5 Social Media Scams You Need To Watch Out
Discover how to protect your team from evolving social media scams. Learn to detect phishing, fake profiles, and job offer scams—plus practical steps using Keepnet tools to reduce human risk and stop threats before they cause harm.
In 2024, scams cost the UK economy 0.4% of its GDP, with the average victim losing £1,443 (US$1,818), according to the State of Scams in the United Kingdom report by the Global Anti-Scam Alliance (GASA) and Cifas. A growing share of these incidents stemmed from fraud and scams on social media, where attackers exploit trust and familiarity to deceive users.
As platforms like Facebook, Instagram, and LinkedIn continue to shape our daily communication and professional networking, they’ve also become ideal hunting grounds for cybercriminals. From phishing links to fake job offers, social media scams are evolving fast—and so must our ability to detect them.
In this blog, we’ll explore the most common social media scams, uncover the key warning signs of social media scams, and share actionable steps to help you and your team stay secure online.
5 Examples of Social Media Scams
Understanding examples of common social media scams can help you recognize the warning signs before it’s too late. Below are five typical social media scams you need to watch out for.
Phishing Links And Fake Profiles
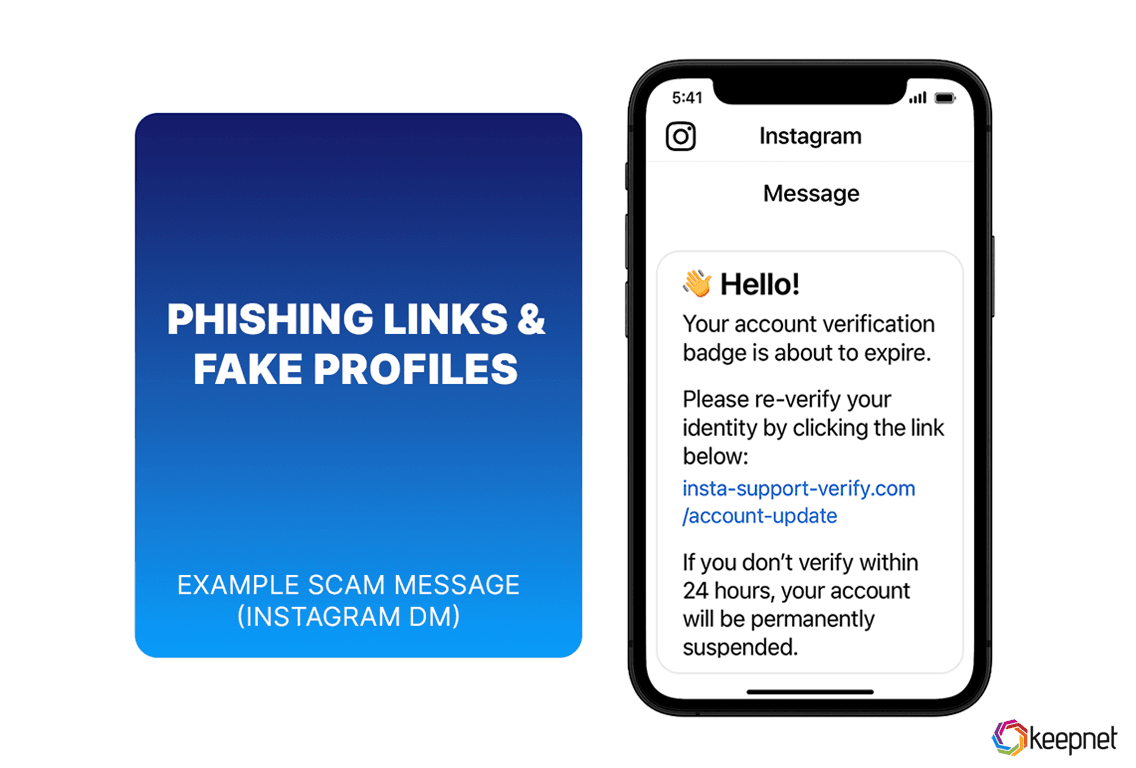
Phishing and fake profiles are among the most common social media scams targeting individuals and businesses alike. Attackers create realistic-looking profiles—often impersonating a colleague, brand, or influencer—to gain trust, but using a social media checker can help verify whether these profiles are authentic. Once connected, they send phishing links designed to steal login credentials, personal data, or financial information.
