Adversary-in-the-Middle (AiTM) Phishing: How to Detect, Prevent, and Protect Your Business in 2025
AiTM phishing attacks bypass traditional MFA, leading to severe business compromise. Learn to spot and prevent AiTM using behavioral analytics, AI-powered detection, and proactive security measures tailored for today’s phishing landscape.
Adversary-in-the-Middle (AitM) phishing is the natural evolution of the classic Man-in-the-Middle (MitM) attack, supercharged by inexpensive cloud reverse proxies and phishing-as-a-service kits. In a typical AitM campaign, the attacker silently inserts a malicious proxy between the victim’s browser and a legitimate service—Microsoft 365, Google Workspace, Okta, you name it. Every keystroke, push notification, FIDO passkey, or session cookie flows through that proxy, allowing the adversary to replay the entire authentication sequence in real time and walk away with both the credentials and a live session token. From the victim’s perspective the login feels flawless; from the attacker’s perspective the perimeter has already fallen.
Why should CISOs, red‑teamers, and DevSecOps engineers care? Because AitM neutralises the very controls we’ve spent the last decade deploying—multi‑factor authentication, passkeys, device‑bound certificates—by stealing the evidence of authentication after the user has supplied it. Once inside, adversaries bypass conditional‑access rules, launch business‑email‑compromise (BEC) fraud, and pivot laterally through SaaS environments in minutes, shrinking dwell time to near zero.
The numbers are impossible to ignore. The Veriff Identity Fraud Report 2025 recorded a 46 % year‑over‑year surge in AitM incidents across high‑value verticals such as finance and iGaming (veriff.com). And just days ago, researchers revealed how threat actors are abusing the QR‑code fallback in FIDO passkeys to sidestep hardware MFA during AitM campaigns, proving that even so‑called “phishing‑resistant” solutions can be undermined (techradar.com).
Bottom line: If your 2025 security roadmap doesn’t explicitly address Adversary‑in‑the‑Middle phishing, you’re planning for yesterday’s threat landscape.
How Adversary-in-the-Middle (AiTM) Phishing Works
Unlike classic phishing, AiTM weaponises your own successful MFA flow against you—stealing the “proof” of authentication rather than guessing or brute-forcing it:
Step-by-Step Mechanics of an AiTM Attack
Understanding the step-by-step mechanics of an AI-Driven attack is important for developing effective defenses and protecting sensitive information:
- The lure: Victims receive a persuasive email, SMS, or social-media DM that masquerades as a routine “Sign-in required” notification. A cleverly crafted URL hides a reverse-proxy domain such as m365-login-secure[.]com.
- Transparent reverse proxy spins up: Tools like EvilProxy, Tycoon 2FA, Sneaky 2FA or open-source kits (Evilginx, Modlishka) stand between the victim’s browser and the legitimate service (e.g., Microsoft 365). The HTTPS certificate is real, so the lock icon offers no comfort.  
- Credential harvesting & real-time relay: The user types a username and password into a pixel-perfect facsimile of the real page. The proxy forwards those credentials upstream so the service behaves normally, while storing a local copy for the attacker. 
- MFA interception/replay: When the service issues an MFA challenge (TOTP, push, WebAuthn, even FIDO passkey QR fallback), the proxy relays it instantly. The victim resolves the prompt, believing it legitimate, and the proxy siphons off the resulting session cookie or OAuth token. 
- Session hijack & persistence: Armed with a live, fully authenticated session, the attacker scripts API calls or logs in through headless browsers, bypassing Conditional Access and geo-fencing. They may set up additional app passwords, register new MFA devices, or drop malicious OAuth apps to persist. 
- Post-compromise operations: Common next steps include Business-Email-Compromise wire-fraud templates, data-exfiltration from cloud drives, and lateral movement into SaaS admin portals.
Real-World Scenario: “Operation Sneaky Invoice”
Imagine your CFO finishing a late flight check-in. An email marked Urgent: invoice approval lands in her inbox. She taps the link, sees Microsoft 365’s familiar login, enters credentials, and approves her push notification. Within 40 seconds attackers—running the Sneaky 2FA PhaaS kit identified in early 2025—have cloned her session cookie, created a new Outlook rule that hides replies, and launched $1.3 million of wire requests to APAC suppliers before breakfast. The entire breach required no malware on the endpoint and no password-reset link—just a relay.  
