What Is Physical Security? Definition, Examples & Best Practices (2026)
Physical security is crucial for safeguarding an organization’s assets, employees, and sensitive information. This guide covers why physical security matters, highlights key components like access control and surveillance, and provides examples and best practices. Equip your organization to handle physical threats with robust security strategies.
While often overshadowed by digital security, physical security is a critical pillar of any organization’s overall security framework. It protects both people and assets from physical threats, serving as the first line of defense against breaches that can lead to data theft, operational disruptions, and reputational harm. Whether for a small business or a large enterprise, a robust physical security strategy is essential to maintaining a secure and resilient organization.
For instance, the 2011 PlayStation Network outage resulted from a security breach that compromised the personal details of approximately 77 million accounts. This incident caused significant downtime and reputational damage for Sony. More recently, in 2023, a vulnerability in Progress Software's MOVEit file transfer application was exploited, impacting over 2,500 organizations, with more than 80% based in the U.S. These cases highlight the dire consequences of security lapses and emphasize the importance of addressing vulnerabilities holistically.
In this blog, we’ll explore the critical components of physical security, its role in an organization’s overall security strategy, and best practices to ensure your organization is protected against both physical and digital threats.
What is Physical Security?
Physical security is the practice of protecting an organization’s people, property, and data from real‑world threats such as unauthorized access, theft, natural disasters, and sabotage. While cybersecurity often dominates conversations about risk, physical security is the first line of defense against breaches that can compromise digital and operational assets.
In simple terms, physical security refers to implementing barriers—both human and technological—to prevent unauthorized access to sensitive systems. This includes access control systems, security guards, video surveillance (CCTV), biometric authentication, alarm systems, fire suppression technologies, and environmental monitoring for hazards like flooding or power loss.
For organizations that handle sensitive data or critical infrastructure, physical security goes beyond locked doors. It involves a layered defense strategy known as defense in depth, where each layer (perimeter, facility, server room, and endpoint devices) adds a new level of protection. For example, a company may use smart card readers at entrances, reinforced server cages in data centers, and motion sensors to detect unauthorized activity.
Today, integrating physical security with cybersecurity is essential. A hacker who gains physical access to a server room could bypass even the most advanced firewalls. Similarly, a stolen laptop without strong physical protections can be a gateway for cyberattacks. That’s why many enterprises now adopt converged security programs — combining cybersecurity awareness training, video analytics, and physical access controls into a unified risk management framework.
From a compliance standpoint, frameworks such as ISO 27001, NIST SP 800‑53, and PCI DSS mandate robust physical security measures, highlighting their critical role in safeguarding confidential information. Without proper physical controls, even the best cybersecurity program can fail.
In essence, physical security isn’t just about preventing break‑ins — it’s about ensuring business continuity, protecting employees, and safeguarding digital and physical assets from a wide range of evolving threats.
Why Physical Security is Important
Physical security is the first line of defense against threats to an organization’s critical assets. While cyber defenses guard against online attacks, physical security protects employees, equipment, data, and facilities from theft, unauthorized access, and natural disasters. Without it, the impact on an organization can be catastrophic, leading to data breaches, financial losses, and even life-threatening situations. By implementing robust physical security measures, businesses ensure a safe environment for employees and visitors while keeping crucial data and assets secure.
Key Components of Physical Security

The three key components of physical security are access control, surveillance, and testing/monitoring. Let’s take a closer look at each:
- Access Control: Access control restricts who can enter the building or sensitive areas. This may include measures like keycards, biometric systems, or security personnel who check IDs. Effective access control reduces physical security risks by keeping unauthorized individuals out of sensitive areas.
- Surveillance: Surveillance systems, including CCTV cameras and motion sensors, are essential for monitoring and recording activities in and around facilities. Not only does this help deter potential threats, but it also provides valuable footage for investigations if a security breach occurs.
