Top Cybersecurity Trends for 2026: AI Threats, Quantum Risks, and Zero-Trust
Learn about the top cybersecurity trends for 2026, from AI-driven threats to quantum computing challenges. Discover actionable strategies to secure your organization.
Cybersecurity Ventures estimates global cybercrime costs will reach $10.5 trillion annually by 2025. This escalating threat highlights the need for organizations to stay ahead of increasingly sophisticated attacks. Cybercriminals are using AI-driven phishing, preparing for the disruptive potential of quantum computing, and exploiting gaps in outdated security frameworks.
In this blog, we’ll explore the top cybersecurity trends for 2025, the risks they pose to your organization, and actionable strategies to defend against them.
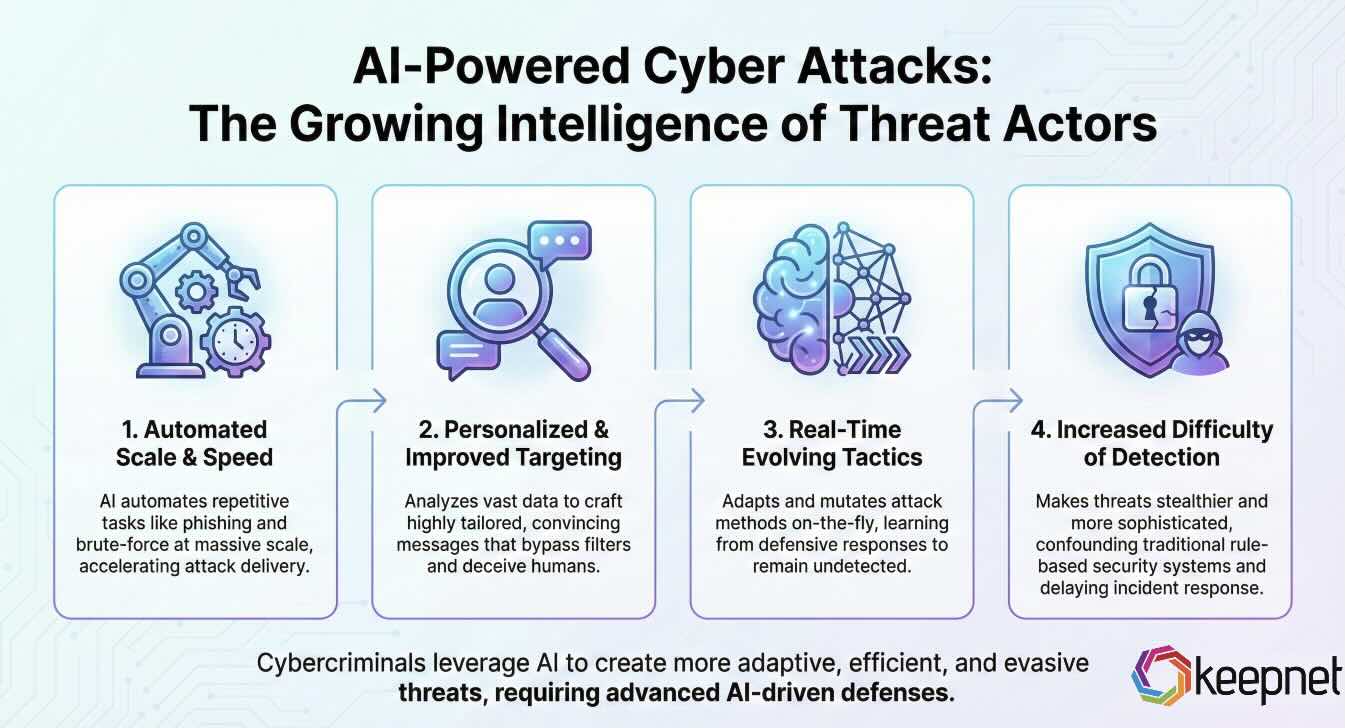
1. AI-Powered Cyber Attacks: The Growing Intelligence of Threat Actors
AI is no longer limited to helping defenders. Cybercriminals are leveraging AI based cyber attacks to automate and improve their attacks, making them more difficult to detect and defend against. AI can rapidly analyze data, personalize attacks, and evolve tactics in real time.