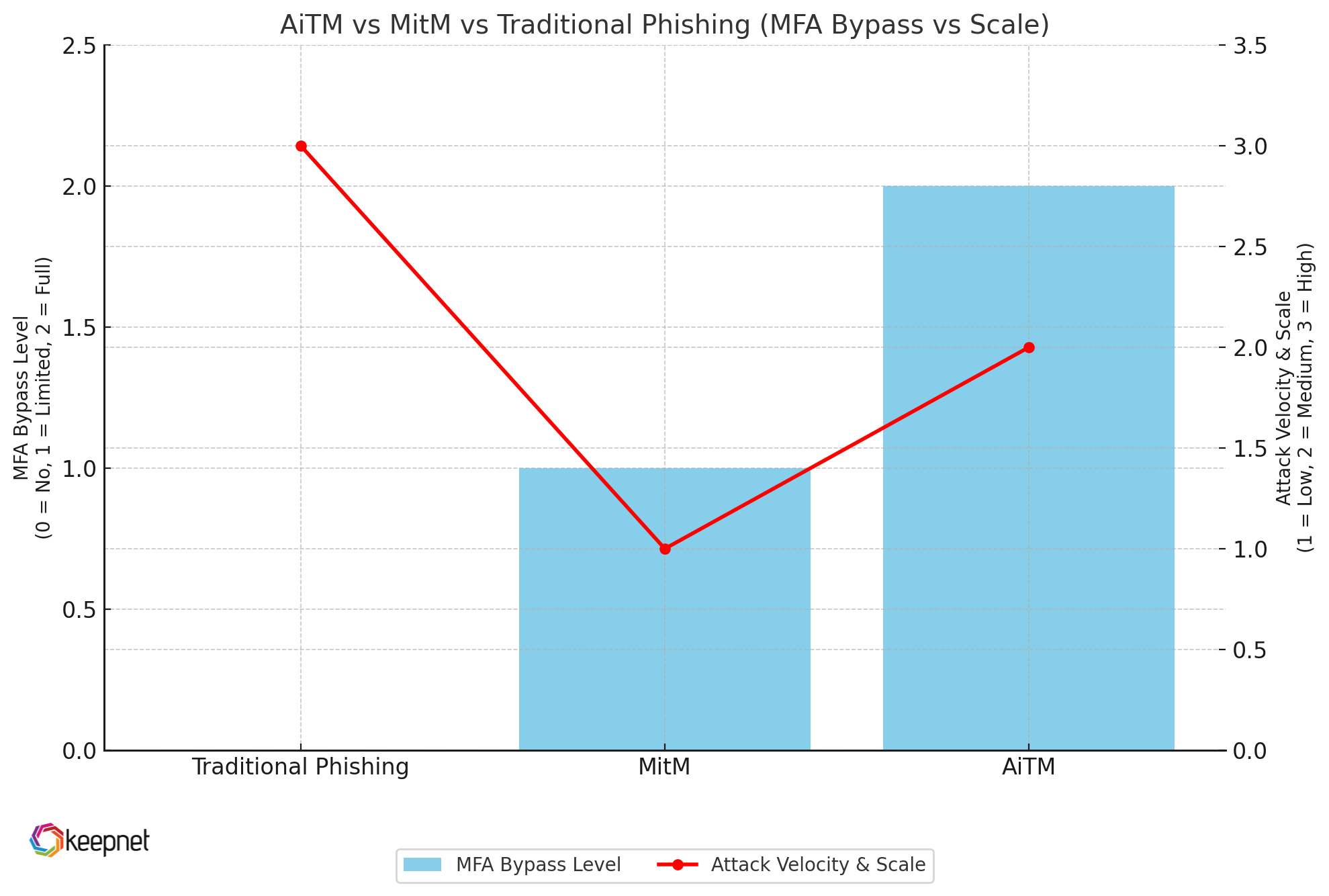
AiTM vs classic MitM vs “spray-and-pray” phishing
MitM attacks focus on intercepting raw traffic at the network layer; AiTM proxies the application layer, giving it surgical access to authentication flows.
| Attack Vector | MFA Bypass Capability | Attack Velocity & Scale |
|---|---|---|
| Traditional credential phishing | No – stops at password | Very high (mass-scale via email/SMS) |
| Man-in-the-Middle (MitM) | Limited – SSL stripping or cert abuse needed | Low (requires LAN or physical proximity) |
| Adversary-in-the-Middle (AiTM) | Yes – token & cookie theft after MFA | High (cloud-based kits, PhaaS dashboards) |
Table 1: AiTM vs MitM vs Traditional Phishing
AiTM phishing collapses the security stack by turning your own successful MFA handshake into an access token. If your roadmap stops at “enable MFA,” you’re defending yesterday’s threat landscape.
Types of Adversary-in-the-Middle (AiTM) Phishing Attacks
AiTM isn’t a single trick, it’s a family of rapidly evolving tactics that weaponise the very authentication flows designed to keep us safe. Below are the four dominant flavours every CISO and red-team lead must track in 2025.
Credential-Harvesting AiTM Attacks
Credential-harvesting AiTM attacks work using a cloud-hosted reverse proxy (EvilProxy, Tycoon 2FA, Sneaky 2FA) that clones a Microsoft 365 or Google Workspace login page pixel-for-pixel. The victim’s username and password are streamed to the attacker while being forwarded upstream so the real service accepts them without error.
- Why it’s lethal: Automation built into Phishing-as-a-Service (PhaaS) kits lets operators stand up thousands of fake tenants, rotate domains, and refresh TLS certs daily; Sekoia recorded a 67 % quarter-over-quarter spike in live EvilProxy URLs in 2025.  
