What Is Cyberbullying? Definition, Examples, Dangers, Causes & Prevention (2025 Guide)
Cyberbullying is the repeated use of digital tools like social media, messaging apps, and online games to harass, threaten, or exclude others. This 2025 guide explains the meaning of cyberbullying, its types, real-life examples, causes, dangers, and effective prevention strategies for schools, workplaces, and families.
Have you ever thought, “Why would someone be so rude online? It’s just that you are posting what you want and how you feel! There’s nothing related to the person who talks rudely about you.” But cyberbullying is becoming a bigger problem every day.
Here’s something shocking:
“Of all the social networks, kids on YouTube are the most likely to be cyberbullied at 79 percent, followed by Snapchat at 69 percent, TikTok at 64 percent, and Facebook at 49 percent.”
Now you might be thinking, What exactly is cyberbullying?
To answer your question, stay till the end of this article, as we will talk about what cyberbullying is, the types, and most importantly, what you and your family can do to prevent and respond to it.
What Is Cyberbullying?
Cyberbullying is the act of bullying someone online through electronic communications, such as messages. Generally, it is done on social media or gaming platforms to hurt, embarrass, or threaten a person.
Examples of text messages you might get in cyberbullying:
- Repeated insulting messages like, “You’re so useless”, or “No one likes you.”
- Threats like, “Pay us more or else…”
- Spreading rumours through messages like, “Did you hear what they did last night?”
- Sharing private photos or data without permission.
- Removing someone from group chats and sending messages like, “We don’t want you here.”
These examples demonstrate how painful online messages can be at times. Now, let us know about the common platforms where cyberbullying happens:
- Social media: Platforms like Facebook, Instagram, Snapchat, and YouTube
- Messaging apps: Apps like WhatsApp, Messenger, and Discord
- Gaming platforms: Xbox Live, PlayStation Network, online multiplayer games
- Email or SMS: Unwanted messages sent through email or text
- School or work platforms: Sometimes, cyberbullying happens in group chats or forums for school or work communication.
How Cyberbullying Works in 2025
Cyberbullying spreads through everyday platforms: Instagram, TikTok, X, WhatsApp, Discord, Snapchat, YouTube comments, school portals, workplace tools like Slack/Teams, online games, and review sites. Offenders use speed (instant posts), scale (mass audiences), and search (content is findable). Newer tactics include AI voice or image clones, deepfake memes, and review bombing that harms reputation or employment prospects. Understanding these channels helps you build better defenses and training.
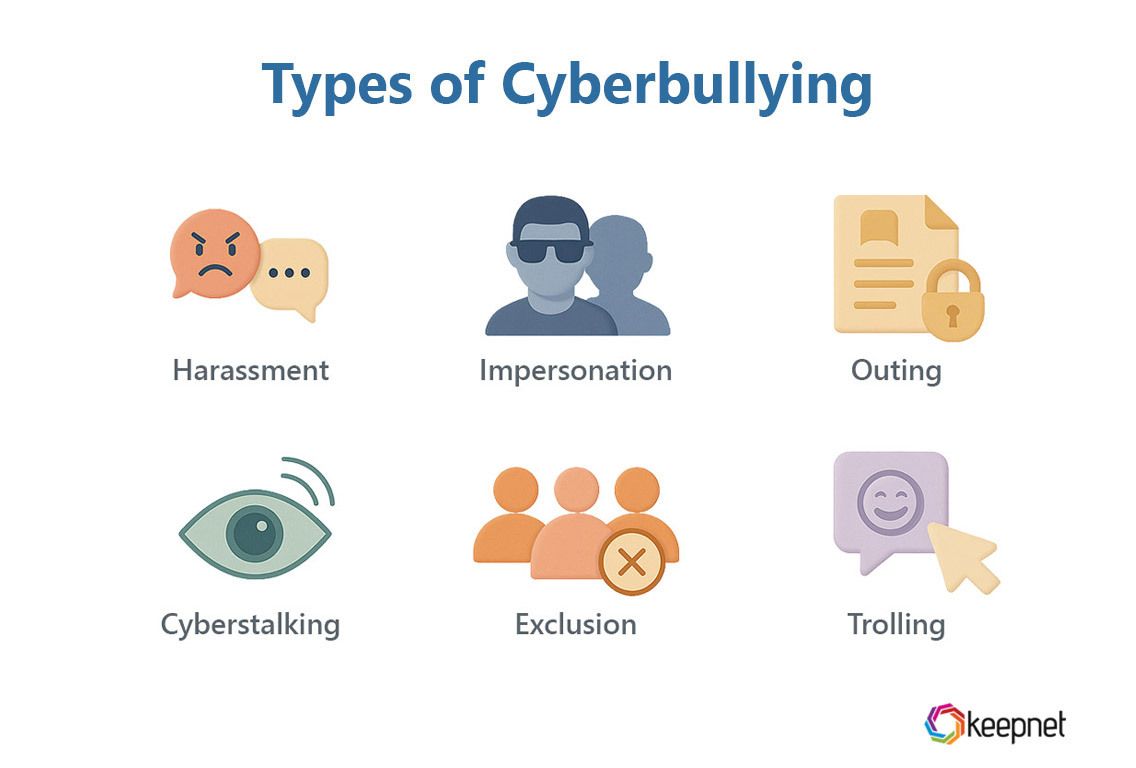
Types of Cyberbullying (With Quick Indicators)
Below are common types of cyberbullying with early warning signs and actions.
