What Is Spyware? (2025 Guide)
Spyware is malicious software that secretly monitors and collects user data without consent. Learn how it works, the risks it poses to organizations, and proven strategies to prevent spyware infections in your business network.
Spyware is software that secretly monitors activity and exfiltrates data from a device, without informed consent. It can capture keystrokes, screen content, messages, credentials, location, microphone/camera feeds, and browser data, then send that information to a remote controller. Spyware ranges from “commercial” tools marketed to governments (often called mercenary or commercial surveillance spyware) to criminal info‑stealers and domestic‑abuse stalkerware. Google’s Threat Analysis Group notes that commercial surveillance vendors (CSVs) sell exploits and spyware to infiltrate consumer devices, typically targeting journalists, dissidents, and high‑risk users.
How Spyware Works?
Spyware covertly runs on your device to record keystrokes, capture files and track behavior, then forwards the stolen data to criminals for fraud or surveillance.
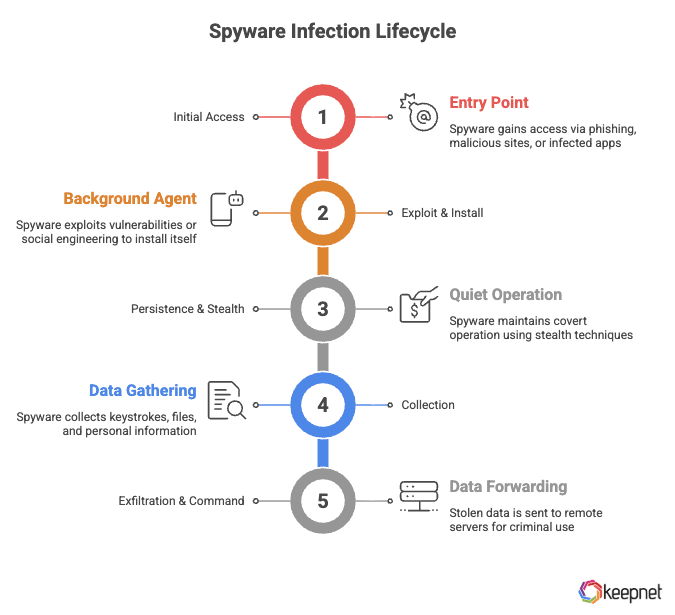
- Initial access: Phishing links/attachments, malicious websites (drive‑by), trojanized apps, supply‑chain attacks, or physical access.
- Exploit & install: Some strains use zero‑days (previously unknown vulnerabilities) or social engineering to install a background agent. A 2024 analysis of zero‑day exploitation highlights the continued use of 0‑days in the wild, including by CSVs.
- Persistence & stealth: Obfuscated services, launch agents, configuration profiles, or boot‑level implants keep the spyware running quietly.
- Collection: Keystrokes, screenshots, browser cookies/tokens, call logs, GPS, mic/cam, cloud backups, password vaults.
- Exfiltration & command: Data is sent to remote servers; operators can update modules, expand privileges, and pivot to other accounts.
Types of Spyware
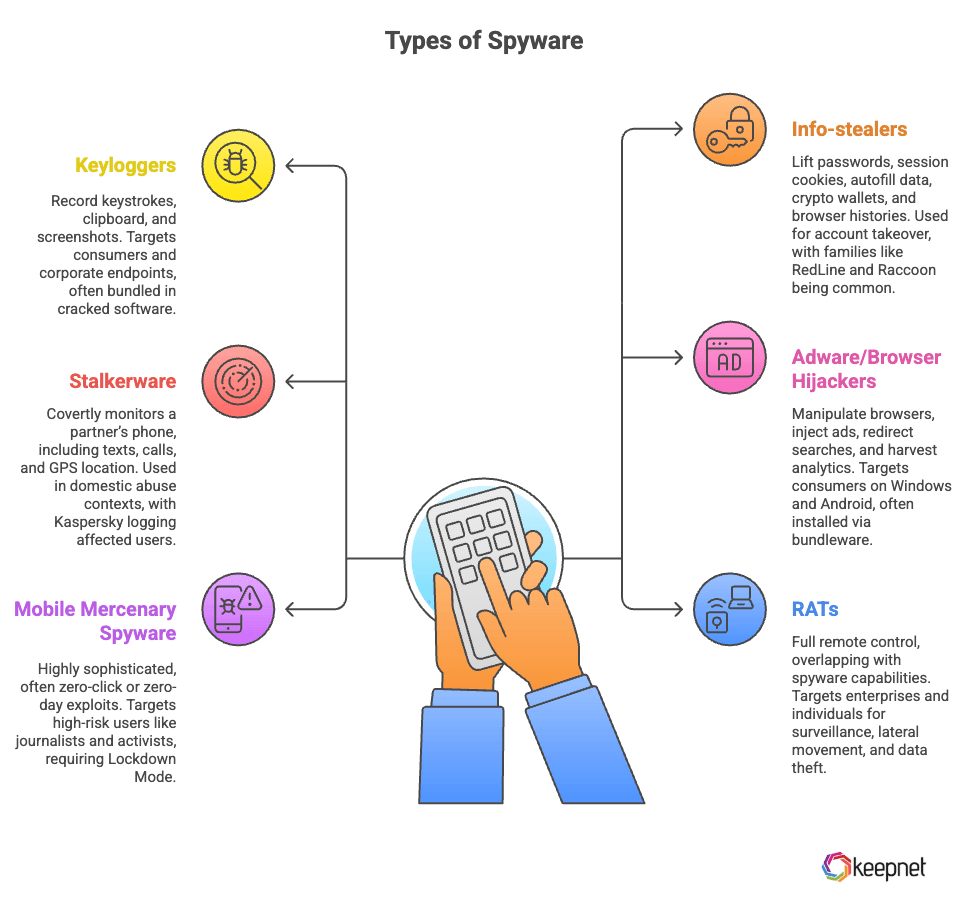
Types of spyware include keyloggers, info-stealers, stalkerware, adware, mobile mercenary spyware, and remote access trojans, each designed to secretly monitor, steal, or control user data and devices. See details in table below:
| Type | What it does | Typical targets | Notable examples / notes |
|---|---|---|---|
| Keyloggers | Record keystrokes, clipboard; may grab screenshots. | Consumers & corporate endpoints. | Often bundled in cracked software or “free” utilities. |
| Info-stealers | Lift passwords, session cookies, autofill, crypto wallets, browser histories. | Broad criminal use for account takeover (ATO). | Families like RedLine, Raccoon, Vidar, Lumma; Recorded Future noted infostealer dominance in H1 2024. |
| Stalkerware | Covertly monitors a partner’s phone (texts, calls, GPS). | Domestic abuse contexts. | Kaspersky logged 31,031 affected unique users in 2023 (+5.8% YoY). |
