What Is Pharming? Definition & Protection
Looking up pharming definition or protection? This guide explains how pharming silently redirects users via DNS poisoning or hijacking, the red flags to spot it, and a prioritized checklist CISOs can deploy, DNSSEC, secure resolvers, router hygiene, EDR, and training, to cut risk fast.
If you’re searching for “pharming definition or protection”, this guide gives you a clear meaning, shows how attacks redirect users to fraudulent websites, and outlines concrete controls your team can deploy today.
The word pharming blends the words phishing and farming. Unlike many phishing attacks that need a click, pharming silently reroutes you to fake sites, even when you type the correct URL of a legitimate website, so attackers can steal sensitive information and commit identity theft.
Pharming At a Glance (Ready Summary)
Pharming is a social engineering, enabled attack that compromises name-resolution paths to the web. It abuses how browsers turn domains into IP addresses and poisons DNS caches or local hosted files (like the hosts file) so traffic is covertly redirected.
Because a pharming page can look perfect, many victims never notice they’ve been rerouted. Defense therefore hinges on layered technical controls (DNSSEC, secure resolvers, EDR/anti-malware), router hygiene, and continuous Security Awareness Training tailored to non-technical staff.
How Pharming Works (DNS, IP addresses, hosts files)
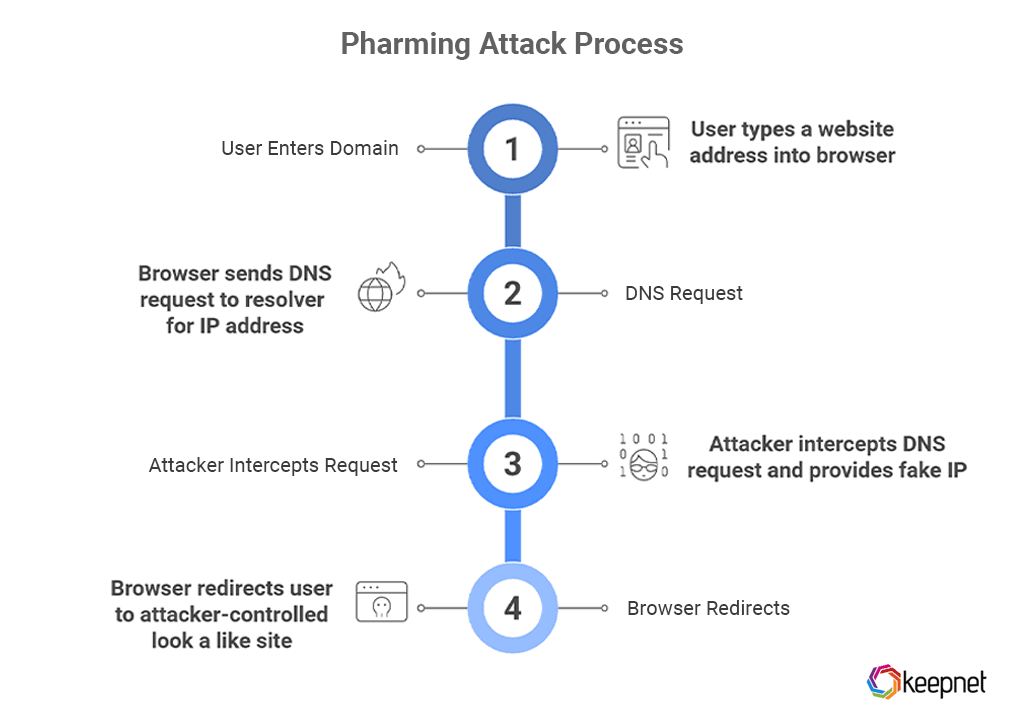
At its core, pharming tampers with the steps your device follows to resolve a domain. Normally, your browser asks a DNS resolver for the site’s IP address.
In a pharming scenario, an attacker corrupts that decision point so the request redirects users to a look-alike site the attacker controls. Two dominant patterns explain how pharming works in practice and why standard anti-virus alone isn’t enough.
Types of Pharming Attack
Pharming shows up through two families of techniques. Both end with the victim on a counterfeit site that collects sensitive information like credentials or payment data.
Malware-based pharming
Here, the endpoint is infected, often after a user downloaded a Trojan from a spoofed email, malicious attachment, or drive-by page. The malware plants or edits locally hosted files (e.g., the hosts file) and may alter DNS settings on the device or home router.
