recognize threats, but it doesn’t always change behavior. Many employees still click on phishing links, reuse passwords, or bypass security policies, even when they know the risks. To truly reduce human cyber risk, organizations need more than just knowledge, they need behavioral reinforcement and a security-driven culture.
Awareness ≠ Behavior Change
Knowing isn’t the same as doing. Security awareness programs increase knowledge, but that doesn’t mean employees apply it in real-world situations.
- Employees understand that reusing passwords is risky, yet many still do it for convenience.
- Despite years of phishing training, social engineering remains a major cause of breaches (21-45% between 2013-2021, to Verizon DBIR).
The Limitations of Old-School Training
Many security awareness programs rely on outdated methods that focus on knowledge rather than action. Employees may pass training but still fall for phishing scams or ignore security rules under pressure. Without ongoing reinforcement, traditional training fails to build lasting secure habits.
One-Size-Fits-All Approach
Most training is generic, failing to account for different roles, risk levels, and learning styles:
- IT admins face risks like credential stuffing, while HR teams handle fraudulent payroll emails, yet they receive the same training.
Compliance-Driven, Not Risk-Driven
Many organizations treat security awareness as a checkbox exercise, focusing on compliance rather than real-world risk reduction.
- Success is measured by training completion rates, not by actual improvements in security behavior.
- Employees complete training to satisfy HR, not because it’s engaging or relevant to their daily work.
Cyber Threats Have Outpaced Awareness Training
Traditional programs focus heavily on email phishing, but attackers have evolved.
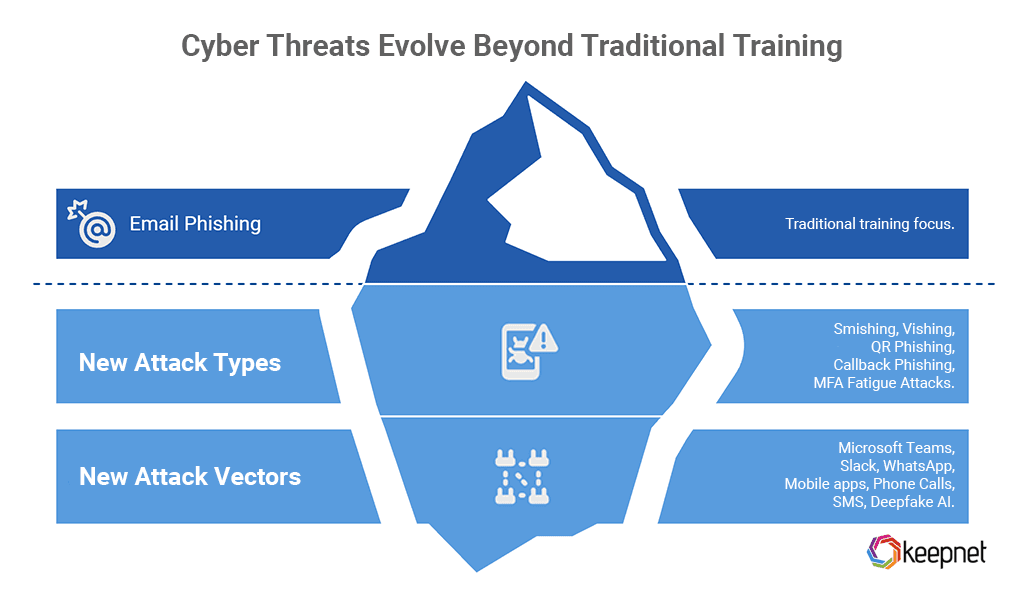
New Attack Types:
New Attack Vectors:
- Microsoft Teams, Slack, WhatsApp
- Mobile apps, phone calls, SMS
- Deepfake AI-based impersonation
Security awareness training hasn’t kept up with these evolving threats, leaving employees vulnerable despite completing training. Organizations must shift toward behavior-driven security programs that reinforce secure habits and adapt to modern threats.
Security Awareness is Still Essential—If Done Right
Security awareness isn’t dead—it just needs to evolve. Organizations must replace outdated, one-size-fits-all training with adaptive, behavior-driven programs that:
- Personalize learning based on role, risk profile, and behavior.
- Integrate behavioral science (nudging, gamification) for engagement.
- Leverage automation and AI to reinforce learning in real-time.
What Makes an Effective Security Awareness Program?
A strong security awareness program goes beyond basic training. It must be personalized, adaptive, and behavior-driven to truly reduce cyber risk.
Role-Based Learning
Different job functions face different threats. Training should be tailored to each role’s specific risks.
- Finance teams need training on Business Email Compromise (BEC) scams.
- IT teams should focus on zero-day exploits and credential attacks.
For further insights, read our article to learn how to implement role-based security awareness training.
Risk-Adaptive Training
Employees with higher risk exposure, such as those handling sensitive data or communicating with external contacts—should receive more frequent and advanced training.
Behavior-Driven Approach
Training should analyze and reinforce real employee behaviors, rather than just teaching security concepts.
- If an employee interacts with unknown senders, they should get real-time phishing detection tips.
- If someone bypasses MFA, they should receive security nudges reminding them of authentication best practices.
