What Is an Account Takeover Attack?
Account takeover (ATO) is when criminals hijack online accounts using stolen credentials, session tokens, or MFA bypass tricks. Learn signs, risks, and how to prevent ATO.
An Account Takeover (ATO) attack is when a cybercriminal gains unauthorized access to an online account (email, banking, SaaS, social media, employee SSO, etc.) and uses it as if they were the real owner, often to steal money, data, or identities, or to spread further attacks.
The most common path is still simple: stolen usernames and passwords. But modern ATO has evolved. Attackers increasingly rely on infostealer malware, session token theft, and MFA bypass techniques, meaning accounts can be compromised even when the password is never typed again.
Why Account Takeover is such a big deal now
ATO is “high ROI” for attackers: one compromised account can unlock payments, stored cards, loyalty points, private messages, password resets, and sometimes an entire organization’s cloud tools.
And credential-based entry remains extremely common. In Verizon’s 2025 DBIR research, compromised credentials were an initial access vector in 22% of breaches reviewed.
How Account Takeover happens
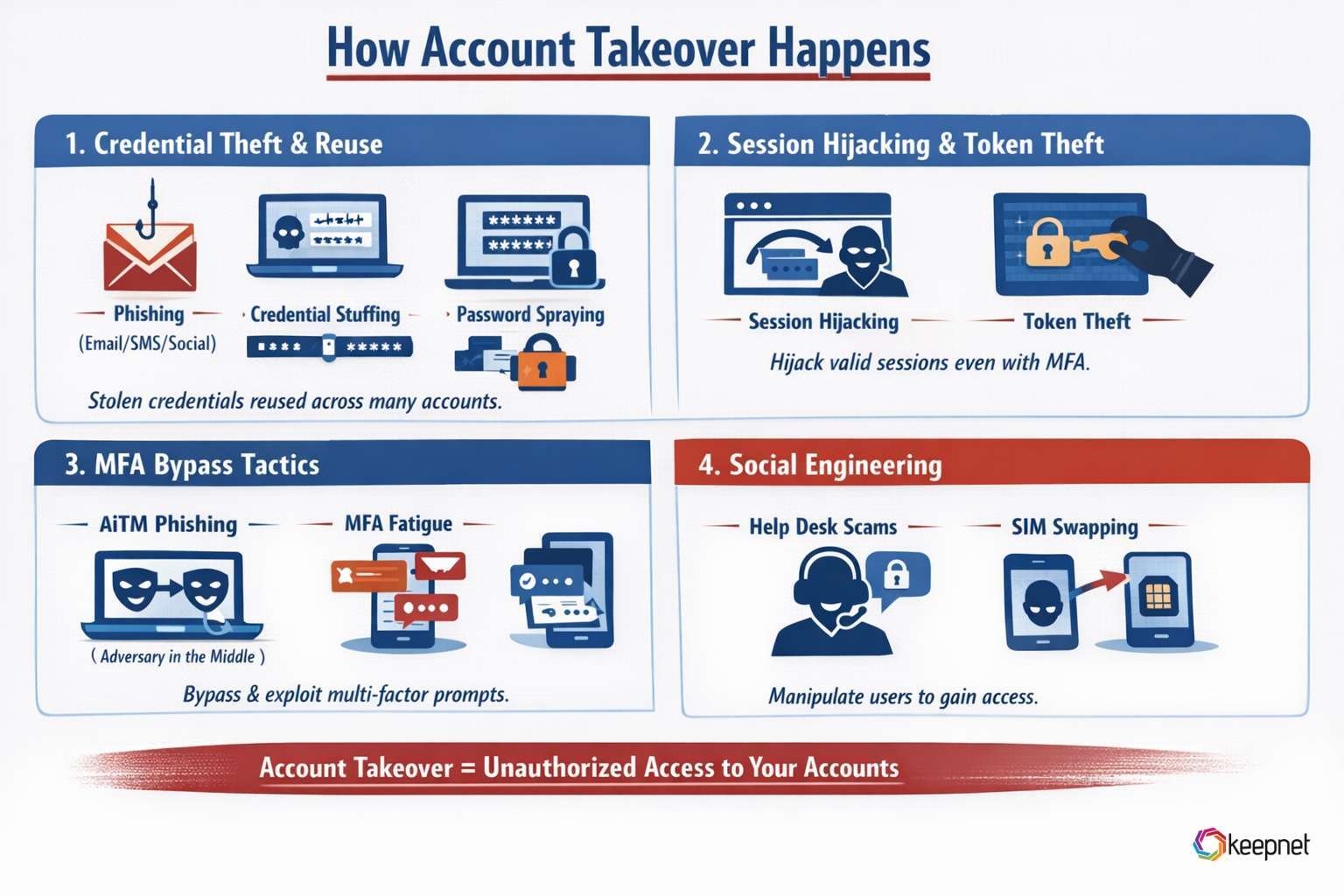
Account takeover usually follows one of these routes (high-level, defensive view):
1) Credential theft and reuse
- Phishing (email/SMS/social) that tricks a user into revealing credentials
- Credential stuffing (automated testing of leaked username/password pairs)
- Password spraying (trying common passwords across many accounts)
Credential stuffing is a well-documented automated threat: attackers test credentials stolen from other breaches because password reuse is widespread.
