What Is Tabnabbing? Definition and Protection
Tabnabbing is a phishing trick where an inactive browser tab changes into a fake login page. When you return, you may enter credentials. Protect yourself by checking the URL, using MFA, and closing unused tabs.
Tabnabbing is a phishing technique that tricks you inside your own browser. Instead of relying only on email links, attackers take advantage of something very human: we keep many tabs open, we multitask, and we trust tabs that “feel familiar.”
In a tabnabbing attack, a page you opened earlier (and forgot about) can be swapped or redirected so that, when you come back, you see a realistic login screen and enter your credentials, without realizing the tab is no longer the site you originally opened.
Tabnabbing definition
Tabnabbing is a browser-based phishing attack where an attacker changes what an inactive tab shows (page content, title, and even the favicon) to impersonate a trusted site. When the user returns to that tab and sees a convincing “session expired—please log in” screen, they enter credentials that go directly to the attacker.
A closely related (and widely discussed) variation is reverse tabnabbing, where a newly opened tab can manipulate the original tab through window.opener and replace it with a phishing page.
How tabnabbing works
A tabnabbing flow usually looks like this:
- You open a legitimate-looking page (or a page that appears safe enough to browse).
- You leave the tab open while you move to other work.
- The inactive tab gets changed (either via a redirect or by a linked page leveraging browser behavior in specific scenarios).
- You return later and see a familiar brand and a login prompt.
- You type your credentials, and the attacker captures them.
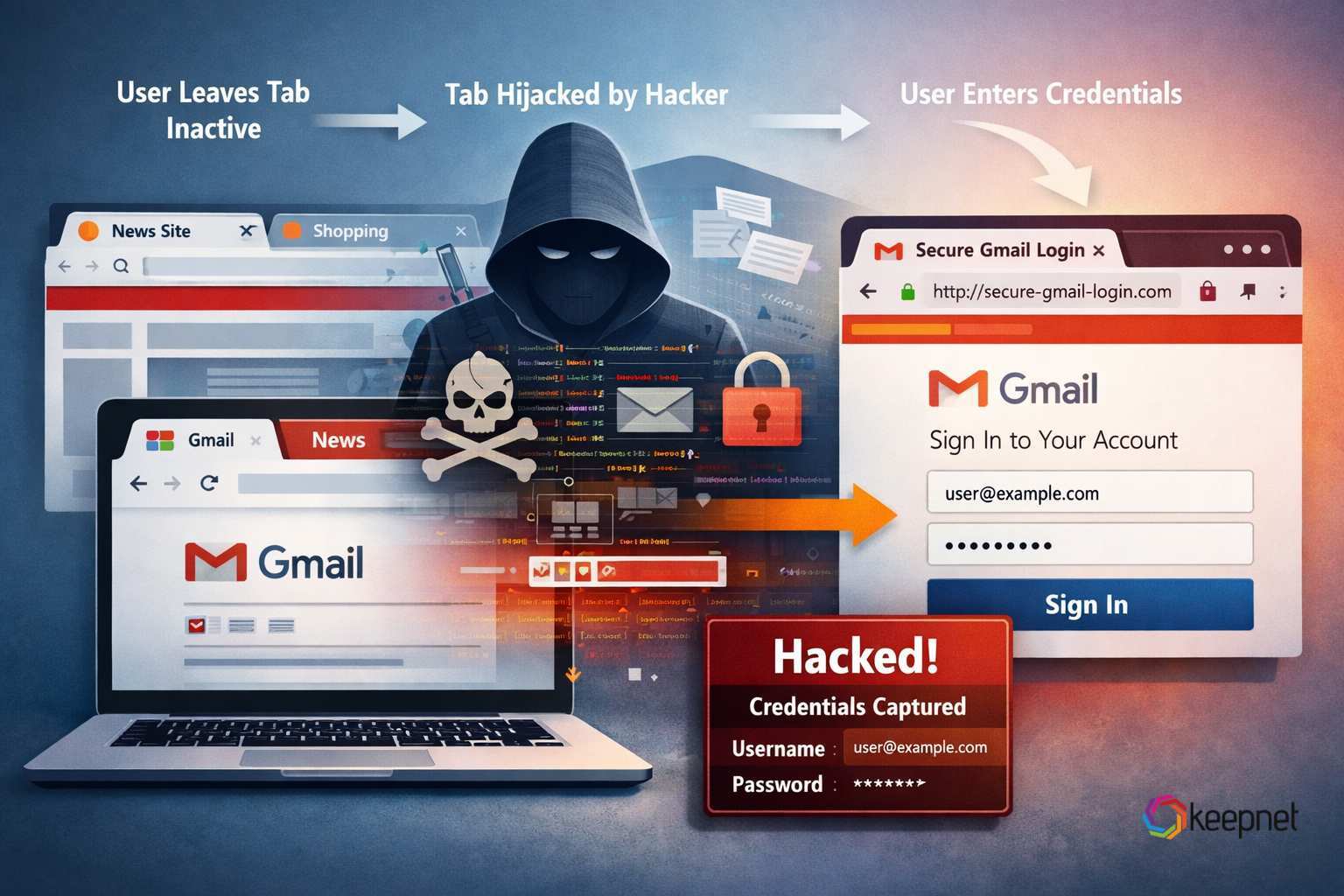
The reason it works is simple: your brain sees a known logo + a login form and assumes it’s the same tab you opened earlier.
