Understanding XDR: The Future of Threat Detection and Response
XDR is the future of threat detection. Explore how this unified approach revolutionizes cybersecurity, outpaces EDR, and secures your digital ecosystem.
Cyber threats are becoming more advanced, making traditional security measures insufficient. Businesses face complex attacks that target vulnerabilities across endpoints, networks, and servers, creating an urgent need for a unified and proactive cybersecurity approach. In fact, the IBM Cost of a Data Breach Report 2024 reveals that the average cost of a data breach has risen to $4.88 million, a 10% increase from the previous year, emphasizing the high stakes of these evolving threats.
XDR (Extended Detection and Response) addresses this challenge by integrating threat detection, real-time analysis, and automated responses. By consolidating security data from multiple sources, XDR provides a clearer view of risks and enables faster, more effective mitigation.
This blog post guides you through understanding XDR’s capabilities and its role in modern cybersecurity strategies.
What is XDR?
XDR (Extended Detection and Response) is a modern cybersecurity approach that unifies threat detection, investigation, and response across multiple security layers—including endpoints, networks, cloud services, email, and identity systems. Unlike traditional tools that operate in silos, an XDR platform brings all telemetry into a single view, correlates related events, and uses analytics and automation to stop attacks faster.
In simple terms, XDR security gives organizations a complete picture of their IT environment and the ability to detect advanced threats, such as ransomware, phishing, and insider attacks, before they cause damage. By combining visibility, automation, and contextual intelligence, XDR solutions reduce false positives, speed up incident response, and strengthen overall cyber resilience.
Core Features of XDR
XDR is designed to provide a unified and proactive approach to cybersecurity. By centralizing data, leveraging machine learning, and integrating various sources, it enhances visibility, streamlines threat detection, and enables swift responses to security incidents. Here’s how XDR achieves this:
- Unified Threat Detection: Centralizes data across IT environments to provide a comprehensive view.
- Real-Time Analysis: Uses machine learning (ML) and automation to detect anomalies and respond instantly.
- Integrated Data Sources: Combines insights from endpoints, network traffic, and user behaviors for a proactive defense.
Why Traditional Security Measures Are Falling Short
Legacy solutions like antivirus software or Endpoint Detection and Response (EDR) struggle to address the complexity of modern threats. These tools operate in silos, focusing on specific attack surfaces rather than providing a unified defense strategy. For instance, insider threats or phishing attacks often bypass traditional detection methods.
Key Challenges with Traditional Solutions
- Limited visibility across IT ecosystems.
- High rates of false positives that overwhelm security teams.
- Reactive threat management rather than proactive prevention.
XDR bridges these gaps by providing a comprehensive, integrated security framework.
How XDR Works: A Unified Security Approach
Extended Detection and Response addresses the limitations of traditional tools by unifying visibility, analytics, and response across the entire IT ecosystem. Instead of managing scattered alerts from different products, an XDR platform delivers a single, integrated view of threats. Here’s how XDR security works in practice:
1. Data Collection Across Multiple Vectors
- XDR collects and correlates data from diverse sources, including:
- Endpoints such as laptops, mobile devices, and servers
- Networks like firewalls, routers, and switches
- Cloud environments (SaaS and IaaS platforms)
- Email systems targeted by phishing or malware
- Identity and access management (IAM) solutions
By pulling telemetry from every layer, XDR cybersecurity creates a holistic picture of activity across the digital environment.
2. Correlation and Contextualization
Once gathered, this information is normalized and enriched with threat intelligence, machine learning, and behavioral analytics. Instead of isolated, noisy alerts, XDR solutions link related events together to expose the complete attack chain. This context helps analysts understand not just what happened, but how and why—turning raw data into actionable intelligence.
