Pop-Up Phishing: How to Spot and Stop Fake Alerts (Before You Panic)
Pop-up phishing is the ‘fake alert’ scam that hijacks your screen with urgent warnings like “Virus found!” or “Account locked.” This guide shows real patterns, what to click (and not), and defenses for users and teams—in minutes, no fluff!
Pop-up phishing is one of the most effective “low-effort, high-reward” tricks in social engineering because it attacks attention, not just technology. The goal is simple: shock you with an urgent message, rush you into clicking, and steer you toward a fake login, a bogus “scan,” a scam support number, or a malicious download.
If you’ve ever seen a sudden pop-up saying “Your device is infected!”, “Apple Security Warning”, “Windows Defender Alert”, “Your bank account is locked”, or “Claim your prize”—you’ve seen the playbook.
This article covers what pop-up phishing is, the most common variations, the red flags people miss, and exactly what to do if you clicked.
What Is Pop-Up Phishing?
Pop-up phishing is a social engineering attack that uses fake on-screen messages (pop-up windows, browser overlays, push notifications, interstitial pages, or “system alert” lookalikes) to manipulate people into:
- entering passwords or payment details
- calling a scam “support” number
- installing unwanted software (malware or “scareware”)
- granting remote access to their device
- approving MFA prompts (“MFA fatigue”)
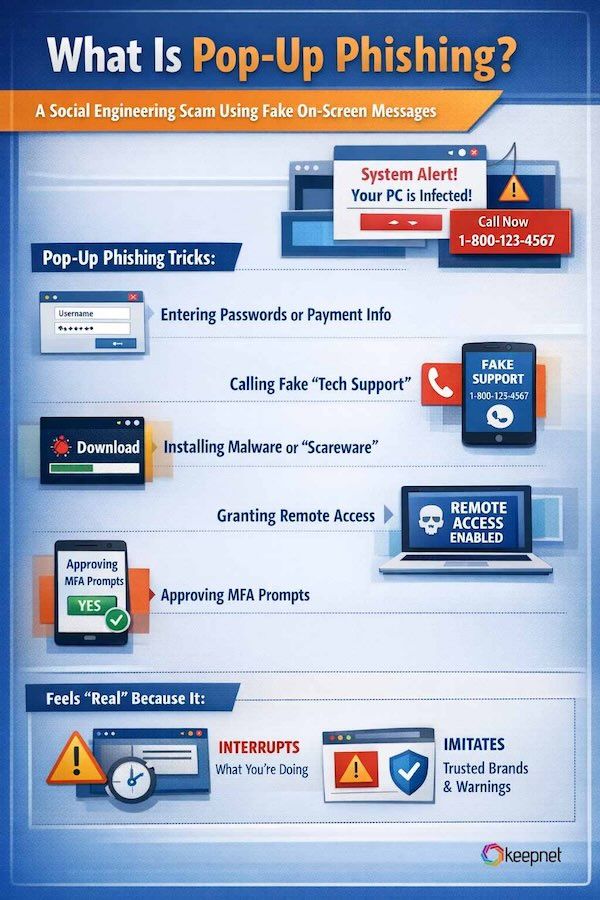
Unlike classic email phishing, pop-up phishing often feels more “real” because it interrupts what you’re doing and imitates trusted brands or system warnings.
Why Pop-Up Phishing Works (Even on Smart People)
Pop-up phishing is optimized for human psychology. Most successful pop-ups combine:
- Urgency (“Act now or you’ll lose access”)
- Authority (Microsoft, Apple, Google, your bank, your IT team)
- Fear or reward (“Virus detected” or “You’ve won!”)
- A single obvious action (“Click here,” “Call now,” “Allow”
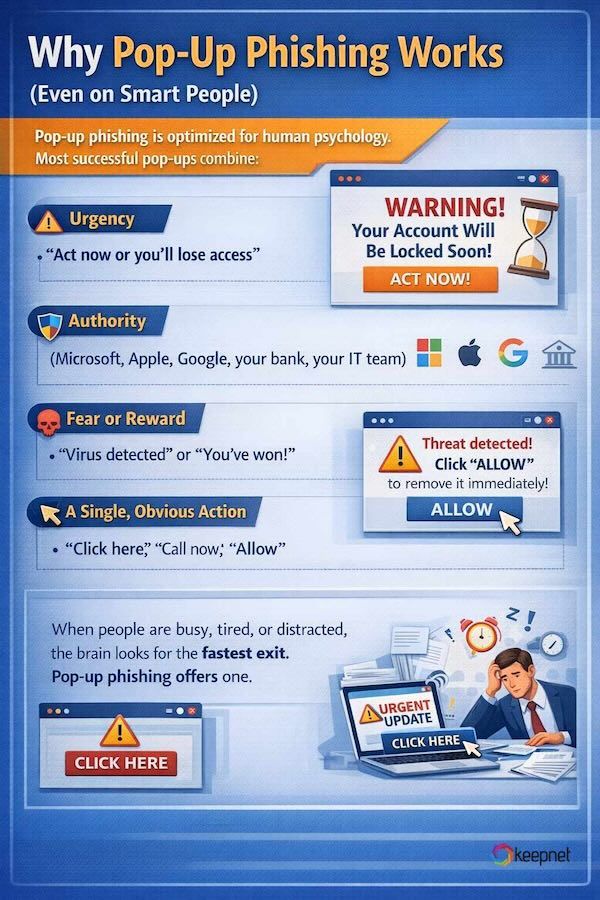
When people are busy, tired, or distracted, the brain looks for the fastest exit. Pop-up phishing offers one.
