What Is Mobile Security: Threats and Components
Discover the essentials of mobile security, including key mobile security components like data encryption and access control. Learn about common mobile security threats such as ransomware and phishing, and explore best practices to protect your devices effectively.
Mobile devices are at the center of modern communication and productivity, with their usage growing at an unprecedented rate. With over 8.65 billion mobile connections globally, the average person owns more than one mobile device. This highlights how integral these devices have become to daily life, both personally and professionally.
However, as mobile usage grows, so do the threats. From protecting sensitive business data to combating malware and phishing, mobile security has become a critical safeguard in our digital age.
In this blog, we’ll explore what mobile security is, why it matters, key mobile security components, common mobile security threats, and the best ways to protect your devices.
What Is Mobile Security?
Mobile security refers to the protection of smartphones, tablets, and other portable devices from threats that can compromise data, functionality, or user privacy. As mobile devices become central to both personal and business life, mobile device security has become critical to guard against malware, unauthorized access, data leaks, and more. This includes securing operating systems, apps, network connections, and user behaviors.
Key aspects include mobile network security, data encryption, app permission control, and remote wipe features. Whether you’re dealing with security in mobile computing or exploring mobile security solutions, it’s essential to stay ahead of mobile security threats. Understanding both the risks and methods of mobile security threats and prevention helps protect sensitive information. For visual learners, a mobile device security diagram can help illustrate how various layers of defense work together to secure mobile security devices in today’s digital world.
With increasing mobile security threats such as phishing, ransomware, and spyware, the importance of robust mobile security components cannot be overstated.
Why is Mobile Security Important
In 2025, mobile devices have become essential tools for communication, banking, work, and entertainment. With this convenience comes serious risk. Mobile security is vital because smartphones and tablets store sensitive personal and business data, making them attractive targets for cybercriminals. From banking details to confidential work files, these devices carry information that, if compromised, can lead to identity theft, data breaches, and financial losses.
Mobile device security protects against a wide range of threats, including phishing, malware, and unauthorized access. Unlike traditional computers, mobile devices often connect to public Wi-Fi and untrusted networks, increasing the risk of a mobile network threat. That’s why strong mobile network security is crucial. Moreover, mobile devices are more likely to be lost or stolen, making features like remote wipe, encryption, and biometric access essential parts of a solid mobile security solution.
Understanding mobile device security threats and prevention strategies helps users and organizations protect against attacks like spyware, data interception, and fake apps. A well-structured mobile device security diagram can illustrate how different layers of defense work together—covering the operating system, network, apps, and user behavior. Businesses especially need robust mobile security management systems to enforce policies and monitor for unusual activity across all mobile security devices.
With rising smartphone security threats and mobile device security risks, the benefits of mobile security are clear: it ensures compliance, protects customer trust, and reduces costly incidents. As part of broader cyber security for mobile devices, adopting modern mobile security solutions is no longer optional. Whether you’re an individual or a business, protecting mobile devices is a critical step toward staying safe in the ever-evolving landscape of mobile cyber security.

As mobile devices manage tasks like online banking, business operations, and personal storage, they are lucrative targets for cybercriminals. This makes it imperative to implement robust mobile security measures to protect critical information and prevent disruptions.