- Harassment & Hate Speech: Persistent insults, slurs, or threats via DM or comments. Signs: sudden spike in hostile notifications. Action: document, block, report, escalate if threats mention physical harm.
- Impersonation & Account Takeover: Creating a fake profile or stealing access to post harmful content. Signs: “you posted this?” messages, login alerts. Action: reset passwords, enable MFA, report the fake profile, notify contacts. Without any identity theft protection, victims are left vulnerable to impersonators turning stolen identities into lasting harm, both online and offline.
- Doxxing & Data Exposure: Publishing private information (address, phone, medical records) to intimidate. Signs: strangers calling/texting; personal info appears on forums. Action: preserve evidence, contact platform and, if needed, local authorities.
- Outing & Non‑consensual Image Sharing: Posting someone’s private messages, photos, or videos without consent. Signs: sudden humiliation, messages like “seen your pics.” Action: rapid takedown requests, report to platform, seek legal advice if necessary.
- Rumor‑Spreading & Defamation: False claims, edited screenshots, “whisper networks.” Signs: peer avoidance, sudden reputation dips. Action: statement of record, evidence log, request removals.
- Exclusion & Group Pile‑Ons (Dogpiling): Deliberately leaving someone out of chats/teams; coordinated attacks. Signs: “chat moved,” mass negative replies. Action: community moderation, rate limits, invite oversight from admins/HR.
- Cyberstalking: Repeated monitoring, location tracking, unwanted messages across platforms. Signs: same person appears everywhere, attempts to contact friends/family. Action: safety plan, block, report; consider local law enforcement.
- Extortion & Sextortion: Threatening to release sensitive content or fake “deepfakes” unless paid. Signs: coercive demands, cryptocurrency requests. Action: preserve evidence, refuse payment, report to platform and authorities.
- Review Bombing & Professional Sabotage: Flooding employer review sites, app stores, or LinkedIn comments to harm a career. Signs: sudden wave of low‑star reviews. Action: centralize responses, platform escalation, legal counsel if defamatory.
- AI‑Assisted Harassment: Deepfake videos/voice notes, synthetic screenshots. Signs: media that looks/sounds like you but isn’t. Action: public statement + platform reports; collect hashes/screens for takedown.
- Tip: If you’re building policies, categorize incidents by intent (malice vs. “joke”), impact (psychological, reputational, safety), and illegality to decide response speed and stakeholders.
Examples of Cyber Bullying (Realistic Scenarios)
Examples help people recognize issues quickly. The following are anonymized, realistic samples across school, home, and work:
- School WhatsApp group: “Everyone block Jahe. She smells like trash. New group without her 👉 .”
- Gaming voice chat: “Report this loser, aim‑botter! Dox in 10, I have his IP.”
- Instagram comments: “You don’t deserve to live. Go do us a favor.”
- Workplace Slack: Anonymous app posts GIFs mocking an employee’s accent after a meeting.
- Fake profile: A copycat account posts edited photos to suggest someone cheated on exams.
- Deepfake prank: A synthetic audio clip mimics a teacher using slurs; students share it as “proof.”
- Review bombing: A group from a private Discord leaves dozens of 1‑star reviews at once to punish a creator.