- Defence priority: Enforce Conditional Access policies that flag “impossible travel” and require phishing-resistant MFA on first-seen devices.
Session Hijacking AiTM Attacks
Instead of storing passwords for later use, the proxy steals the session cookie or OAuth token generated after MFA. Attackers replay it through a headless browser or the Microsoft Graph API, materializing inside the inbox within seconds.
- Real-world proof: ANY.RUN’s April 2025 timeline shows Tycoon 2FA adding browser-fingerprinting evasion and encrypted payload delivery specifically to protect stolen session cookies from detection tooling. 
- Why it’s lethal: Even forced password resets won’t kick the intruder out; they’re riding a fully authenticated token.
- Defence priority: Bind tokens to device IDs, enable continuous access evaluation (CAE) so revoked cookies die immediately, and hunt for duplicate sessions on new fingerprints.
MFA Interception & Replay AiTM Attacks
The proxy relays push approvals, TOTP codes, or WebAuthn challenges in real time. Because the victim completes MFA, the attacker does too—nothing is “broken,” it’s simply duplicated.
- 2025 snapshot: Researchers observed broad campaigns in which AiTM operators harvested more than 500,000 fresh MFA tokens in under three weeks, fuelled by subscription PhaaS dashboards that show live “MFA-passed” counts to affiliates. 
- Why it’s lethal: Security teams often trust a successful MFA event and lower their guard; AiTM weaponises that trust.
- Defence priority: Shift to phishing-resistant WebAuthn with device-bound secrets and alert on duplicate approvals from disparate IPs within 60 seconds.
QR-Code-Based AiTM Phishing
Modern passkeys and some hardware FIDO keys allow a cross-device sign-in fallback: scan a QR code on one device to approve on another. AiTM proxies exploit this workflow by surfacing a bogus QR code that the victim dutifully scans, handing over a fresh FIDO assertion in the process.
- Breaking news: The July 2025 “PoisonSeed” campaign showed attackers bypassing FIDO keys at scale using spoofed portals that forced the QR fallback, prompting Microsoft and Okta to rush guidance on disabling the feature.  
- Why it’s lethal: It undercuts the strongest MFA we have and tricks users who believe they are using hardware-secured login.
- Defence priority: Disable cross-device QR fallback, require Bluetooth proximity or USB touch for passkeys, and educate staff that unsolicited QR prompts are now a red flag.
Key Takeaways for 2025
- Credential harvesting is no longer the end-game—session hijack is.
- MFA interception proves “MFA-enabled” is not the same as “MFA-safe.”
- QR phishing drags even FIDO keys into the AiTM risk surface.
- Every tactic is industrialised by PhaaS, so speed of detection is paramount.
If your security roadmap doesn’t explicitly test, monitor, and block all four AiTM variants, you’re leaving a gap that modern adversaries are already monetising.
Comprehensive Report on Real-Life AiTM Phishing Incidents ( Case Studies)
Adversary-in-the-Middle phishing attacks represent a sophisticated evolution of traditional phishing, where attackers intercept communications between users and legitimate services to steal credentials, session cookies, and other sensitive data. These attacks are particularly dangerous because they can bypass multi-factor authentication, a security measure many organizations rely on. Below is a detailed analysis of prominent real-world AiTM phishing incidents from recent news, including case studies, lessons learned, and mitigation strategies, supported by reputable sources.
Darktrace Case Study: Dropbox-Based AiTM BEC Attack (October 2024)
A multi-stage AiTM Business Email Compromise (BEC) attack leveraged Dropbox to deliver phishing links. Attackers targeted lower-priority users, exploiting Dropbox’s trusted reputation to encourage users to click malicious links embedded in emails with subject lines like “FirstLast shared ‘Filename’ with you.” Techniques included session cookie theft and MFA bypass, with suspicious activities such as logins from rare geolocations (e.g., Kenya, IP 41.90.175.46) and registration of new MFA methods via Microsoft Authenticator.
- Detection and Mitigation: Darktrace’s AI-driven security platform identified anomalous login patterns and MFA changes, escalating the issue to their Security Operations Center (SOC). Autonomous response mechanisms disabled the compromised SaaS account, preventing data exfiltration. The customer was notified to reset passwords and implement remedial actions.
- Lessons Learned: Trusted cloud services like Dropbox are prime targets for AiTM attacks due to their widespread use and perceived legitimacy. Real-time monitoring for unusual login locations and MFA changes is critical for early detection. Autonomous response systems can effectively contain attacks by quickly disabling compromised accounts.
Microsoft Security Blog: Banking Sector AiTM and BEC Campaign (June 2023)
A multi-stage AiTM phishing and BEC campaign targeted banking and financial services organizations, originating from a compromised trusted vendor. The threat actor, tracked as Storm-1167, used an indirect proxy instead of a reverse proxy, providing greater control and flexibility in phishing page design. Attackers stole session cookies to bypass MFA, performed session replay attacks, and modified MFA methods without challenge, including adding a OneWaySMS method with an Iranian phone number. The campaign sent over 16,000 emails in a second-stage phishing effort, using unique seven-digit codes in email subjects to track targets.
