Spear Phishing Explained: Definition, Examples, Prevention & Training (2025 Guide)
Spear phishing is more than just another cyber buzzword—it’s one of the most dangerous cyber threats today. Unlike generic phishing attacks that target thousands at once, spear phishing focuses on specific individuals or organizations, making it harder to detect and more devastating when successful.
Spear phishing is a highly targeted phishing attempt where attackers send personalized, deceptive messages, usually email, to specific people or organizations to steal credentials, money, or data. Unlike generic phishing, it uses victim context (names, roles, projects) to appear legitimate and bypass filters and human caution.
Quick differences at a glance (bullets for skimmers & snippets):
- Target: specific people or organizations (not mass lists)
- Personalization: high—name, role, project, vendor details
- Success driver: trust, not volume
- Risk level: severe business impact if a single email succeeds
People often search variants like spear-phishing, spearphishing, spear phising, spear pishing, spear-phising. The concept is the same: targeted, convincing attacks that exploit trust.
By March 2025, AI-powered spear phishing agents had become 24% more effective at tricking users than elite human red team experts.
Why Spear Phishing is More Dangerous Than Broad Phishing
Personalization: Messages often appear to come from a trusted source, such as a boss, colleague, or vendor.
Higher success rate: Because the message feels authentic, employees are more likely to click, reply, or share sensitive information.
Business impact: A single spear phishing email can lead to stolen credentials, wire fraud, or ransomware infections.
Spear Phishing vs. Phishing – The Key Difference
When people ask, “What is the primary difference between phishing and spear phishing?”, the answer comes down to scope, intent, and precision. Both are types of social engineering attacks, but they operate very differently.
Phishing: A Wide Net Attack
- Definition: Phishing is a general attack targeting many users at once.
- Example: An attacker sends thousands of emails pretending to be a bank, hoping a few people will click a malicious link.
Spear Phishing: A Targeted Strike
- Definition: Spear phishing is a targeted attack aimed at specific individuals or organizations, often using personal details gathered from LinkedIn, social media, or previous data breaches.
- Example: An employee receives an email from what looks like their CEO requesting an urgent wire transfer.
| Aspect | Phishing | Spear Phishing |
|---|---|---|
| Target | Large groups, often random | Specific people or organizations |
| Personalization | Generic ("Dear Customer") | High (name, role, project details) |
| Success Driver | Volume | Trust |
| Risk Level | Broad nuisance | Severe business risk |
Table 1: Key Differences Spear Phishing and Phishing at a Glance
Quiz:
Q: What is the primary difference between phishing and spear phishing?
A. Phishing is a general attack targeting many users, whereas spear phishing is a targeted attack aimed at specific individuals. ✅
B. Phishing is only email; spear phishing is only social media.
C. Spear phishing is less dangerous.
D. Phishing emails are always unknown senders.
Check our blog to understand difference between Spear Phishing and Phishing in more detail.
How Spear Phishing Attacks Work
A spear phishing attack is not a random email scam, it’s a carefully planned and executed cyber operation. Here is how it works:
1. Reconnaissance (research)
Attackers gather details (name, title, teammates, suppliers, live projects) from social media and public sources. Captures: spear phishing attack meaning, spear phishing attack definition, cyber spear phishing.
2. Impersonation (pretext)
They mimic executives, HR, IT, or vendors—tone, signature, domain lookalikes—to craft a convincing spear phishing email. Captures: spear phishing is, spear phishing refers to, what is a spear phishing.
3. Delivery (channels)
Email dominates, but messages also land via Teams/Slack/DMs—which is why searches like spear fishing cyber/spearfishing cyber attack appear.
4. Hook (deception)
“Approve this invoice,” “reset your password,” “download this file.” Urgency + authority = action. Captures: spear phishing attacks, what is cyber spear phishing.
5. Execution & breach
Credential theft, wire fraud, data exfiltration—often the start of bigger incidents.