If any example feels familiar, move to preserve evidence (screenshots + raw files + URLs), block/limit, and report.
Effects & Dangers of Cyberbullying
Cyberbullying has multi‑layered consequences—personal, social, and organizational. When writing policies or training, address each layer.
- Psychological & Physical: Stress, anxiety, sleep disruption, loss of appetite, fear of devices. People may withdraw from school/work or hobbies. Encourage medical or mental‑health support when needed.
- Academic & Career: Missed classes or meetings, lower grades or performance, avoidance of public tasks, reluctance to collaborate. Keeping digital devices optimized with tools like a cleaner tool for Mac or similar software also helps reduce unnecessary technical stress, allowing victims to focus more on recovery and productivity rather than device issues.
- Reputation & Opportunities: Search results and viral posts can harm college admissions or hiring decisions; deepfakes can create false “evidence.”
- Financial & Legal: Extortion, fraud, or identity theft; costs for legal takedowns; potential lawsuits when harassment crosses into illegal territory.
- Organizational Risk: Productivity loss, attrition, hostile‑work‑environment claims, compliance breaches (e.g., discrimination law), and brand damage when incidents go public.
The dangers of cyberbullying multiply because online content can be persistent (hard to remove) and pervasive (cross‑platform). This is why early detection and fast response matter.
Root Causes: What Is the Main Cause of Cyberbullying?
There isn’t a single cause, but several drivers repeatedly show up:
- Anonymity & Distance: Online disinhibition reduces empathy and increases risk‑taking.
- Power & Status Dynamics: People use harassment to gain clout, consolidate a group, or control others.
- Norms & Incentives: Platforms that reward outrage or speed see more pile‑ons. Weak moderation worsens it.
- Spillover from Offline Conflicts: Classroom drama or office politics continue online after hours.
- Bias & Prejudice: Racism, sexism, ableism, and other bigotries often fuel attacks.
- Skills Gap: Low digital literacy—poor privacy settings, oversharing, or not knowing how to report—makes people easier targets.
- Misinformation & AI Tools: Manipulated media and synthetic accounts make lying faster and more convincing.
Main cause in one sentence: when power imbalance meets low accountability in online spaces, cyberbullying thrives.
Facts About Cyberbullying (Common Myths vs. Reality)
Even experienced leaders sometimes carry myths. Here are unique, practical facts you can use in briefings:
- “It’s only online; just log off.” Not realistic—school/work require digital presence; evidence persists even if you log off.
- “Kids will figure it out.” Without skills training and clear reporting paths, many never escalate until the problem is severe.
- “Free speech means hands off.” Free speech doesn’t protect threats, doxxing, or targeted harassment. Policies can—and should—moderate behavior while respecting lawful speech.
- “AI deepfakes are unstoppable.” They’re challenging, but you can counter with rapid reporting, media forensics, and public statements with authoritative verification (e.g., watermarked originals, source‑of‑truth repositories).
Early Warning Signs for Cyberbullying (Students, Parents, Employees, Managers)
Recognize signals before damage grows.
- For students & parents: sudden device secrecy, deleting apps, school avoidance, mood swings, new online “friends” pressuring for photos.
- For teachers & counselors: attendance dips after online conflicts; several students disengage from group work; “side chats” excluding one student.
- For employees & managers: unexplained drop in meeting participation, being muted or ignored in chats, anonymous emoji “dogpiles,” sudden wave of prank calendar invites.
- For IT/Security: repeated password reset alerts, fake account reports, unusual mentions spike in social‑listening dashboards.
How to Prevent Cyberbullying (Policy + Culture + Tools)
How to prevent cyberbullying effectively? Treat it like any human‑risk problem: align culture, clear rules, and practical training.
1. Policy & Governance
Create a plain‑language Acceptable Use and Anti‑Harassment policy with examples (“Don’t create fake accounts,” “No doxxing,” “No pile‑on campaigns”). Include escalation paths and consequences. For schools, add age‑appropriate classroom norms and parent signatures.
2. Design for Digital Empathy
Add “friction” to slow harm: comment delays after multiple reports, “are you sure?” prompts for flagged words, rate limits in large channels, anonymous reporting that immediately pings moderators.