Pop-Up Phishing Variations You’ll See on Google (and in Real Life)
Below are the most common pop-up phishing “flavors” people search for—plus what the attacker typically wants.
1) Fake Virus Pop-Up / Scareware Pop-Up
These claim your device is infected and push you to “scan,” “clean,” or download a security tool. The endgame is usually malware, subscription fraud, or data theft.
2) Tech Support Scam Pop-Up (Call This Number)
A loud, full-screen warning tells you to call “Microsoft Support” or “Apple Support.” The scammer then pressures you into remote access and payment.
3) “Session Expired” / “Password Reset Required” Pop-Up
This variation mimics login screens for Microsoft 365, Google Workspace, banking apps, HR portals, or VPN tools. هدف: steal credentials.
4) “Unusual Sign-In Attempt” + MFA Prompt Flooding
You see a pop-up that looks like a security alert, then you receive repeated MFA prompts. The attacker wants you to approve just once.
5) Browser Update Pop-Up (“Update Chrome/Safari Now”)
Fake update prompts trick users into downloading malicious installers, extensions, or configuration profiles.
6) Push Notification Phishing (“Allow Notifications”)
A site asks you to click Allow to prove you’re not a bot, watch a video, or continue. After you allow it, your browser sends phishy alerts even when you’re not on that website.
7) Prize / Survey / Coupon Pop-Ups
“You won an iPhone!” “Spin to win!” “Complete this survey!” These aim for payment details, personal data, or affiliate fraud.
8) QR Pop-Ups (Quishing Overlays)
A pop-up shows a QR code to “verify,” “sign in,” or “fix an issue.” The QR leads to a phishing page—often harder to inspect on mobile.
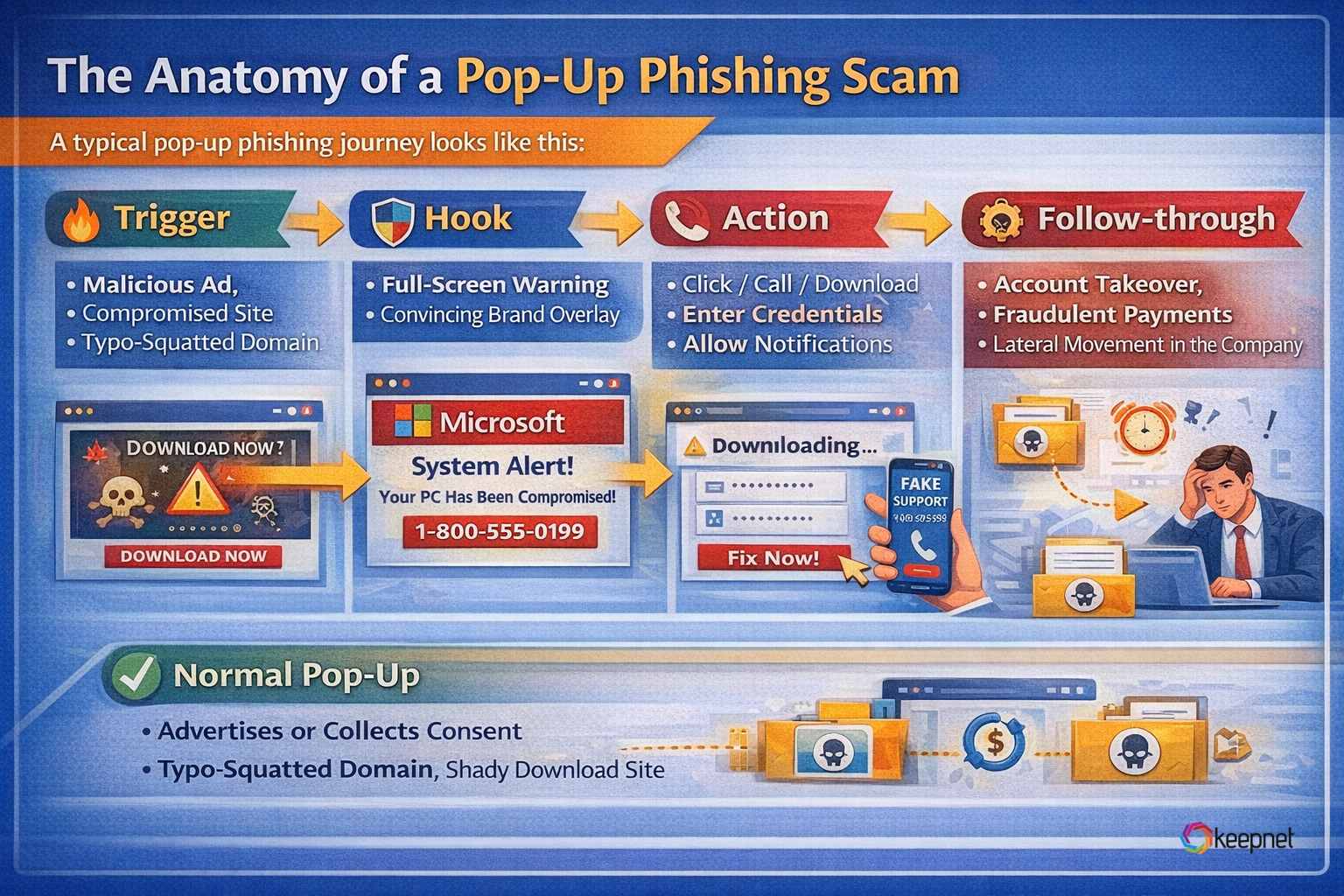
The Anatomy of a Pop-Up Phishing Scam
A typical pop-up phishing journey looks like this:
- Trigger: Malicious ad, compromised site, typo-squatted domain, or shady download site
- Hook: Full-screen warning or convincing brand overlay
- Action: Click / call / download / enter credentials / allow notifications
- Capture: Credentials, card data, remote access, or device infection
- Follow-through: Account takeover, fraudulent payments, lateral movement in the company
12 Red Flags That a Pop-Up Is Phishing
If you want a fast “sniff test,” look for these:
- A phone number inside a “security alert” (major red flag)
- Spelling/grammar mistakes or weird phrasing
- Overly dramatic threats (“Your SIM will be destroyed!”)
- Countdown timers pushing you to act
- Your browser is blamed, not a specific security tool you installed
- Unknown URL/domain in the address bar (not the brand’s real domain)
- Requests to install an “antivirus” you’ve never heard of
- Permission tricks (“Click Allow to continue”
- Full-screen lock behavior that tries to stop you closing the tab
- Claims you “won” something without entering a contest
- Pressure to bypass policy (“Disable your security to proceed”)
- It appears on random websites unrelated to the alert’s brand
What To Do If You Clicked a Pop-Up Phishing Alert
