Government Security Awareness Training 101: A 2026 Playbook
Launch effective government security awareness training in 2025. Use AI-powered phishing simulations and role-based training modules to prevent misdelivery, vishing, and ransomware, while meeting FISMA, NIST, and CMMC compliance requirements.
Government Security Awareness Training prepares public sector employees to identify and respond to threats such as phishing, ransomware, and social engineering, while also reducing mistakes that can lead to data breaches.
In 2026, security awareness training will be essential. Although reported incidents decreased due to changes in reporting, the number of confirmed government breaches remained steady. Ransomware was responsible for 30% of these, and human errors—especially misdelivery—remain common, according to the 2025 Verizon DBIR. Attackers continue to target government systems aggressively.
This playbook explains how to design a strong, compliant training strategy aligned with FISMA, NIST, and CMMC, and empower every employee to be part of your defense strategy.
What is Government Security Awareness Training?
Government Security Awareness Training is a foundational program that equips public sector employees with the skills to recognize, avoid, and report the most common cyber threats—such as phishing emails, ransomware infections, and social engineering tactics.
Unlike generic corporate training, this program is tailored to the operational realities of government environments. It aligns with regulatory standards like FISMA, NIST, and CMMC, and includes role-specific learning, phishing simulations, and ongoing performance assessments.
The objective is to make cybersecurity second nature for every government employee—whether they’re managing public records, handling citizen data, or approving contracts—so they can spot phishing attempts faster, avoid misdelivery errors, and respond swiftly to suspicious activity.
For a deeper dive into how government agencies can prepare for evolving compliance needs, check out this free training kit for NIS2 compliance.
Why Government Organizations Are Prime Cyber Targets
Government agencies store vast amounts of sensitive data—citizen records, infrastructure blueprints, tax and healthcare information—making them attractive to cybercriminals and nation-state attackers. Unlike private companies, many public sector systems still rely on outdated software, creating vulnerabilities that are easily exploitable.
These organizations also operate with large, distributed teams and complex supply chains, increasing the risk of human error and unauthorized access. Attackers know that even a single successful phishing email or misdirected file can compromise an entire network.
Limited cybersecurity budgets, slow procurement processes, and the pressure to keep public services running make it harder for agencies to defend themselves, making them consistent high-value targets.
For deeper insight into behavioral vulnerabilities, explore the Keepnet article on 6 Human Risk Indicators That Could Compromise Your Cybersecurity to learn which user behaviors most often lead to breaches.
Top Cybersecurity Threats Facing Government Employees
Government employees face a growing range of cyber threats, many of which exploit human behavior and outdated systems. The most common risks include:
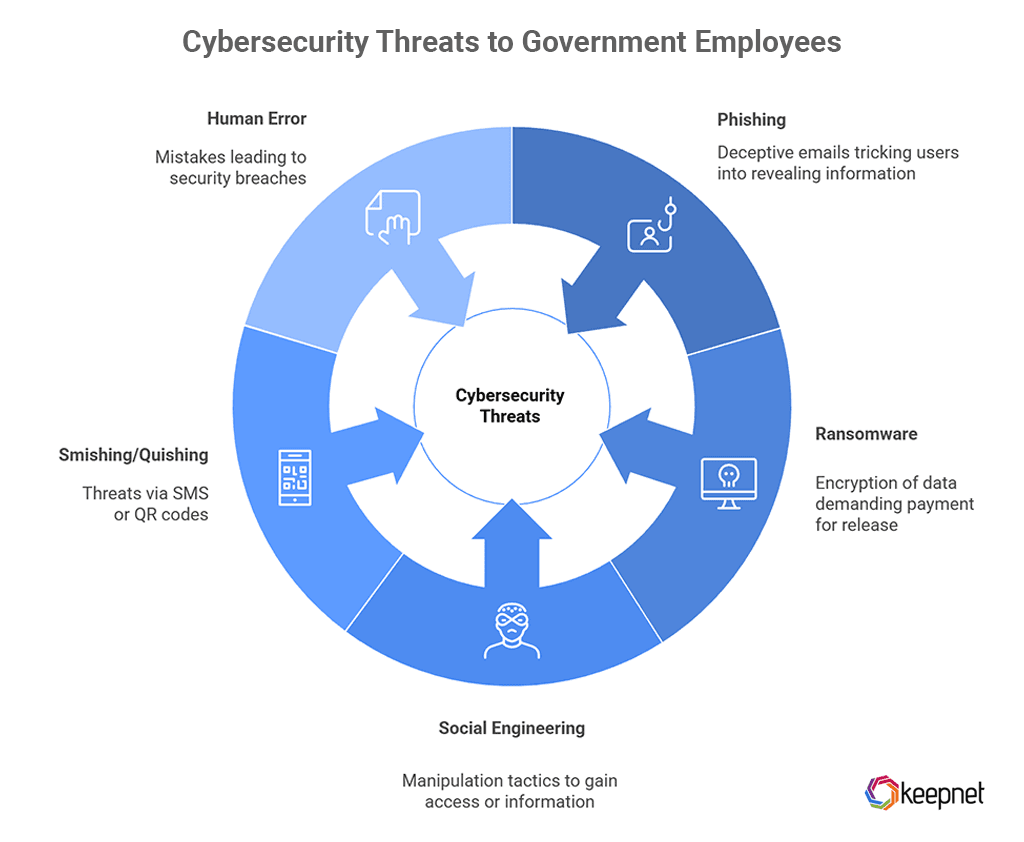
- Phishing and Spear Phishing: Attackers craft convincing emails that mimic trusted sources, tricking staff into clicking malicious links or sharing credentials. These are especially dangerous in government due to access to sensitive systems and data.