3. Privacy Hygiene
Ensure your social media accounts are private. Update the settings of who can see or comment on your posts. If someone misbehaves, first report the account and then block that user so that they won’t be able to contact you again. At times, you may also need to untap your phone if you suspect someone is spying or hacking into your device, as bullies often try to access personal data this way.
You may have observed that in every industry, people connect with someone who talks with respect online. For example, businesses these days are conscious about offering online customer care personalization with positive messages. This is because if you are kind to people online, then it earns love and respect for your brand.
4. Skills Training (Students & Employees)
Run scenario‑based drills: how to screenshot correctly, how to report on each platform, what to say when a friend is targeted (“I’m here. Let’s save evidence and report together.”). Practice bystander interventions: private check‑ins, report buttons, not amplifying harmful posts.
5. Trusted Adults & Champions
In each class or team, name a go‑to person. At work, empower HR + Security + Legal to collaborate. In youth settings, define teacher/counselor roles and involve parents.
6. Monitoring & Early Detection
Use keyword alerts and social listening for brand and safety (within legal/ethical boundaries). Encourage anonymous reports; track time‑to‑first‑response.
7. Partnerships & Helplines
Maintain a list of local counseling services, cybercrime units, and online safety NGOs for warm handoffs. If there is immediate danger, contact emergency services.

How to Stop Cyberbullying When It Happens (5R Playbook)
When a case appears, move quickly and consistently. Share this 5R model with your community:
- Recognize – Confirm it is bullying (pattern + harm + power imbalance).
- Record – Screenshot, save URLs, export chat logs, store original files. Keep dates, times, usernames, and platform IDs.
- Restrain – Block, mute, restrict comments, change privacy settings, and secure accounts (password + MFA). Avoid direct confrontation if it will escalate.
- Report – Use in‑app reporting; notify school/HR/platform; involve police if threats, extortion, or stalking occur.
- Recover – Offer counseling support; plan online reputation repair; debrief the class/team; update policy/training to prevent recurrence.
Cyberbullying vs. Online Conflict vs. Illegal Harassment
Not all online meanness is cyberbullying, and not all cyberbullying is a crime.
- Online conflict: Two‑sided, short‑term argument without power imbalance.
- Cyberbullying: Repeated, targeted harm with power imbalance (one‑to‑many, older‑to‑younger, boss‑to‑employee).
- Criminal harassment / threats / extortion / image‑based abuse: May violate laws; treat as safety matters and escalate to authorities.
- Is cyberbullying illegal? Laws vary by country/state. Some acts (threats, stalking, revenge porn, doxxing that leads to harm) may be crimes. Consult local legal counsel or school/HR legal teams for your jurisdiction.
Parents & Teachers: A Simple Home–School Plan
Parents and educators can reduce harm with a shared, predictable plan.
- Family digital agreement: rules for device bedtime, privacy settings, and who to call when something goes wrong.
- School integration: brief lessons on media literacy, respectful online communication, and reporting.
- Bystander skills: encourage students to support targets privately and report publicly.
- Documentation drills: practice screenshots and saving links so students are ready before a crisis.
Cyberbullying in the Workplace (For CISOs, HR, and Security Awareness Leaders)
Cyberbullying at work damages engagement and creates compliance risk. Leaders should:
- Bake it into security awareness programs. Use micro‑learning on harassment recognition, how to stop cyberbullying at work, and safe reporting.
- Instrument collaboration tools. Configure Slack/Teams moderation, archive offensive content for investigations, and limit anonymous apps that enable pile‑ons.
- Set up a cross‑functional response team. HR (well‑being + policy), Security (evidence, account security), Legal (risk), Comms (brand).
- Measure what matters. Time to first response, number of bystander reports, escalation rate, and resolution satisfaction.
- Support targets. Offer EAP or counseling, workload relief, and a manager‑led restoration plan.
60‑Minute Incident Response Checklist (Managers & Moderators)
You can’t fix everything in an hour, but you can stop the bleeding.
- Minutes 0–10: Triage the report, confirm harm, assign a case owner, secure accounts (password + MFA), and limit further exposure (mute/lock threads).
- Minutes 10–30: Capture evidence (screens + raw files), log platforms involved, map the attackers (IDs/links), and classify the type (see list above).
- Minutes 30–45: File platform reports, notify HR/School leadership/Security, and decide on immediate safety steps.
