WhatsApp Account Takeovers: Threats, Prevention & Recovery Strategies (2026)
Worried your WhatsApp account could be hacked? Learn how account takeovers really happen, the human-layer tricks attackers use, and how to prevent them with strong security habits, security awareness training, and phishing simulations across your team
With over 2 billion active users, WhatsApp has become a prime target for account takeover attacks. Most “WhatsApp hacks” aren’t magic exploits against the app — they’re human-layer attacks that trick people into giving away verification codes, installing spyware, or approving access they don’t understand.
In this guide, we’ll break down how WhatsApp account takeovers really happen, how criminals combine phishing, social engineering and SIM swapping, and the practical steps individuals and organizations can take to prevent them. For security leaders, this is a textbook example of why security awareness training software and phishing simulation tools are critical to reducing human risk.
What Is a WhatsApp Hack or WhatsApp Account Takeover?
A WhatsApp account takeover happens when attackers gain unauthorized access to your account, usually by targeting you, not WhatsApp’s encryption. They rely on SIM swapping, fake login links (phishing), QR code scams, and social engineering scams to convince users to hand over verification codes or install malicious apps. Once inside, they can spy on your messages, impersonate you, and use your identity to run scams.
Bottom line: a WhatsApp account takeover is a human risk event. It doesn’t just compromise your conversations — it erodes trust, invades privacy, and can quickly escalate into fraud, data loss, and reputational damage for both individuals and businesses
How Criminals Take Over WhatsApp Accounts (Human-Layer Tactics)
Cybercriminals rarely “break” WhatsApp’s encryption. Instead, they focus on manipulating people. Most attacks exploit user behavior — rushing through alerts, reusing passwords, trusting urgent messages, or installing unverified apps (see phishing examples). That’s why WhatsApp account takeover is best understood as a human risk management problem, not just a technical one.
Some of the most common ways attackers take over WhatsApp accounts include:
Social Engineering Attacks
Cyber-criminals rarely crack WhatsApp’s encryption; instead, they rely on proven WhatsApp hacking methods rooted in social engineering attack. Here are two of the most common tricks—explained plainly, with key phrases woven in naturally for readers searching “how to hack WhatsApp” without encouraging wrongdoing.
- Impersonation Scams: Attackers pose as a friend, family member, or even “WhatsApp Support.” The fake persona spins a sense of urgency—“I’m stranded, please wire money” or “We need to verify your account.” Because the request looks familiar and time-sensitive, victims often share personal details or send funds before thinking twice. If you ever receive a surprise message asking for sensitive information, call the real contact on a known number first. A quick check can stop your account from being hacked on WhatsApp.
- Verification-Code Scam: WhatsApp protects log-ins with a six-digit SMS code. Scammers exploit that safeguard by sending a bogus note that says, “We’ve detected unusual activity—reply with the code we just sent to secure your account.” The moment the victim forwards the one-time password, the attacker takes over the profile, locks the real user out, and can message friends to widen the breach. Remember: WhatsApp never asks for your verification code in a chat, and no legitimate contact should either.
Call Forwarding Exploits
Another lesser-known but dangerous WhatsApp hacking method involves abusing call forwarding features. In this scam, hackers trick users into dialing special codes like **21*number#, which silently redirects incoming calls to a number controlled by the attacker. Once activated, any verification call from WhatsApp—which usually contains a one-time code—is intercepted by the hacker. With that code, the attacker can take over the victim’s WhatsApp account without ever needing direct access to their phone.
This type of attack is especially deceptive because users think they’re performing a harmless action—often under the impression they’re “fixing a bug” or “verifying their line”—when in reality, they’re handing control of their WhatsApp to a scammer.
Malware and Spyware Infiltration (When “Tools” Hack You Instead)
One of the most profitable WhatsApp takeover methods in 2026 is simply to fool users into installing “helpful” software that is anything but. On forums and shady sites you’ll see ads for “advanced WhatsApp tools” that claim to boost features or offer extra protection. In reality, many of these rogue apps act as spyware. Because many people are unsure how secure WhatsApp really is, they download unofficial “mods” or clones hoping for extra features or privacy — and end up handing their data directly to attackers.