| Adware / browser hijackers | Manipulate browsers, inject ads, redirect searches; harvest analytics. | Consumers (Windows/Android). | Often installed via bundleware or rogue extensions. |
| Mobile mercenary spyware | Highly sophisticated; often 0-click / 0-day exploitation. | High-risk users (journalists, activists, officials). | Apple documents threat notifications and recommends Lockdown Mode for at-risk users. |
| RATs (remote access trojans) | Full remote control; overlaps with spyware capabilities. | Enterprises & individuals. | Used for surveillance, lateral movement, and data theft. |
Table 1: Types of spyware
Top 30 Spyware Statistics & Trends
Spyware attacks are rising worldwide, with significant number of new samples detected daily. Check top spyware statistics and trends below:
- 80% of all internet users have been affected by spyware.
- 93% of the components required for spyware to work are already present in computers.
- Unwanted software and adware account for 50% of mobile malware deliveries in 2022.
- 16% of mobile malware is in the form of malvertising in Q1 2024.
- Android Minecraft clones infected with adware were installed 35 million times in 2023.
- There are over 1 billion active malware programs worldwide, including sophisticated nation-state developed spyware, in 2024–2025.
- Mobile malware infections have surged dramatically, with Android devices 50 times more likely to be compromised than iOS devices in 2024–2025.
- Iran leads global mobile malware infection rates at 30.3% in 2024–2025.
- In 2024, 20 new US-based spyware investors were identified, bringing the total number of American backers of commercial spyware to 31.
- The growth in US spyware investors outpaced other major investing countries such as Israel, Italy, and the United Kingdom in 2024.
- A global survey of 561 entities across 46 countries between 1992 and 2024 identified 34 new investors, bringing the total to 128.
- The number of identified investors in the EU Single Market plus Switzerland stands at 31, with Italy accounting for the largest share at 12.
- Investors based in Israel number 26 as of 2024.
- The global spyware market is growing and evolving, with additions of four new vendors, seven new resellers or brokers, 10 new suppliers, and 55 new individuals linked to the industry in 2024.
- Three new countries were linked to spyware activity in 2024: Japan, Malaysia, and Panama.
- iOS zero-click exploits (e.g., Pegasus-like spyware) were implicated in 3% of mobile infections studied in Q2 2023.
- The top mobile malware families in 2023 include SpyNote, XLoader, and FluBot.
- Attackers exploited 75 zero-day vulnerabilities in the wild in 2024, with over 50% linked to spyware attacks.
