What is Information Security Program?
Building a robust information security program with your organization is essential to protect sensitive data effectively. Discover the security lifecycle, critical elements, and practical examples of successful strategies to guard against evolving cyber threats.
Information security is no longer optional, it's a necessity. Whether you’re a CISO or an IT manager, developing a comprehensive information security program should be at the top of your priority list. This program is a framework that helps protect your company’s data, ensuring it’s safe from cyber threats, data breaches, and malicious attacks. Let’s break down exactly what an information security program is, how it operates, and the critical steps involved in implementing one.
What is the definition of an information security program?
An information security program (ISP) is a detailed plan that defines how a company protects its sensitive data from unauthorized access, breaches, and leaks. This program establishes policies, procedures, and controls designed to safeguard information—whether it’s customer data, intellectual property, or proprietary business information. A good ISP isn’t just about technology; it also includes security awareness training for employees, which is crucial to reducing human error.
For example, in 2025, many companies enhanced their programs to address rising threats like phishing attacks and ransomware. In fact, employee cybersecurity awareness training is often seen as the backbone of these programs. It’s more than a defensive measure; it’s a proactive way to keep threats at bay.
How does the information security lifecycle work?
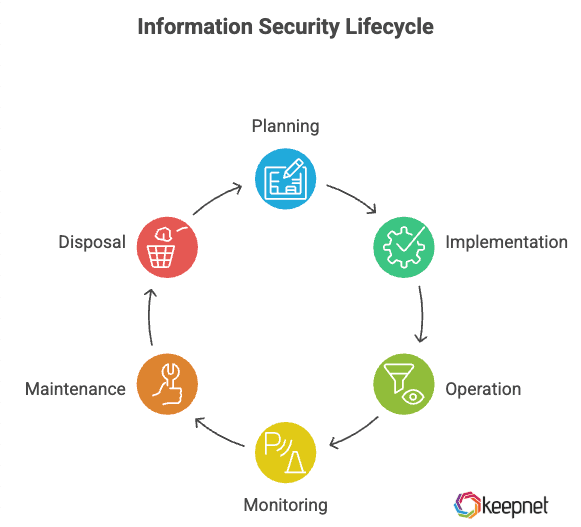
The information security lifecycle is the process by which an organization plans, implements, operates, and maintains its security program. The lifecycle is typically broken into several phases:
Planning
This is the foundation of the lifecycle. It’s where security policies, objectives, and procedures are defined. You’ll need to assess risk management, identify potential threats, and set up controls to manage these risks effectively. It’s also essential to ensure your planning includes a robust password protection strategy and multi-factor authentication.
Implementation
Once you’ve got the plan, it’s time to execute it. This stage involves deploying security solutions like firewalls, antivirus software, data encryption, and physical security measures. It also includes conducting security awareness training for employees to help them recognize potential threats like vishing or smishing.
Operation
In this phase, you’re actively enforcing the security policies. It's when you manage user access, monitor for anomalies, and ensure data protection controls are functioning. A well-executed operation phase will include regular phishing simulations and email threat monitoring to spot vulnerabilities early.
Monitoring
You can’t just set and forget your security program. Ongoing monitoring is crucial to detect and respond to security incidents in real time. Whether it's monitoring mobile devices or analyzing quishing attempts, consistent vigilance is key to ensuring your systems remain secure.
Maintenance
This is where you regularly update and improve your security systems. Cyber threats evolve, and so should your defenses. Ensure you patch vulnerabilities, update software, and tweak policies based on your monitoring data.
Disposal
When it’s time to retire old hardware, software, or even data, proper disposal is essential. Securely wiping or destroying data that’s no longer needed ensures that sensitive information doesn’t fall into the wrong hands. Think of this as a clean exit strategy, safeguarding your business from potential leaks.
Difference Between Information Security Lifecycle and Cybersecurity
While information security and cybersecurity are often used interchangeably, they’re not quite the same thing. Information security is broader, encompassing the protection of data in all its forms—digital and physical. Cybersecurity, on the other hand, focuses exclusively on protecting electronic data from cyber threats like hacking or malware.
In simple terms, cybersecurity is a part of the bigger information security picture. For example, a good information security program would include cybersecurity measures but also physical access controls like locked server rooms.
Key elements of an effective information security program
So, what makes an information security program effective? Here are the critical components:
- Governance and Policy: Clear, defined policies that outline security goals and procedures.
- Risk Management: Identifying risks and setting controls to manage them.
- Security Controls: Implementation of both technical and administrative controls, like encryption and user awareness training.