- Ransomware: Cybercriminals often target government networks with ransomware, encrypting critical data and demanding payment. Legacy systems and poor patch management make agencies more vulnerable.
- Social Engineering and Vishing: Phone-based scams (vishing) and impersonation tactics are rising. Attackers pose as colleagues or vendors to extract sensitive information.
- Smishing and Quishing: Threats delivered via SMS or QR codes are becoming more common in multi-channel communication environments.
- Human Error: Simple mistakes—like sending data to the wrong recipient or weak password practices—continue to be a leading cause of breaches in the public sector.
These threats aren't hypothetical—they're active, evolving, and increasingly tailored to exploit gaps in training and system defenses.
Watch the video below to see real scam stories involving smishing and vishing.
What Should Government Security Awareness Training Include?
A strong government security awareness program must be more than a checkbox exercise. It should be structured, measurable, and aligned with both operational roles and regulatory standards. Below are the key elements every agency should implement to create an effective and sustainable training strategy.
Role-Based Training
Cyber risks differ by function. A clerk managing citizen records faces different threats than a policy advisor or IT admin. Role-based training delivers tailored learning paths based on responsibilities—whether it’s spotting phishing attempts, handling sensitive documents, or managing vendor communication. This ensures each employee gains the knowledge most relevant to their daily tasks.
To explore how role-based security training can be customized and scaled across government teams, read the Keepnet guide on Role-Based Security Awareness Training.
Simulated Phishing Attacks & Gamified Training
Realistic simulations transform passive instruction into hands-on security readiness. Government agencies can use tools like Keepnet’s AI-powered Phishing Simulator to launch intelligent, context-aware phishing campaigns that mimic the latest threat tactics. Combined with Quishing Simulator and Callback Phishing, these tools safely test how employees respond to evolving attack vectors, such as QR code baiting or callback fraud.
What makes the training truly effective is the incorporation of gamification. Features like leaderboards, instant feedback, badges, and progress tracking transform security awareness into an engaging and competitive experience. This boosts employee participation and improves long-term retention of safe behaviors.
Learn more about how gamification drives results in awareness programs by reading the Keepnet blog: The Power of Gamification in Security Awareness Training
Compliance & Audit Readiness
Government agencies must follow strict cybersecurity regulations like FISMA, NIST SP 800-53, and CMMC. This means it’s not enough to simply offer training—agencies must also prove that employees have completed it, understood key policies, and are showing continuous improvement in their security behavior.
Key components include maintaining accurate logs of training completions, policy acknowledgments, and test scores, along with records that show measurable improvement over time. These elements are critical during audits and assessments to demonstrate a culture of compliance and proactive risk management.
For a full breakdown of what security awareness compliance involves and how to meet evolving standards, explore the Keepnet guide on Security Awareness Compliance: Requirements, Frameworks, and Best Practices.
How to Launch an Effective Security Awareness Program in Government Agencies
With government agencies increasingly targeted by phishing, ransomware, and insider threats, building an effective security awareness program is no longer optional. It demands a structured approach that aligns with actual risks, employee roles, and regulatory standards. Below are three critical steps to build a program that drives real behavior change and strengthens your agency’s cyber resilience.