- Disguised as Legitimate Updates or Mods: Attackers package malicious software inside fake “feature boosters,” unofficial “GB WhatsApp” clones, or phony security patches. Because many people still wonder “is WhatsApp hackable?”, they download these mods hoping for extra protection—only to hand their data to the attacker.
- Phishing Links & Side-Loaded APKs: A single tap on a link that claims to show “how to hack WhatsApp” can trigger an automatic download. Once the APK is side-loaded, the spyware quietly requests accessibility permissions, giving the hacker full visibility into contacts, call logs, and messages.
- Data Exfiltration After installation, the malware forwards every incoming message, attachment, or voice note to a command-and-control server. The victim may never see any outward sign that their WhatsApp account is compromised—until friends receive odd messages or bank accounts start draining.
From a security awareness perspective, this is a classic training scenario: if a tool isn’t from an official app store or verified vendor, users should be taught to treat it as high risk and avoid installing it on any device used for work or personal messaging.
SIM Swapping (SIM Hijacking)
Among the most ruthless WhatsApp hacking methods is SIM-swapping—sometimes called SIM hijacking. Here’s how attackers use it to make “is WhatsApp hackable?” feel alarmingly real:
- Social-Engineering the Carrier: A criminal impersonates you at your mobile provider, armed with stolen personal data or forged ID. By claiming a lost or damaged phone, they ask to “transfer my number to a new SIM.” If the support agent slips, the attacker instantly owns your phone line.
- Catching the Verification Code: Once the number lives on the attacker’s SIM, every text or call—including the six-digit WhatsApp verification code—lands in their pocket. In seconds, they can log in, lock you out, and message your contacts as if nothing happened. Victims often search “how to hack WhatsApp account” after the fact, not realizing that SIM-swapping is the real culprit.
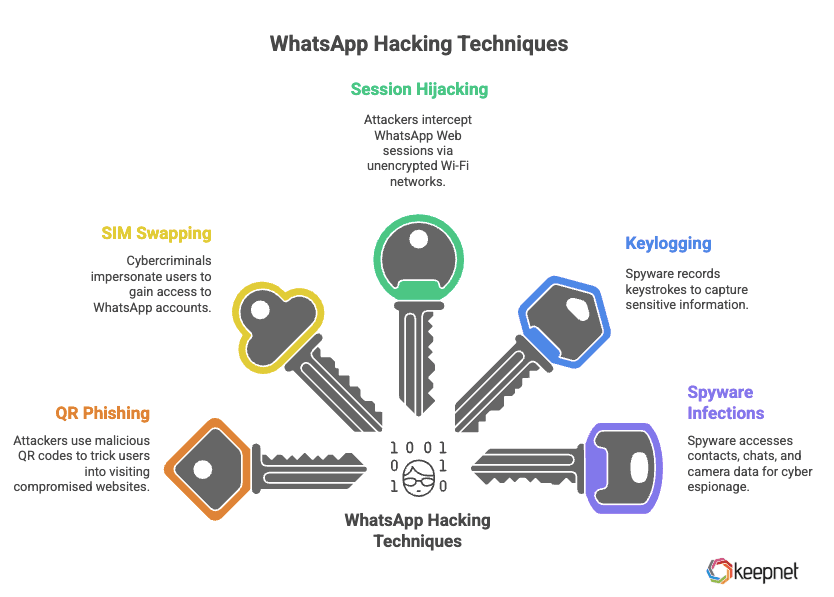
What Are the WhatsApp Account Takeover Techniques in 2026?
Hackers use various advanced methods to gain unauthorized access to WhatsApp accounts, often exploiting user behavior and technical vulnerabilities. Some of the most common techniques include:
- QR Phishing (Quishing): Attackers use QR codes containing malicious URLs to trick users into visiting compromised websites.
- SIM Swapping: Cybercriminals impersonate users to convince telecom providers to issue a new SIM card, allowing them to gain access to WhatsApp accounts.
- Session Hijacking: Exploiting unencrypted Wi-Fi networks, attackers intercept WhatsApp Web sessions to gain access to active accounts.
