What Is End-to-End Encryption? Everything You Need to Know
End-to-end encryption (E2EE) ensures private communication by securing data so only the sender and recipient can access it. Learn how E2EE protects messages, emails, and cloud storage, its benefits, challenges, and how businesses use it for enhanced security.
That little padlock in your browser is easy to love, but it’s not a trust badge. Today, even most phishing sites use HTTPS. End-to-end encryption (E2EE) is different: think of sealing a message in a box only you and the intended recipient can open. The service in the middle can carry the box, but it can’t peek inside. That’s the core end-to-end encryption meaning and why people increasingly ask, “What is end-to-end encryption and why should I care?”
Here’s how E2EE works in plain English: your device encrypts content with keys that live on the endpoints; only the recipient’s device can decrypt it. Not even the platform should be able to read the message. This model now powers private messages, calls, and file sharing in apps like WhatsApp and Signal by default, while Messenger and Instagram offer it as an option. A useful end-to-end encryption example: two colleagues exchanging a contract—servers relay the file, but only their devices can open it.
E2EE is one of the strongest answers to “Is it secure?”, but it isn’t a silver bullet. Metadata (who talked to whom, when) can still be exposed; cloud backups may require you to enable E2EE; malware or social engineering can compromise the endpoints; and some platforms differ (e.g., Telegram’s default chats aren’t E2EE—only Secret Chats are). The takeaway: treat E2EE as the foundation, not the finish line. Pair it with strong identity checks, phishing awareness, MFA, and healthy device hygiene to truly protect sensitive data.
Understanding End-to-end Encryption?
End-to-end encryption (E2EE) means your data, messages, photos, files, is encrypted on your device and only decrypted on the recipient’s device. No one in the middle can read it, not your internet provider, not the platform, not an attacker on the network. That’s the practical end-to-end encryption meaning: true privacy between endpoints.
- How it works: modern apps use public-key cryptography. You encrypt with the recipient’s public key; only their matching private key can decrypt. Because those keys live on the endpoints, the service can deliver your content without being able to open it. That’s the essence of how end-to-end encryption works.
- Simple example: send “Happy Birthday!” in an E2EE app like WhatsApp or Signal. Anyone who intercepts the traffic sees only unreadable ciphertext, while the recipient reads the message instantly on their device. For a deeper, visual walkthrough of E2EE in everyday use, watch the video below.
Why Is End-to-End Encryption Important?
Cyberattacks are more frequent, more targeted, and more expensive than ever—industry estimates put global cybercrime costs at $15.63 trillion by 2029. In that reality, the question isn’t just what is end-to-end encryption but why it’s now table-stakes for privacy. End-to-end encryption (E2EE) gives people and businesses confidence that communications are protected against interception, data mining, and unauthorized access.
At its core, the end-to-end encryption meaning is simple: only the sender and the intended recipient can read the content. If you’re wondering how does end to end encryption work, the short version is public-key cryptography—your device encrypts with a recipient’s public key; their device unlocks it with a private key. That’s why messages, calls, and files remain end-to-end encrypted in transit and at rest on the service’s servers.
For organizations, the benefits of end to end encryption go beyond confidentiality. E2EE reduces breach exposure, protects sensitive data (IP, contracts, customer info), and supports compliance by limiting who can access content—even insiders at the provider. A practical end-to-end encryption example is two teams exchanging a draft contract: the platform can relay the file, but only endpoints can open it, delivering real end to end data protection.
Just as important is what E2EE is not. The HTTPS padlock is necessary but insufficient; many phishing sites also use HTTPS. So, is end-to-end encryption secure? Yes—when enabled and implemented correctly—but don’t mistake a secure connection for private content. Think of HTTPS as protecting the tunnel and end to end encryption as protecting what’s inside the box.
Adoption is growing across consumer and enterprise tools. WhatsApp and Signal use end-to-end encryption by default; end-to-end encryption Messenger and end-to-end encryption Instagram are available as options; email services like ProtonMail bring E2EE to mailboxes. These widely used apps make the topic accessible—answering what is E2EE, how does E2EE work, and why these defaults matter to everyday privacy.
