Hacking TikTok in 2025: How Does a TikTok Hack Actually Happen?
TikTok hacks are on the rise in 2025. From phishing scams to weak passwords, explore how hackers are hacking TikTok accounts and what you can do to secure yours.
In 2025, the number of TikTok hack incidents has skyrocketed, putting millions of users at risk of identity theft and data breaches. As the platform’s popularity continues to soar, hacking TikTok has become a growing focus for cybercriminals looking to exploit vulnerabilities.
From phishing attacks to weak login credentials, hackers are constantly finding new ways to hack TikTok accounts.
Whether you’re trying to understand how a TikTok hack happens or looking to avoid falling into the trap of those searching for “how to hack TikTok,” it’s essential to know how attackers operate.
In this article, we’ll break down how a TikTok hack typically occurs, explore the most common TikTok hack techniques, and share practical tips to help you stay protected.
What is TikTok Hack?
A TikTok hack refers to any situation where someone gains unauthorized access to your TikTok account. This often happens through phishing scam examples, fake login pages, or weak, reused passwords.
In some cases, attackers even use leaked credentials from other platforms to break into accounts — a tactic known as credential stuffing.
You might see online searches for how to hack TikTok, but these aren’t harmless tricks. They're often tied to illegal activity and can cause serious harm.
Whether it’s a personal account, a creator’s profile, or a brand page, the damage from a TikTok hack can include lost content, privacy breaches, and damaged reputations.
Once a hacker gets in, they can lock you out by changing your email, phone number, or password, making recovery difficult.
From there, they might send malicious messages, promote scam giveaways, or even impersonate you to target your followers. In some cases, hacked TikTok accounts are sold on dark web marketplaces.
What makes hacking TikTok accounts especially dangerous is how quickly it spreads.
TikTok’s viral nature means that just one post from a compromised account can reach thousands — or millions — of people.
That’s why it’s important to stay vigilant, understand the tactics hackers use, and take steps to protect your account before it’s compromised.
Why TikTok Is a Top Target for Hackers in 2025
It’s no accident that search terms like “tiktok hacked and logged out,” “tiktok hacked and email changed,” and “tiktok account hacked and deleted” are trending in 2025.
With over a billion daily users and highly personal data at stake, TikTok has become a goldmine for cybercriminals. From social engineering to full-scale account takeovers, attackers see TikTok as a vulnerable, high-reward platform—and they’re moving fast to exploit it.
Let’s break down exactly why TikTok accounts are being hacked, stolen, deleted, and monetized in record numbers.
Explosive Growth = Bigger Target Surface
TikTok passed 1.8 billion monthly users in early 2025. In the U.S. alone, more than 150 million people use it daily, with an average session lasting 95 minutes.
This “always-on” behavior means cybercriminals don’t need to wait for business hours to strike. Whether through phishing links in DMs or malware from fake third-party apps, the constant engagement creates an endless stream of opportunities for TikTok hacks.
That’s why so many people are suddenly searching:
- “tiktok account hacked and can’t log in”
- “tiktok hacked today”
- “tiktok account hacked how to recover without verification”
If you’ve ever been logged out of your account without changing your password, or noticed that your email and phone number were replaced, you’ve already seen how sneaky and destructive these hacks can be.
TikTok Is a Data Goldmine
TikTok collects far more than just your videos. According to its own policies, it can access your:
- Biometric data (faceprints, voiceprints)
- Precise location information
- Contacts, messages, and even clipboard data
All of this makes a TikTok account hacked incident far more dangerous than just losing your content. It opens the door to impersonation attack, identity fraud, deepfake attacks, and real-world harassment. This is why hacked accounts are increasingly discussed on forums like Reddit under queries such as:
- “tiktok hacked account reddit”
- “tiktok hacked and deleted reddit”
- “tiktok account hacked and banned reddit”
The stakes are no longer limited to losing followers — they now include losing your identity, reputation, and even income streams linked to Creator Rewards.