3. Automated Detection and Response
With continuous monitoring, XDR security platforms can identify suspicious behavior in real time. When a threat is detected, the system can:
- Quarantine infected endpoints to prevent lateral movement
- Block malicious IP addresses, domains, or processes
- Disable compromised user accounts through IAM integration
- Send clear, contextual alerts so analysts know exactly where to focus
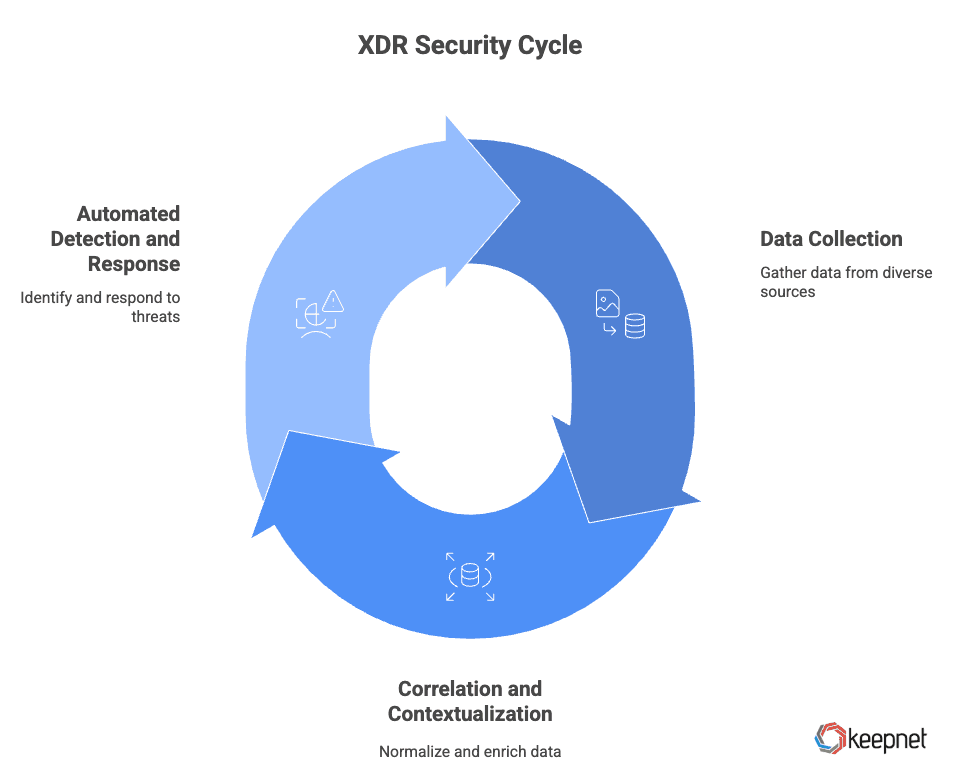
This automated, coordinated response makes XDR far more effective than siloed detection tools, reducing dwell time and improving overall cyber resilience.
Key Benefits of XDR
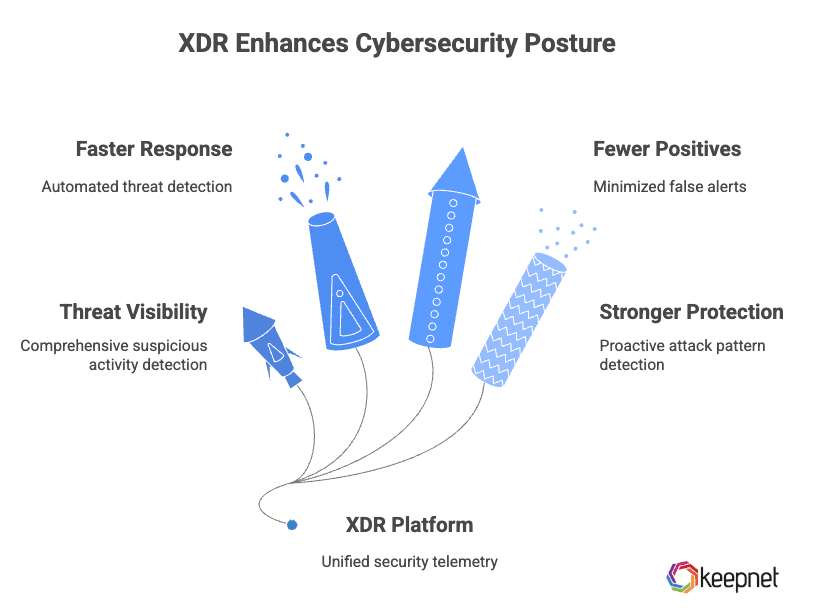
XDR is more than just another tool—it’s a modern XDR security solution that gives organizations the visibility and speed they need to stay ahead of cyber threats. Here are the core benefits that make XDR cybersecurity a game-changer:
1. Comprehensive Threat Visibility
Unlike siloed security products, an XDR platform aggregates telemetry from endpoints, networks, cloud services, email, and identity systems. This unified approach ensures that no suspicious activity—whether on a laptop, server, or firewall—goes unnoticed.
2. Faster Detection and Response
By automating threat detection and orchestrating responses across multiple vectors, XDR solutions help security teams act before an attack escalates. From isolating a compromised endpoint to blocking malicious IP addresses, XDR reduces the time from detection to containment.
3. Fewer False Positives
Traditional tools often flood analysts with noise. XDR cybersecurity correlates events and applies advanced analytics to minimize false positives, freeing up analysts to focus on the alerts that truly matter.
4. Stronger Protection Against Advanced Threats
Modern attacks, such as zero-day exploits, insider abuse, and targeted intrusions, require defenses that can adapt. With XDR security, organizations gain a proactive shield that detects subtle attack patterns and responds in real time, even against sophisticated adversaries.
XDR vs. EDR: What’s the Difference?