Finally, treat E2EE as the foundation, not the finish line. Endpoint hygiene, phishing awareness, MFA, secure backups, and identity verification still matter because attackers target people and devices. Pairing strong end to end encryption with these controls is how modern teams keep communications private, resilient, and trustworthy—without sacrificing usability.
How Does End-to-End Encryption Work?
End-to-end encryption (E2EE) ensures that only the intended recipient can access a message or file. Here's how it works:
- Encryption: The sender encrypts data using the recipient’s public key.
- Transmission: The encrypted data is sent over the network, remaining unreadable to anyone intercepting it.
- Decryption: The recipient’s device decrypts the data using their private key.
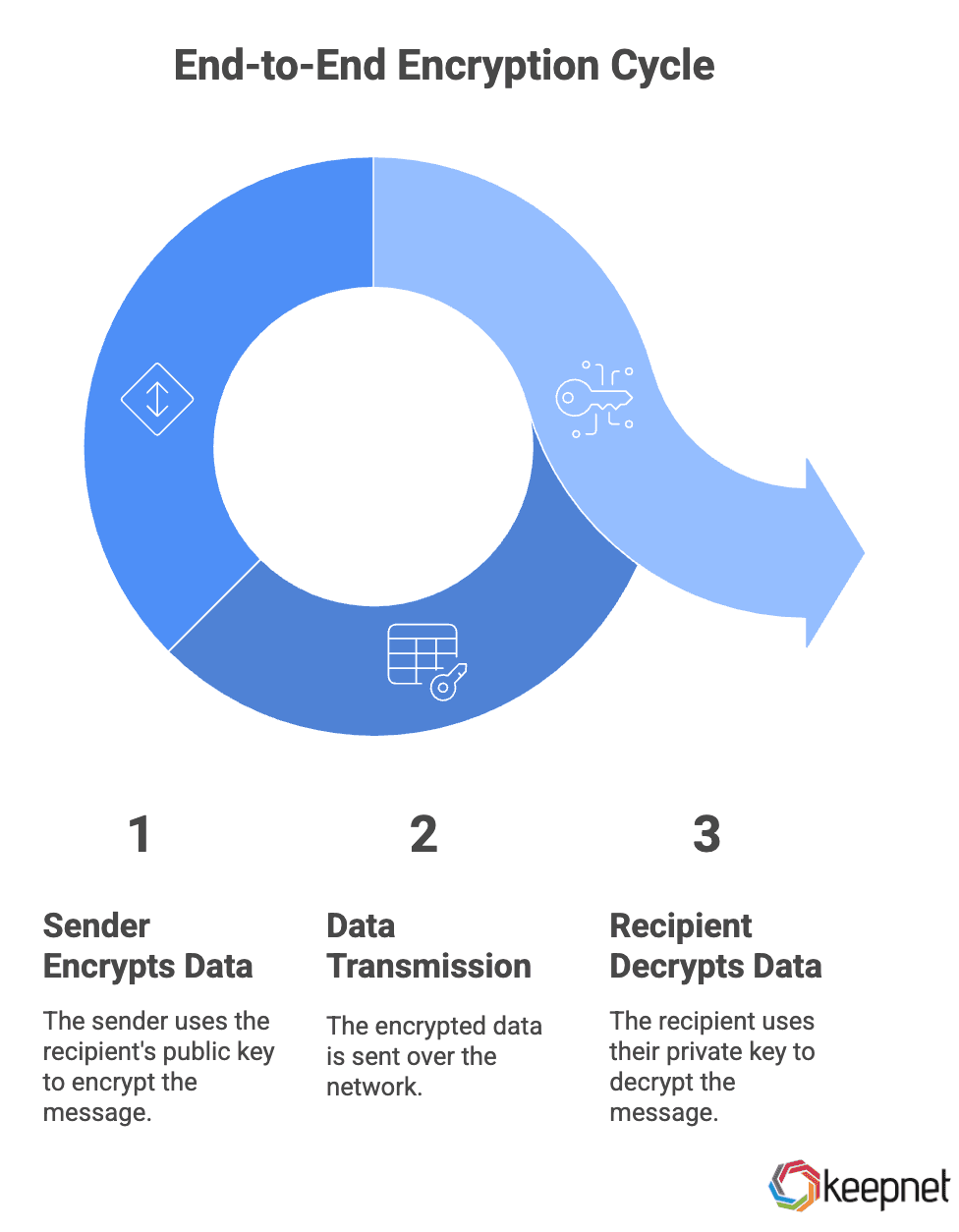
This process relies on encryption algorithms like RSA, AES, and the Signal Protocol, which power secure messaging in Telegram’s Secret Chats, iMessage, and Signal.