- Minutes 45–60: Communicate with the target (care + plan), document actions in your tracker, set review in 24 hrs, and consider a short, factual statement if rumors are spreading.
Reporting & Evidence: How to Build a Strong Case
Platforms and authorities act faster when your report is complete.
- Evidence pack: screenshots (include full screen + timestamps), URLs, raw media (original files), platform report IDs, and a short timeline.
- Chain of custody: store originals in a secure folder; record who accessed them.
- Non‑amplification rule: do not repost abusive content publicly while collecting evidence; share only with investigators.
Practical Tools & Templates for Cyberbullying
Below is a compact table you can use in policy documents or lessons.
Types of Cyberbullying — Examples, Impact, First Response
| Type | Example | Likely Impact | First Response |
|---|---|---|---|
| Harassment | Repeated DMs: “You’re worthless. | Anxiety, avoidance | Screenshot, block, report |
| Impersonation | Fake account posting as target | Reputation harm | Report fake, notify peers, MFA |
| Doxxing | Posting home address | Safety risk | Evidence, platform + police if threats |
| Outing | Sharing private photos | Humiliation | Takedown request, counseling support |
| Rumors/Defamation | Edited “proof” of cheating | Social exclusion | Statement of record, removal |
| Dogpiling | 200 mocking comments | Psychological harm | Rate limit, moderator action |
| Cyberstalking | Daily unwanted messages | Fear, isolation | Safety plan, legal advice |
| Extortion/Sextortion | Pay or we post | Financial, emotional | Do not pay, report immediately |
| Review Bombing | Dozens of 1‑stars | Career/brand harm | Centralized response, evidence |
| AI Deepfakes | Fake voice/video | Trust & reputation | Public verification, takedown |
Types of Cyberbullying — Examples, Impact, First Response
How Keepnet Extended Human Risk Management Helps Against Cyberbullying
If you lead security awareness or student safety programs, you need both culture and capability. Keepnet Extended Human Risk Management Platform can help you operationalize the playbooks above:
- Security Awareness Training – deliver micro‑lessons on recognizing cyberbullying, preserving evidence, reporting across platforms, and bystander intervention. Include modules for parents, teachers, students, and employees.
- Phishing Simulator – while built for social‑engineering resilience, simulations teach privacy, MFA, and reporting discipline—skills that also reduce cyberbullying exposure (strong authentication, careful sharing, fast escalation).
Looking to roll this out? Start with a 30‑day plan: baseline survey → policy refresh → scenario training → reporting drill → dashboard review. Then repeat quarterly.
Legal and Policy Measures
There are rules for people to protect themselves from cyberbullying. In countries like the USA and, UK, cyberbullying is illegal.
For example, in the UK, you are committing a criminal offence if the cyberbullying is causing ‘alarm or distress’ to the victim (the Protection from Harassment Act 1997) or can be considered ‘grossly offensive’ (the Malicious Communications Act 1988 and the Communications Act 2003).
Likewise, in Canada, Bill C-13 criminalises harassing or annoying behaviour done through electronic communication.
Many schools and workplaces have policies against bullying. These policies govern acceptable and unacceptable behaviours, incident reporting procedures, and the steps to be taken to support victims.
Importance of Accountability and Reporting
If no one ever spoke about bullying incidents that happened to them, then it would be difficult to stop this offence. In the absence of the knowledge that someone is being affected due to disrespectful online activities, there can be no action or implementation of laws and policies.
That is where accountability becomes important. People who bully others should be punished for their actions.
By reporting cyberbullying, authorities will come to know about the incident and can take immediate action.
An action for betterment: Next time, if you see something wrong online, make sure you report it. Your voice can protect others and stop harmful behaviour.
Build a Kinder and Safer Online World Together
Cyberbullying is a real and serious problem. It's our responsibility to fight against it and create a safe online space for everyone.
To achieve this, the first step is to spread awareness about this issue, followed by conducting ourselves according to digital etiquette on social media. You should also encourage others to do the same.
If you find that someone is practising cyberbullying online, then report that account immediately.
Many countries, like Italy, the UAE, the USA, UK, have already incorporated cyberbullying laws into their systems. Other countries should take inspiration from these countries and create laws that take strict action against cyberbullies.
Remember, every small step counts. If we are all in this together, then we can make the internet a better place where everyone respects and supports each other with positive vibes.