Tabnabbing vs. traditional phishing (and reverse tabnabbing)
Traditional phishing typically depends on luring you to a fake page via email.
Tabnabbing shifts the battlefield to your open tabs, where your guard is lower because you think you’re “already on the right site.”
Reverse tabnabbing is especially relevant to website owners: if your site opens external links in a new tab (target="_blank") without protection, that new page may be able to rewrite the original page and swap it with a phishing site.
Why tabnabbing is dangerous
Tabnabbing can lead to:
- Account takeover (email accounts are the “master key” for password resets)
- Credential stuffing risk (reused passwords across services)
- Business email compromise pathways if corporate credentials are captured
- Follow-on social engineering, because attackers can message colleagues from a compromised account
And because it’s “just a login page,” victims often don’t realize anything happened until later.
Common signs you’re seeing a tabnabbing attempt
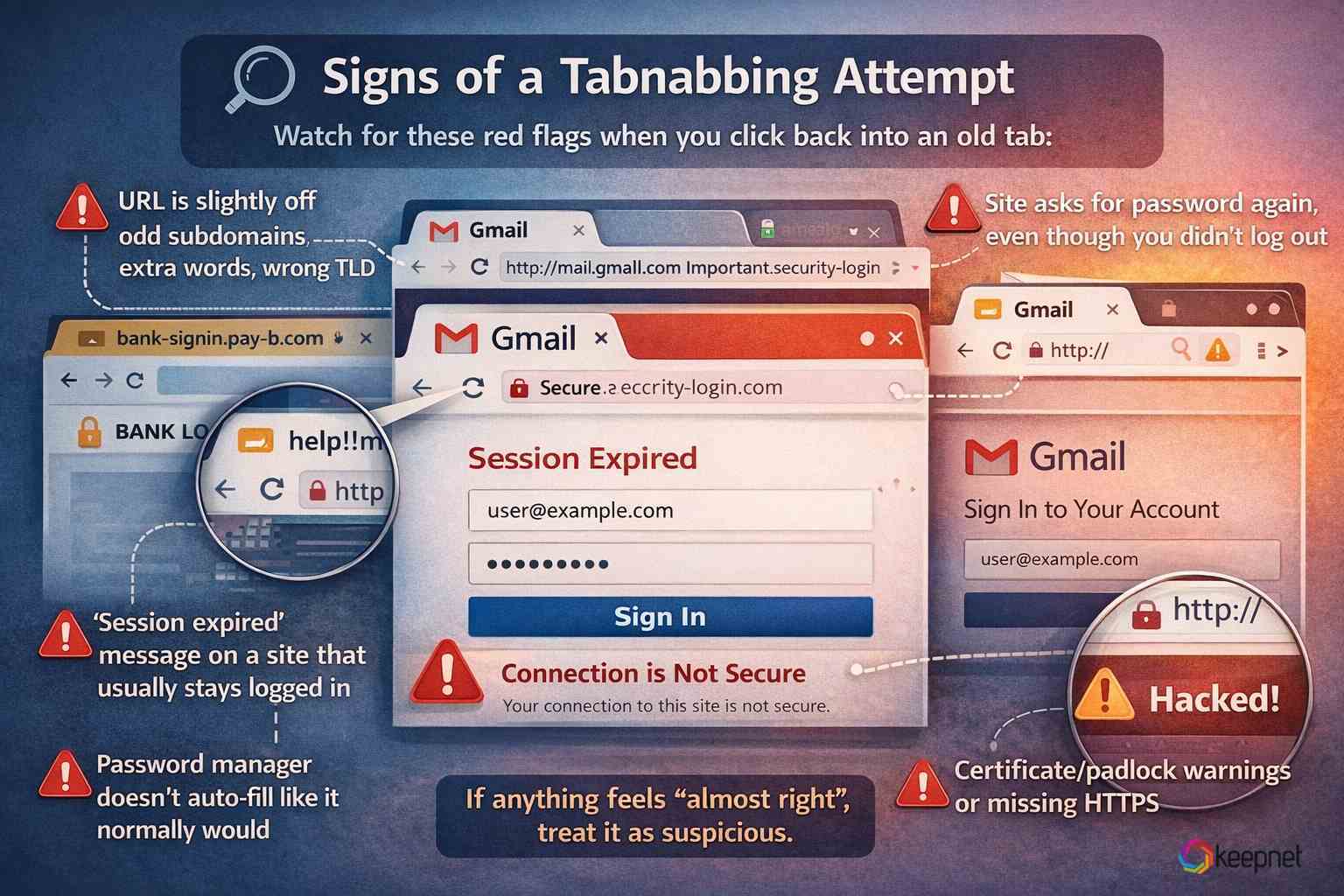
When you click back into an old tab, watch for these red flags:
- The URL is slightly off (extra words, odd subdomains, wrong TLD)
- A sudden “session expired” message on a site that usually stays logged in
- The site asks for a password again even though you didn’t log out
- The browser password manager doesn’t auto-fill where it normally would
- Certificate/padlock warnings or a missing HTTPS indicator
If anything feels “almost right,” treat it as suspicious.
How to protect yourself from tabnabbing (end-user checklist)
These are practical defenses that reduce risk immediately:
Keep your tab hygiene simple
- Close tabs you no longer need (especially financial, admin, and email tabs).
- If you must keep many tabs open, consider grouping them and closing groups when done.
Always verify the URL before logging in
This is the #1 habit that beats tabnabbing. If the login prompt appears unexpectedly, glance at the address bar first.
Use a password manager
Password managers are a strong “anti-phishing layer” because they tend not to fill credentials on lookalike domains. If auto-fill doesn’t trigger, pause.
Turn on MFA (prefer phishing-resistant where possible)
Even if credentials are stolen, MFA can prevent access, especially with stronger methods.
Update your browser
