What Is Identity-First Security? (Definition, Benefits, and Implementation)
Identity-first security puts identities—human and machine—at the center of protection. Instead of trusting the network perimeter, it verifies every login and session, limits privileges, and detects identity misuse fast (spraying, token theft, MFA fatigue) with strong controls and ITDR.
Security used to be built around a clear perimeter: office networks, firewalls, and “inside vs. outside.” That perimeter has blurred. Zero Trust frameworks describe the shift away from static network boundaries and toward focusing on users, assets, and resources—with no implicit trust based solely on location. (NIST)
Identity-First Security is the practical answer to that shift.
Identity-First Security (Definition)
Identity-First Security is a cybersecurity approach that treats identity as the primary control plane—verifying each access request, enforcing least privilege, and continuously monitoring identity behavior across users, devices, apps, and workloads (including non-human identities). It’s a natural extension of Zero Trust, where identity becomes the most reliable way to control access in modern environments. (Microsoft Learn)
Why Identity-First Security Matters Now
Most breaches don’t start with “Hollywood hacking.” They start with credential abuse, phishing attacks, session theft, or access misconfigurations — and often escalate into account takeover when stolen credentials get reused across apps. Verizon’s 2025 DBIR key findings highlight that credential abuse and social actions like phishing are major factors in breaches, and show how infostealer logs frequently include corporate logins—often from unmanaged devices.
