Using Real-World Breaches in Security Awareness Training: 2026 Playbook
Learn how to use real breach scenarios—like phishing, deepfakes, and QR threats—in security awareness training. This 2026 playbook shows how AI, behavioral data, and role-specific content can drive real behavior change across your organization.
Phishing emails impersonating suppliers. Deepfake voice calls mimicking CEOs. QR code traps hidden in routine invoices. These aren’t theoretical threats—they’re real attacks that bypass even the best firewalls by targeting people.
Most training programs still treat these incidents as isolated or unlikely. But when employees encounter breach scenarios rooted in actual events—especially those from their industry or role—the lessons hit harder and stick longer.
In this blog, we’ll explore how breach-based simulations transform user behavior, highlight real attack patterns from 2025–2026, and explain how Keepnet’s Security Awareness Training Software platform turns frontline employees into an active layer of defense through realistic, role-specific, and measurable security awareness training.
The Psychology of Real Incidents in Training
Real incidents trigger emotional responses—confusion, urgency, even fear. These reactions are powerful tools in training. When employees feel the impact of a breach scenario, even in a simulation, the lesson becomes personal and memorable.
Story-based learning taps into this psychology. People retain information better when it’s part of a narrative, especially if the story mirrors something they could realistically experience in their role.
Adding job-specific context makes this even more effective. A marketing employee targeted with a credential phishing email tied to a fake campaign will react differently than a finance employee facing a vendor invoice scam. When the threat feels relevant, users engage more deeply—and change their behavior more reliably.
Watch the video below from Keepnet’s Real-Life Security Awareness Training Story Series, featuring the real story of a vishing attack that resulted in a $32,000 loss.
Real Breach Case Studies That Reshape Behavior
Security awareness training is far more effective when it reflects real-world situations. Generic examples often fail to engage employees—but real breaches make the risks tangible and the lessons stick.
In this section, we’ll break down several major cyberattacks from 2025 to uncover the human errors that attackers exploited—and the consequences that followed. Let’s look at real cases, including breaches at Marks & Spencer, Co-op, Jaguar Land Rover, and the Legal Aid Agency, to see how employee actions can directly shape an organization’s cybersecurity posture.
Marks & Spencer (M&S) Breach
In April 2025, Marks & Spencer fell victim to a cyberattack that originated through a third-party contractor and was triggered by human error. The breach caused major disruptions across the business, including halted online orders, issues with contactless payments, and stock availability problems in stores. The financial impact was significant, with operating profits projected to drop by £300 million. This incident underscores the importance of training employees to recognize third-party risks and respond effectively to early signs of compromise, especially in complex retail environments. (Source)
Co-op Cyberattack
In late April 2025, the Co-operative Group detected an attempted cyberattack and responded by proactively disabling access to parts of its IT systems. The timing—just days after the M&S breach—prompted the organization to take immediate action to protect its infrastructure, temporarily disrupting stock monitoring, virtual desktops, and some internal services.
While no customer data was reported as compromised, the attack affected behind-the-scenes operations and limited remote work capabilities. Co-op emphasized that the action was precautionary and not due to any employee error. This case highlights the importance of employee readiness and system monitoring in quickly identifying and containing potential threats—especially when they coincide with broader industry targeting. (Source)
Jaguar Land Rover (JLR) Data Breach
In March 2025, a hacker named “Rey” claimed responsibility for breaching Jaguar Land Rover’s internal systems, leaking over 700 documents that included source code, development logs, and employee credentials.
The breach reportedly stemmed from compromised Jira credentials, likely stolen through infostealer malware. This type of attack often bypasses traditional defenses by targeting employee behavior—such as weak password practices or unpatched systems.
The incident highlights the need for training that focuses on credential hygiene, malware recognition, and the everyday habits that can expose critical assets. It’s a reminder that even a single compromised login can have widespread consequences. (Source)
Legal Aid Agency Breach
In April 2025, the UK's Legal Aid Agency suffered a major data breach that exposed personal details of people who applied for legal aid—some dating back as far as 2010. The leaked information included names, birth dates, contact details, national ID numbers, and financial records like debts and payments.