- Incident Response: A robust incident response plan is essential for quickly addressing and mitigating security breaches.
- User Education: Regular security awareness training is crucial in minimizing risks posed by phishing and ransomware attacks.
These elements ensure that your organization has a solid defense against both internal and external threats.
What is a written information security program?
A written information security program (WISP) is a formal document that outlines all the security measures, policies, and procedures your company follows to protect its data. It’s basically your information security strategy written down, showing exactly how you plan to secure sensitive information from threats like data breaches or human error. Having everything in writing helps ensure accountability across your team, making it easier to comply with regulations like GDPR or HIPAA. Without a WISP, it’s much harder to stay on top of security gaps and legal requirements.
What is an example of information security?
An example of information security in action could be implementing a company-wide encryption policy. This means every employee’s device—laptops, phones, etc.—must have data encryption, ensuring information stays protected even if a device is lost or stolen. Another solid example is conducting phishing simulations regularly. By testing your employees on how well they can detect phishing emails, you not only raise awareness but also reduce the risk of falling victim to actual attacks.
What are the key concepts of information security?
The key concepts of information security are based on the CIA triad—Confidentiality, Integrity, and Availability:
- Confidentiality: Ensures that sensitive data is accessible only to those with the right permissions. Methods like access controls and encryption help keep your information secure.
- Integrity: Keeps data accurate and reliable. No one should be able to alter or tamper with your data, whether intentionally or by mistake.
- Availability: Ensures authorized users can access the data when they need it, using backups and system redundancy to avoid downtime or data loss.
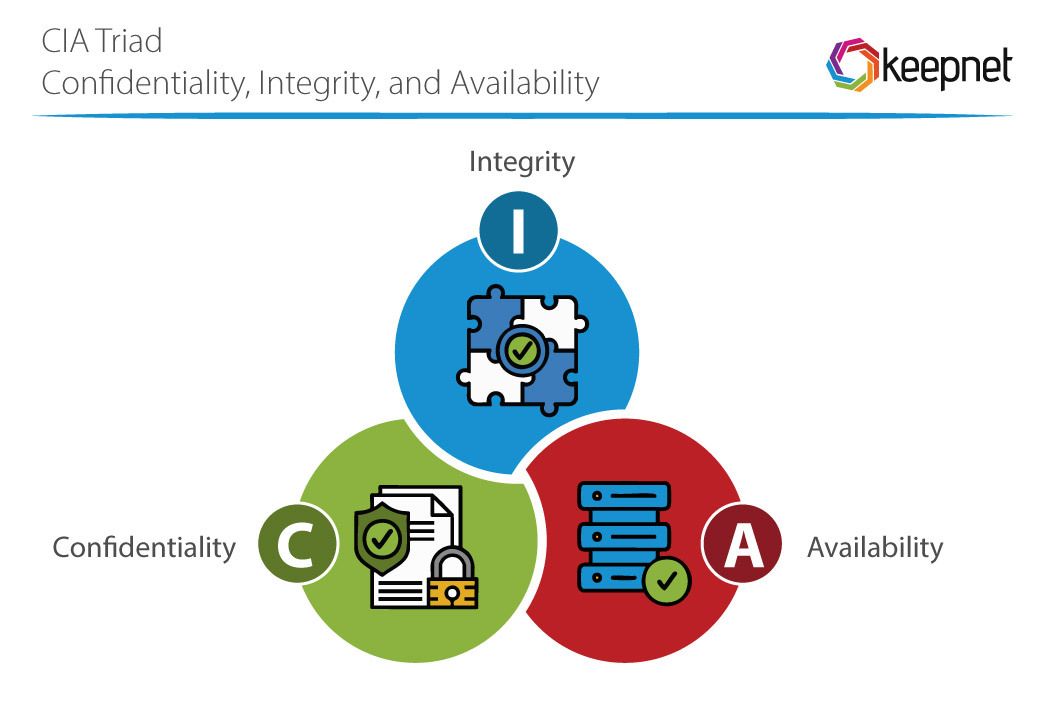
These principles form the core of a solid information security strategy.
What is the main goal of information security?
The main goal of information security is simple: to protect your organization’s valuable data from threats. Whether it’s customer information, internal business documents, or intellectual property, you need to guard it against cyberattacks, unauthorized access, and data leaks. Keeping your data secure ensures compliance with legal standards, prevents costly breaches, and maintains your business’s reputation.
What are the main types of information security?
When it comes to information security, there are three main types that every organization needs to focus on. Think of them as different layers of defense that work together to protect your data.