These scams often appear in private messages, comments, or sponsored posts. A single click on a malicious link can compromise your account or infect your device.
How To Identify A Phishing Link On Social Media
Phishing links on social media often look legitimate but are designed to trick you into giving away sensitive information. Here’s how to spot them quickly:
- Examine the link before clicking: Hover over the link to see the actual URL. Look out for misspellings, strange characters, or unfamiliar domains.
- Check the context of the message: Was it unexpected or overly urgent? Phishing attempts often pressure you to act fast—like claiming your account is at risk or you've won a prize.
- Assess the sender’s profile: New or unverified accounts, low engagement, and inconsistent content are warning signs.
- Avoid links in suspicious messages: If something feels off—like poor grammar or unusual tone—don’t click.
Training your team to recognize these red flags with the Phishing Simulator significantly reduces the risk of successful attacks.
Giveaway And Contest Scams
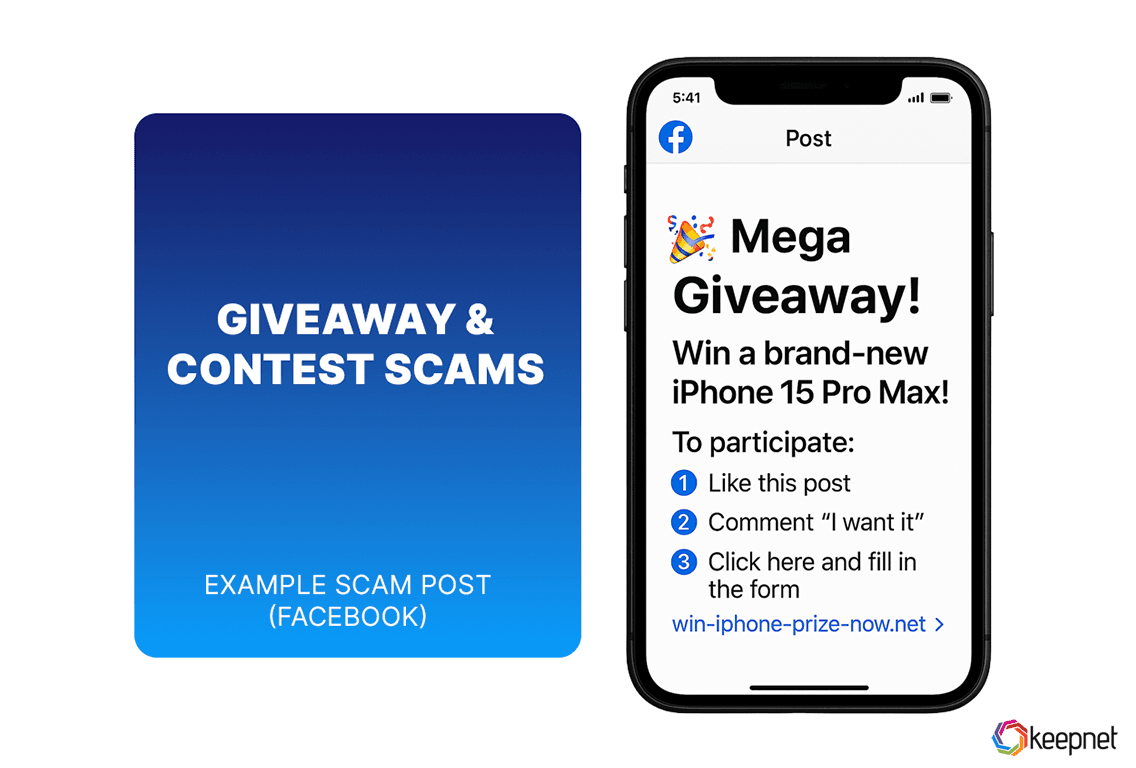
Scammers often lure users with fake giveaways or contests that promise prizes like phones, gift cards, or cash. These scams are designed to collect personal data or trick users into sharing the scam further. If it sounds too good to be true—it usually is.