The Ministry of Justice attributed the breach to long-term neglect and poor management of the agency’s outdated IT systems. The incident underscores the critical importance of keeping cybersecurity infrastructure up to date and training employees to identify and respond to system vulnerabilities before they can be exploited. (Source)
These real cases illustrate that when employees are trained using real breach scenarios, they gain a clearer understanding of how attacks unfold—making them more likely to detect and respond to threats swiftly, before significant damage occurs.
For more examples of successful breach prevention strategies in action, explore our article: Keepnet’s Data Breaches Protection Success Stories.
Turn breach lessons into role-based campaigns (and prove behavior change)
Real breaches make training feel urgent and relevant—but the biggest value comes when you convert each breach story into a repeatable campaign that’s tailored by role and measured over time.
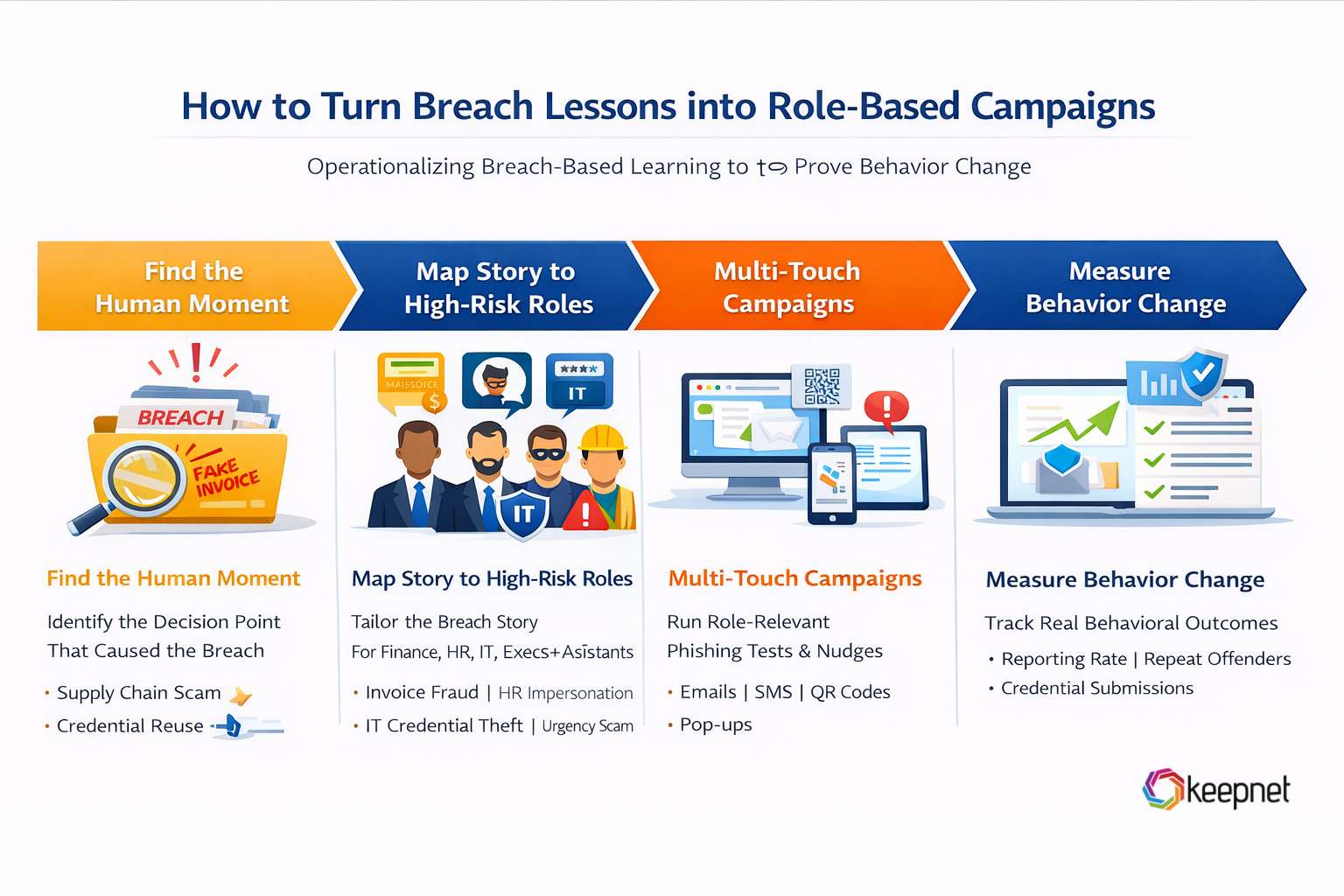
Here’s a practical way to operationalize breach-based learning:
- Extract the “human moment” from the breach: Identify the exact decision point that led to compromise (e.g., supplier impersonation, credential reuse, QR scan, phone-based social engineering).