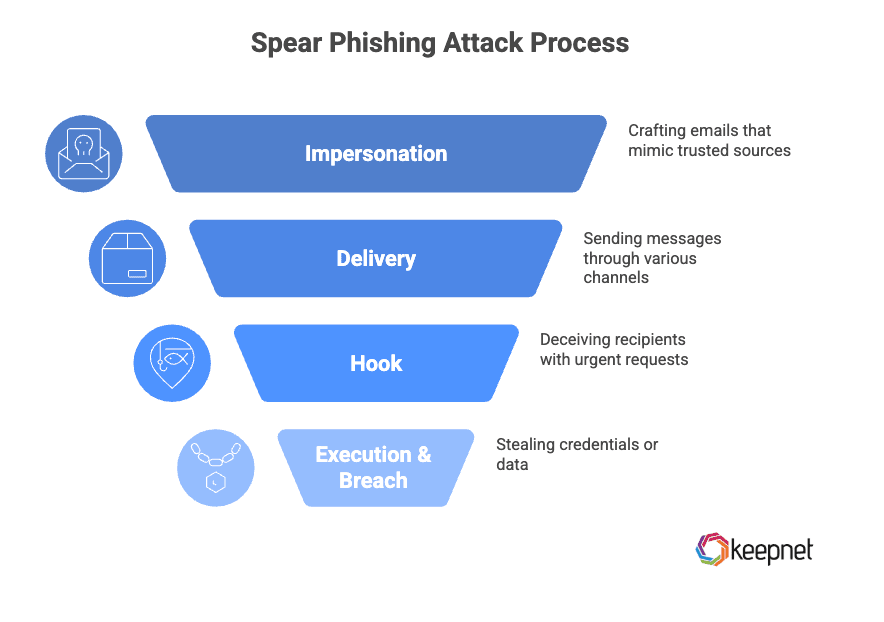
Bottom line: Spear phishing is a targeted cyber attack engineered to evade both technology and people’s guardrails.
Real-World Spear Phishing Examples
One of the best ways to understand spear phishing is to look at real-world spear phishing examples. Unlike broad phishing scams, spear phishing emails are tailored to trick a specific individual or business. Here are some of the most common types and notable cases.
1. Executive Impersonation (CEO Fraud)
Cybercriminals impersonate senior executives—like the CEO or CFO—using email domains that look legitimate. The email typically requests an urgent wire transfer or the release of confidential information.
- Example: An attacker sends a message to the finance department: “I need you to process this urgent payment before the end of the day. Do not delay.”
- Impact: Millions of dollars can be lost from a single successful attack.
2. Vendor or Supplier Fraud
Attackers impersonate a trusted vendor or partner and send an invoice with altered bank details. Since the email looks like it’s from a known supplier, employees often comply without question.
- Example: A construction company received a fake invoice from a “vendor” and wired funds to a fraudulent account.
- Impact: Businesses not only lose money but also damage relationships with real partners.
3. Employee Credential Theft
Instead of money, some attacks aim to steal login details. The spear phishing email may contain a fake login page for Microsoft 365, HR portals, or payroll systems.
- Example: A staff member gets an email saying: “Your password is expiring today. Click here to reset it.”
- Impact: Once credentials are stolen, attackers gain access to sensitive systems and data.
A Spear Phishing Example
From: Maria Ortiz <m.ortiz@payables-vend0r.com>
Subject: RE: PO-4481 | Updated bank details for December payment
Hi <FirstName>,
Our finance team completed the audit and we’re consolidating accounts.
Please send the December payment to the updated IBAN attached.
Same PO, same amount, just the new bank record effective today.
Appreciate your help,
Maria
Accounts Payable, <Trusted Vendor>
To dive deeper, check our blog on spear phishing examples.
Why Spear Phishing Is So Dangerous in 2025
Spear phishing works because it exploits trust, process, and time pressure—not because your tools are “bad.” A few realities make it uniquely risky:
- Personalization at scale: Open-source intel and breached datasets make tailored pretexts cheap to produce.
- Lookalike signals: Attackers mimic real email threads, vendors, and tone—often reusing your templates.
- Tool evasion: Well-crafted text, cloud sharing links, and legitimate infrastructure reduce detection rates.
- Human context: Finance cycles, travel, quarter-end pressure, and procurement changes create believable urgency.
- Ecosystem risk: Even if you block an email, a less-mature supplier may not; compromise can boomerang back as a trusted message from a real partner.