Monetization Makes Hijacked Accounts More Valuable
With TikTok rolling out monetization tools like Creator Funds and Pulse programs, hackers are now targeting accounts not just for fun—but for profit.
A hacked TikTok profile connected to a bank account or payment method can be quickly drained, sold, or exploited.
That’s why creators are frequently searching, “tiktok hacked and email changed” or “tiktok account hacked and stolen”.
Some victims even find their accounts rebranded, sold on dark web marketplaces, or permanently deleted before they can report it.
Regulatory Chaos Gives Hackers a Head Start
Governments around the world are scrambling to regulate TikTok’s operations. In the U.S., ByteDance is under court orders to divest the platform or face a full ban.
Meanwhile, Europe has issued record-breaking fines over cross-border data mishandling.
This public and political chaos gives hackers the edge. Many users searching “report tiktok account hacked” or “tiktok hacked form” find that response times are slow and support is overwhelmed.
And while TikTok does offer ways to report an account that’s been hacked or stolen, the lack of rapid resolution has turned recovery into a nightmare.
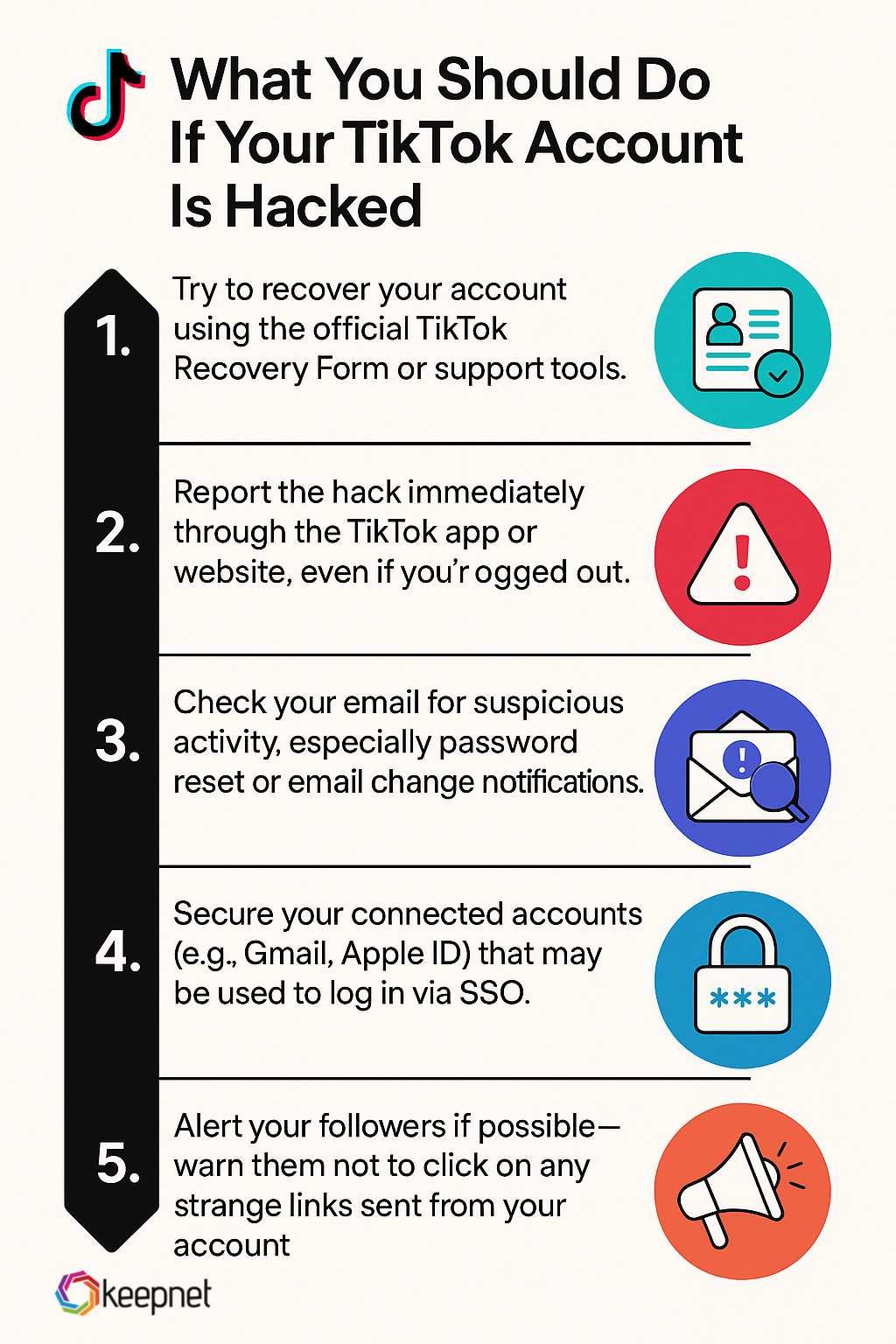
What You Should Do If Your TikTok Account Is Hacked
If you’re one of the growing number of people searching “tiktok hacked and logged out” or “tiktok hacked report form,” here’s what you need to do:
- Try to recover your account using the official TikTok Recovery Form or support tools.