- Keylogging: Using spyware to record keystrokes, attackers can capture sensitive information, including WhatsApp credentials.
- Spyware Infections: Spyware, often hidden in seemingly harmless apps or WhatsApp clones, can access contacts, chats, microphone, and even camera data for cyber espionage purposes. Advanced spyware can be deployed remotely and may not require any user interaction to activate.
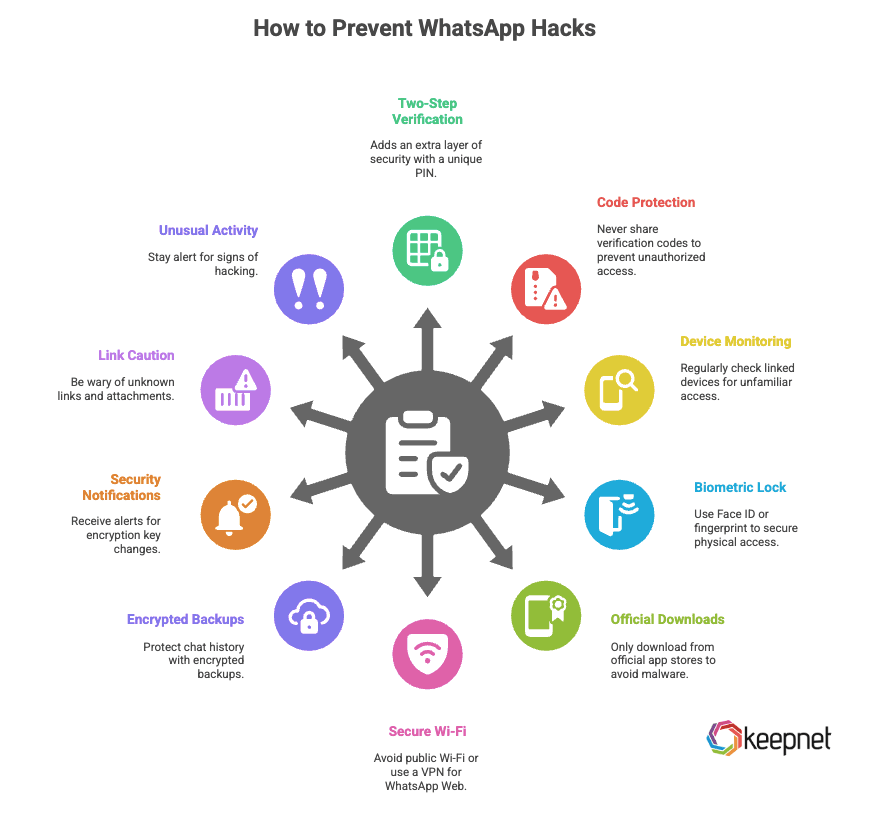
How to Prevent WhatsApp Hacks - Security Checklist
Preventing WhatsApp account hacks requires more than just installing the app. Use this step-by-step checklist to defend against account takeovers, data theft, and surveillance:
- Enable Two-Step Verification (Step Verification): Go to Settings > Account > Two-step verification and set a unique 6-digit PIN. This adds an essential layer of protection beyond the SMS verification code.
- Never Share Verification Codes: Your 6-digit code is the key to your account. Even if someone claims to be WhatsApp support or a friend, never share it — not by message, call, or email.
- Monitor Linked Devices: Regularly review Settings > Linked Devices to see which devices have access. If you spot anything unfamiliar, log it out immediately.
- Lock WhatsApp with Biometrics: Enable Face ID or fingerprint unlock to prevent physical access tfo your chats, even if your phone is unlocked.
- Download only from Official App Stores: Avoid third-party or modified WhatsApp versions (like “GB WhatsApp”) — they’re a common source of spyware and malware infections.
- Avoid Public Wi-Fi for WhatsApp Web: Never use WhatsApp Web on unsecured public Wi-Fi. If needed, use a trusted VPN to encrypt your session.
- Turn On Encrypted Backups: In Settings > Chats > Chat Backup > End-to-end Encrypted Backup, enable backup encryption and set a strong password. This protects your chat history in case your Google Drive or iCloud is compromised.