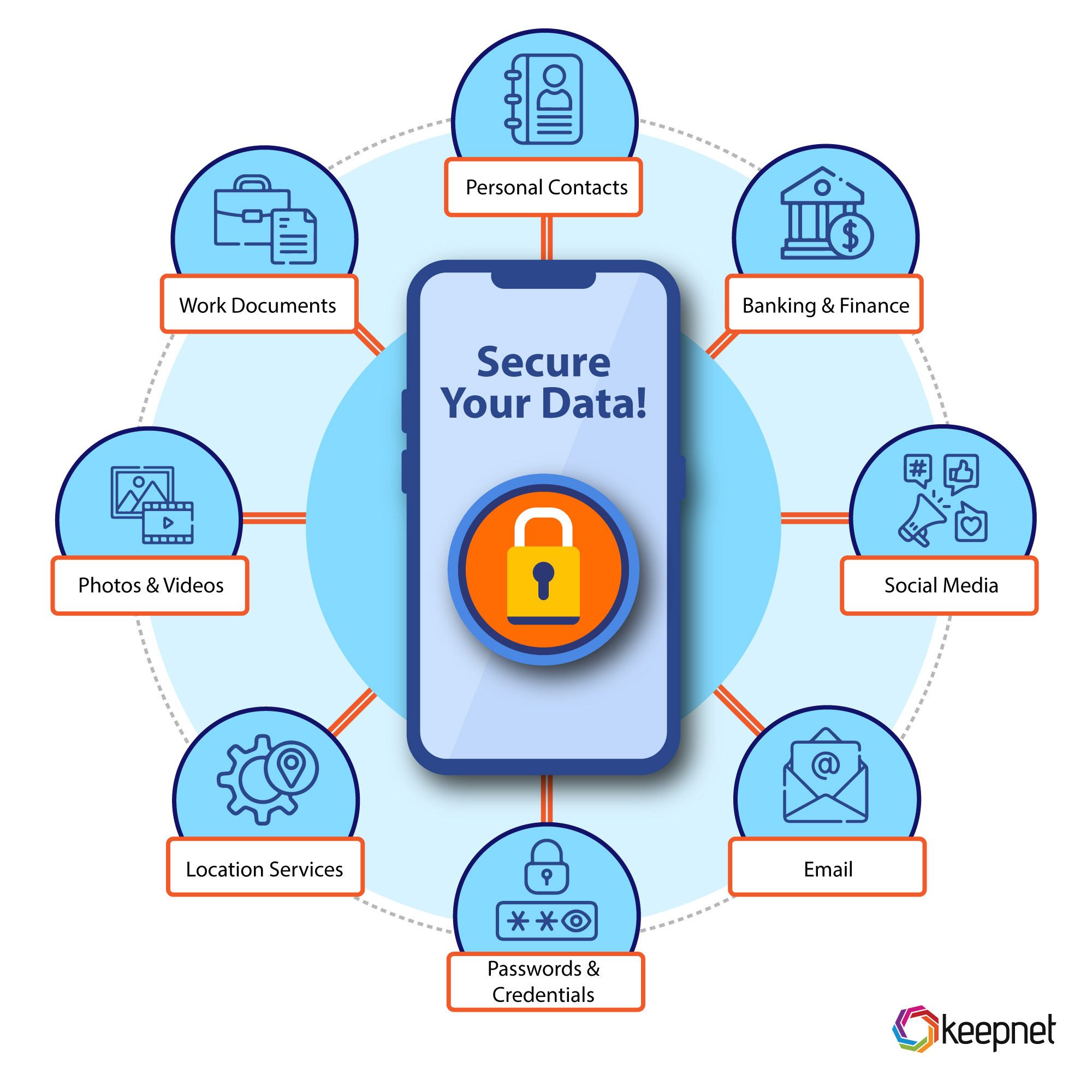
How Does Mobile Device Security Work?
Mobile device security works through multiple protective layers designed to safeguard smartphones, tablets, and other mobile security devices from both internal and external threats. Core components include data encryption, which protects sensitive data during storage and transfer—especially important for defending against mobile network threats and mobile device attacks. These tools are essential for maintaining security in mobile computing, where constant internet connectivity creates new vulnerabilities.
Another key element is strong authentication, such as passwords, PINs, and biometrics, which help secure mobile devices and reduce mobile device security risks. Organizations often use mobile security management tools or a centralized mobile security platform to enforce policies and monitor access. Keeping devices up to date is equally important, regular software updates and patching are critical in preventing smartphone security threats and closing gaps before attackers can exploit them.
To further protect against mobile security threats, especially social engineering, many mobile security solutions come with phishing prevention tools. These help users recognize suspicious links and fake websites, preventing common smartphone security risks. Visual tools like a mobile device security diagram can illustrate how each layer—from the app level to the network—works together for stronger protection.