Where Is End-to-End Encryption Used?
When people ask what is end-to-end encryption, the more practical follow-up is: where does it actually protect me day to day? The answer: almost everywhere your private content lives or moves—messaging apps and group chats, voice/video calls, email, file sharing, and even cloud backups. With E2EE, only the sender and intended recipient can read the data; platforms move the packets but can’t peek inside.
Because threats target the places we collaborate most, E2EE shows up in tools you already use—WhatsApp and Signal for chats and calls, optional modes in Messenger/Instagram, private-by-design email like Proton, and end-to-end encrypted cloud storage. The key is knowing how end to end encryption works (keys stay on the endpoints) and whether it’s on by default or needs to be enabled per chat or product.
Below, we break down the most common places you’ll find end to end encryption and what to check to keep sensitive data truly private:
- Messaging & calling: The clearest E2EE examples are private messengers. WhatsApp and Signal protect one-to-one chats, calls, and shared files so only the sender and recipient can read them. Telegram, by contrast, uses E2EE only in Secret Chats (regular and group chats are not end-to-end encrypted), which is a crucial distinction for privacy-sensitive use cases. Messenger now rolls out end-to-end encryption by default for personal chats and calls, while Instagram offers E2EE for DMs but it isn’t on for every account by default—you can enable it per chat.
- Email: If you need end to end encryption for email, providers like ProtonMail (Proton) use strong E2EE so messages between Proton users—and even files/calendar items within the Proton ecosystem—are unreadable to the service itself. This is a practical answer to “what is end-to-end encryption in email?”: content is encrypted on your device and decrypted only on the recipient’s device.
- Cloud storage & file sharing: For end-to-end encrypted cloud storage, services such as Tresorit use client-side encryption with zero-knowledge architecture: your files are encrypted before they leave your device and remain encrypted in the cloud. That means the provider can’t read them, which is the core end-to-end encryption meaning for stored data.
- Apple ecosystem nuance (UK): Apple’s iCloud Advanced Data Protection (ADP) extends E2EE to backups, Photos, Notes, and more. However, Apple states it can no longer offer ADP in the UK for users who haven’t already enabled it. Key categories like iCloud Keychain and Health remain E2E-encrypted globally, and iMessage/FaceTime continue to use E2EE. If you’re in the UK, this means fewer iCloud categories can be protected with end-to-end encryption unless you had ADP turned on before the change.
Takeaway - where is end-to-end encryption used? Across the tools you rely on: private messaging apps (WhatsApp, Signal), Telegram Secret Chats, Messenger with default E2EE, Instagram encrypted DMs, ProtonMail for secure email, and Tresorit for end-to-end encrypted storage. The practical move is to confirm E2EE is actually enabled in each app you use—and understand platform-specific limits—so your sensitive data stays private from the network, the service, and attackers in between.
Benefits of End-to-End Encryption
End-to-end encryption keeps data private and secure, ensuring that only the sender and recipient can access it.
- Protects Privacy – Prevents hackers, service providers, and governments from reading messages or files.
- Prevents Data Breaches – Encrypts sensitive information, making it useless to cybercriminals even if intercepted.
- Secures Communication – Ensures private conversations remain confidential, whether for personal use or business.