Many identity compromises still begin with human actions: clicking, entering credentials, or approving a malicious prompt. That’s why Identity-First Security works best when it’s reinforced with security awareness training and realistic phishing simulations that strengthen everyday decision-making.
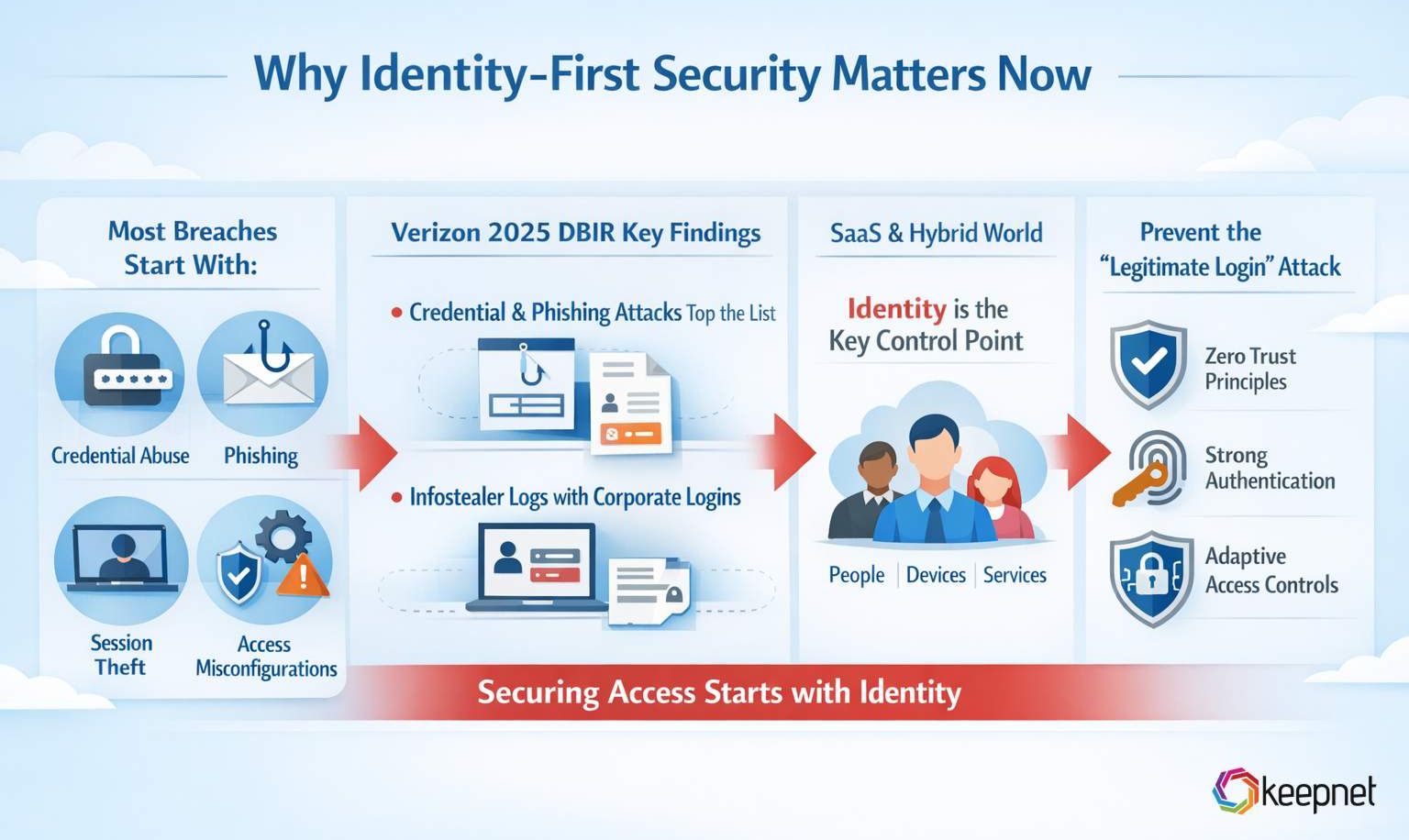
In a SaaS + hybrid world, identity becomes the common denominator. Microsoft’s Zero Trust guidance explicitly calls identities (people, services, devices) the powerful, flexible way to control access to resources.
Identity-First Security is about preventing the “legitimate login” attack.
Identity-First Security vs. Zero Trust vs. IAM (Quick Clarity)
Identity-First Security is the security strategy that says: “IAM isn’t just IT plumbing — it’s the front line.” In practice, that also means reinforcing IAM controls with security awareness training and ongoing simulations, because most identity compromise begins with social engineering — not technical exploits.
Identity-First Security vs. IAM
- IAM (Identity & Access Management) is the tooling and processes: SSO, MFA, provisioning, access policies.
- Identity-First Security is the security strategy that says: “IAM isn’t just IT plumbing—it’s the front line.”
Identity-First Security vs. Zero Trust
- Zero Trust is the broader security model and architecture (multiple pillars).
- CISA’s Zero Trust Maturity Model structures Zero Trust into five pillars, including Identity. (CISA)
- Identity-First Security is the operating stance: treat identity as the starting point for every control decision.
Identity-First Security vs. “Identity-Centric / Identity-Based / Identity-Driven Security”
These are common keyword variations. In practice, they all refer to the same idea:
- Identity is the perimeter
- access decisions must be verified, contextual, and continuously evaluated