- Detection and Mitigation: Microsoft’s detection alerts identified stolen session cookies, possible AiTM attempts, suspicious inbox manipulation rules, and anomalous tokens. Mitigation actions included revoking session cookies, rolling back MFA modifications, and requiring MFA re-challenges for updates.
- Lessons Learned: Compromised trusted vendors can serve as entry points for sophisticated AiTM attacks. Indirect proxies enhance attackers’ ability to customize phishing campaigns. Comprehensive monitoring and rapid response to detection alerts are essential to limit damage.
Proofpoint Case Study: Tycoon 2FA PhaaS Attack on Microsoft 365 (April 2025)
A large-scale AiTM phishing attack targeted thousands of organizations worldwide using the Tycoon 2FA Phishing-as-a-Service (PhaaS) platform. The attack mimicked Microsoft 365 authentication screens, customized with the target organization’s Entra ID (formerly Azure Active Directory) branding. Attackers stole usernames, passwords, 2FA tokens, and session cookies, using advanced evasion tactics like invisible Unicode characters, custom CAPTCHAs, and anti-debugging features.
- Detection and Mitigation: Proofpoint’s Nexus AI platform detected the threat by identifying suspicious URL domains, uncommon senders, precision-validated phishing, reverse proxy techniques, and custom branding on phishing pages. The attack was detected within customer data, even behind defenses of six other email security vendors, three of which are leaders in the 2024 Gartner Magic Quadrant for Email Security Platforms. Recommended protections include enhanced authentication (e.g., FIDO2 hardware tokens), user education, improved email filtering, and advanced threat detection systems like Proofpoint’s Account Takeover Protection (ATO) and Targeted Attack Protection (TAP)
- Lessons Learned: PhaaS platforms like Tycoon 2FA enable attackers to launch sophisticated AiTM campaigns at scale. Custom-branded phishing pages increase the likelihood of deceiving users. Multi-layered defenses, including advanced authentication and user training, are critical to counter such threats.
Zscaler Case Study: Gmail-Targeted AiTM Attack (July 2022)
An AiTM phishing attack targeted enterprise users of G Suite (Gmail), specifically chief executives, senior members, and their assistants in the US. The same threat actor behind a previous Microsoft-targeted campaign used similar tactics, techniques, and procedures (TTPs), with infrastructure overlap (e.g., loftds[.]com redirector)
Phishing emails impersonated Google, posing as password-expiry reminders to prompt users to click malicious links.
The attack chain involved multiple URL redirections, Open Redirect abuse of Google Ads and Snapchat, and client-side fingerprinting to evade automated analysis systems. The attack bypassed Gmail’s MFA using proxy-based phishing kits.
- Detection and Mitigation: Zscaler detected the attack, identifying indicators like HTML.Phish.Gmail. Users were advised to verify URLs before entering credentials to prevent falling victim to such attacks.
- Lessons Learned: AiTM attacks are not limited to Microsoft services; other platforms like Gmail are also vulnerable. Senior executives are prime targets for BEC due to their access to sensitive data and authority. MFA alone is insufficient; user vigilance in verifying URLs is important.
Technical Breakdown: Behind the Scenes of an AiTM Attack
To truly defend against Adversary-in-the-Middle phishing, we need to dissect how these attacks are engineered from the ground up. From domain spoofing to token replay automation, modern AiTM campaigns operate like professional SaaS products—complete with dashboards, live metrics, and modular toolchains. This section unveils the technical anatomy of a full-blown AiTM operation.