- Report the hack immediately through the TikTok app or website, even if you’re logged out.
- Check your email for suspicious activity, especially password reset or email change notifications.
- Secure your connected accounts (e.g., Gmail, Apple ID) that may be used to log in via SSO.
- Alert your followers if possible—warn them not to click on any strange links sent from your account.
If you can’t access verification tools anymore (e.g., your phone number or email has been changed). Persistence, screenshots, and early reporting can increase your chances of recovery
TikTok isn’t just a video-sharing app anymore—it’s a digital identity hub with real financial value. In 2025, every TikTok account is a potential target.
If your TikTok account is hacked, banned, or deleted, don’t treat it lightly. Cybercriminals sure don’t.
How Does a TikTok Hack Happen in 2025?
TikTok takeovers now follow five repeatable attack paths—each fine-tuned for speed, scale and profit.
| # | 2025 Attack Path | What the Attacker Does | Why It Works |
|---|---|---|---|
| 1 | Zero-Day DM Exploits | Malicious code delivered via direct message runs the moment it’s opened, seizing full account control. | Victim action is minimal; recent zero-days proved the tactic at scale. |
| 2 | Phishing & Fake-Support Lures | Spoofed TikTok or brand emails/DMs push users to cloned login pages that capture credentials. | Mobile screens hide URLs, and creators are primed to click “partnership” links. |
| 3 | Credential Stuffing & Brute Force | Automated bots test billions of leaked email-password pairs until one grants access. | Weak or reused passwords from old breaches remain abundant fuel. |
| 4 | Session-Cookie Hijacking | Infostealer malware steals active TikTok cookies, letting attackers bypass MFA and log in instantly. | Black-market cookie dumps still contain millions of valid sessions. |
| 5 | SIM-Swap & 2FA Bypass | Attacker ports the victim’s phone number, intercepts SMS codes, then resets the password. | Many users rely on SMS 2FA; telco reps are vulnerable to social engineering. |
Table 1: TikTok Hack Attack Paths 2025
What is Typical Takeover Timeline of TikTok Hack?
- Recon (minutes) – Gather leaked credentials or profile email from public posts.
- Initial Breach (seconds-hours) – DM exploit, phishing click, or credential-stuffing “hit.”
- Persistence (under 5 min) – Change email, phone, password; add new 2FA device.
- Monetization (hours) – Push scam livestreams / crypto giveaways, sell the handle on dark-web markets, scrape followers for spear-phishing lists
- Cleanup (optional) – Delete original videos (as seen in the Kai Cenat hack).  
Bottom line: the 2025 attacker doesn’t need your password—just a single careless click, an old breach record, or an unpatched phone. The faster you deploy strong, unique passwords + app-based 2FA + device-level malware protection, the smaller the attack surface becomes.
Why Preventing a TikTok Hack Matters in 2025 for Every User?
As TikTok’s user base continues to expand, so does the risk of cyber threats.