As mobile cyber security continues to evolve, understanding how to implement and maintain effective mobile device security solutions is vital. Whether you’re comparing mobile security vs computer security, or simply trying to prevent mobile security issues, the benefits of mobile security are clear: reduced risk, better data protection, and greater peace of mind when protecting mobile devices in a hyper-connected world.

These measures help organizations and individuals proactively combat mobile security threats and safeguard their devices.
What Are the Key Components of Mobile Security?
Securing mobile devices in today’s threat landscape requires a layered approach, combining technology, best practices, and user awareness. At the heart of mobile security are several key components designed to defend against a wide range of mobile security threats and prevention challenges. These components are especially important as mobile device attacks, mobile network threats, and smartphone security risks continue to rise across both personal and business environments. Let’s explore how the essential elements of mobile device security work together to protect against modern risks.
1. Data Encryption
Encryption is a foundational pillar of mobile device security. It protects sensitive data by transforming it into unreadable code during both storage and transmission. This prevents unauthorized access, even if mobile security devices are compromised. Especially within mobile network security, end-to-end encryption is critical to shielding private messages, financial transactions, and business communications from prying eyes.
2. Authentication and Access Control
Strong authentication is another must-have for secure mobile devices. Methods such as biometrics, passwords, and multi-factor authentication reduce mobile device security risks by ensuring only authorized users can access the device or sensitive applications. Role-based access control is also commonly used in enterprise mobile security management to further limit access based on job roles and permissions.
3. Secure App Development and Monitoring
One of the lesser-known but equally vital components of mobile security in cyber security is developing apps with security in mind. This means writing secure code, using secure APIs, and running regular security tests to reduce vulnerabilities. Post-launch, real-time monitoring (like Flutter monitoring) helps identify unusual behavior—an important defense against mobile threats. Developers and organizations alike benefit from using reliable mobile security platforms that support mobile device security solutions from development to deployment.
4. Regular Updates and Patch Management
Outdated software is a common gateway for cybercriminals. Routine updates and patching help fix vulnerabilities before they can be exploited. Keeping both operating systems and apps current is essential in cyber security for mobile devices, especially when defending against fast-moving smartphone security threats and emerging malware targeting mobile environments.
5. Email Security and Phishing Prevention
Email is one of the most abused channels in mobile cyber security. Tools like phishing simulations train users to detect malicious links and fake emails, reducing the risk of falling for scams—a common mobile phone security issue. Protecting against phishing is also critical for security mobile devices, especially those used by remote teams or employees frequently working on the go.
Understanding the benefits of mobile security means recognizing how each component contributes to a holistic strategy. From mobile security solutions and mobile security platforms to end-user education and protecting mobile devices, building a strong defense is no longer optional. Whether you’re managing BYOD environments or seeking enterprise-level controls, these components offer scalable answers to address mobile security issues. And when comparing mobile security vs computer security, remember that mobile environments face unique risks that demand specialized attention—and proactive protection.
What Are the Common Mobile Security Threats?
Cybercriminals use a variety of sophisticated tactics to target mobile devices, exploiting vulnerabilities to steal data, disrupt operations, and gain unauthorized access. Understanding these mobile security threats is critical for mitigating risks. Here are some of the most prevalent threats:

Network Threats
Unsecured public Wi-Fi networks are hotspots for cybercriminals. Attackers can intercept data transmitted over these networks using techniques like man-in-the-middle (MITM) attacks. Additionally, malicious hotspots may be set up to mimic legitimate networks, tricking users into connecting and unknowingly exposing their sensitive information.
Weak Passwords
Easily guessed, reused, or default passwords remain a significant vulnerability. Weak passwords allow attackers to exploit brute-force techniques or credential-stuffing attacks, gaining unauthorized access to accounts and devices. Using password managers to generate and store strong passwords can reduce this risk.