From then on, requests for a bank or SaaS domain silently resolve to an attacker IP. Because the redirection happens after you press Enter, even cautious users who never click unknown links can be trapped.
DNS cache poisoning & DNS hijacking
Instead of touching every endpoint, attackers target resolvers. DNS cache or server poisoning injects bogus mappings into a resolver’s memory so many users are redirected to fraudulent websites. DNS hijacking swaps a user’s or router’s DNS settings for rogue resolvers. The impact scales fast, one poisoned resolver can funnel an entire office to attacker fake sites, including through public Wi-Fi where unprotected routers are common.
Pharming vs. Phishing (and why it matters)
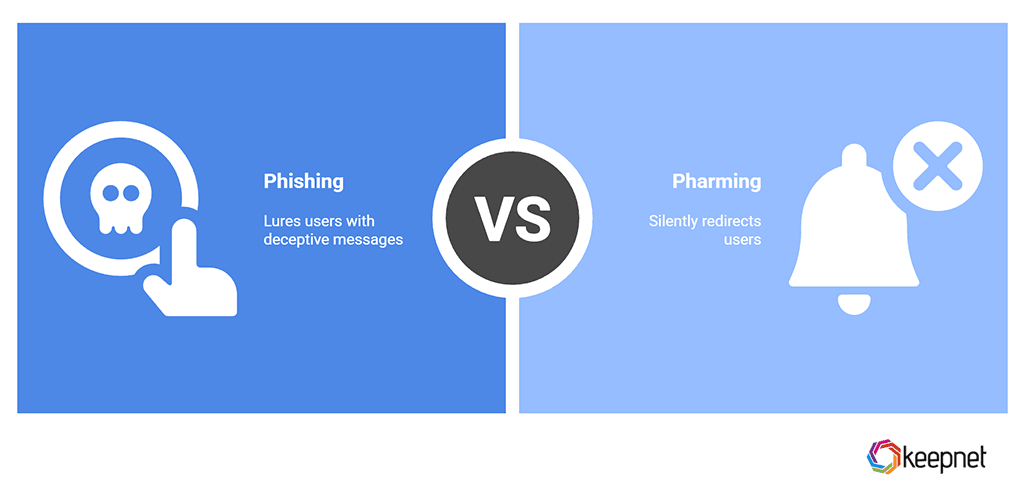
Phishing lures users to a bad page, usually with a message, link, or attachment. Pharming removes the lure: no link is needed. That makes it harder to spot and more dangerous at scale.
In the real world, attackers blend pharming and phishing, using a phish to install malicious code and then relying on silent redirection after. Your program should therefore treat pharming as an escalation path of phishing attacks, not a separate problem.
Red Flags and Real-world Examples
Even sophisticated pharming leaves traces. Pages that “feel off,” unusual fonts or layouts, certificate warnings, login prompts surfacing in odd flows, or a sudden block from your EDR when visiting a familiar site are all clues.
On the user’s side, watch for unexpected MFA prompts, account alerts, or odd posts on social media, all signs that a legitimate website may have been impersonated.
The “50 financial institutions” incident
One of the best-known examples hit 50 financial organizations across regions in the late 2000s. Users were redirected to fake sites that captured credentials while malicious code also tried to install additional payloads.
The campaign mixed DNS manipulation with endpoint compromise (a downloaded a trojan) and spread quickly before takedowns.
The lesson: pharming is not theoretical; it targets high-value services and scales fast.