Falling victim to a hack TikTok incident isn’t just a minor inconvenience—it can result in identity theft, stolen personal data, or even financial loss, especially for creators and businesses.
From weak passwords to overlooked privacy settings, cybercriminals are constantly hacking TikTok accounts using various methods.
A TikTok hack can happen to anyone, making account security essential for every user.
Protecting your TikTok account isn’t just about keeping your videos safe—it’s about defending your entire digital identity.
Enabling two-factor authentication is a strong first step, but staying ahead of threats requires ongoing vigilance and awareness.
For more details, check out the Keepnet Security Awareness Podcast episode exploring how TikTok hacks happen and what makes accounts vulnerable in 2025.
TikTok Hack Myths vs. Facts
Common misconceptions about TikTok hacks lead users to neglect proper security. Here’s what’s true and what’s not:
| # | Myth | Fact |
|---|---|---|
| 1 | Only influencers get hacked. | Any account, regardless of follower count, can be targeted. Cybercriminals often target smaller profiles due to weaker security practices. |
| 2 | If my account is private, I'm safe. | Private accounts limit visibility, but phishing links, weak passwords, and malware can still compromise your security. |
| 3 | Strong passwords alone are enough. | Strong passwords are essential but ineffective without multi-factor authentication (2FA) and good cyber hygiene. |
| 4 | I’ll know immediately if I'm hacked. | Many hackers quietly hijack accounts, leaving subtle signs like minor settings changes or unread messages. Regularly reviewing login history is essential. |
| 5 | Hacking TikTok is complicated and rare. | Hacking methods like credential stuffing, phishing, and cookie hijacking are straightforward and happen thousands of times daily. |
Table 2: TikTok Hack Myths vs. Facts
Understanding these truths ensures you don’t fall victim to misconceptions.
How Do Criminals Hack TikTok?
With over a billion users worldwide, TikTok has become a prime target for cybercriminals.
From phishing scams to credential stuffing, hackers are using increasingly clever techniques to hijack accounts.
In this section, we’ll explore the most common ways TikTok accounts hacked.
Phishing Attacks
Hackers often impersonate TikTok or well-known brands to lure users into providing their login credentials. Phishing email examples may direct users to a fake login page, or they may come as direct messages within the app, asking for sensitive details under false pretenses.
TikTok users must be aware of the different tactics used in phishing campaigns.
As noted in a recent phishing-based data breach, even high-level companies can fall victim to these tactics. This highlights how critical user education is in avoiding scams.
Brute Force Attacks
With weak or reused passwords, hackers can perform brute force attacks to guess login credentials. If your password is weak, it’s only a matter of time before it’s cracked.
Malware & Spyware
Malicious software can steal data from your phone, including TikTok login information. One such example is the rise of Android malware like SOVA banking malware, which is capable of stealing app credentials and even performing ransomware attacks.
Exploiting Weak Privacy Settings
Many users don’t adjust their TikTok privacy settings properly, leaving them exposed to threats. Hackers can exploit these loose settings to gather personal information and engage in social engineering attacks.
What are TikTok Hack Statistics & Trends for 2024-2025
This section provides a comprehensive analysis of the reported hacking incidents, their implications, and emerging trends, drawing from recent analyses and breach reports.
Background and Context
TikTok, owned by ByteDance, has been at the center of cybersecurity debates, particularly in the United States, where a law passed in April 2024 required ByteDance to divest its stake by January 19, 2025, or face a potential ban.
This legislative action, driven by concerns over data security and potential Chinese government influence, has coincided with several reported security breaches, amplifying public and governmental concern.