Risks to Organizations
- Automated Phishing Campaigns: AI can craft thousands of convincing and personalized phishing emails in minutes.
- Deepfake Fraud: AI-generated videos and audio can impersonate executives, tricking employees into making unauthorized transfers.
- AI-Powered Exploits: AI tools can scan for and exploit vulnerabilities faster than traditional methods, increasing the risk of data breaches.
Defense Strategy
To combat these threats, adopt AI-driven threat detection and regularly test employee awareness with phishing simulations using tools like Phishing Simulator. Keeping your employees vigilant is key to stopping AI-enhanced attacks.
2. Quantum Computing: The Looming Threat to Encryption
Quantum computing is on the horizon, offering the potential to solve problems far beyond the reach of traditional computers. However, it also threatens to undermine the very foundation of data security by breaking widely used encryption methods.
Risks to Organizations
- Future Data Breaches: Sensitive data encrypted today may be decrypted by quantum computers in the future, exposing financial records, intellectual property, and personal information.
- Encryption Obsolescence: Current cryptographic algorithms like RSA and ECC could become ineffective, leaving data unprotected.
Defense Strategy
Organizations must start preparing now by adopting quantum-resistant encryption. Implementing multi-factor authentication (MFA) and ensuring employees understand the importance of data protection through regular security awareness training is essential.
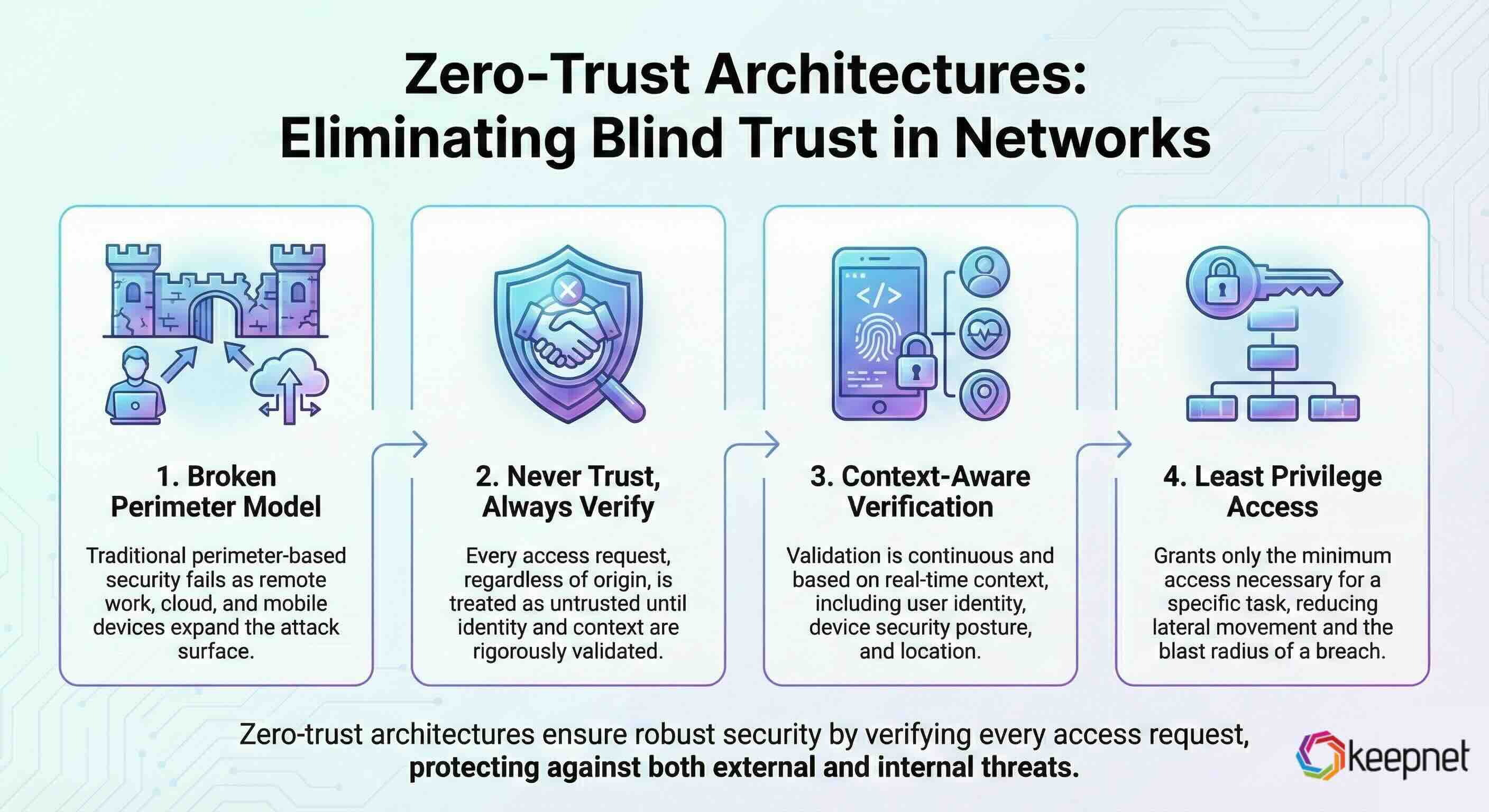
3. Zero-Trust Architectures: Eliminating Blind Trust in Networks
As remote work, cloud services, and mobile devices expand the corporate attack surface, traditional perimeter-based security is no longer effective. Zero-trust architectures ensure that every access request is verified, regardless of where it originates.
Risks to Organizations
- Lateral Movement: Once attackers breach a network, they can move laterally if proper controls aren't in place.
- Insider Threats: Employees with excessive access privileges can inadvertently or maliciously compromise sensitive data.
- Remote Work Vulnerabilities: Distributed workforces increase the risk of unauthorized access.
Defense Strategy
Implement a zero-trust framework that includes continuous authentication, least-privilege access, and network micro-segmentation. Reinforce these measures with security awareness training tool.