The Core Principles of Identity-First Security
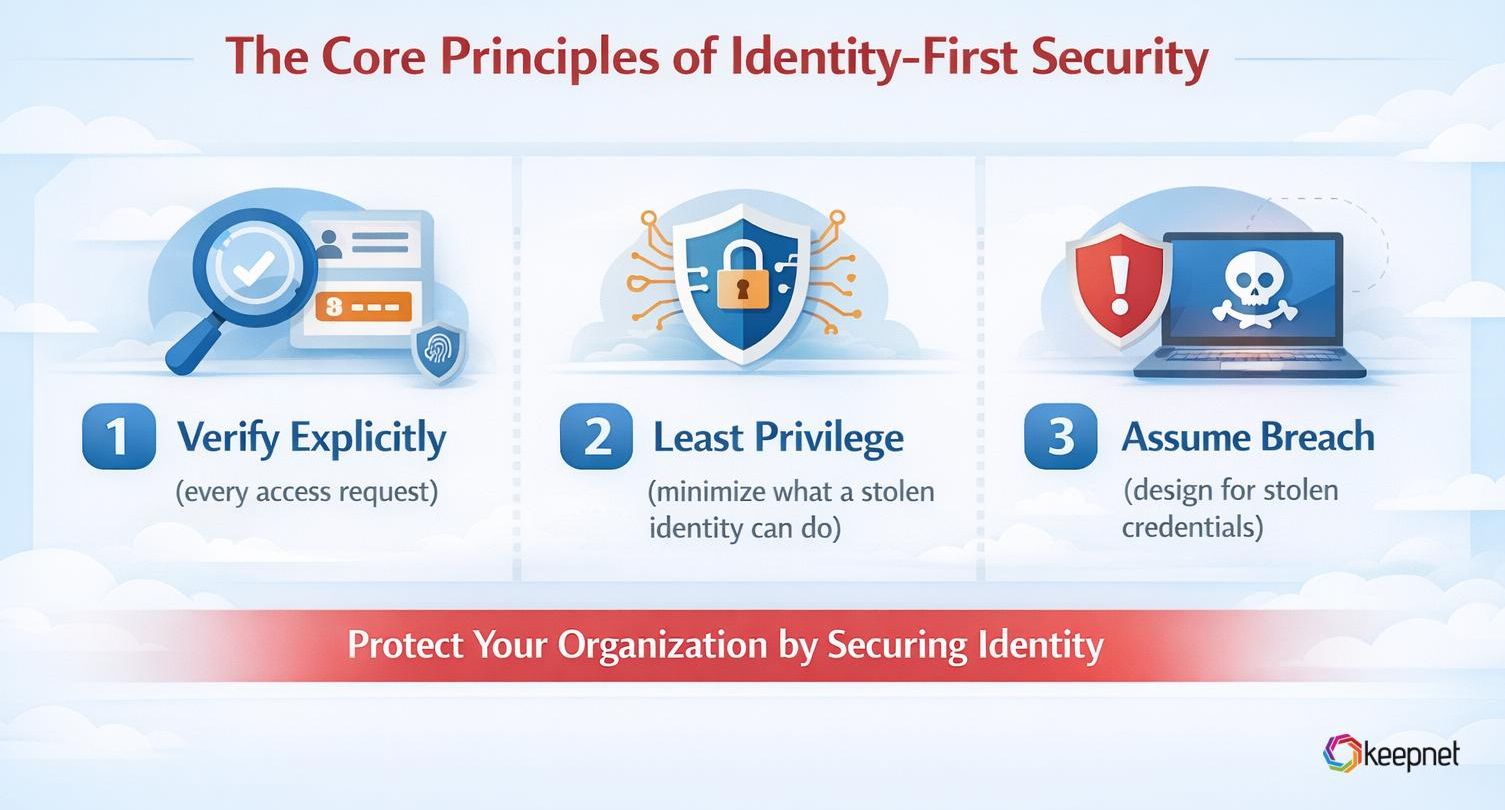
1) Verify explicitly (every access request)
Before an identity accesses a resource, verify authentication strength, device posture, and whether the behavior is typical for that identity — especially against modern threats like MFA fatigue attacks and MFA phishing.
2) Least privilege (minimize what a stolen identity can do)
Identity-first programs aggressively reduce standing admin access, broad entitlements, stale accounts, shared credentials, and long-lived secrets — and they reinforce these controls with role-based security awareness training and consistent testing through a phishing simulator especially for admins and high-risk roles.
3) Assume breach (design for stolen credentials)
NIST’s Zero Trust framing assumes there is no implicit trust for user accounts or assets based on network location alone.
So identity-first security expects some accounts will be targeted and builds fast containment: revoke sessions, reset keys, re-check device posture.
What “Identity” Includes (Human + Non-Human)
An identity-first program covers:
Human identities
Employees, contractors, vendors, partners, admins.
Non-human identities (the silent risk)
Service accounts, workloads, API keys, CI/CD tokens, OAuth apps, bots, RPA accounts. These often have:
- high privileges
- weak rotation
- low visibility
Identity-first security treats these identities as first-class citizens: discover, govern, monitor, and rotate.
The Identity-First Security Stack (What You Actually Build)
Think of it as five layers:
Layer 1: Strong authentication (prefer phishing-resistant)
CISA encourages organizations to implement phishing-resistant MFA as part of Zero Trust adoption.