Reported Security Breaches in 2024-2025
The following table summarizes the key hacking incidents reported in 2024 and 2025, based on available information:
| Date | Threat Actor | Method | Data Compromised | Scale | TikTok's Response | Verification Status |
|---|---|---|---|---|---|---|
| June 2024 | Unknown | Malicious links via private messages | Account access, including CNN and other prominent accounts | Relatively small number of accounts | Stopped attack, worked with affected users | Verified by Bloomberg |
| April 2025 | R00TK1T | Alleged database breach | Over 900,000 usernames and passwords | Large-scale claim | No public response yet | Unverified, under scrutiny |
| May/June 2025 | Often9 | Exploited internal API vulnerability | 428 million user records (emails, phones, etc.) | Massive claim | Launched probe, stated no passwords involved | Debated, data quality issues |
Table 3: Major TikTok Hack Incidents (2024–2025)
June 2024 Breach
On June 4, 2024, Bloomberg reported that hackers targeted well-known brands and celebrities on TikTok by sending malicious links through private messages, successfully hijacking accounts, including that of CNN.
The breach affected a relatively small number of accounts, and TikTok responded by taking measures to stop the attack and prevent future occurrences.
The company also worked directly with affected account owners to restore access if needed.
This incident occurred amidst the U.S. law signed by President Joe Biden in April 2024, giving ByteDance 12 months to sell its TikTok stake or face shutdown, highlighting the timing's sensitivity.
For more details, see - TikTok Hit by Security Breach That Used Malicious Links.
April 2025 Breach
On April 24, 2025, a hacker collective known as R00TK1T announced via its Telegram channel that it had exfiltrated and was preparing to leak credentials for approximately 927,000 TikTok users, including usernames and passwords.
The group claimed that warnings to ByteDance went unheeded, prompting the public release of a sample dataset.
If authentic, this data could enable mass account takeovers, phishing campaigns, and identity theft, with R00TK1T asserting the ability to delete user accounts, locking users out of the platform.
As of the latest reports, these claims have not been independently verified, sparking widespread concern among cybersecurity experts and TikTok's global user base.
TikTok has not yet responded publicly to these specific allegations, though the company has faced prior scrutiny over data protection practices. See - Hackers Claim TikTok Breach: 900,000+ User Credentials Allegedly Leaked for further details.
May/June 2025 Breach
On May 29, 2025, a newly emergent threat actor named "Often9" claimed on a prominent cybercrime forum to have stolen 428 million unique TikTok user records through the exploitation of an internal API vulnerability.
The alleged stolen dataset included email addresses, mobile numbers, TikTok user IDs, usernames, nicknames, biographies, avatar URLs, profile links, account flags (such as private_account, secret, verified, ttSeller status), and publicly visible metrics like follower counts.
However, skepticism surrounds the claim due to the dataset's quality, with many entries showing empty or generic fields for emails and phone numbers, suggesting possible scraping from public profiles or inclusion of old breach data.
Analysis by Hackread found that most exposed email addresses in a sample (1,200 lines from 428 million) were found in fewer than two previous breaches on HaveIBeenPwned, adding to doubts.
TikTok launched a probe into the purported breach and clarified that no passwords were involved.
This incident follows a historical context of similar claims, such as a September 2022 allegation of 2 billion records, which TikTok denied.
For more details, check - Massive TikTok breach claimed to compromise 428M users and Threat Actor Claims TikTok Breach, Puts 428 Million Records Up for Sale.
What are Emerging Trends in TikTok Hacking
Based on the reported incidents, several trends are evident in TikTok's security landscape for 2024-2025:
Increased Frequency of Reported Breaches
The timeline shows multiple reported or claimed breaches within a short period, suggesting a potential rise in hacking attempts.
This includes the verified June 2024 breach and the unverified April and May/June 2025 claims, indicating heightened activity from threat actors.
Large-Scale Data Breaches
The claimed breaches in 2025, particularly the Often9 claim of 428 million records, suggest a trend toward mass data exfiltration.
Such large-scale breaches, if verified, could pose significant risks for identity theft, phishing, and dark web sales, reflecting hackers' focus on high-volume data.
Targeting Prominent Accounts
The June 2024 breach specifically targeted high-profile accounts like CNN, indicating a trend of hackers focusing on prominent users for greater impact.
This could be driven by motives such as financial gain, visibility, or disruption, given the public nature of these accounts.
Methods Used
Hackers have employed diverse tactics, including social engineering (malicious links via private messages in 2024) and technical exploits (API vulnerabilities in 2025 claims).