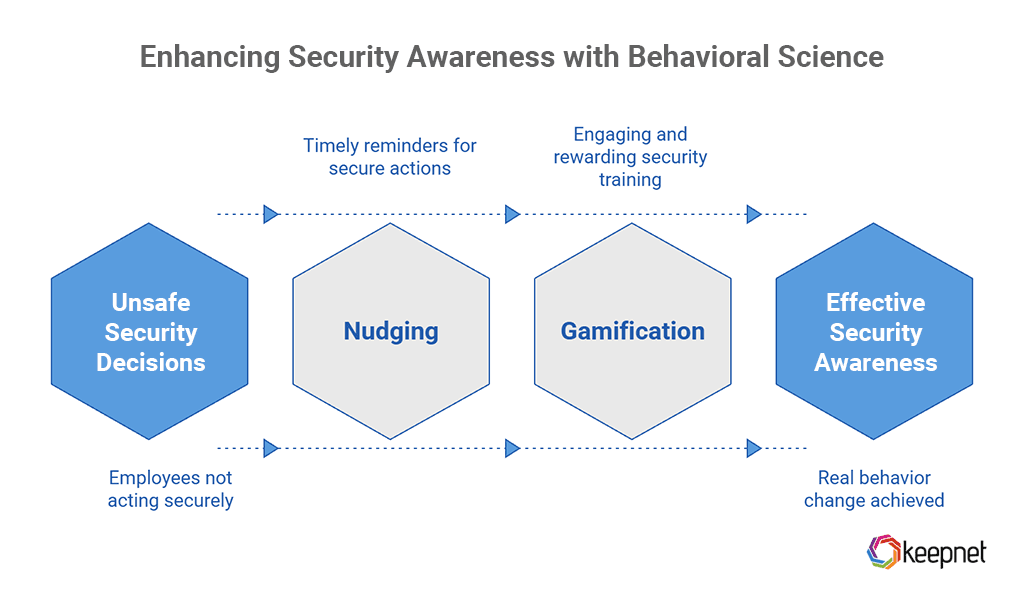
Using Behavioral Science: Nudging & Gamification
People don’t always act on what they know. Behavioral science techniques like nudging and gamification can encourage employees to make safer security decisions by reinforcing good habits in real time.
- Nudging: Small, timely reminders that encourage secure actions.
Example: Before sending sensitive data, a pop-up warning asks, "Are you sure this is safe?"
- Gamification: Making security engaging and rewarding through challenges, leaderboards, and incentives to encourage participation
By focusing on role-based risks, adaptive learning, and behavioral reinforcement, organizations can create effective security awareness programs that drive real behavior change.
Moving from Awareness to Security Behavior and Culture
Security awareness alone isn’t enough—behavior change is the key to real risk reduction. Organizations must shift from simply educating employees to actively reinforcing secure behaviors. This is where Security Behavior and Culture Programs (SBCPs) come in, focusing on habit formation and continuous improvement.
The Future of Security Awareness and Behavior Change
Security awareness provides a foundation by helping employees recognize threats, but it must be reinforced with real-time interventions and behavioral reinforcement to be effective.
A modern security program:
- Embeds security into daily workflows rather than relying on periodic training.
- Uses automation and adaptive learning to personalize training based on individual risks.
- Applies behavior analytics to measure and strengthen secure actions over time.
By shifting from knowledge-based training to behavior-driven security culture, organizations can build long-term resilience against human-targeted cyber threats.
The Solution: A Human Cyber Risk Management Framework
To effectively reduce human risk, organizations must move beyond traditional awareness training and adopt a Human Cyber Risk Management Framework—a comprehensive approach that reinforces security behaviors in real time.
- Continuous Learning – Shift from one-time annual training to ongoing, personalized security reinforcement based on employee risk levels.
- AI-Driven Security Nudges – Use real-time AI-powered alerts to guide employees toward safer decisions when they are most at risk.
- Contextual Reinforcement – Embed security reminders directly into daily communication tools like Microsoft Teams, Slack, and email clients to reinforce best practices.
- Metrics That Matter – Move beyond training completion rates and focus on measurable behavior improvements, such as fewer phishing clicks and faster incident reporting.
To build a truly effective security culture, organizations must understand how behavior change works. Learn more about the COM-B scientific behavioral model and its role in cybersecurity awareness here: What Is the 'COM-B' Scientific Behavioral Model in Cybersecurity Awareness?
Security Awareness Needs an Upgrade, Not a Replacement
Security awareness training is still valuable, but outdated approaches no longer work. Generic, one-size-fits-all programs focused only on compliance fail to create lasting behavior change, leaving organizations exposed to evolving threats.
A modern security awareness program should be personalized, adaptive, and behavior-driven, using nudging, gamification, and real-time security interventions to reinforce secure habits in daily workflows.
The goal isn’t just to educate employees but to build a security-conscious culture where safe behaviors become second nature. Organizations that move beyond basic training and focus on sustained behavior change will see a meaningful reduction in human cyber risk.
To explore an approach that integrates scientific behavior change models, AI-driven phishing simulations, and real-time security reinforcement, visit Keepnet's Cybersecurity Awareness Training.