- Zero-day exploits decreased from 97 in 2023 to 75 in 2024, but the average trend line shows a steady increase in zero-day exploitation.
- More than half of attributable zero-day attacks in 2024 were conducted by cyber-espionage threat actors, including government-backed groups and commercial surveillance vendors' customers.
- China-linked groups exploited five zero-days in 2024.
- Commercial surveillance customers exploited eight zero-days in 2024.
- North Korean operators were linked to five zero-day exploits in 2024 for the first time, blending cyber espionage and financial motives.
- 97 zero-days were exploited in attacks in 2023, a surge of over 50% compared to 62 in 2022, with many linked to spyware vendors and their clients.
- Annual counts of zero-day exploitation have fluctuated over the past four years, but the average trend shows a steady increase.
- In 2024, end-user platforms and products (e.g., web browsers, mobile devices, and desktop operating systems) bore 56% of tracked zero-days.
- Browser exploits fell from 17 in 2023 to 11 in 2024.
- Mobile device zero-days dropped from 17 in 2023 to nine in 2024.
- Desktop operating system exploits rose from 17 in 2023 to 22 in 2024, with Windows zero-days climbing to 22.
- Attackers exploited 33 of the 75 zero-day flaws (44%) to target products used primarily in business environments in 2024, up from 37% in 2023.
How to tell if you have spyware
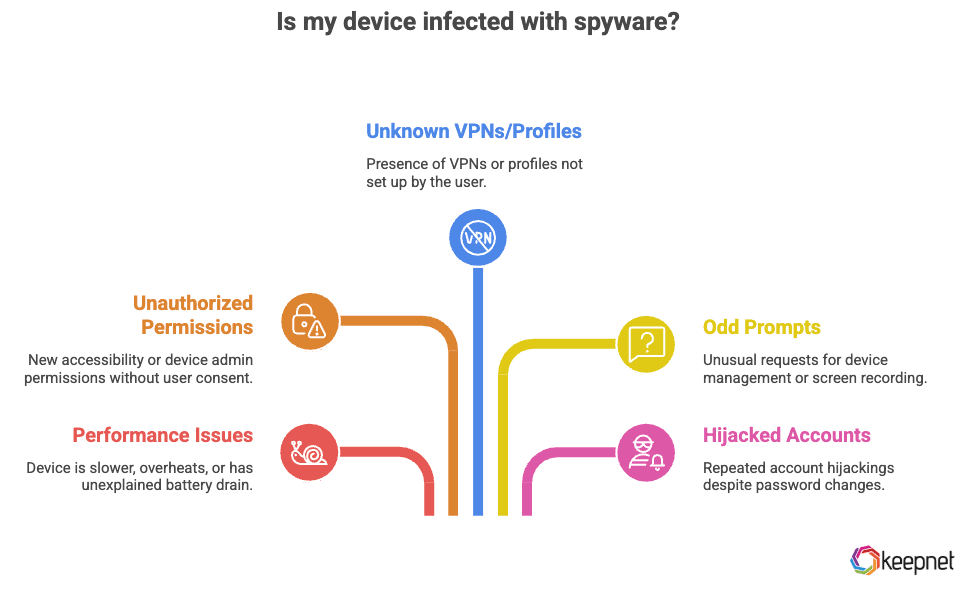
You may have spyware if your device is slower than usual, shows unexpected pop-ups, drains battery quickly, overheats, or sends unusual network traffic without your action. Check details below:
- Unexplained battery drain, data spikes, overheating, or persistent background activity.
- New accessibility or device admin permissions you didn’t enable.
- Unknown VPNs, profiles, rooted/jailbroken status—especially if you didn’t do it.
- Odd prompts for device management or screen recording permissions.
- Accounts repeatedly hijacked despite password changes (a sign of stolen cookies/tokens).
Checks that help (safe & practical):
- Update the OS first. Many mercenary‑spyware attacks exploit 0‑days that vendors later patch. Google’s 2024 analysis underscores active zero‑day exploitation trends.
- Look for suspicious profiles & apps (mobile), unknown extensions (browsers), or lateral movement alerts (enterprise SIEM/EDR).
- Enable iOS Lockdown Mode if you are high‑risk (journalist, activist, politician, election worker, etc.). Apple explicitly recommends it in mercenary‑spyware contexts.
- High‑risk forensic check. The Mobile Verification Toolkit (MVT) can help trained technologists look for known spyware traces on iOS/Android. (Intended for experts; not a casual consumer tool.)