These methods highlight the multifaceted nature of attacks, combining social engineering exampleswith technical vulnerabilities to compromise user data and accounts.
Skepticism Around Breach Claims
The legitimacy of large-scale breach claims, especially in 2025, is often debated due to data quality issues.
For instance, the Often9 dataset's many empty fields suggest it might be from scraped public profiles or old breaches, aligning with historical patterns of false claims on cybercrime forums, such as a previous fake "1.2 billion Facebook user" data sale.
Regulatory and Governmental Scrutiny
TikTok's security breaches occur amidst significant regulatory pressure, particularly in the U.S., where concerns about data security and potential ties to the Chinese government have led to legislative actions.
The April 2024 law and ongoing debates about a potential ban underscore the broader context, with leaders like John F. Plumb, assistant secretary of defense for space policy, highlighting TikTok as a potential cybersecurity risk in 2023 testimony.
TikTok's Response to Security Challenges:
For the June 2024 breach, TikTok took immediate action, stopping the attack and collaborating with affected users, demonstrating a reactive approach.
For the 2025 claims, TikTok launched investigations and clarified details, such as no passwords being involved in the Often9 claim, but the platform continues to face challenges in maintaining user trust and addressing vulnerabilities.
Can Someone Hack a TikTok Account Using Python?
With a surge in searches like “how to hack a TikTok account using Python,” many are curious about whether it’s even possible—and more importantly, how to protect against these emerging threats. Let’s set the record straight.
🚫 No, You Shouldn’t Try to Hack TikTok (Here’s Why)
Attempting to hack TikTok, or any online platform, is illegal and unethical. It can result in:
- Criminal charges under anti-cybercrime laws
- Permanent bans from TikTok and other platforms
- Severe consequences if you’re caught distributing hacking tools or code
Even searching for Python scripts to hack TikTok accounts puts you at risk—many so-called “hacking tools” are actually malware that steal your own data.
How Hackers Actually Exploit TikTok Users
Rather than complex code or exploits, most TikTok account hacks happen through:
- Phishing attack examples: Fake login pages or DMs that trick users into revealing passwords
- Password reuse: Using the same password across platforms
- Weak credentials: Simple passwords like “123456” or “tiktok123”
- Session hijacking: Stealing tokens from browser sessions or apps
Python isn’t the real danger—social engineering is.
Search trends like “how to hack a TikTok account using Python” reflect more than curiosity—they reflect the need for stronger cybersecurity education. I
nstead of looking for ways to attack, learn how to defend.
Most TikTok hacks don’t rely on complex scripts or coding; they succeed because people are tricked into handing over their credentials.
Hackers often impersonate TikTok support, send fake login links, or create urgent-sounding messages to manipulate users emotionally.
It’s not about brute-force attacks—it’s about exploiting human trust. That’s why security awareness and caution are your strongest defenses.
Step-by-Step: Recovering a Hacked TikTok Account
Recovering your hacked TikTok account quickly can prevent serious damage. Follow these actionable steps immediately:
1. Identify the breach: Check your registered email for unusual activity, like a changed password notification or new device login alerts. 2. Initiate TikTok’s account recovery: • Visit TikTok’s Account Recovery page. • Select “Report a problem” and choose “Hacked Account.” 3. Provide verification information: • Enter your original email address or linked phone number. • Provide previous passwords, login locations, or linked social accounts.
4. Contact TikTok support directly: • Use the “Feedback” option within TikTok or email privacy@tiktok.com for priority response. • Include your username, last login details, and clear proof of account ownership. 5. Secure your account post-recovery: • Immediately set a strong, unique password. • Enable multi-factor authentication (preferably app-based). • Review and revoke suspicious devices in your account settings. Tip: Act within the first 24 hours after noticing the breach—the faster you respond, the higher your chance of recovering your account fully intact.