Identity-first security prioritizes phishing-resistant methods for privileged access first (admins, finance, HR, security), then expands.
Layer 2: Central policy enforcement (SSO + conditional access)
Create consistent access decisions using:
- risk-based policies
- device compliance signals
- geo/time restrictions
- step-up authentication
Layer 3: Privileged Access Management (PAM)
- no permanent admin
- just-in-time elevation
- approvals for sensitive actions
- strong logging
Layer 4: Identity Governance (IGA)
automated joiner/mover/leaver
access reviews
entitlement cleanup
separation of duties (SoD)
Layer 5: ITDR (Identity Threat Detection & Response)
ITDR exists because identity attacks are now constant. Microsoft defines ITDR as an emerging focus area designed to help prevent, detect, and respond to identity-related threats. Microsoft
Practical ITDR outcomes:
- detect password spraying & impossible travel
- flag abnormal token use/session anomalies
- stop suspicious MFA enrollment changes
- disrupt lateral movement that relies on identity abuse
Common Identity Attacks (and How Identity-First Stops Them)
Password spraying
Identity-first controls:
- conditional access/risk policies
- phishing-resistant MFA
- lockout/throttling + anomaly detection
- ITDR alerts on “many users, few passwords”
MFA fatigue and social engineering
Identity-first controls:
- phishing-resistant MFA for critical users CISA
- number matching / proof-of-presence where applicable
- user coaching + fast reporting paths (security culture)
Token theft / session hijacking
Identity-first controls:
- short session lifetimes for sensitive apps
- device binding / compliant device requirements
- continuous evaluation and rapid session revocation
Non-human identity abuse (API keys, service principals)
Identity-first controls:
- inventory + ownership
- rotation + vaulting
- least privilege scopes
- anomaly detection on unusual use patterns
How to Implement Identity-First Security (A Practical Roadmap)
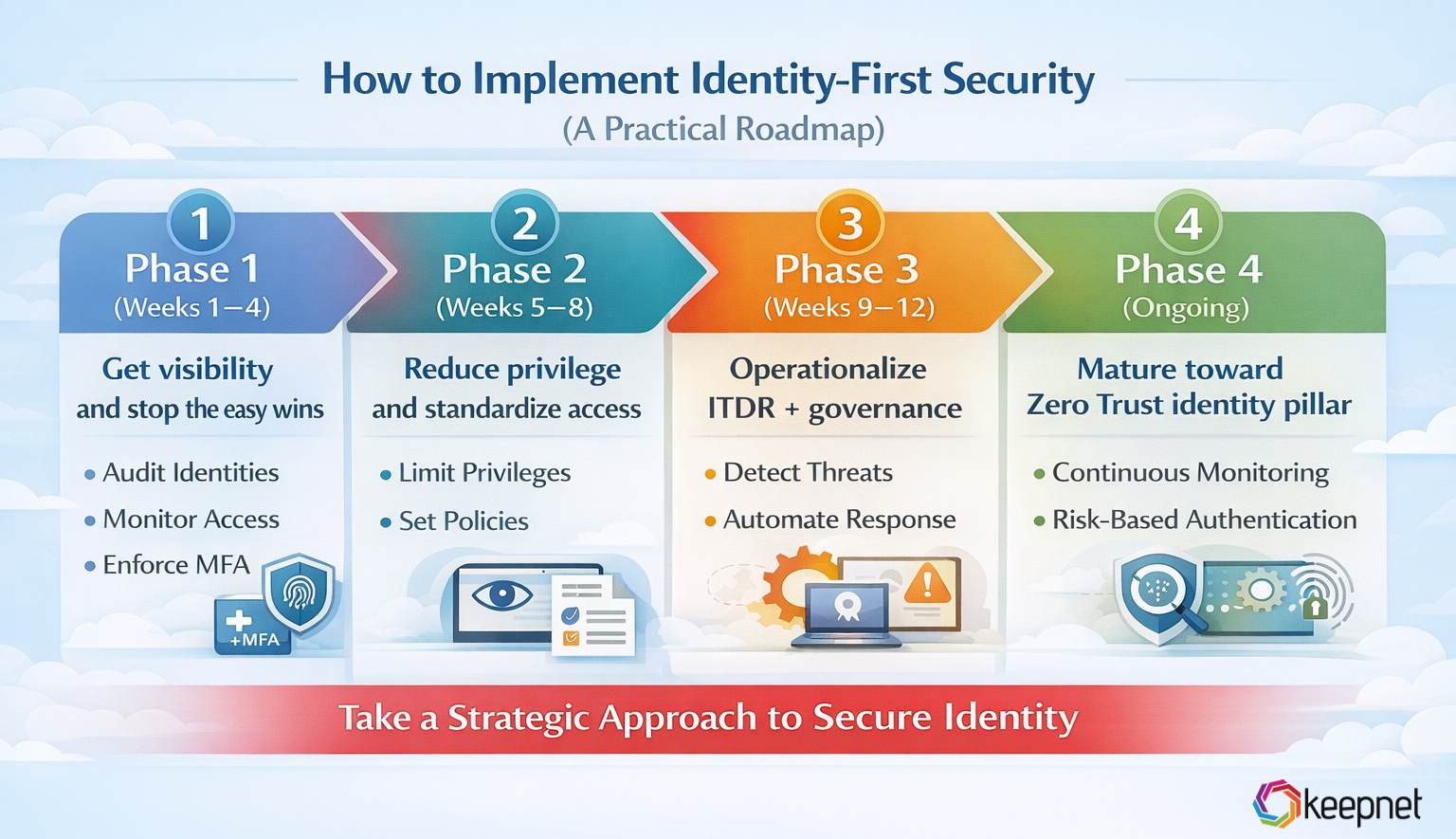
Phase 1 (Weeks 1–4): Get visibility and stop the easy wins
- Consolidate your IdP and inventory identities
- Identify privileged accounts and lock down admin paths
- Turn on logging for authentication, access, and policy decisions
- Start phishing-resistant MFA for admins and security leaders