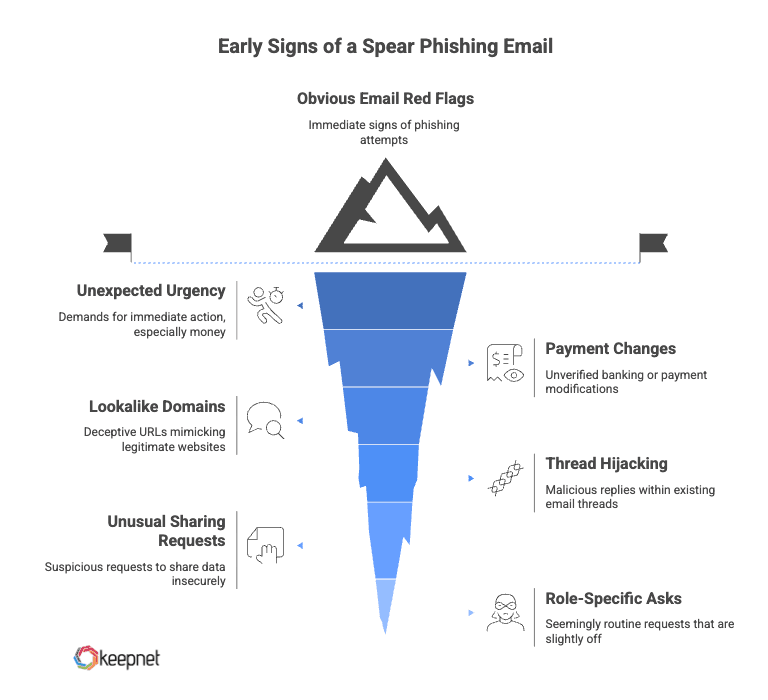
Early Warning Signs of a Spear Phishing Email
Teach employees to pause when they see:
- Unexpected urgency (especially money or credentials).
- Banking or payment changes without a formal vendor management process.
- Lookalike domains (e.g., vend0r.com vs. vendor.com).
- Thread hijacking (replying to a real conversation with a new attachment/link).
- Unusual sharing requests (“open this in your personal email” or “approve with your backup MFA”).
- Role-specific asks (AP, payroll, legal reviews) that appear routine but are slightly off.
How to Prevent Spear Phishing Attacks (A Practical Playbook)
There’s no silver bullet. The most resilient organizations align people, process, and technology—and they measure improvement.
People: Awareness That Builds Reflexes
Security awareness should move beyond annual slides. Aim for short, frequent micro-lessons tied to current threats and roles. Simulated spear phishing emails, spear vishing calls, and QR code phishing tests turn abstract advice into muscle memory. Build a security culture where phishing reporting is applauded—not punished when someone nearly clicks.
- Run role-based phishing simulations: AP, treasury, HR, executive assistants, and admins.
- Teach media-agnostic skills: spotting manipulation, verifying out-of-band, saying “no” politely.
- Publish a one-page playbook for “urgent payment or credential” requests (steps & phone numbers).
Process: Verification That Scales
Codify and enforce verification where the risk is highest.
- Payment controls: No bank-detail changes without two-party verification via known numbers.
- Access controls: Prohibit password resets via email or chat; require ticketing + voice verification.
- Vendor management: Maintain a trusted contact directory with independently validated numbers.
- Incident drills: Practice “stop-pay” procedures and mailbox compromise playbooks quarterly.
Technology: Defense-in-Depth, Tuned for Targeted Phishing
Tools matter, but they must be configured around spear-phishing realities.
- Email authentication: Enforce DMARC (ideally p=reject), SPF, and DKIM—and monitor alignment.
- Advanced detection: Use behavioral and relationship-graph analytics to flag anomalous requests.
- Browser & link protections: Safe-container or click-time analysis for unknown domains and QR redirects.
- MFA hardening: Prefer phishing-resistant factors (FIDO2/WebAuthn), not only push approvals.
- Least privilege & segmentation: Limit blast radius when an account is compromised.
- Automated reporting loop: Make “Report Phish” one click, auto-triage messages, and close the loop with reporters.
A 10-Point Spear Phishing Protection Checklist
This spear phishing protection checklist shows how to cut real risk fast: DMARC at p=reject, FIDO2/WebAuthn, vendor bank-change verification, role-based simulations, and rapid feedback loops. Focus on finance controls, mailbox rule audits, and quarterly tabletop exercises to prevent wire fraud and account takeover. Start here to convert awareness into consistent, measurable defense.
Adopt these ten actions to reduce time-to-report, cut false approvals, and protect treasury, HR, and executive workflows.
- DMARC at p=reject with ongoing monitoring.
- Click-time URL inspection + QR redirect scanning.
- FIDO2/WebAuthn for high-risk roles; disable push-only MFA.
- Role-based phishing simulations (email, voice, SMS, QR, MFA).
- Vendor bank-change verification policy (two humans, out-of-band).