Protection Checklist From Pharming Scams
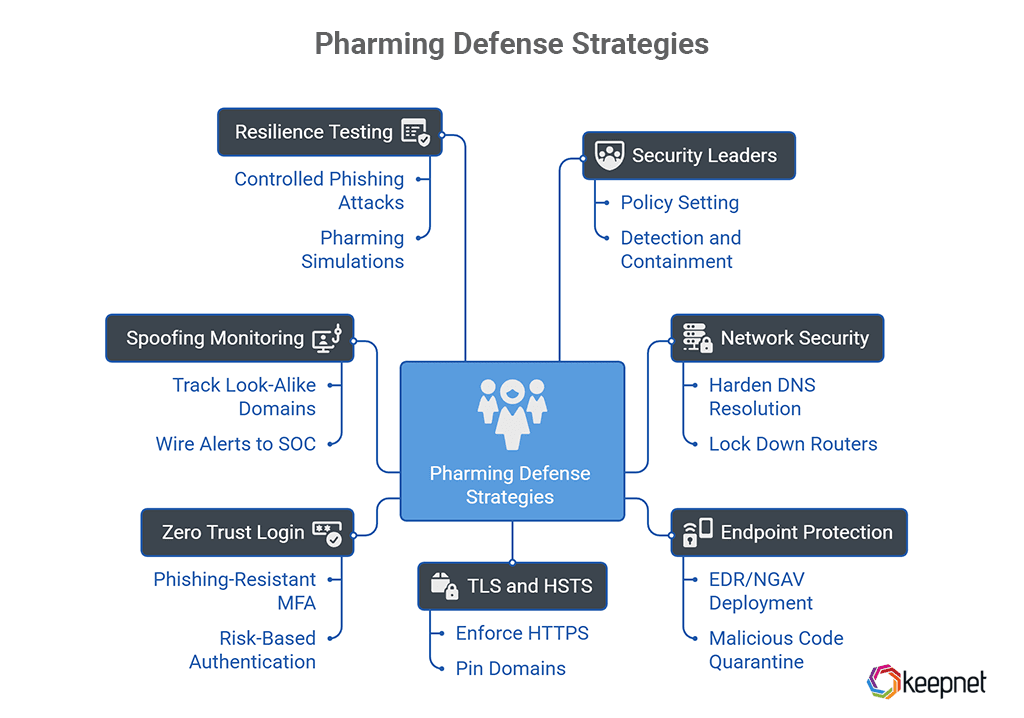
Pharming defense requires depth, controls at the endpoint, the network, the resolver, and the human layer. Use the list below to harden your stack and reduce the blast radius.
Controls for Security Leaders (CISOs, Heads of IT)
Set policy that assumes redirection will happen somewhere and focuses on detection and containment.
- Harden DNS resolution: Enforce secure resolvers with DNSSEC validation and DNS filtering. Prefer provider networks that monitor for poisoning and block known fraudulent websites.
- Lock down routers & WAN edges: Change default admin passwords, disable remote admin, apply automatic firmware updates, and verify DNS settings on all branch routers; block outbound port-53 except to approved resolvers.
- Endpoint protection: Deploy EDR/NGAV that detects hosts-file tampering, unauthorized DNS changes, and browser injections; quarantine malicious code and roll back.
- TLS and HSTS: Enforce HTTPS everywhere. Pin domains for critical internal services. Use web gateways that inspect certificates and strip or block downgrade attempts.
- Zero Trust login: Add phishing-resistant MFA (FIDO2), risk-based authentication, and social engineering–aware verifications for high-risk actions.
- Monitor for spoofing: Track look-alike domains and “combo-squats”; wire alerts to your SOC.
- Resilience testing: Run controlled phishing attacks plus pharming simulations (DNS swap / hosts-file tamper in a lab) to validate detection and user responses.
Controls for Employees and Front-line Managers
Give colleagues clear rules that are easy to follow under pressure.
- Pause on odd UX: If a banking or payroll page looks “nearly right,” stop. Check the address bar, padlock, and certificate details before entering sensitive information.
- Use trusted networks: Avoid unknown public Wi-Fi; if you must, use a corporate VPN.
- Verify alerts: If you receive a sign-in notification or payment request, confirm through a second channel.
- Keep software current: Updates close known holes used by malicious code.
- Report quickly: Early reports cut losses; treat strange redirects like any other incident.
Buyer’s Note: Where Vendor Capabilities Help
Practical safeguards include secure DNS services, network policies that force resolvers, and EDR capable of catching hosts-file edits.
But technology isn’t enough. You’ll close the remaining gap with role-based training, behavior nudges, and recurring phishing simulations that keep the “this looks off” instinct sharp, especially for finance and customer teams who handle high-value workflows.
How to Stop Pharming Attacks with Keepnet Human Risk Management
Pharming exploits human trust and invisible plumbing. To reduce risk at scale, combine technical hardening with measurable behavior change. Keepnet’s Human Risk Management Platform helps quantify and reduce people-driven risk across email, web, voice, SMS, QR and MFA fatigue vectors.
Keepnet’s Security Awareness Training delivers adaptive, localized micro-lessons that teach staff to spot fraudulent websites and report odd redirects. And Phishing Simulator runs multi-channel tests, email, voice, SMS, and more, to stress-test controls and behaviors end-to-end. Keepnet has been chosen a Strong Performer by Gartner for consecutive years, and we’re ready to help you translate policy into protection.
Editor’s note: This blog was updated November 30, 2025