1. Physical Security
Physical security is all about protecting the physical access to your systems and data. It’s not just about digital threats—someone could literally walk into your building and steal sensitive equipment or plug in a malicious USB. For example, having secure server rooms that only authorized staff can access, or using surveillance cameras and keycard entry systems, is a key part of physical security. You also want to make sure laptops and mobile devices are locked up or wiped remotely if they’re lost or stolen.
2. Technical Security
This is what most people think of when they hear "cybersecurity"—using technology to protect your systems and data. Firewalls, antivirus software, and encryption all fall under this category. Basically, you’re putting up digital barriers to keep hackers out and protect your information. Data encryption, for example, makes data unreadable to anyone who doesn’t have the key to decrypt it, which is critical when sensitive information is being transmitted online. Things like multi-factor authentication (MFA) and regular software updates also fall under technical security, as they help close vulnerabilities before cybercriminals can exploit them.
3. Administrative Security
This might sound boring, but administrative security is crucial—it’s the policies and procedures that manage your overall security risks. This includes security awareness training for employees so they know how to spot a phishing email or report suspicious activity. It also involves access control policies, deciding who gets to access certain data and systems. Without strong administrative controls, even the best technical solutions can fail. You want a culture where people understand their role in keeping the company safe, from creating strong passwords to following the proper procedures when accessing sensitive information.
In short, physical security keeps intruders out of your building, technical security keeps hackers out of your network, and administrative security keeps your team educated and your policies strong. All three are essential to a well-rounded information security strategy.
What is Information Security Program Quizlet?
On Quizlet, an online learning platform, an Information Security Program Quizlet refers to study sets created by users to help learners understand key concepts related to information security programs. These study sets typically cover topics like:
- The CIA triad (Confidentiality, Integrity, Availability)
- Risk management and how to identify vulnerabilities
- Different types of security controls (e.g., administrative, technical, and physical)
- Compliance standards such as GDPR and HIPAA
It’s a helpful resource for students and professionals preparing for certifications like CISSP or Security+, or for anyone looking to better understand the framework and structure of a security program.
What is information security program development?
Information security program development refers to the process of designing, building, and implementing a comprehensive security framework for an organization. This involves several key steps:
- Assessment: Identifying the security needs of the organization, including sensitive data, potential vulnerabilities, and the current threat landscape.
- Planning: Developing security policies and procedures that address those needs. This includes setting goals, defining roles and responsibilities, and ensuring compliance with industry regulations.
- Implementation: Deploying security technologies like firewalls, encryption, and access controls, along with user training programs.
- Monitoring and Maintenance: Continuously monitoring security controls to detect new threats and regularly updating the program to ensure it remains effective over time.
Developing an effective information security program is not a one-time project. It’s an ongoing process that evolves as new technologies emerge and cyber threats change.
Information security program template
| Element | Description |
|---|---|
| Governance and Policy | Establishes the overall security framework, including the objectives, rules, and responsibilities. Ensures alignment with business goals and legal regulations. |
| Risk Management | Ongoing process to identify, assess, and prioritize security risks. Includes regular risk assessments, vulnerability scanning, and setting risk tolerance levels. |
| User Education and Awareness | Continuous training programs for employees to recognize, avoid, and respond to security threats like phishing, social engineering, and other human-risk factors. |
| Technical Controls | Deployment of technology solutions like firewalls, intrusion detection systems (IDS), encryption, and multi-factor authentication (MFA) to protect data and systems. |
| Physical Security | Securing physical assets such as servers, computers, and networks through access controls, surveillance, and secure facilities. Prevents unauthorized physical access. |
| Data Classification | Establishing categories of data sensitivity (e.g., confidential, internal, public) and applying different levels of security controls based on the data's classification. |
| Access Control | Role-based access control (RBAC) policies, ensuring that only authorized users have access to specific data or systems. Includes managing user roles, permissions, and authentication. |
| Incident Response Plan | Clearly defined steps for identifying, responding to, and recovering from security incidents. Includes incident detection, containment, forensic analysis, and communication strategies. |
| Compliance Management | Ensures adherence to legal and regulatory requirements such as GDPR, HIPAA, ISO 27001, and other relevant standards. This also involves regular audits and assessments. |
| Third-Party Risk Management | Evaluates and manages the security risks posed by vendors, contractors, and third-party service providers. Includes security due diligence and regular vendor assessments. |
| Business Continuity and Disaster Recovery (BCDR) | Plans for maintaining or restoring business operations after a disruptive event. Includes data backups, system recovery, and communication protocols during outages or attacks. |
| Monitoring and Auditing | Regularly tracks and logs system activity, network behavior, and user actions to detect suspicious activity and assess policy adherence. Audit logs ensure accountability. |
| Policy Enforcement | Methods for ensuring that security policies are enforced, including disciplinary actions for violations, regular reviews, and updates to policies. |
| Patch Management | Ongoing management of software updates and patches to close vulnerabilities in operating systems, applications, and hardware. Essential for minimizing exploit risks. |
| Data Encryption and Protection | Use of encryption protocols for data at rest and in transit to safeguard sensitive information. Includes endpoint security and data loss prevention (DLP) tools. |
| Vulnerability Management | Regular scanning, identifying, and addressing system and software vulnerabilities. Involves penetration testing and patching vulnerabilities before they can be exploited. |
| Security Testing and Simulations | Regular testing of security protocols through simulations like phishing tests, penetration testing, and red teaming to gauge the effectiveness of current security measures. |
| Continuous Improvement | Regularly reviewing and updating the security program to stay ahead of evolving threats. Incorporates feedback from audits, incident reports, and changes in the threat landscape. |
Table: Information security program template
This information security template ensures that all aspects of a well-rounded information security program are covered—from the governance and technical controls to user training and compliance. It also includes essential elements like third-party risk management, disaster recovery, and vulnerability management, which are crucial for a modern organization’s security posture.