Modern browser security improves constantly; staying updated helps reduce exposure.
How to protect your organization (security + awareness)
Tabnabbing sits in the overlap between technical controls and human behavior. The strongest organizations do both:
- Use security awareness tools to train employees to verify URLs and distrust surprise login prompts.
- Test your employees against phishing attacks using simulated phishing tests.
- Use phishing-resistant MFA for critical systems.
- Monitor for suspicious logins, impossible travel, and anomalous sessions.
- Reduce credential reuse with SSO and strong password policies.
Protection for website owners and developers (reverse tabnabbing fix)
If your website uses links that open in a new tab, protect users by preventing the new page from accessing window.opener.
Add rel="noopener" (or rel="noreferrer") to external links with target="_blank"
Example:
<a href="https://example.com" target="_blank" rel="noopener noreferrer">
External resource
</a>
Why this matters:
- rel="noopener" tells the browser not to set window.opener, so the new page can’t control the page that opened it.
- rel="noreferrer" prevents leaking referrer data and (per MDN) also behaves as if noopener was specified.
- Chrome’s own guidance (including Lighthouse best practices) recommends using rel="noopener" or rel="noreferrer" with target="_blank" to prevent these vulnerabilities.
This is one of those rare security wins that is easy, low-cost, and high-impact.
How Keepnet Human Risk Management Platform Helps Against Tabnabbing Phishing
Tabnabbing is a good reminder that many attacks don’t “break” technology—they bend attention. The best defense is a combination of safer web practices (like rel="noopener") and consistent user education that reinforces URL verification, MFA habits, and reporting culture.
If you’re building an organization-wide program, Keepnet’s Human Risk Management Platform helps you measure and reduce risky behaviors over time with adaptive learning and risk analytics, while Security Awareness Training and the Phishing Simulator help teams practice spotting real-world lures (including browser-based deception patterns) before attackers do.
Keepnet’s simulation and awareness capabilities are built for modern social engineering, and the tool has been named a go-to vendor for stopping deepfake and AI disinformation attacks by Gartner.