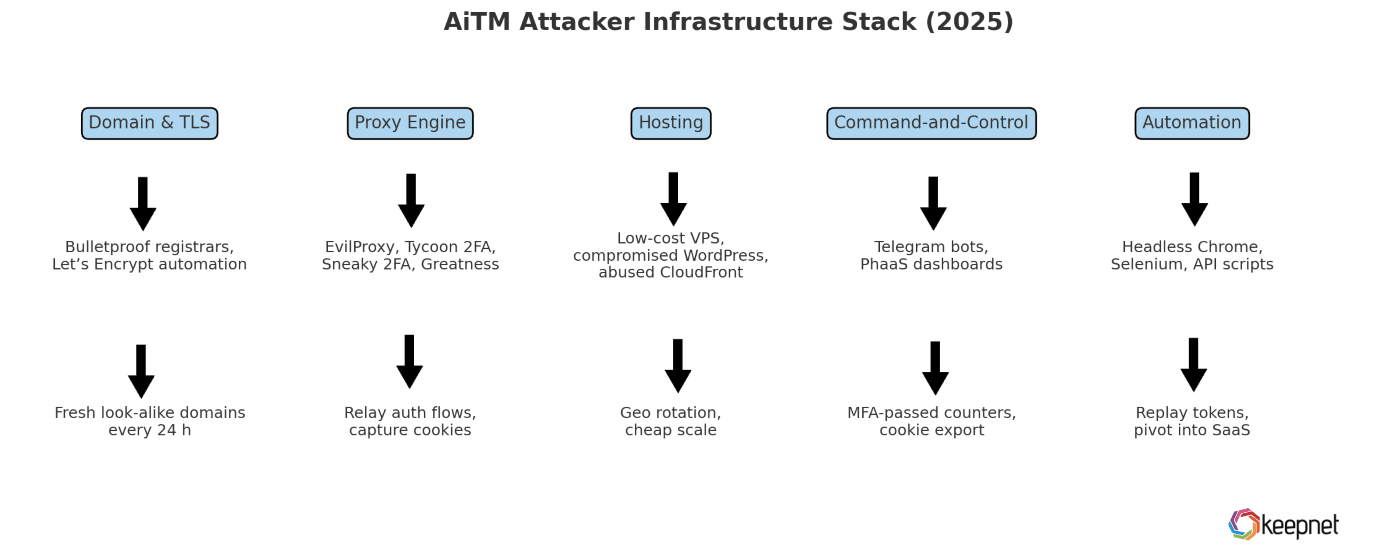
Attacker Infrastructure in 2025
In 2025, AiTM attackers are no longer lone hackers—they’re operating with the precision and scalability of cloud-native engineering teams. Their infrastructure is modular, automated, and built to bypass MFA at scale. Below is a breakdown of each core layer in the AiTM tech stack and the tools that make it possible.
To truly defend against Adversary-in-the-Middle phishing, we need to dissect how these attacks are engineered from the ground up. From domain spoofing to token replay automation, modern AiTM campaigns operate like professional SaaS products—complete with dashboards, live metrics, and modular toolchains. This section unveils the technical anatomy of a full-blown AiTM operation.
| Layer | Typical Tools & Services | Purpose |
|---|---|---|
| Domain & TLS | Bulletproof registrars, Let’s Encrypt automation | Fresh look-alike domains every 24 h |
| Proxy Engine | EvilProxy, Tycoon 2FA, Sneaky 2FA, Greatness | Reverse-proxy that relays auth flow and captures cookies |
| Hosting | Low-cost VPS, compromised WordPress sites, or CloudFront abused via free-tier | Geographic rotation + cheap scale |
| Command-and-Control | Telegram bots, SaaS dashboards (PhaaS) | Live “MFA-passed” counters, stolen cookie export |
| Automation | Headless Chrome + Selenium / Graph API scripts | Replays tokens, deploys mailbox rules, pivots to SaaS |
Table 2: Attacker Infrastructure in 2025
Barracuda saw >1 million PhaaS-powered AiTM attacks in just January–February 2025.
Inside a Modern AiTM Phishing Kit (Example: Tycoon 2FA)
Forget hand-coded HTML clones and phishing PDFs—today’s AiTM kits like Tycoon 2FA come packaged like SaaS platforms, complete with dashboards, automation, and live credential feeds. Here’s what you get when you subscribe:
- Prebuilt white-label portals: Spin up fake login flows for Microsoft 365, Google Workspace, Okta, or Zscaler with a checkbox. Pages are dynamically pulled from the real service to ensure pixel-perfect cloning.
- One-click domain and TLS provisioning: The kit auto-generates subdomains (e.g. login-authportal[.]com) and immediately attaches valid SSL certificates via Let’s Encrypt—no manual setup required.
- Live campaign dashboards: See real-time counters like “MFA passed” and “Credentials harvested” for each target, helping operators track ROI and tweak lures.
- Session cookie exfiltration API: Each time a victim completes MFA, the kit pushes the active session token to a Telegram bot or webhook—ready to be replayed within seconds.
- Persistent foothold tools: With a single toggle, the attacker can silently register rogue OAuth apps or enroll a new MFA method on the victim’s account for long-term access—even if the password changes.
Bottom line: Tycoon 2FA doesn’t just phish credentials—it commodifies full-session hijack with automation pipelines. If your SOC only watches for login failures or password reuse, this slips right past you.
End-to-End Flow
To understand how Adversary-in-the-Middle phishing unfolds in real time, it helps to zoom out and see the full attack chain—from the first click to complete session takeover. The diagram below visualizes each phase of the AiTM flow, showing how attackers intercept credentials, bypass MFA, and hijack sessions with surgical precision—all without triggering traditional alarms.
- Link click: Victim lands on proxy.
- Credential relay: Proxy forwards username/password, records copy.
- MFA relay: Victim approves push/TOTP/QR; proxy captures assertion.
- Cookie theft: Auth token exfiltrated to attacker.
- Post-login abuse: Scripts use token to exfil data, set mailbox rules, launch BEC.
Key Technical Insights for Defenders
- Bind your tokens to the device: Session hijacking starts where MFA ends. Enforce device-bound tokens and enable Continuous Access Evaluation (CAE) to instantly revoke access when cookies are compromised.