- Executive assistant training + travel-scenario drills.
- AP/treasury “stop-pay fast lane” with 24/7 contacts.
- Mailbox rule audits and anomaly alerts.
- Rapid feedback to reporters (education within minutes).
- Quarterly tabletop exercises with finance, IT, and legal.
Spear Phishing Training & Awareness Programs That Actually Work
Effective phishing awareness training is continuous, contextual, and measurable. One-off courses create awareness but not behavior change. Instead:
- Blend learning formats: micro-videos, scenario-based stories, and interactive quizzes.
- Mirror real life: Use the same brands, tools, and processes your people see daily.
- Escalate difficulty: Start with clear examples; progress to subtle thread hijacks and lookalike domains.
- Cover all channels: Email, spear vishing, SMS, QR, social DMs, and MFA fatigue.
- Close the loop: After a phishing simulation, deliver instant training explaining the red flags the person missed.
- Reinforce reporting: Reward fast reporters; showcase “catch of the month.”
If you’re running a program in-house, consider a 12-month cadence: monthly phishing simulations by role, quarterly tabletop exercises, and two focused learning campaigns (e.g., “Invoice Fraud Month,” “MFA Hardening Month”). That rhythm keeps risk top-of-mind without overwhelming people.
Metrics That Matter: From Clicks to Security Culture
Leaders often over-focus on click rate. It’s useful, but incomplete. For spear-phishing resilience, track:
- Report rate: % of employees who report suspected phishing. A higher number shows healthy vigilance.
- Time-to-report (TTR): Minutes from receipt to report. Faster TTR shrinks attacker dwell time.
- High-risk role performance: AP/treasury, executive assistants, admins—the roles attackers target first.
- Repeat offender recovery: Coaching impact over time; fewer repeats means learning sticks.
- Positive behaviors: Out-of-band verification usage; policy-driven “no” responses; early challenge calls.
- Program coverage: % of workforce completing training and participating in multi-channel phishing simulations.
When you discuss progress with the board, combine these metrics into a human risk score tied to financial scenarios (e.g., “Invoice Fraud Loss Avoidance”), not just raw percentages.
Executive Playbook: 30-60-90 Days to Reduce Spear-Phishing Risk
This executive playbook lays out a practical 30–60–90 day plan to reduce spear-phishing risk without boiling the ocean. In three sprints, you’ll stabilize email authentication and reporting, harden high-risk workflows with phishing-resistant MFA, and scale role-based simulations across email, voice, SMS, and QR. Each phase ties actions to measurable outcomes—time-to-report (TTR), report rate, and high-risk role performance—so leaders can track progress against BEC/vendor fraud exposure. Use this roadmap to turn policy into practice and convert awareness into consistent, auditable defense.
Days 0–30: Stabilize.
- Turn on DMARC monitoring; set SPF/DKIM corrections in motion.
- Implement push-to-report in mail clients; stand up rapid triage.
- Launch a baseline simulation across a non-financial pretext to measure current state.
- Publish a one-page “Urgent Payments & Access Requests” verification policy.
Days 31–60: Harden.
- Pilot FIDO2/WebAuthn for finance and admins; reduce push prompts.
- Run a vendor-change tabletop with AP, procurement, and legal.
- Start role-based security awareness training for AP and executive assistants.
- Enable mailbox-rule anomaly alerts and high-risk forwarding detections.
Days 61–90: Scale.
- Expand phishing-resistant MFA to all sensitive apps.
- Launch quarterly tabletop schedules; codify “stop-pay” escalation.
- Introduce multi-channel simulations (voice, SMS, QR).
- Publish a quarterly human-risk report to the exec team with TTR, report rate, and role performance.
How to Prevent Spear Phishing Attacks With Keepnet
If you’re ready to reduce targeted phishing risk in a measurable way, align your program around three pillars: Keepnet Human Risk Management Platform to centralize analytics and orchestrate controls.
Keepnet delivers continuous, role-based Security Awareness Training plus a multi-channel Phishing Simulator—email, voice, SMS, QR, MFA fatigue—to harden human defenses
For organizations that need to show quick results and sustained improvement, connect your payment and access verification policies to human-risk metrics—report rate, time-to-report, and high-risk role performance—so leaders see progress in terms of avoided losses and reduced dwell time.
Explore how Keepnet’s approach brings these pieces together with multi-channel simulations, instant coaching, localized content, and risk analytics that make it easy to brief the board.