Signs of a Fake Social Media Giveaway
Spotting a fake giveaway is easier when you know what to look for. Here are the most common red flags:
- Unverified or suspicious profiles: Scammers often use newly created or unverified accounts to run fake contests.
- Unrealistic rewards: Offers that seem too generous—like luxury items for simple actions—are usually scams.
- Requests for personal or financial information: No real giveaway will ask for your credit card number or ID to claim a prize.
- Lack of official rules or terms: Legitimate contests always include clear participation guidelines.
- Poor spelling and grammar: Typos and awkward phrasing can signal a scam.
- Urgency or pressure to share: If the post insists you act fast or tag others to win, be cautious.
For more real-world examples, read Keepnet’s detailed guide on the Most Common Social Media Phishing Scams.
What To Do If You Fall For A Contest Scam
If you’ve fallen for a fake giveaway, acting quickly can limit the damage. Follow these steps immediately:
- Change your passwords: Update login credentials for all affected accounts, especially if you reused the same password elsewhere.
- Enable two-factor authentication: Add an extra layer of security to protect your accounts from unauthorized access.
- Monitor financial accounts: Keep an eye on bank statements and report any suspicious transactions.
- Report the scam: Notify the social media platform and relevant authorities to help prevent others from falling victim.
- Run a device scan: Use antivirus software to check for malware if you clicked any suspicious links.
Malware And Spyware Scams
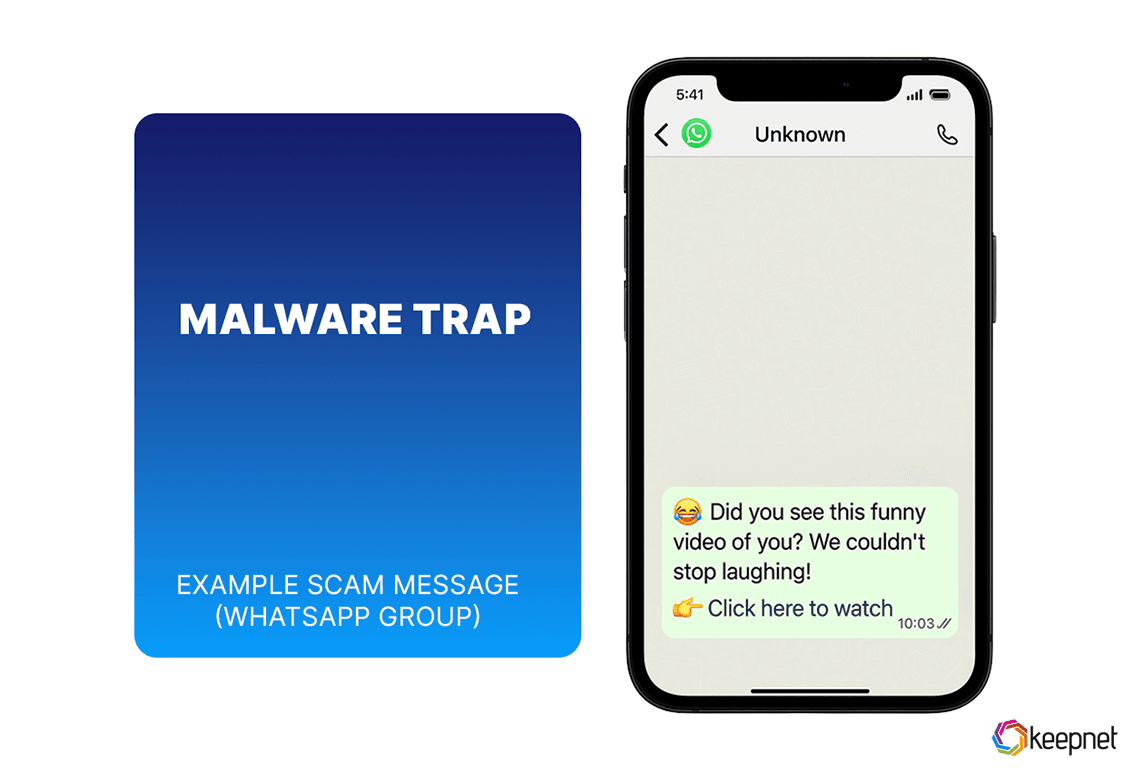
Some social media scams trick users into downloading malware or spyware disguised as harmless links, apps, or videos. Once installed, this malicious software can steal sensitive data, monitor activity, or take control of your device.