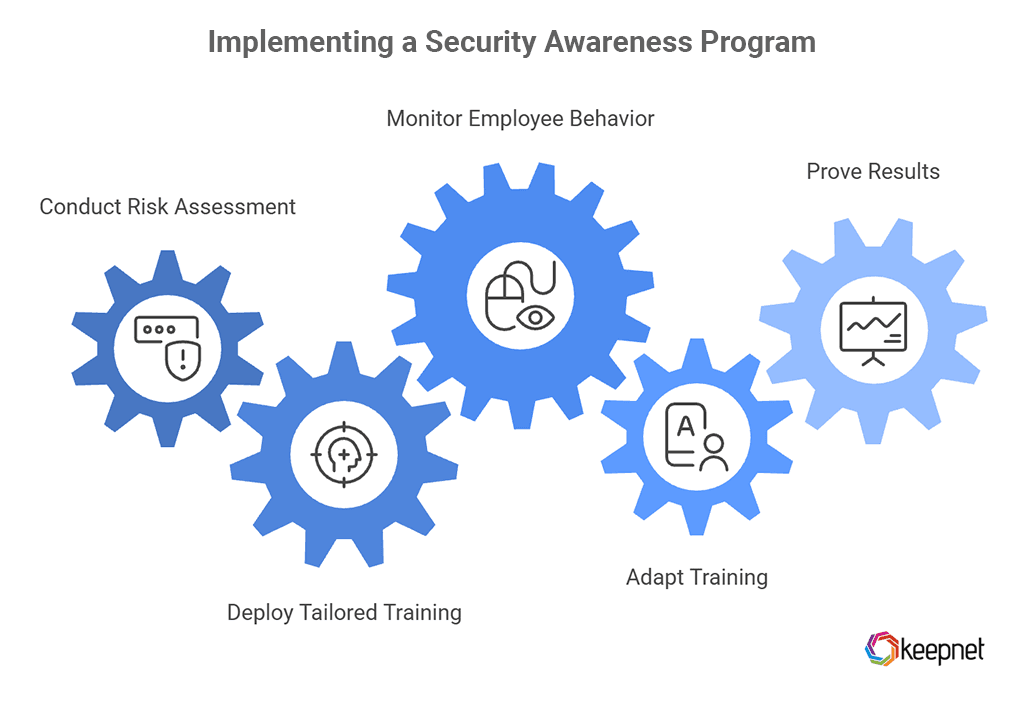
1. Conduct a Focused Risk Assessment
Start by identifying departments that handle high-risk data, such as citizen records, tax data, or infrastructure details. Use phishing simulations and employee surveys to assess the current level of cybersecurity awareness and pinpoint where users are most vulnerable. This ensures your training targets actual exposure—not assumptions.
Explore the Keepnet blog on Phishing Risk Score Trends Across Industries to better understand how different sectors measure risk and how you can benchmark your agency's performance effectively.
2. Deploy Tailored, Role-Specific Training
Design your training content based on job roles. Clerks, IT staff, and executives all face different threats—so a one-size-fits-all approach won’t work. Use Security Awareness Training to deliver relevant, scenario-driven content that covers phishing, smishing, quishing, and vishing threats specific to each function.
Integrate hands-on practice with Phishing Simulator, Quishing Simulator, Smishing Simulator, Vishing Simulator, MFA Phishing Simulation, and Callback Phishing to simulate real threats and evaluate user response in a safe environment. Offer multilingual support and microlearning to increase accessibility and participation.
3. Monitor, Adapt, and Prove Results
Track employee behavior through metrics like email reporting, click rates, and risk scoring. Identify patterns of risky behavior using analytics, and update your training based on real-world data—not static content.
Use Incident Responder to capture and act on suspicious email reports, and leverage Threat Intelligence to keep content aligned with current attack trends. Regularly produce performance reports to demonstrate progress and satisfy audit requirements.
Measuring Impact: Key Metrics for Government Security Training
To ensure your security awareness program delivers measurable results, it’s essential to track the right performance indicators. In a government context, these metrics help demonstrate effectiveness, support compliance audits, and guide continuous improvement.
| KPI | What It Measures |
|---|---|
| Phishing Simulation Results | Click rates, report rates, and response times—showing how well users detect threats. |
| Training Completion Rates | Percentage of employees who finish modules within assigned timeframes. |
| Behavioral Risk Scores, | Risk levels calculated from simulation outcomes and user actions. |
| Incident Reporting Volume | Number of suspicious emails or events reported by staff. |
| Repeat Offender Rates | Employees who consistently fail simulations or skip training |
| Policy Acknowledgment Rates | Confirmation that users have read and accepted cybersecurity policies. |
Table 1: Core KPIs for Evaluating Government Security Awareness Programs
Tracking outcome-driven metrics provides security leaders in government with the insights needed to refine programs, mitigate human risk, and meet compliance requirements with confidence.