How to Remove Spyware Safely
If you believe you’re targeted by mercenary or domestic‑abuse spyware and personal safety is at risk: Seek expert help first (e.g., a trusted security response team or digital rights helpline). Do not tip off an abuser/opponent.
For individuals
- Isolate & update: Disconnect from untrusted networks, then update the OS and apps.
- Back up what you control, then reset: For mobile, perform a full factory reset (don’t restore from potentially tainted backups). For desktops, consider a clean reinstall from a known‑good image.
- Scan devices: Use reputable anti‑malware. Then review login sessions and revoke tokens/sessions on Google, Apple, Microsoft, password managers, etcb
- Rotate credentials carefully: Change passwords after cleaning, enable passkeys/FIDO2 where possible, and turn on MFA (avoid SMS; prefer app or security keys).
- Harden the account surface: Review account recovery options, app passwords, forwarded mail rules, OAuth grants, and browser extensions.
For organizations
- Containment: EDR isolate hosts; block C2 infrastructure, revoke OAuth tokens, disable compromised identities, and rotate secrets.
- Reimage from gold: Rebuild affected endpoints and mobile devices; re‑enroll via MDM/EDR.
- Credential hygiene: Organization‑wide credential resets for impacted realms; invalidate SSO sessions.
- IR & legal: Preserve forensic artifacts; coordinate with legal/compliance if surveillance laws may be implicated.
How to Prevent Spyware: Individual & Enterprise
To prevent spyware, individuals should use trusted antivirus tools, avoid suspicious downloads, update software regularly, and limit app permissions. Enterprises should enforce endpoint protection, use network monitoring, apply patch management, and train employees on phishing and social engineering threats. Check details below:
Individuals
- Keep OS and browsers fully patched; install apps only from official stores.
- Avoid sideloading and “modded” apps; beware permission creep.
- Use passkeys/security keys and reputable password managers.
- On iOS, high‑risk users should consider Lockdown Mode; on Android, avoid Developer Mode unless needed.
- Treat unexpected links/attachments as hostile; verify out‑of‑band.
Enterprises
- Baseline controls: EDR + MDM/MAM, DNS filtering, application allow‑listing, macro/script controls, and browser isolation for risky content.
- Identity‑first security: Phishing‑resistant MFA, just‑in‑time/admin elevation, conditional access, and continuous session risk evaluation.
- Exploit mitigation: Rapid OS/browser patch SLAs; threat‑informed validation against current 0‑day classes. 2024 analyses show 0‑days remain a live channel for spyware deployers.
- User protection: Regular phishing and social‑engineering training; clear escalation playbooks for suspected surveillance.
- High‑risk posture: For executives/journalists/NGO staff, deploy high‑risk mobile profiles (no sideloading, reduced attack surface, monitored comms) and have an expert‑run triage path (MVT or vendor services). Guidance from CISA and partners can help shape hardening programs.
Legal & Ethical Notes
- Installing monitoring software on someone else’s device without explicit, lawful consent is illegal in many jurisdictions.
- Governments now impose sanctions and visa restrictions for misuse of commercial spyware. Organizations should vet vendors and enforce strict governance. U.S. Department of State.
How Keepnet Helps Against Spyware
Keepnet empowers organizations to prevent, detect, and respond to spyware threats through its Extended Human Risk Management Platform. Spyware often spreads through deceptive links, malicious attachments, or social engineering tactics — areas where human error is the key entry point.
- Phishing Simulations: Keepnet’s multi-channel simulations (email, voice, SMS, QR, MFA fatigue) train employees to recognize and report spyware delivery attempts before infection occurs.
- Security Awareness Training: Engaging, localized, and gamified training helps users identify suspicious apps, pop-ups, and fake software updates — the most common spyware vectors.
- Threat Intelligence & Reporting: Keepnet provides actionable insights on emerging spyware campaigns and user behavior, allowing IT teams to spot risks early and strengthen defenses.
- Incident Response & Analytics: With automated reporting and behavior analytics, enterprises can measure human risk levels and close gaps that spyware actors exploit.
By combining education, simulation, and analytics, Keepnet transforms employees from the weakest link into a resilient defense layer against spyware and other social engineering attacks.
Glossary
- 0‑day: A vulnerability with no available patch at time of exploitation.
- CSV (Commercial Surveillance Vendor): Company selling exploits and spyware to clients (often governments).
- Info‑stealer: Malware that harvests credentials, cookies, and browser data for ATO.
- Stalkerware: Software used to covertly monitor an intimate partner’s device.
- Lockdown Mode (iOS): An optional mode that reduces attack surface for high‑risk users.
- MVT: Mobile Verification Toolkit used by investigators to detect known traces of mobile spyware.
Editor’s note: This blog was updated November 30, 2025