These scams often appear as:
- Fake video links claiming, “You’ve been tagged” or “Watch this now”
- Free downloads or giveaways requiring app installations
- Sponsored ads with clickbait content
To stay protected, avoid downloading anything from unknown sources and regularly update your security software. Using tools like Threat Intelligence helps detect and stop these threats before they spread. It allows you to check whether your company’s data has been compromised by data breaches and take immediate action to contain the risk.
Impersonation And Hacked Accounts
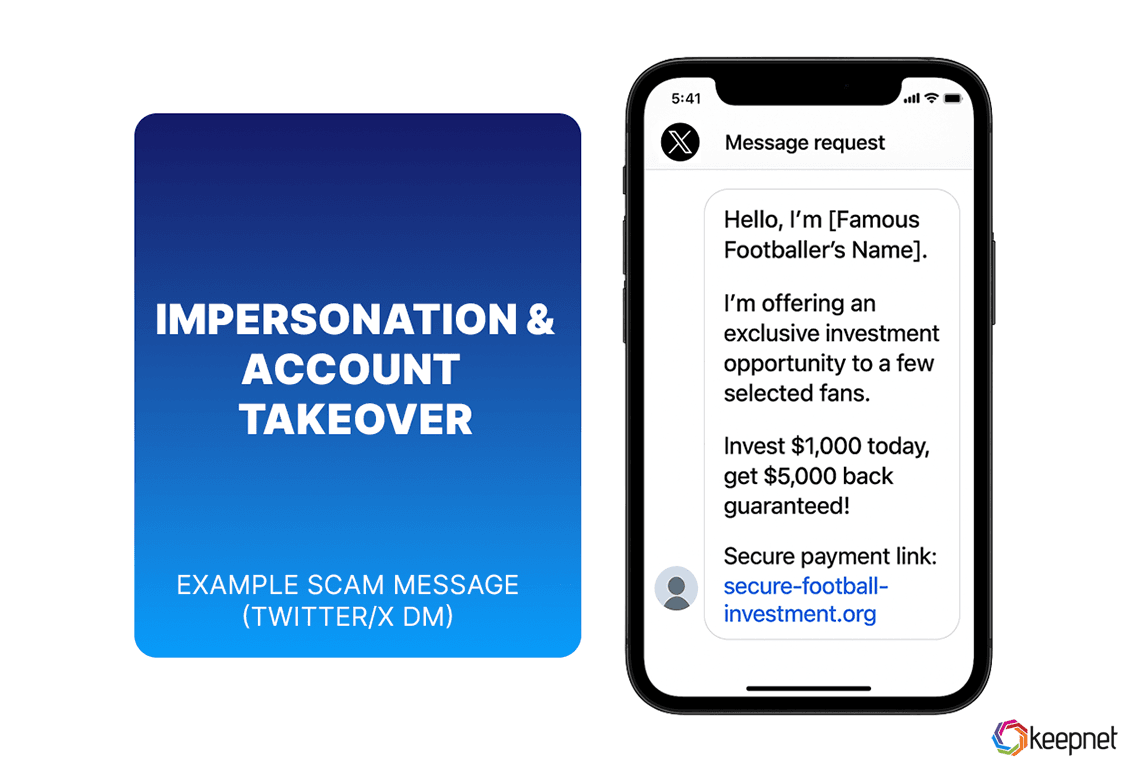
Impersonation scams involve attackers creating fake profiles that mimic real people or brands to trick users into trusting them. In other cases, scammers gain access to legitimate accounts and use them to send malicious messages. Both tactics can lead to data theft, financial loss, or reputational damage.
How To Spot An Impersonator Account
Spotting impersonator accounts early can prevent major security incidents. Here are key signs to watch for:
- No verification badge: Trusted brands and public figures typically have a verified checkmark.