2) Session hijacking and token theft
Threat actors increasingly use approaches like:
- Adversary-in-the-middle (AiTM) phishing to steal sessions in real time
- MFA fatigue / prompt bombing to pressure a user into approving a login
- Token theft to bypass prompts entirely
This is why security teams increasingly push phishing-resistant MFA rather than “any MFA.”
4) Social engineering around the login
Examples:
- Help desk manipulation (reset requests, identity verification tricks)
- SIM swapping to intercept SMS-based codes (where SMS is used)
Account Takeover vs. account hijacking vs. identity theft
You’ll see these terms used together:
- Account takeover: Unauthorized access to a specific account (email, bank, SaaS).
- Account hijacking: Often used interchangeably with ATO.
- Identity theft: Broader—using stolen identity data to open new accounts, apply for credit, or impersonate someone elsewhere.
ATO can be the “first domino” that leads to identity theft.
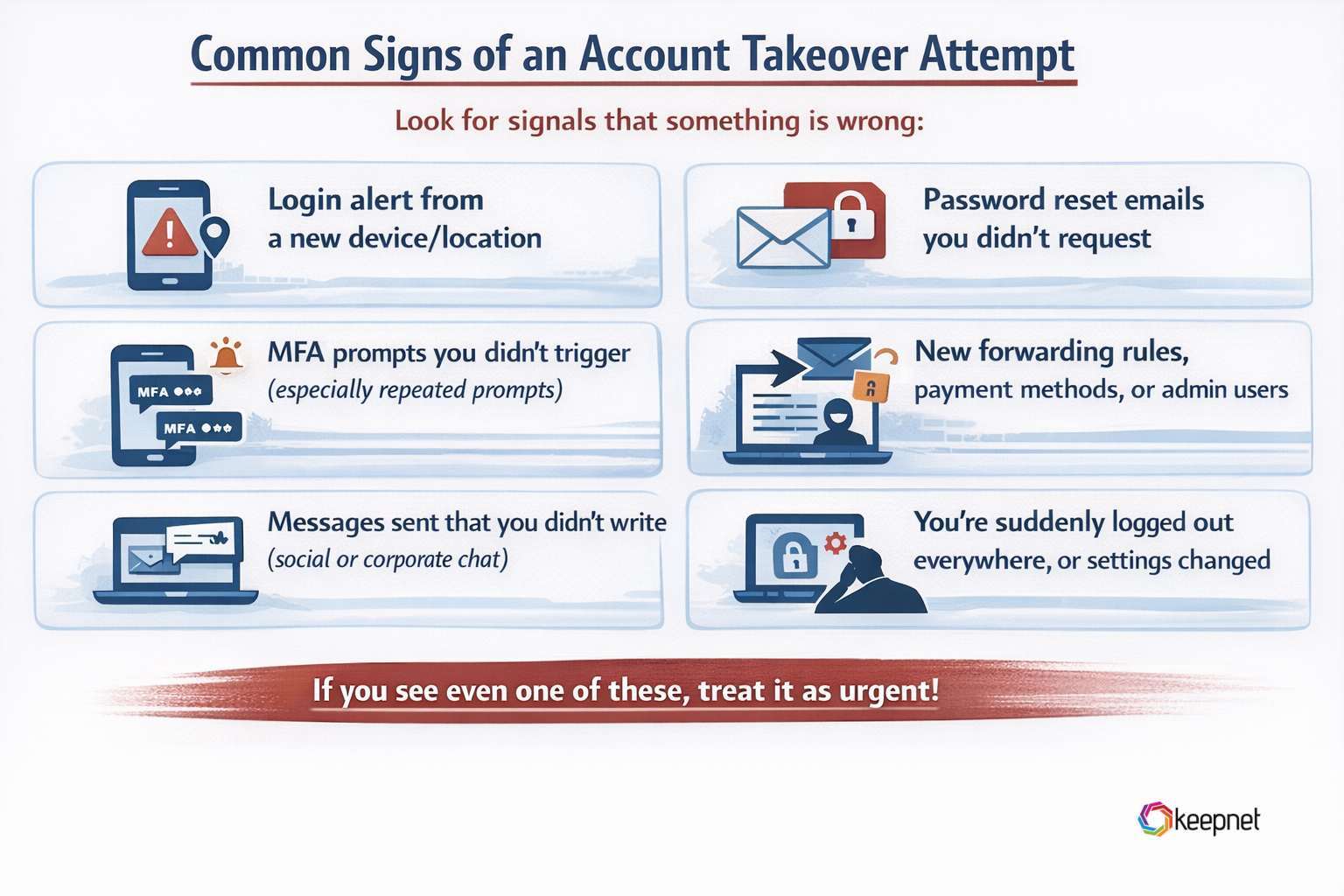
Common signs of an Account Takeover attempt
Look for signals that something is wrong:
- Login alert from a new device/location
- Password reset emails you didn’t request
- MFA prompts you didn’t trigger (especially repeated prompts)
- New forwarding rules in email, new payment methods, new admin users
- Messages sent that you didn’t write (social or corporate chat)
- You’re suddenly logged out everywhere, or settings changed
If you see even one of these, treat it as urgent.