- Testing and Monitoring: Regularly testing security systems ensures they are functional and effective. For example, conducting fire drills, testing alarm systems, and assessing emergency response protocols all fall under this component. Testing and monitoring help maintain the integrity of security measures by ensuring they work as intended when needed.
Each of these elements plays a critical role in creating a secure environment by providing a layered approach to preventing, detecting, and responding to physical security threats.
How to Measure Physical Security?
Measuring physical security involves evaluating the effectiveness of security controls, response protocols, and risk management strategies. Here are a few metrics to gauge the robustness of your physical security measures:
- Access Incident Reports: Tracking and analyzing instances of unauthorized access attempts can reveal weaknesses in access control systems.
- Response Time: Measure the speed at which security personnel respond to alarms or breaches. Shorter response times can significantly reduce the impact of an incident.
- Employee Awareness: Conduct surveys or quizzes to determine employees’ knowledge of security procedures. A well-informed staff can act as an additional security layer.
- Surveillance Coverage: Ensure all critical areas are adequately covered by surveillance, and test cameras regularly to confirm they’re operational.
By measuring these factors, organizations can identify gaps and make informed decisions to strengthen their physical security controls.
Common Physical Security Risks and Threats
Physical security faces an evolving set of risks and threats, often arising from both external and internal sources. Here are some of the most common physical security risks businesses face:
- Theft and Vandalism: These are common issues, especially for businesses with valuable equipment or confidential information on-site. Thieves may target data centers, while vandals can damage property, interrupting operations.
- Unauthorized Access: Individuals without permission might attempt to access sensitive areas within the building, potentially causing harm or data breaches.
- Natural Disasters: Fire, floods, earthquakes, and other natural events pose significant risks to physical assets and infrastructure.
- Terrorism and Civil Unrest: In areas where terrorism or political unrest is a concern, security threats may include bomb threats, protests, or riots, all of which can compromise safety.
Understanding these physical security threats helps organizations build a stronger security strategy that mitigates risks and protects critical assets.
What Are the Common Examples of Physical Security?
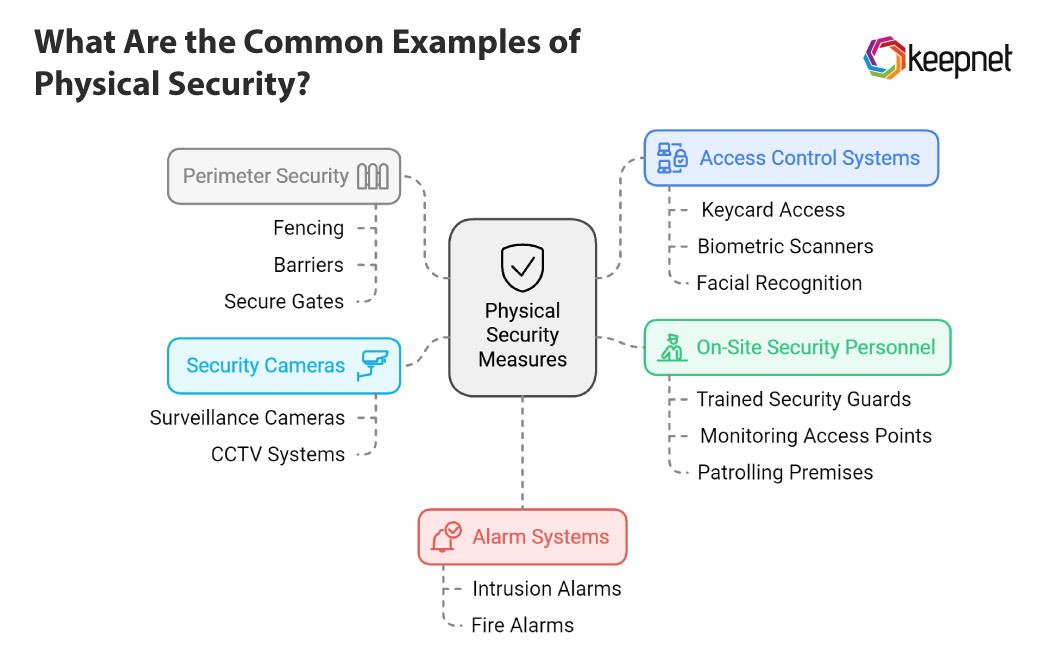
A variety of examples of physical security can effectively safeguard different environments. Here are some of the most commonly used physical security measures:
- Perimeter Security: Fencing, barriers, and secure gates around a facility’s perimeter help prevent unauthorized access. This is particularly common for high-security facilities.