- Unusual or generic content: Posts may seem out of character, poorly written, or copied from elsewhere.
- Low activity or engagement: Fake accounts often have few followers, likes, or comments.
- Minor name or handle changes: Look for subtle misspellings, extra characters, or swapped letters in usernames.
- Recent account creation: Scammers often use newly created profiles to avoid detection.
Steps To Take If Your Account Is Hacked
If your social media account is compromised, taking immediate steps can help contain the impact and secure your data. Follow these actions without delay:
- Change your password: Use a strong, unique password you haven’t used before.
- Enable two-factor authentication (2FA): Add an extra layer of security to prevent future unauthorized access.
- Log out of all sessions: Force a logout on all devices to cut off the hacker’s access.
- Notify your contacts: Let your followers or friends know your account was compromised to prevent further spread.
- Report the breach to the platform: Use the platform’s help tools to report the hack and begin account recovery.
- Scan your device for malware: Check for any spyware or keyloggers that may have been installed.
Job Offer And Investment Scams
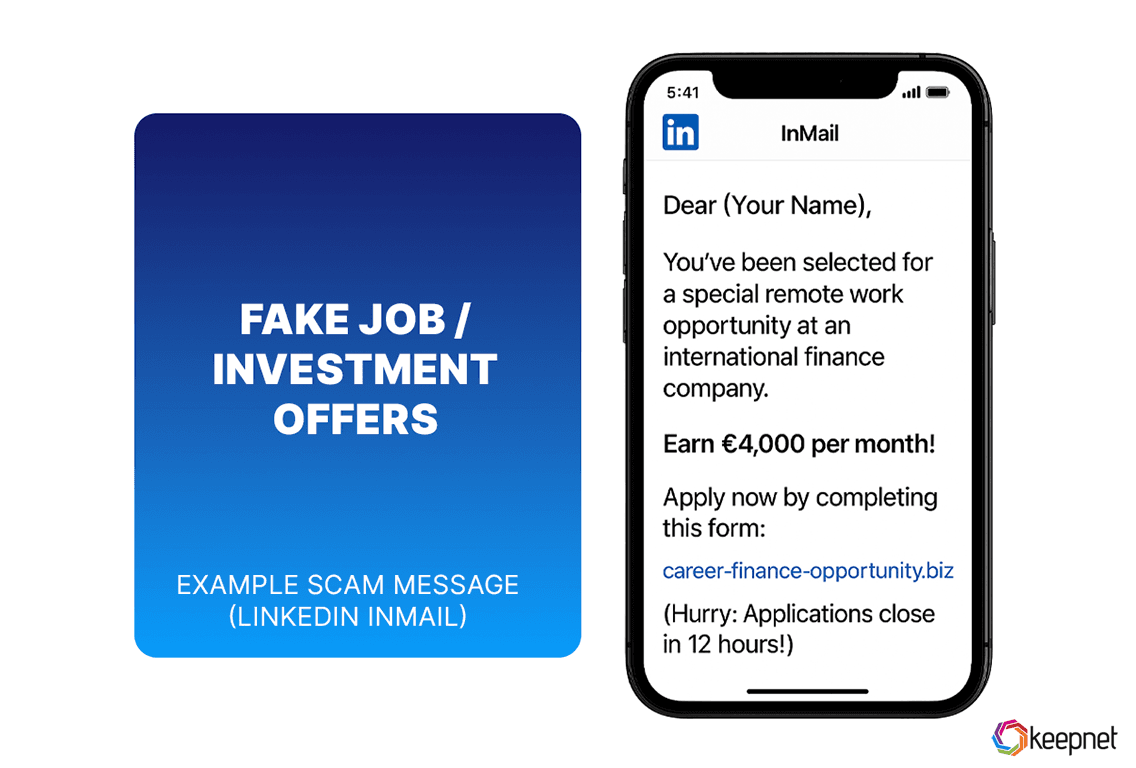
Scammers often use fake job offers or investment opportunities to target users on platforms like LinkedIn, Facebook, and Instagram. These messages may promise high salaries, remote roles, or fast returns—but typically ask for personal information, upfront payments, or software downloads.