- Fuse telemetry across layers: Connect the dots between email gateway URL rewrites and IdP sign-in logs. If a link click is followed by an MFA success from a new IP within seconds—sound the alarm. That’s an AiTM fingerprint.
- Fingerprint the proxy: Many AiTM phishing kits leave behind telltale signs in their TLS JA3 hashes or SNI values. Feed these into your firewall, secure web gateway, or XDR for proactive blocking.
If your detection logic stops at “MFA passed,” you’re already too late. AiTM lives in the post-MFA world—and unless you’re monitoring for token integrity, you’re handing attackers a valid key to your front door.
Indicators of Compromise (IoCs)
Adversary-in-the-Middle phishing doesn’t leave behind the usual broken login attempts or brute-force trails. Instead, it slips through in silence—relying on stolen session tokens and live credential relays. Spotting an AiTM breach means looking for signals that normal behavior happened at the wrong time, from the wrong place, or with the wrong fingerprint.
- Behavioral IoCs to Watch For: Successful logins from new IPs immediately after email clicks, (especially if IP geolocation differs significantly from the user’s known location).
- MFA success from unrecognized devices: This is followed by high-privilege actions (forwarding rules, app password creation).
- Duplicate sessions: One user appears to be logged in from two locations simultaneously—one real, one attacker-controlled.
- OAuth application grants: These weren’t user-initiated. Especially those with access to mail, calendar, or file APIs.
Technical Artifacts & Network-Level IoCs
JA3 hashes / TLS fingerprints: Certain AiTM kits reuse the same TLS stacks or SNI strings. Feed known bad fingerprints into your web proxy or firewall.
- Suspicious domain patterns: Common examples include subdomains like login-auth[.]xyz, secure-o365[.]cloud, or mfa-verify[.]site—often with recent registration dates and Let’s Encrypt TLS certs.
- Session cookie anomalies: Tokens used on different OS/browser/device combinations within short timeframes (session replay).
Pro tip for SOC teams: If your alert rules only fire on failed logins or brute force attempts, you’ll miss AiTM entirely. Update detection logic to correlate successful MFA events with recent URL click-throughs and new device fingerprints. That’s where AiTM lives.
Impact and Consequences of AiTM Phishing Attacks
Adversary-in-the-Middle (AiTM) phishing attacks don’t just result in stolen passwords—they bypass multi-factor authentication, compromise live sessions, and escalate to full-blown data breaches. The damage unfolds fast, and the ripple effects can last for months or even years. Understanding the true impact of AiTM phishing is critical for CISOs, security teams, and legal departments preparing their incident response and risk mitigation strategies.
Organizations often underestimate these attacks because they appear to start as simple login events, but the consequences go far beyond the inbox.
Short-Term vs. Long-Term Impacts
In the immediate aftermath of an AiTM breach, the focus tends to be on containment: isolating compromised accounts, revoking sessions, and notifying stakeholders. But the long-term damage can be far more difficult to quantify and recover from.
Short-term impacts:
- Immediate loss of email and document access
- Internal communication breakdown due to mailbox rule manipulation
- Delayed detection leading to multi-account lateral movement
Long-term consequences:
- Persistent access via OAuth apps or rogue MFA devices
- Regulatory fines due to delayed breach reporting
- Breakdown in customer trust and executive accountability
Financial, Reputational, and Legal Consequences
AiTM phishing attacks are among the costliest forms of social engineering, especially when they result in business email compromise (BEC) or intellectual property theft.
Financial risks include:
- Wire transfer fraud totaling millions of dollars
- Legal fees and forensic investigation costs
- Revenue disruption due to system lockouts
Reputational risks include:
- Loss of customer confidence and vendor trust
- Negative media coverage that affects brand perception
- Social media fallout from leaked internal emails
Legal risks include:
- Non-compliance with GDPR, CCPA, HIPAA, or sector-specific mandates
- Class-action lawsuits from impacted customers or partners
- Board-level liability in the absence of adequate controls
If your organization still treats phishing as a basic threat, it’s missing the real danger. AiTM phishing doesn’t just compromise accounts—it erodes trust, drains capital, and leaves legal teams scrambling. Understanding the impact is the first step toward prevention.
Advanced Detection Methods for AiTM Phishing
Traditional detection tools are built to catch brute force attempts, credential stuffing, and malware payloads—not attacks that happen after a successful login. Adversary-in-the-Middle phishing thrives in the gaps between identity platforms, browsers, and behavioral analytics. To detect these stealthy attacks, organizations need to adopt modern methods that blend machine learning, browser telemetry, and cross-platform identity context.
AI-Driven Threat Detection
Artificial intelligence has become a critical layer in catching AiTM activity, not because it sees what humans can’t—but because it sees faster and deeper. AI models can instantly process a wide variety of signals—MFA location data, login frequency, device posture, browser type—and determine when a session doesn’t behave like the user behind it.