4. Deepfakes and Social Engineering: The New Face of Deception
Deepfake technology is becoming more accessible and sophisticated, making social engineering attacks harder to detect. These realistic deepfakes are being used to manipulate employees and bypass traditional security checks.
Risks to Organizations
- Fraudulent Transactions: Employees tricked by deepfake audio or video may transfer funds to malicious actors.
- Data Breaches: Attackers using synthetic identities can gain unauthorized access to sensitive systems.
- Reputation Damage: Successful deepfake attacks can erode trust in leadership and organizational security.
Defense Strategy
Conduct deepfake simulations to train employees to recognize voice-based scams. Implement multi-channel verification for high-stakes requests to confirm authenticity.
5. Human Risk Management: Reducing the Weakest Link in Cybersecurity
Despite advanced security technologies, human error remains one of the leading causes of data breaches. 68% of data breaches involve human factors (Ventures DBIR 2024).
Risks to Organizations
- Phishing and Social Engineering: Employees who lack awareness can fall for deceptive emails or phone calls.
- Weak Passwords and Poor Practices: Simple passwords and bad habits create vulnerabilities.
- Failure to Recognize Threats: Lack of training leaves employees unable to spot evolving cyber threats.
Defense Strategy
Adopt a comprehensive approach to human risk management. Use continuous security awareness training and phishing simulations to reinforce good security habits. Leverage tools like the Keepnet Human Risk Management Platform to identify, monitor, and mitigate human-related vulnerabilities.
How Keepnet’s Human Risk Management Platform Aligns with 2026 Cybersecurity Trends
As cyber threats evolve, human risk management is essential for defending against AI-powered attacks, quantum risks, and social engineering. Keepnet’s Human Risk Management Platform helps organizations tackle these trends by:
- AI-Driven Phishing Simulations: Train employees to recognize AI-enhanced phishing attacks and reduce susceptibility.
- Human Risk Scoring: Identify and measure employees' vulnerabilities to pinpoint areas for improvement.
- Agentic Awareness Training: Offer customized, ongoing training to combat deepfakes, social engineering, and other emerging threats.
By leveraging Keepnet’s platform, you can build a resilient human firewall that stays ahead of evolving cybersecurity risks.