Phase 2 (Weeks 5–8): Reduce privilege and standardize access
- Replace standing admin with JIT elevation
- Enforce SSO + conditional access on top business apps
- Clean stale accounts, shared accounts, and risky app consents
Phase 3 (Weeks 9–12): Operationalize ITDR + governance
- Deploy ITDR detections and response playbooks
- Run quarterly access reviews
- Add non-human identity governance (owners, rotation SLAs)
Phase 4 (Ongoing): Mature toward Zero Trust identity pillar
Use CISA’s Zero Trust Maturity Model as your “what good looks like” reference: identity is one of the five pillars and has maturity stages to guide progress.
KPIs That Prove Identity-First Security Works
Avoid vanity metrics (“we enabled MFA”). Use measurable outcomes:
- Phishing-resistant MFA coverage (admins first) CISA
- Privileged access exposure (standing admin count, JIT adoption)
- Time to revoke sessions after suspected compromise
- Password spraying detection time and block rate
- Stale identity cleanup rate (inactive accounts removed)
- Non-human identity coverage (inventory %, rotation SLA compliance)
- Credential leak exposure (corporate logins on unmanaged devices, infostealer indicators)
Common Mistakes (Why Identity Programs Fail)
- Treating MFA as “done” (without phishing resistance for high-risk roles)
- Ignoring non-human identities (keys and service accounts become the real perimeter)
- No entitlement hygiene (privilege sprawl becomes permanent)
- Weak offboarding (accounts linger and get reused)
- Limited logging (you can’t detect what you can’t see)
- Policies that block productivity (users work around them)
Conclusion: Identity-First Security Works Best When Human Risk Is Managed, Not Assumed
Identity-first security is strongest when it combines technical guardrails with measurable behavior change — because many identity compromises still begin with human actions: entering credentials, approving a prompt, or trusting a convincing request. Keepnet’s "Human Risk Management Platform" brings this human layer into the identity-first strategy by unifying "Security Awareness Training" and a "Phishing Simulator" in one approach — helping organizations reduce the behavior-driven risk behind account takeover, password spraying, MFA fatigue, and impersonation.