While EDR is powerful for protecting devices, XDR is holistic, recognizing that modern attacks often span across multiple vectors.
| Feature | EDR | XDR |
|---|---|---|
| Data Source | Endpoint-only | Endpoint + Network + Email + Cloud + Identity |
| Visibility | Limited to devices | End-to-end visibility across the entire environment |
| Detection Capabilities | Signature + Behavior-based | Correlated, contextual, and multi-layered |
| Response Actions | Endpoint-specific | Coordinated across all security domains |
| Alert Volume | High | Lower, more accurate, more actionable |
Table 1: XDR vs. EDR: What's the Difference?
Is XDR Right for Your Organization?
If your security team is drowning in alerts, struggling with tool sprawl, or reacting too slowly to advanced threats, Extended Detection and Response (XDR) may be the solution. By consolidating siloed technologies into a single XDR platform, organizations gain visibility, context, and automation that traditional tools simply can’t deliver.
XDR security is especially valuable for:
- SMBs and mid-sized enterprises that lack large SOC teams but still need enterprise-grade defenses.
- Mature security programs seeking to simplify operations by replacing multiple tools with one unified XDR solution.
- High-risk industries like healthcare, finance, and retail, where sensitive data and complex infrastructures create larger attack surfaces.
- Remote and hybrid environments, where expanded endpoints and cloud adoption demand stronger, centralized threat detection.
Common Use Cases for XDR
The real power of XDR cybersecurity lies in how it applies advanced analytics and automation across diverse scenarios:
- Stopping Ransomware: From the first phishing email to lateral movement inside the network, XDR solutions detect, track, and isolate ransomware attacks before they cripple operations.
- Detecting Insider Threats: With behavioral analytics and machine learning, XDR security platforms identify unusual user activity such as unauthorized data access, exfiltration, or privilege escalation.
- Mitigating Supply Chain Attacks: By correlating anomalies across third-party applications, cloud services, and infrastructure layers, XDR cyber security closes blind spots that attackers often exploit in supply chain compromises.
Challenges of XDR Adoption
Like any transformative cybersecurity investment, Extended Detection and Response (XDR) comes with certain challenges that organizations should consider before implementation:
1. Vendor Lock-In
Many XDR solutions are optimized to run within their vendor’s ecosystem. While this tight integration can improve performance, it may also limit flexibility if your team relies on a diverse stack of third-party tools.
2. Initial Complexity
Deploying an XDR platform often requires integration with legacy systems, fine-tuning analytics, and aligning processes. This initial complexity can delay time-to-value, particularly for organizations with large or fragmented infrastructures.
3. Skill Gaps
Even the best XDR security tools require skilled analysts to maximize effectiveness. Security teams may need additional training to fully leverage advanced detection, correlation, and automated response capabilities.
Despite these hurdles, most organizations find the short-term barriers outweighed by the long-term advantages of XDR cybersecurity, including unified visibility, reduced false positives, faster incident response, and improved overall resilience. For businesses serious about defending against advanced threats, extended detection and response represents a strategic leap forward.
Implementing XDR with a Zero Trust Approach
The Zero Trust security model is built on a simple but powerful principle: never trust, always verify. No user, device, or application should be automatically trusted—even if it’s operating inside the traditional network perimeter. Instead, every access attempt must be continuously validated and monitored for risk.
Extended Detection and Response (XDR) strengthens this approach by delivering real-time visibility and automated defenses across the IT environment. An XDR platform continuously collects and analyzes telemetry from endpoints, networks, cloud services, and identity systems to uncover suspicious activity that might bypass perimeter defenses.
When combined with Zero Trust, XDR security solutions provide a proactive, layered defense strategy:
- Continuous Verification: Ensures every access request is authenticated and authorized.
- Advanced Detection: Correlates signals from multiple vectors to reveal hidden threats.
- Automated Response: Quarantines endpoints, blocks malicious traffic, or disables compromised accounts in real time.
Together, Zero Trust and XDR cybersecurity create a stronger, more resilient security posture—empowering organizations to detect, prevent, and respond to threats before they escalate.
Keepnet Human Risk Management Platform
While XDR security platforms deliver powerful defenses against technical threats, most breaches still exploit the human element—clicking a phishing link, reusing weak passwords, or mishandling sensitive data. To achieve true end-to-end protection, organizations must strengthen both their technology layer (XDR) and their human layer (Keepnet).
The Keepnet Human Risk Management Platform addresses this challenge by equipping employees with the skills, awareness, and tools to reduce human risk:
- Phishing Simulator: Run realistic phishing campaigns to train employees to identify and avoid social engineering attacks.
- Incident Responder: Automate detection and remediation of malicious emails, stopping threats before they spread.
- Awareness Educator: Deliver interactive training modules that help staff recognize and respond to cyber risks.
When paired with extended detection and response (XDR), Keepnet closes the biggest gap in cybersecurity: the human factor. Together, they create a unified defense strategy that reduces vulnerabilities, accelerates response, and builds a resilient security culture.
Editor's note: This article was updated on September 17, 2025.