In many cases, victims are tricked into installing malware or sharing sensitive data that can lead to financial loss or corporate breaches. Always research the sender, verify job offers through official company channels, and never transfer money or download files from unknown sources.
Types of Scams on Social Media
Social media platforms are home to a wide variety of scams that target users in both personal and professional contexts. From fake financial offers to manipulative social engineering tactics, scammers continuously adapt their methods to appear convincing.
Let’s explore how these different scam types work and what you can do to recognize and avoid them.
Financial Scams on Social Media
Financial scams are among the most widespread social media scams, often appearing as fake investment opportunities, loan offers, or crowdfunding campaigns. Scammers use professional-looking ads or posts to gain trust and convince users to send money or share banking details. Always verify the legitimacy of financial offers and never make payments based on social media messages alone.
Social Media Bank Scams
Bank scams on social media typically involve attackers posing as customer service agents from well-known banks. They may reach out via direct message, claiming there's a problem with your account and urging you to click a link or share personal banking details. These scams often mimic official branding, but lack verification badges and use generic or suspicious language.
Always contact your bank through official channels and never share sensitive financial information over social media.
Social Media Engineering Scams
Social engineering scams use psychological manipulation to trick users into revealing confidential information or performing risky actions. On social media, attackers may pose as coworkers, friends, or authority figures to build trust before making requests—such as clicking a link, transferring money, or sharing credentials.
These scams often rely on urgency, flattery, or fear to lower your guard. Training your team with adaptive Phishing Simulator to recognize these tactics is key to preventing human error, which remains a top cause of security breaches.
Social Media Impersonation Scams
Impersonation scams involve attackers creating fake accounts that closely resemble real people or organizations. They may clone a colleague’s profile, a company page, or even a public figure to gain trust and trick victims into sharing information or sending money.
These scams often use stolen photos, copied bios, and familiar-sounding messages. Always verify the identity of anyone making unusual requests—even if the profile looks familiar.
To understand how deepfake technology is fueling these threats, read Keepnet’s article on DeepNude AI: Ethical Risks and Cybersecurity Threats in 2025.
How To Stay Safe On Social Media
Staying safe on social media requires more than just strong passwords—it demands awareness, vigilance, and proactive security habits. With threats constantly evolving, users must learn how to recognize scams and protect their digital footprint. In this section, we’ll cover key privacy settings and smart practices to reduce your exposure to social media scams.
Setting Up Strong Privacy Settings
Strong privacy settings limit what attackers can see and exploit. These quick changes reduce your exposure to targeted social media scams:
- Limit profile visibility: Less public info makes it harder for scammers to impersonate or target you.
- Control tagging permissions: Prevent scammers from linking you to fake or malicious posts.
- Review third-party app access: Remove unused or untrusted apps that may leak data.
- Hide contact details: Keep emails and phone numbers private to block phishing and vishing attempts.
- Restrict story viewers: Limit who sees temporary content to avoid accidental oversharing.
Tips For Avoiding Social Media Scams In The Future
As social media scams grow more sophisticated, protecting your organization requires a layered, proactive approach. Here’s how to stay ahead:
- Verify before you trust: Always confirm job offers, investment tips, or urgent requests via official sources—not direct messages.
- Be cautious with links—even from known contacts: Use the Phishing Simulator to assess how well employees detect malicious links in realistic scenarios.
- Train for new attack methods: Prepare your team for mobile and QR-based scams using Smishing Simulator and Quishing Simulator.
- Track exposure from data breaches: Threat Intelligence shows if employee credentials have been leaked, what data was compromised, and how many users were affected.
- Speed up threat response: Incident Responder helps identify and act on email-based attacks 48.6 times faster, minimizing risk from social-driven phishing.
- Maintain continuous awareness: Reinforce learning with ongoing, scenario-based Security Awareness Training focused on current scam trends.
Combining these strategies strengthens your defense against both current and evolving threats on social platforms.
To further assess your organization’s readiness, check out Keepnet’s guide on Security Culture Maturity Model.
Editor's note: This article was updated on May 30, 2025.