TikTok Security Settings Walk-Through (2025 Update)
TikTok has expanded security options significantly in 2025. Follow this updated checklist to secure your account:
Enable Two-Factor Authentication (2FA):
• Go to Profile → Menu (three lines) → Settings and Privacy → Security → 2-Step Verification.
• Select “Authentication App” as your primary verification method to avoid SMS vulnerabilities.
Check Account Login History:
• Navigate to Settings → Security → Your Devices.
• Remove unknown or inactive devices immediately.
Review Privacy & Safety Settings:
• Set your account to private: Settings → Privacy → Toggle Private Account.
• Limit direct messages, comments, duets, and stitches to “Friends Only” or “Nobody.”
Disable Location Data Access:
• Under Settings → Privacy → Location Services, restrict TikTok’s ability to track your precise location.
Limit App Permissions:
• On your mobile device settings, regularly audit and restrict unnecessary permissions granted to TikTok.
Following this routine quarterly significantly reduces your attack surface.
How Can You Protect Your TikTok Account from Being Hacked?
To protect yourself from a TikTok account hack, you need to adopt a layered security approach. This includes securing your account settings, updating your password policies, and staying vigilant about potential threats. Here’s what you can do:
Use Strong, Unique Passwords
Avoid using simple, easy-to-guess passwords. Tools like password managers can help you create and store strong, unique passwords.
The importance of password strength is often underestimated, but it plays a vital role in keeping hackers at bay. Consider reviewing some tips on password protection intelligence to avoid this common pitfall.
Enable Two-Factor Authentication (2FA)
Two-factor authentication on TikTok adds an extra layer of security by requiring a second form of verification.
This means that even if someone steals your password, they will need access to your phone or email to log in.
2FA is widely regarded as one of the most effective ways to secure your account.
Be Aware of Phishing Scams
Stay cautious of suspicious emails, texts, or DMs, especially those asking for login details.
Always verify the legitimacy of requests and avoid clicking on suspicious links.
Phishing has become a leading threat vector, not just for TikTok, but for all digital accounts.
Learning to identify phishing emails can save you from significant trouble—here’s a guide on recognizing phishing emails that can help.
Monitor App Permissions
Regularly check what permissions you've granted to TikTok and other apps on your phone. This will reduce the risk of apps accessing your personal data without your consent, as highlighted in mobile device security.
What Are the Best Practices to Prevent TikTok Hack?
TikTok users can minimize security risks by following best practices that go beyond just securing passwords. Here are a few expert-recommended measures:
Regularly Review Your Privacy Settings
Ensure that your privacy settings on TikTok limit who can view your content, send you messages, and interact with your account. Set your account to private, control your comments, and restrict duets and stitches to avoid exposing yourself to unwanted interactions or threats.
Update Your Software
Make sure both TikTok and your mobile device's operating system are always updated to the latest version. Security patches often address vulnerabilities that hackers could exploit. Cybercriminals are constantly finding new ways to breach systems, so it’s crucial to stay ahead with updated software.
Be Mindful of Third-Party Apps
Avoid using third-party apps or services that promise to increase your followers or likes. These can often be a trap where malicious actors gain access to your account. If you're unsure about app safety, learn more about how certain apps can compromise your privacy, like in-app browsers tracking user activity.
Enable Account Recovery Options
Ensure you have recovery options like email or phone number verification activated. This makes it easier to regain access to your account if you suspect it’s been hacked.
Stay Informed
Security awareness is your best defense. Stay updated with the latest cybersecurity news and trends affecting TikTok and social platforms. For example, the evolution of security awareness shows how threats are constantly evolving, making it essential for users to remain vigilant.
Further Reading:
- The Importance of Password Protection Intelligence
- Securing Mobile Devices
- Email Security: 7 Biggest Threats
- SOVA Android Banking Malware
- How to Protect Your Business Against Ransomware
- Phishing Email Examples to Avoid in 2025
- The Importance of Collaborative Defense in Cybersecurity
- Understanding Smishing: The Growing Threat
- Ransomware and SMEs: How Vulnerable Are Small Businesses?
Editor’s Note: This blog was updated on November 13, 2025.