Challenges to Watch For in Government Training Initiatives
Rolling out security awareness training in government comes with unique obstacles. Here are the key issues agencies often face:
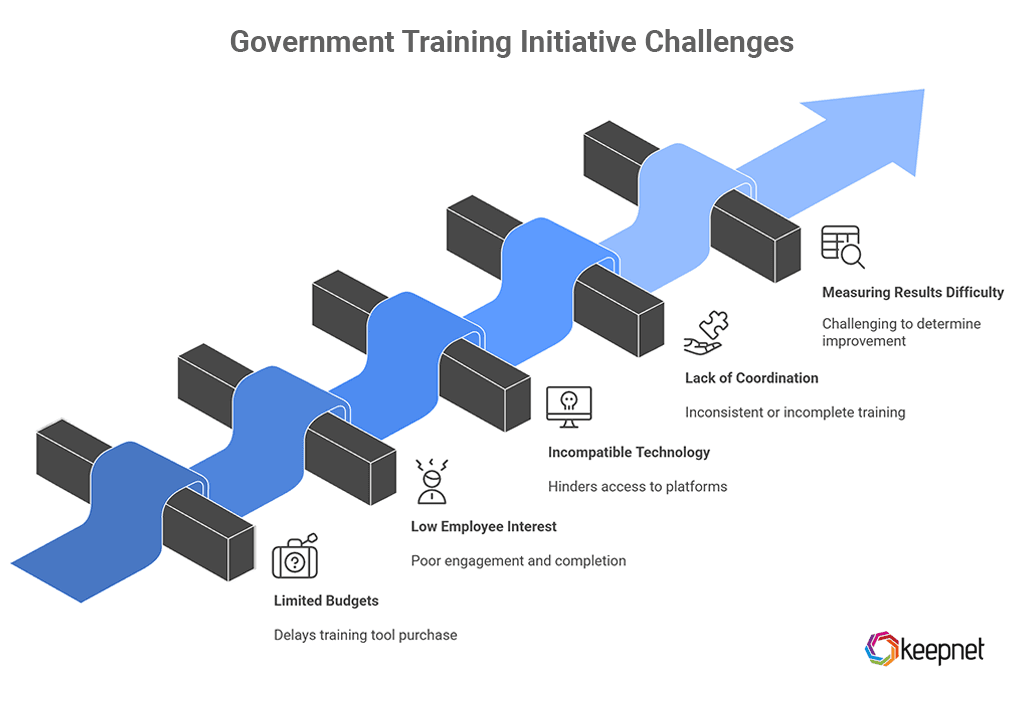
- Limited Budgets and Slow Approvals: Many government programs face strict budgets and lengthy procurement processes that delay the purchase and launch of training tools.
- Low Employee Interest: Staff often perceive training as irrelevant or repetitive, resulting in poor engagement and low completion rates.
- Incompatible Technology: Outdated systems and hardware can hinder the ability to run simulations or access modern training platforms.
- Lack of Coordination Between Teams: When IT, HR, and compliance departments fail to collaborate, training may be inconsistent or incomplete.
- Measuring Results with Difficulty: Without proper tracking tools, it’s challenging to determine who is improving, who remains at risk, and whether the program is effective.
To overcome these roadblocks, agencies need flexible training solutions that are easy to implement, provide actionable data, and keep employees actively involved.
Building a Resilient Public Sector Through Continuous Awareness Training
Cyberattacks on government agencies continue to rise in scale and sophistication, making employees a primary line of defense. Proactive security awareness training is important to prevent breaches that could expose citizen data, disrupt public services, or compromise critical government operations.
The reliability of your digital infrastructure depends on how prepared your staff is to recognize and respond to threats like phishing, smishing, and ransomware. One click on a malicious link can trigger a chain reaction of service outages, reputational damage, and regulatory consequences.
That’s why government agencies must treat security training not as a one-time task but as a continuous process embedded into their daily workflows. When training evolves into an ongoing behavior-driven program, it lays the foundation for a sustainable culture of cybersecurity.
To make that shift from training to culture, explore the Keepnet Human Risk Management Platform. This platform equips government agencies with AI-powered phishing simulations, adaptive learning modules, and automated incident response—enabling you to reduce risky behaviors, reinforce compliance, and build a workforce that actively defends against evolving cyber threats.
Editor's note: This blog was updated on January 9 th, 2026.