Ransomware
Ransomware is a growing concern, with attackers locking users out of their devices or encrypting their data until a ransom is paid. These attacks often exploit vulnerabilities in outdated software or rely on phishing emails to gain a foothold. Beyond financial losses, ransomware can lead to data breaches and severe operational disruptions.
Spyware
Spyware is designed to monitor and collect information from a device without the user’s knowledge. It can log keystrokes, track locations, or access sensitive data like login credentials and emails, often leading to privacy violations and data theft. Some spyware even masquerades as legitimate apps to avoid detection.
Malware
Malware, including viruses, Trojans, and worms, targets mobile devices to disrupt their functionality, steal sensitive data, or surveil user activities. Mobile-specific malware often spreads through malicious apps, email attachments, or compromised websites, posing a constant threat to users.
Data Leakage
Data leakage occurs when sensitive information is unintentionally shared or exposed. This can happen due to insecure apps, poorly configured cloud storage, or users unknowingly granting excessive permissions to applications. The consequences of data leakage can include compliance violations, regulatory penalties, and reputational harm.
These mobile security threats highlight the importance of adopting proactive measures, such as encryption, regular updates, and phishing training, to protect devices from ever-evolving risks.
What Are the Best Practices for Mobile Security?
Many businesses choose to outsource software development to top-rated companies to leverage specialized expertise and ensure robust security measures from the outset. Whether you build in-house or with a partner, the key is the same: design security in from day one—use a secure SDLC, threat modeling, vetted libraries, and continuous testing. On the device and user side, the following practices close the loop and meaningfully reduce risk:
- Use strong, unique passwords and enable multi-factor authentication (MFA): Pair a password manager with device-level biometrics and enforce MFA for all high-risk actions.
- Regularly update device software and applications: Turn on automatic OS/app updates, retire unsupported devices, and patch quickly to close known vulnerabilities.
- Encrypt sensitive data stored on devices: Enforce full-disk encryption and, where possible, app-level encryption with keys stored in secure hardware (e.g., Secure Enclave/TPM).
- Avoid connecting to unsecured public Wi-Fi for sensitive tasks: Prefer mobile data or trusted networks; if public Wi-Fi is unavoidable, use a corporate VPN and disable auto-join.
- Conduct Security Awareness Training to educate users about threats like phishing: Cover smishing, vishing, QR code risks, malicious apps, and safe browsing; encourage quick reporting.
Leverage platforms like Keepnet Extended Human Risk Management Platform to monitor and mitigate potential risks: Run targeted simulations (e.g., voice/SMS/QR/MFA-fatigue), deliver just-in-time training, and track behavioral metrics to reduce human-driven incidents.
Bonus safeguards to round out your program:
- Use MDM/MAM controls: Enforce passcodes, containerize corporate data, and block rooted/jailbroken devices.
- Limit app permissions and adopt least privilege: Review and revoke unnecessary camera, location, and microphone access.
- Plan for loss/theft: Enable remote lock/wipe and require automatic device lock after short idle periods.
- Blending secure development (from the very start) with disciplined user and device controls gives you defense-in-depth for mobile—without sacrificing usability.
Protect Your Mobile Device from Security Threats with Keepnet Human Risk Management
As mobile security threats continue to evolve, protecting your mobile security devices requires more than just antivirus software. Keepnet’s Human Risk Management Platform offers robust mobile security solutions designed to defend against phishing, data breaches, and other mobile device security threats. With tools like the Phishing Simulator and Security Awareness Education, users are trained to recognize phishing attempts, suspicious email attachments, and emerging smartphone security risks—a vital part of any modern mobile security platform.
By leveraging Keepnet’s technology, organizations can address key areas of mobile security in cyber security, including mobile device security, mobile network security, and user behavior. Whether you’re securing employee devices or managing company-owned hardware, Keepnet helps you secure mobile devices, reduce mobile device security risks, and empower your workforce with the knowledge to stop attacks before they succeed. Stay proactive, stay informed, and ensure your team is ready to face the latest mobile threats with Keepnet.
Editor's note: This article was updated on 15 August 2025.