Key capabilities of AI-based AiTM detection systems include:
- Real-time analysis of login patterns and token usage
- Detection of simultaneous or rapid-sequence logins from multiple geographies
- Behavioral deviation user risk scoring that flags risky sessions, even when MFA was passed
When paired with cloud-native identity providers, AI threat engines can isolate compromised sessions before attackers reach sensitive data.
Browser-Level Detection Mechanisms
The browser is where AiTM phishing begins—and often, where it can be stopped. By integrating security controls directly inside the browser environment, organizations can detect when login flows are being intercepted or proxied.
Modern approaches include:
- CSP (Content Security Policy) violation reports that flag unauthorized domain calls
- Browser fingerprinting to detect inconsistencies between what the user expects and what the proxy serves
- WebAuthn telemetry, revealing if authentication was completed on a registered device or manipulated through fallback methods
These tools give security teams visibility not just into what users do, but how and where they do it—critical context when validating the legitimacy of a session.
Behavioral Analytics and Anomaly Detection Tools
The final piece of the puzzle is understanding behavior over time. AiTM phishing often looks like normal user behavior in the moment. But zoomed out across hours or days, the anomalies emerge: a user logs in from Germany seconds after clicking an email in Canada; an OAuth grant is approved for a tool the user has never touched; a mailbox rule appears that forwards all email to a disposable address.
Behavioral analytics platforms build an identity graph that maps what each user’s digital life normally looks like—then flags events that break the pattern.
Capabilities worth implementing:
- Cross-app and cross-device behavior mapping
- OAuth anomaly detection
- Identity risk scoring based on context and deviation from norm
In the post-MFA world, the best detection strategy isn’t just about stopping logins—it’s about watching what happens next. With AI, browser-level visibility, and behavioral baselines, we can finally catch AiTM in the act.
Why AiTM Attacks Are Critical to the Success of Business Email Compromise (BEC)
Business Email Compromise has traditionally relied on social engineering tactics—impersonating executives, spoofing domains, and convincing finance teams to wire money. But in 2025, those tactics have evolved. Today’s most successful BEC campaigns are powered by Adversary-in-the-Middle (AiTM) phishing attacks that bypass MFA, hijack sessions, and give attackers legitimate, ongoing access to executive inboxes.
If you’re protecting against BEC without defending against AiTM, you’re only fighting half the battle.
How AiTM Fuels Modern BEC Scenarios
AiTM phishing provides the perfect launchpad for BEC:
- Bypasses MFA completely: Once the attacker has the session token, they don’t need to steal the password again. MFA is rendered useless.
- Grants full inbox visibility: Attackers read internal email threads in real-time, understand payment schedules, vendor relationships, and communication styles.
- Sets up stealthy persistence: Through malicious mailbox rules or OAuth apps, the attacker can observe and manipulate conversations over days or even weeks without being detected.
- Launches from trusted infrastructure: Because the attacker sends emails from the real corporate account, there are no spoofing indicators or failed DMARC logs to trigger alarms.
Why Security Teams Must Align AiTM and BEC Defenses
- BEC is not just a human error anymore. It’s now a hybrid attack, using technical compromise (AiTM) to enable psychological manipulation (BEC).
- Email security gateways won’t catch this. There’s no spoofing, no strange domains, no external sender to block. Therefore, protect your secure email gateways (SEGs).
- MFA is not enough. If your BEC defense strategy starts and ends with “we have MFA enabled,” you are vulnerable to AiTM.
How to Prevent Adversary-in-the-Middle Phishing
Stopping Adversary-in-the-Middle (AiTM) phishing requires more than firewalls and MFA. These attacks succeed by exploiting human trust and technical blind spots—especially in the gaps between email security, identity platforms, and browser behavior. Prevention must be multi-layered, combining user training, technical safeguards, and detection logic tailored to AiTM tactics.
Let’s break down what prevention looks like in 2025.
Employee Training and Awareness Programs
Your employees are the first—and sometimes last—line of defense. AiTM phishing preys on urgency and realism, often imitating legitimate sign-in portals with pixel-perfect accuracy.
To harden your human layer using security awareness training:
- Include AiTM-specific scenarios in phishing simulations (e.g., MFA interception and QR-based lures)
- Train users to recognize suspicious login pages, especially those with unusual domains, generic branding, or QR phishing prompts
- Reinforce the importance of reporting any login prompt that feels “off”—even if it includes an MFA step
The moment staff realize that “passing MFA” doesn’t always mean they’re safe, your defense posture improves.
Technical Safeguards for Stopping AiTM Attacks
Even the best-trained users will occasionally fall for a well-crafted lure. That’s why your infrastructure needs controls designed to prevent token theft and replay.