- Builds Trust – Users and businesses can communicate securely, knowing their data is safe from unauthorized access.
E2EE is critical for safeguarding digital communication in an era of increasing cyber threats.
Challenges of End-to-End Encryption
While end-to-end encryption (E2EE) enhances security, it also comes with challenges:
- Government Regulations – Some governments push for backdoor access, arguing it hinders law enforcement investigations.
- Metadata Exposure – While E2EE protects message content, it doesn’t hide sender and recipient details, which can still be tracked.
- Endpoint Vulnerabilities – If a hacker gains access to a user’s device, E2EE won’t prevent data theft.
- Limited Adoption—Some platforms, like Telegram, offer E2EE only in specific features, leaving other data exposed.
Despite these challenges, E2EE remains a critical tool for digital privacy and security.
Popular Platforms That Use End-to-End Encryption
Several platforms use end-to-end encryption (E2EE) to secure messages, calls, and emails:
- Signal – Encrypts all messages, calls, and files by default.
- WhatsApp – Uses E2EE, but metadata (sender info, timestamps) remains visible.
- Telegram – Only Secret Chats are E2EE; regular chats are not.
- iMessage – Encrypted, but iCloud backups need Advanced Data Protection (ADP), which is no longer available in the UK.
- ProtonMail – Emails are fully E2EE, preventing even the provider from accessing them.
While these platforms enhance privacy, users should check their settings and backup policies to ensure full encryption.
How to Ensure Your Data Is Encrypted End-to-End
To protect your data with end-to-end encryption (E2EE), follow these steps:
- Use E2EE-enabled apps – Choose platforms like Signal, WhatsApp, or ProtonMail, which offer strong encryption by default.
- Check encryption settings – Some apps, like Telegram, require you to manually enable Secret Chats for E2EE.
- Keep your apps updated – Regular updates fix security vulnerabilities that attackers might exploit.
- Secure your device – Encryption won’t help if your phone or computer is compromised, so use strong passwords, biometric authentication, and security software.
By following these steps, you can ensure your private data stays protected from unauthorized access.
Common Misunderstandings About End-to-End Encryption
There are several misconceptions about end-to-end encryption (E2EE). Here’s the reality:
1. Myth: E2EE prevents all hacking.
Reality: It protects data in transit, but if a device is compromised, hackers can still access information.
2. Myth: Only messages are encrypted.
Reality: E2EE secures not just messages but also calls, files, and other shared data.
3. Myth: Service providers can still read encrypted data.
Reality: With fully implemented E2EE, only the sender and recipient have the decryption keys—not even the service provider can access it.
Understanding these facts helps users make informed security choices when using encrypted platforms.
How Keepnet Empowers Businesses with End-to-End Encryption
Keepnet's Extended Human Risk Management (xHRM) platform helps businesses strengthen security by combining end-to-end encryption (E2EE) with advanced threat protection. Through AI-driven phishing simulations, adaptive training, and automated phishing response, Keepnet ensures employees understand and apply encryption best practices to protect sensitive data like client information and financial records.
Beyond training, Keepnet’s threat intelligence and phishing defense tools enhance security by detecting and blocking attacks before they compromise encrypted communications. This approach helps organizations eliminate employee-driven threats, insider risks, and social engineering, ensuring compliance and building a strong security culture.
Explore Keepnet’s Extended Human Risk Management platform to strengthen security with AI-driven training and threat defense.
The Future of End-to-End Encryption
AI-driven features like message summarization and scam detection are changing how data is processed, raising concerns for end-to-end encryption (E2EE). Many AI systems require offloading data to external servers, potentially weakening encryption protections. Governments, especially in the UK and EU, are also pushing for AI-based content scanning, which could further compromise privacy.
Companies like Apple are developing solutions like Private Cloud Compute to process AI tasks securely, but these rely on software controls rather than encryption. As AI becomes more integrated into messaging and cloud services, the challenge will be maintaining strong encryption while enabling AI-driven convenience. (Source)
This article was updated 28 August, 2025.