- Enable Security Notifications: Activate Security Notifications to receive alerts if a contact’s encryption key changes, which may indicate a potential compromise.
- Be Wary of Unknown Links and Attachments: Don’t click on links or download files from unknown numbers, even if they appear to be job offers, giveaways, or urgent alerts.
- Stay Alert for Unusual Activity: Signs of hacking include missing messages, rapid battery drain, strange behavior on WhatsApp Web, or messages you didn’t send. If you notice these, take immediate action.
WhatsApp for Business: A New Frontier for Hackers
With the growing adoption of WhatsApp for business communication, cybercriminals are increasingly targeting business accounts for financial fraud and reputation attacks. These accounts are especially attractive due to their verified status, brand recognition, and direct access to clients and employees.
Common threats include:
- Fake Invoices: Hackers who gain control of a business number send fraudulent payment requests or invoices to customers, often using real branding to avoid suspicion.
- Executive Impersonation Using AI Voice Cloning: Attackers use deepfake audio to mimic the voices of company leaders. Posing as the CEO or CFO, they request urgent wire transfers or sensitive data through WhatsApp messages or voice notes.
- Brand Reputation Damage: Compromised accounts may be used to send spam, scams, or explicit content to clients or group chats, severely undermining customer trust.
- Social Engineering of Employees: Scammers target employees directly via WhatsApp, posing as internal departments (e.g., IT or HR) to steal credentials or gain internal access.
To protect WhatsApp accounts from getting hacked:
- Enable two-step verification on all WhatsApp Business accounts
- Use mobile device management (MDM) solutions to monitor and control employee devices
- Provide regular free cybersecurity awareness training focused on phishing, social engineering, and mobile threats.
These risks make WhatsApp Business account protection a human risk management topic: organizations should combine technical controls with ongoing security awareness training and phishing simulations so employees recognise social engineering on messaging apps as quickly as they do in email
What Are WhatsApp’s Built-In Privacy and Security Features that Prevent Account Takeover?
WhatsApp offers a range of built-in privacy features designed to protect users from unauthorized access, surveillance, and social engineering attacks. These tools help secure both your personal information and your communication, but they work best when users actively enable and manage them.
The table below summarizes the most important WhatsApp privacy and security features, how they work, and why they matter.
| Feature | Description | How It Protects You |
|---|---|---|
| End-to-End Encryption | Messages, calls, and media are encrypted so only you and the recipient can read or hear them. | Prevents interception by hackers, ISPs, and even WhatsApp during transmission. |
| Two-Step Verification | Adds a PIN code in addition to the SMS verification code. | Blocks account takeovers even if someone gets your verification code. |
| Security Notifications | Notifies you when a contact’s security code (encryption key) changes. | Helps detect if a contact has reinstalled WhatsApp or if their account was compromised. |
| Privacy Settings | Allows you to control who can view your profile photo, status, last seen, and online status. | Reduces exposure to social engineering and stalking by limiting visibility. |
| Encrypted Cloud Backups | Lets you protect chat backups with a password or encryption key. | Ensures no one — including WhatsApp, Apple, or Google — can read your backed-up chats. |
| Linked Devices Panel | Shows all devices connected to your account and allows manual disconnection. | Lets you detect and remove unauthorized sessions remotely. |
| App Lock (Biometric) | Enables fingerprint or Face ID lock to open the app. | Adds an extra layer of physical security if your phone is lost or accessed by someone else. |
Table 1: WhatsApp Privacy and Security Features
WhatsApp’s Latest Security Updates in 2026
To stay ahead of evolving cyber threats, WhatsApp has introduced several security enhancements in 2026 that strengthen account protection and improve transparency without burdening users.
Account Protect
When you try to move your WhatsApp account to a new device, a prompt now appears on your previously linked device, asking you to confirm the transfer. This feature helps prevent unauthorized account migrations — especially in SIM swap or stolen device scenarios.
Device Verification
WhatsApp now includes background integrity checks that silently verify your device’s authenticity during login. This makes it harder for malware-infected or cloned devices to access your account, even if the verification code is stolen.