Get Help from Keepnet About Security Awareness
When it comes to security awareness, the human element is often the weakest link in an organization's defense. No matter how strong your technical controls are, if your employees aren’t equipped to recognize and avoid threats like phishing, ransomware, or social engineering, your business is at serious risk. This is where Keepnet Labs steps in to help.
At Keepnet Human Risk Management platform, we understand that the foundation of any strong information security program lies in empowering your team to make smart, security-conscious decisions. Our comprehensive security awareness solutions focus on educating your employees in an engaging, practical way that builds lasting habits, not just temporary knowledge.
Here’s how Keepnet can help you level up your security awareness efforts:
1. Phishing Simulation Platform
One of the most effective ways to reduce your exposure to phishing attacks is to train your staff using phishing simulations. Keepnet Phishing Simulator mimics real-life phishing attempts, allowing you to test how well your employees can spot these malicious emails. By running regular simulations, you can identify employees who may need additional training and track overall progress. Not only does this help reduce the risk of successful phishing attacks, but it also builds a culture of constant vigilance among your workforce.
2. Comprehensive Security Awareness Training
Beyond phishing, Security Awareness Training offers a wide range of topics to cover every aspect of human risk. From password protection and safe browsing habits to identifying smishing and vishing attempts, our training modules are designed to ensure employees are prepared to handle the latest cyber threats. The training is tailored to suit different roles within your organization, so whether you’re training your customer support team or your IT department, we’ve got content that fits their needs.
3. User-Friendly Dashboards and Reporting
Tracking and understanding your employees' progress is key to making sure your security awareness program is effective. Keepnet’s platform comes with intuitive dashboards that give you an overview of who has completed their training, how they performed in phishing simulations, and where the most vulnerable areas of your organization are. The reporting tools make it easy to share insights with management and demonstrate improvements in employee security behavior over time.
4. Customizable Training Content
Every business has unique security needs, and that’s why Keepnet offers customizable training content. You can tailor the training modules to reflect your company’s specific policies, industry threats, and compliance requirements. For instance, if your business needs to focus more on GDPR or HIPAA compliance, we’ve got you covered with industry-specific modules. This level of customization ensures that your team gets training that’s relevant and practical for their everyday tasks.
5. Interactive and Engaging Training
We know that traditional training methods can often feel dry and ineffective. That’s why Keepnet focuses on making security awareness interactive and engaging. Our platform includes quizzes, games, and real-world scenarios to keep employees interested and help them retain the information. When training is fun, it sticks—and when it sticks, your business is safer.
6. Vishing and Smishing Simulations
Email phishing isn’t the only attack vector targeting your organization. Keepnet also offers vishing simulation and SMS phishing simulation, so your employees can practice recognizing and responding to these more subtle, yet dangerous, forms of attacks. These simulations are an essential part of any modern security awareness program, as cybercriminals increasingly target users via phone and text.
7. Automated Training Workflows
Managing a security awareness program can be time-consuming, but Keepnet’s platform makes it easier with automated training workflows. You can schedule regular training sessions, phishing simulations, and follow-up reminders without lifting a finger. The platform ensures that employees stay on track with their training, reducing the administrative burden on your IT and security teams.
Editor's note: This article was updated on October 6, 2025.