The impact of ATO (individuals and businesses)
For individuals
- Fraudulent purchases, drained balances, stolen reward points
- Locked out of accounts
- “Cascade compromise” (email takeover → resets for other services)
For organizations
- Business email compromise, payroll diversion, vendor fraud
- Data exposure through SaaS apps and cloud drives
- Lateral movement from one compromised account to many more
How to prevent Account Takeover
End-user checklist (fast wins)
- Use unique passwords (a password manager makes this realistic). Verizon’s research highlights that password reuse remains a major enabler.
- Enable MFA everywhere—but prefer stronger options where available.
- Move to phishing-resistant MFA (passkeys/FIDO/WebAuthn) when your services support it. CISA notes FIDO/WebAuthn as the only widely available phishing-resistant authentication approach.
- Treat unexpected MFA prompts as an attack (deny + report).
- Keep devices and browsers updated (reduces malware and token theft exposure).
- Watch your inbox rules (forwarding rules are a classic “silent persistence” trick).
Organization checklist (what actually reduces ATO at scale)
1) Upgrade authentication (reduce credential value)
- Adopt phishing-resistant MFA (FIDO2/WebAuthn) for high-risk users and critical systems.
- Use risk-based authentication (step-up auth on suspicious logins)
- Shorten session lifetime for sensitive apps; bind sessions to device posture where possible
2) Stop automated attacks at the front door
Credential stuffing is automated and often large-scale; one breach can put many other services at risk.
Defenses:
- Rate limiting, intelligent lockouts, bot detection
- Password breach checks (block known-compromised passwords)
- Monitoring auth logs for “low-and-slow” abuse patterns (Verizon also notes how credential stuffing blends into normal traffic).
3) Detect takeover behavior (not just “bad passwords”)
Use signals like:
- Impossible travel / anomalous geo
- Device fingerprint changes
- High-risk actions right after login (changing email, payout method, MFA settings)
4) Secure recovery paths (attackers love resets)
- Harden help desk workflows
- Reduce reliance on SMS for high-risk resets
- Require step-up verification for email changes, payout changes, admin role grants
What to do if you suspect your account was taken over

- Reset password immediately (from a clean device if possible).
- Revoke sessions (“log out of all devices”).
- Check MFA settings (remove unknown authenticators/backup methods).
- Review account rules/settings (email forwarding, recovery email/phone, app passwords).
- Notify your IT/security team (work accounts) and monitor for follow-on attempts.
How Keepnet Helps Businesses Stay Vigilant Against Account Takeover (ATO) Attacks
Account takeover rarely starts with “hacking.” It usually starts with a human moment—an employee enters credentials into a lookalike page, approves an unexpected MFA prompt, shares a verification code over the phone, or scans a malicious QR code. That’s why stopping ATO requires more than technical controls. It requires continuous, measurable behavior change.
Keepnet helps organizations reduce account takeover risk by combining Security Awareness Training with realistic simulations and coaching, so employees learn what attackers actually do—and what to do next.
Train the behaviors that prevent ATO
With Keepnet, you can teach employees the exact habits that block takeover paths, such as:
- verifying URLs before logging in
- recognizing credential-harvesting lures and fake login pages
- resisting MFA fatigue and suspicious approval requests
- reporting suspicious prompts and social engineering attempts fast
- following verification steps during support calls and “urgent” requests
Test employees with real-world simulations (not guesswork)
Keepnet’s Phishing Simulator enables multi-channel simulations that mirror how attackers capture credentials and bypass defenses—helping you identify risk before criminals do. You can run targeted exercises using:
- SMS phishing simulator (smishing) to test one-time code theft and fake “security alerts”
- Voice phishing simulator (vishing) to test help desk manipulation and impersonation attempts
- Deepfake phishing simulator to prepare teams for AI-driven voice impersonation
- QR phishing simulator (quishing) to reduce “scan-and-trust” behavior
- MFA phishing simulator to train employees against push fatigue and fake MFA flows
- Callback phishing simulator to stop “call this number now” lures that lead to credential capture
Reduce human risk with measurable improvement
Instead of one-off awareness, Keepnet supports ongoing improvement through tracking and reinforcement—so you can see:
- which roles and teams are most exposed to ATO techniques
- how reporting rates improve over time
- whether risky behaviors are decreasing after training and simulations
If you want to turn your ATO guidance into action,
Keepnet helps you test, train, and measure employee readiness across today’s most common takeover pathways.
Keepnet’s simulation and awareness capabilities are built for modern social engineering, and the tool has been named a go-to vendor for stopping deepfake and AI disinformation attacks by Gartner.