Automatic Security Codes (Key Transparency)
Instead of manually verifying encryption codes with contacts, WhatsApp now automatically checks whether your connection is secure using a technology called Key Transparency. When you open a chat's encryption info screen, it confirms that the end-to-end encryption hasn’t been tampered with — without requiring technical steps from the user.
These updates reflect WhatsApp’s focus on strengthening security while keeping the user experience simple and seamless.
Real-World WhatsApp Hack Incidents
Cybercriminals continue to exploit WhatsApp vulnerabilities, targeting individuals, businesses, and government officials. Here are some of the most significant real-world hacking incidents involving WhatsApp:
1. NSO Group’s Pegasus Spyware Attack (2019 - 2024)
In 2019, WhatsApp sued the Israeli surveillance company NSO Group, accusing it of using Pegasus spyware to hack around 1,400 devices. The spyware exploited a vulnerability in WhatsApp’s video calling feature, allowing attackers to infect devices even if the recipient didn’t answer the call.
The attack targeted journalists, human rights activists, and government officials, raising serious concerns about privacy and digital surveillance. In December 2024, a U.S. judge ruled that NSO Group had violated hacking laws and WhatsApp’s terms of service, marking a major victory for privacy rights. (Source: The Guardian)
2. WhatsApp Data Breach (November 2022)
In November 2022, a major WhatsApp data breach exposed the phone numbers of nearly 500 million users across 84 countries. The stolen data was put up for sale on a hacking forum, making users vulnerable to phishing attacks, spam, and scams.
Although WhatsApp denied that the data was obtained through a breach of its systems, experts warned that cybercriminals could use this information for social engineering attacks and identity theft. This incident underscored the risks associated with leaked personal data and the need for enhanced privacy protection. (Source: Cybernews)
3. AI Voice Cloning and SIM Swap Scam (2023)
In 2023, cybersecurity expert Jake Moore conducted an experiment to demonstrate how AI voice cloning and SIM swap attacks can be used to bypass security and commit fraud.
Using publicly available videos from a business owner’s YouTube channel, he was able to clone the person's voice using AI software. To make the attack more convincing, he also hacked the victim's WhatsApp account via SIM swapping.
Once inside the account, he sent a voice message to the company’s financial director, requesting a £250 payment to a fake contractor. Since the message came from the victim’s WhatsApp account and sounded exactly like him, the financial director believed it was legitimate and transferred the money within 16 minutes.
This case highlights the growing risk of AI-driven fraud and how cybercriminals are combining deepfake technology with traditional hacking techniques to deceive their victims. (Source: WeLiveSecurity) This trend is prompting more users to adopt secure solutions, such as secure travel eSim options for better protection.
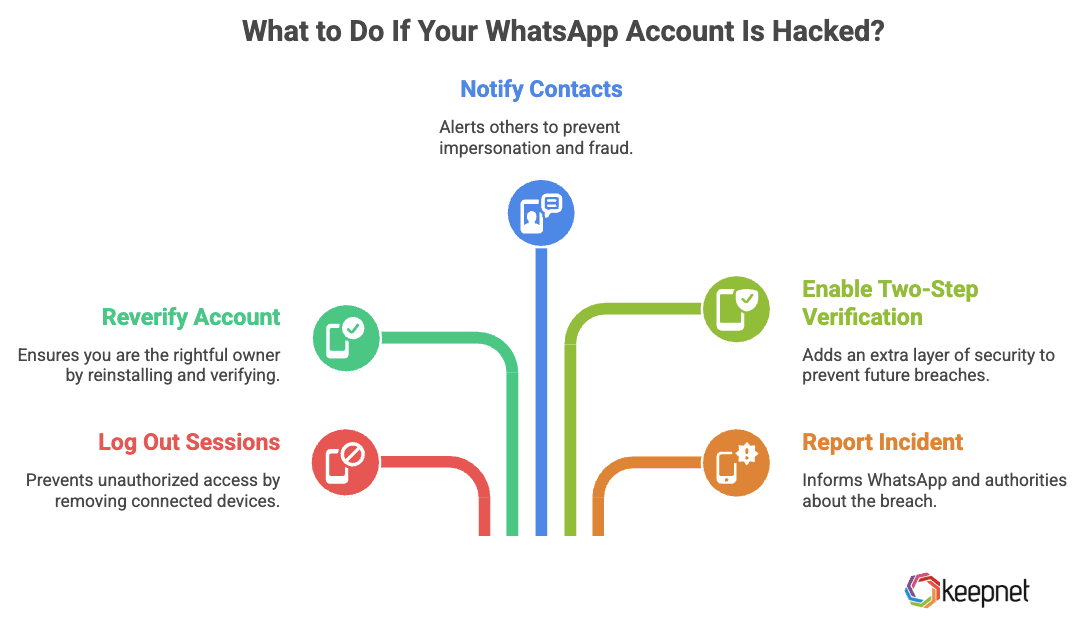
What to Do If You Realize Your WhatsApp Account Is Hacked?