- Access Control Systems: Keycard access, biometric scanners, and facial recognition systems limit entry to authorized individuals only. These systems can log entry and exit times, providing a reliable record of personnel movements.
- Security Cameras: Surveillance cameras and CCTV systems monitor activity in real-time, deterring potential threats and capturing evidence if a breach occurs.
- Alarm Systems: Intrusion and fire alarms alert security personnel and emergency responders to incidents, ensuring a swift response to minimize damage.
- On-Site Security Personnel: Trained security guards provide immediate response to security incidents, monitor access points, and patrol the premises.
Implementing these types of physical security controls helps organizations to build a safe and resilient environment for employees, customers, and assets.
What Are the Physical Security Best Practices?
Building an effective physical security strategy involves adopting best practices that address potential vulnerabilities. Here are a few critical practices to consider:
- Conduct Regular Security Audits: Regular audits identify weaknesses in current physical security measures, allowing organizations to address them proactively.
- Train Employees on Security Protocols: Staff should know basic security protocols, including recognizing and reporting suspicious behavior. Training can be reinforced through security awareness training programs.
- Limit Access to Critical Areas: Only authorized personnel should have access to sensitive locations. Access restrictions reduce the risk of unauthorized entry and data breaches.
- Implement Multi-Layered Security: A combination of surveillance, access control, and monitoring provides layers of defense that make it harder for intruders to breach the system.
- Use Technology and Automation: Leveraging technologies like automated alarms, AI-driven surveillance, and biometric authentication enhances security and reduces human error.
Following these best practices ensures your organization remains resilient against evolving physical security threats, creating a safer workplace for employees and protecting critical assets.
Increase Cyber Awareness with Keepnet for Physical Security
Physical security and cybersecurity are increasingly intertwined, as physical breaches can lead to cyber incidents and vice versa. Keepnet Labs offers comprehensive solutions to raise awareness around these interconnected threats. With products like Phishing Simulators, security awareness training, and Human Risk Management Platforms, organizations can boost resilience against cyber risks.
Integrating Keepnet resources not only strengthens an organization’s cyber defenses but also educates employees on the importance of both physical and digital security, leading to a more secure workplace.
Further Reading on Security Awareness and Cybersecurity
For a deeper dive into related topics, here are some recommended articles that expand on cyber security strategies:
- 2024 QR Code Phishing Trends: In-Depth Analysis of Rising Quishing Statistics – Learn about the latest phishing tactics using QR codes and how to defend against them.
- 10 Essential Tips to Protect Yourself from Phishing Attacks – Practical tips for identifying and avoiding phishing attacks in both physical and digital environments.
- What is Spear Phishing and How to Prevent It – Explore targeted phishing strategies and methods to reduce this cyber risk.
- What is Ransomware – A deep dive into ransomware attacks, their impact, and best practices to defend against them.
- The Role of Human Error in Successful Cyber Security Breaches – Understand how human error contributes to breaches and how physical and cyber training can minimize risks.
- The Importance of Collaborative Defense – Explore how collaborative security efforts across teams can strengthen defenses against physical and cyber threats.
- Guarding the Gates: How MFA & Phishing Simulations Reinforce Digital Walls – Learn how multifactor authentication and phishing simulations can reinforce your overall security strategy.
- Email Incident Response 101 – A step-by-step guide on handling email-based incidents to prevent further escalation, blending digital vigilance with physical security awareness.
Editor's Note: This blog was updated on February 23, 2026.