If you interacted with a suspicious pop-up, don’t panic—follow a clean sequence.
Step 1: Don’t call, don’t pay, don’t install
If the pop-up tells you to call a number or install a tool, stop. That’s how the scam escalates.
Step 2: Close it safely
- Try closing the tab (not the pop-up button).
- If it’s “stuck,” force-quit the browser/app and reopen it.
- Reopen without restoring previous tabs if your browser asks.
Step 3: Remove anything you installed (if applicable)
- Uninstall unknown apps/programs.
- Remove suspicious browser extensions.
- Check for odd “device management” profiles (especially on mobile/enterprise devices).
Step 4: Change passwords (from a clean device)
If you typed credentials:
- change the password immediately
- enable MFA (prefer authenticator app or hardware key)
- check recent sign-ins and active sessions
- rotate the password anywhere you reused it
Step 5: Scan and report (especially at work)
- Run your approved endpoint security scan
- report to IT/SOC with the URL and screenshots
- if remote access was granted, treat it as a security incident
How To Prevent Pop-Up Phishing (Personal + Business)
Pop-up phishing is best reduced with layered defenses: browser hygiene, technical controls, and behavior training.
Personal Protection Checklist
- Keep your browser and OS updated (via official settings, not pop-ups)
- Use a password manager (it won’t autofill on fake domains)
- Block suspicious permissions: avoid “Allow notifications” on random sites
- Don’t search “support phone numbers” via pop-ups—go to official websites
- If something looks urgent, pause and verify via a second channel (official app, bookmark, IT portal)
Business Protection Checklist (Security Teams)
- Enforce DNS/web filtering and block known malicious categories
- Use browser isolation or hardened browsers for high-risk roles
- Control extension installs (allow-list only)
- Monitor for push notification abuse and risky browser permissions
- Implement phishing-resistant MFA where possible (FIDO2 / security keys)
- Train staff with short, realistic phishing simulations (including pop-up & “Allow” traps)
- Make reporting easy: one-click “Report Phish” + fast feedback loop
Pop-Up Phishing vs. “Normal Pop-Ups”: The Simple Difference

A normal pop-up tries to advertise or collect consent (cookies, newsletter). A phishing pop-up tries to move you into a risky action fast—login, install, pay, call, or allow permissions.
If the pop-up asks for credentials, money, remote access, or urgent action, treat it as hostile until proven otherwise.
Turn Pop-Up Phishing Into a “Boring” Non-Event
Pop-up phishing wins when people feel rushed and alone. It loses when your organization builds clear habits, technical guardrails, and fast reporting.
If you’re building a measurable human-risk program, Keepnet’s Human Risk Management Platform that include various tools like Security Awareness Training, and Phishing Simulator help teams train against modern social engineering patterns (including pop-up-driven credential traps, push notification abuse, MFA fatigue, and QR-led attacks).