Top technical safeguards include:
- Enforce phishing-resistant MFA (WebAuthn, FIDO2) with device binding and no QR fallback
- Enable Continuous Access Evaluation (CAE) to revoke tokens in real time when conditions change
- Use secure DNS filtering to block known AiTM kit domains (e.g., EvilProxy, Tycoon 2FA, Greatness)
- Implement browser isolation or inspection tools to detect proxy manipulation at the endpoint
- Correlate email gateway click logs with IdP login telemetry to catch post-MFA anomalies
Best Practices Checklist for Organizations
To help teams stay aligned, use this quick-reference AiTM defense checklist:
✅ All employees enrolled in phishing training that includes AiTM scenarios
✅ WebAuthn/FIDO2 enabled for high-risk roles (finance, admin, IT)
✅ Browser fingerprinting and session token binding enforced
✅ OAuth grant monitoring and revocation tools deployed
✅ Mail flow rules and app passwords audited weekly
✅ All login traffic inspected for TLS JA3 / SNI anomalies
By combining human vigilance with system-level defenses, you can stop AiTM phishing before it compromises your business.
Role of AI in Combating AiTM Attacks
Adversary-in-the-Middle phishing attacks have rendered traditional rule-based defenses—and even some “phishing-resistant” MFA setups—ineffective. As these threats evolve, so must our detection capabilities. Artificial Intelligence and Machine Learning have become essential not only for spotting AiTM activity in real time but for learning from every anomaly to prevent future compromise. This shift from reactive to proactive cybersecurity is critical for organizations that want to stay ahead of industrialized phishing-as-a-service operations.
In fact, we’ve already seen this play out in SMS phishing campaigns, where AI has helped identify the most spoofed brands by analyzing behavioral patterns at scale.
Leveraging AI and ML for Proactive Defense
AI does more than match IOCs to blacklists—it builds a behavioral fingerprint for every user, device, and session. It understands what a “normal” login looks like, and when something feels off—even if MFA was passed.
In the context of AiTM phishing, AI can:
- Detect when logins originate from known reverse proxy kits or suspicious IP infrastructure
- Flag authenticated sessions that immediately set mailbox rules or perform OAuth grants—hallmarks of BEC and persistent access setups
- Correlate email click events with authentication anomalies, especially if a user clicks a link and then passes MFA from a never-before-seen browser or geography
These insights are particularly important when protecting users from deepfake-enabled pretexting, as described in our recent analysis of the future of cybersecurity risk in hyper-personalized awareness training.
Future Predictions: What AI Will Do Next
As attackers refine their tactics, here’s what defenders can expect from AI between now and 2026:
- Predictive phishing intelligence – Analyzing emerging domain registrations and phishing kit signals across the dark web to preemptively blacklist infrastructure before it’s active
- Automated phishing simulations – Using AI to simulate adversary behavior internally and generate risk scores dynamically across departments—similar to the “adaptive learning paths” discussed in our Security Learning Curve framework
- Session integrity scoring – AI assigning real-time trust scores to active sessions, allowing systems to block access or require reauthentication based on contextual signals like user behavior drift or token origin mismatch.
If your SOC is still relying solely on static detections and playbooks, you’re operating with a blind spot. Today’s AiTM attacks move at machine speed—and only AI can keep up. Integrate AI into every layer of your identity infrastructure now, or risk watching your MFA and awareness investments get quietly bypassed.
Further Reading: Explore More Threats and Insights
See the resources below for additional context, case studies, and emerging trends that complement your understanding of Breach and Attack Simulation and broader cybersecurity strategies:
- Telephone-Oriented Attack Delivery (TOAD): Learn how TOAD scams exploit voice and urgency to bypass email filters.
- Top 10 Cybersecurity Movies & TV Shows: Get inspired by hacker culture in film and media.
- The Cyber Risk Playbook for Security Leaders: Strategic guidance for CISOs managing evolving threats.
- Phishing vs. Spam Emails: Understand the real difference and how BAS can highlight phishing blind spots.
- The Future of Cyberfraud Fusion: A strategic view on how attackers blend phishing, vishing, and smishing.
- False Clicks in Phishing Simulations: Explore how employee behavior can skew your BAS results and how to fix it.
- Cybersecurity in the Remote Work Era: Importance of cybersecurity for distributed environments.
- The Most Spoofed Brands in SMS Phishing (2025): Understand which brands threat actors impersonate most.
- Language Personalization in Awareness Training: How to improve security culture using native-language BAS content.
- Ransomware Gangs and BlackCat Alpha: Insights into BlackCat Alpha and how to simulate similar extortion tactics safely.
- Security Awareness and Cyber Insurance: How security awareness can reduce premiums and risk exposure for cyber insurance.
- What Is an Information Security Program?: A foundational read before implementing large-scale testing.
- Top Cybersecurity Tips for Employees 2025: A companion guide to strengthen human defenses.
- Top Security Projects for 2025 (Gartner Insights): Where BAS ranks among strategic cybersecurity priorities.
- Brand Abuse in Quishing Attacks: How attackers exploit QR codes and logos.
- Preventing DoS Attacks: How to test resilience against denial-of-service tactics.
Editor's note: This article was updated on 18 November 2025.