If you suspect that your WhatsApp account is hacked, take these steps immediately to regain control and secure your data:
- Log Out of All Sessions: Open Settings > Linked Devices and log out of all connected devices to remove any unauthorized access.
- Reverify Your Account: Reinstall WhatsApp and complete the verification process using your phone number. Do not share your verification code with anyone.
- Notify Your Contacts: Inform your friends and family that your account was hacked to prevent scammers from impersonating you.
- Enable Two-Step Verification: Once you regain access, activate two-step verification in Settings > Account to add an extra layer of protection.
- Report the Incident: Contact WhatsApp Support and provide details of the breach. If financial fraud or sensitive data is involved, report it to local authorities or a cybercrime unit.
Taking swift action can help minimize damage and prevent further misuse of your account.
WhatsApp vs. Signal and Telegram: Which Messaging App Offers Better Security?
While WhatsApp remains one of the most widely used messaging apps in the world, it's not the only option for users seeking secure communication. Privacy-focused alternatives like Signal and Telegram each offer unique strengths and limitations in terms of data encryption, metadata protection, and user control.
Understanding how these platforms compare can help individuals and businesses choose the right tool based on their privacy requirements, threat models, and usability needs.
| Messaging App | Security Features (Pros) | Limitations (Cons) |
|---|---|---|
| Signal | - Open-source end-to-end encryption (Signal Protocol) - No cloud backups by default - Disappearing messages and screen security features - No metadata logging | - Smaller user base - Limited support for media-rich group features and backup portability |
| Telegram | - Offers “Secret Chats” with end-to-end encryption - Multi-device support - Self-destructing messages | - Regular chats are not end-to-end encrypted by default - Requires manual activation of secure mode |
| - End-to-end encryption enabled by default on all personal chats and calls - Frequent security updates - Supports encrypted backups (optional) - Large global user base | - Backups are not encrypted by default unless manually enabled - Susceptible to social engineering and phishing scams |
Table 2: Security Comparison of WhatsApp, Signal, and Telegram
Choosing the Right App for Your Needs
- Choose Signal if your top priority is maximum privacy and you're comfortable using a platform with fewer mainstream features.
- Choose Telegram if you want speed, multi-device syncing, and more flexibility — but remember to turn on Secret Chats for true end-to-end encryption.
- Choose WhatsApp if you’re looking for a strong mix of security and convenience, especially if most of your contacts already use it — and be sure to enable two-step verification and encrypted backups for better protection.
Ultimately, no messaging app is 100% secure on its own. Users should combine secure apps with strong digital hygiene practices to stay protected against phishing, impersonation, and data leaks.
Protect Your WhatsApp Account from Hacks
While WhatsApp’s end-to-end encryption makes it a secure messaging platform, it remains a target for cybercriminals. Threats like phishing scams, spyware attacks, and SIM swapping highlight the need for stronger security practices beyond WhatsApp’s built-in protections.
To safeguard your account, always enable two-step verification, monitor linked devices, and stay cautious of unsolicited messages. Businesses must also ensure that employees are aware of social engineering tactics and implement organization-wide security policies to prevent unauthorized access.
For a comprehensive approach to human risk management, explore Keepnet’s Human Risk Management Platform to identify vulnerabilities, get security awareness training, and strengthen your organization’s cybersecurity culture.
Editor’s Note: This blog post was last updated on February 19, 2026.