- Map the story to high-risk roles: Translate the same breach into role-relevant versions (Finance: invoice fraud; HR: impersonation; IT: credential theft; Exec/Assistants: urgency + authority scams).
- Run multi-touch simulations + reinforcement: Pair multi channel phishing simulations with short reinforcement (microlearning or nudges) so employees don’t just “recognize” threats—they build repeatable habits.
- Measure behavior change (not just completion): Track outcomes like reporting rate, time-to-report (dwell time), repeat-offender reduction, and credential submission rate to see whether risk is actually declining.
If you’re evaluating platforms, the key question is whether you can run these role-based breach campaigns continuously—and prove improvement with reporting over time. See how Keepnet supports this approach in its Security Awareness Training platform.
AI-Driven Simulations and Predictive Awareness
Cyber threats evolve constantly—and so should your training. Static, one-size-fits-all approaches no longer prepare users for the real tactics threat actors use. That’s where AI-driven phishing simulations make the difference.
By analyzing employee behavior, past incidents, and threat intelligence, AI can create personalized phishing simulations that reflect an individual’s risk profile. For instance, a finance manager who regularly processes invoices may receive a simulated phishing email disguised as a vendor payment request—mirroring real threats they’re most likely to encounter.
Beyond simulation, AI helps predict which users are likely to fall for future attacks. It identifies repeat offenders, detects patterns of risky behavior, and automatically assigns adaptive learning paths to close those gaps. This data-driven approach transforms training from a checkbox exercise into a predictive defense strategy.
With AI, organizations can shift from reactive to proactive—anticipating vulnerabilities before attackers exploit them. To learn how to tailor phishing simulations to specific job functions and risk levels, explore our CISO’s Guide on Customizing Phishing Simulations for Different Departments.
From Phishing Simulation to Response – Building Resilience
Recognizing a phishing email is only the first step. Real resilience is built when employees can detect, report, and react to threats in real time. That’s why modern security awareness training must simulate the entire response cycle, not just the initial recognition.
To measure and strengthen this capability, organizations must go beyond basic click rates and track behavioral metrics that reflect actual response readiness. Key metrics include:
- Phishing Reporting Rate: Tracks how often users report phishing emails. A rising rate shows that users are not just avoiding threats but actively escalating them.
- Phishing Dwell Time (Time to Report): Measures how long it takes an employee to report a phishing email. Shorter dwell times reduce exposure and potential impact.
- Repeat Offender Rate: Identifies users who repeatedly fall for phishing simulations. This helps target specific users for focused retraining.
- Credential Submission Rate: Captures how many users entered credentials on a phishing page. A lower rate reflects improved awareness and caution.
- Departmental Risk Score: Highlights departments with higher susceptibility to phishing, helping focus training where it’s most needed.
- User Risk Score: Assesses individual vulnerability by combining behavior metrics like clicks, reports, and repeat offenses to drive personalized training.
By embedding these data points into phishing simulations and response drills, organizations gain a clear view of their human risk posture and can take strategic action to strengthen it.
To explore how to define and use security awareness training metrics effectively, check out Keepnet’s full guide: How to Set the Right Security Awareness Metrics to Protect Your Organization.
Components of a 2026-Aware Security Training Playbook
In 2026, cyberattacks are no longer broad and obvious—they’re tailored, subtle, and timed to exploit everyday workflows. From deepfake voice scams to malicious QR codes hidden in invoices, attackers are adapting faster than many training programs.
To keep up, organizations need more than basic awareness—they need a strategic, data-driven playbook that reflects real threats, adapts to different roles, and drives measurable behavior change.
Here are the core components every 2026-ready security awareness playbook should include.
1. Emerging Threat Modules
Cyber attackers are constantly innovating, and training programs must evolve just as quickly. A 2026-ready playbook must include dedicated modules for fast-growing threat types like:
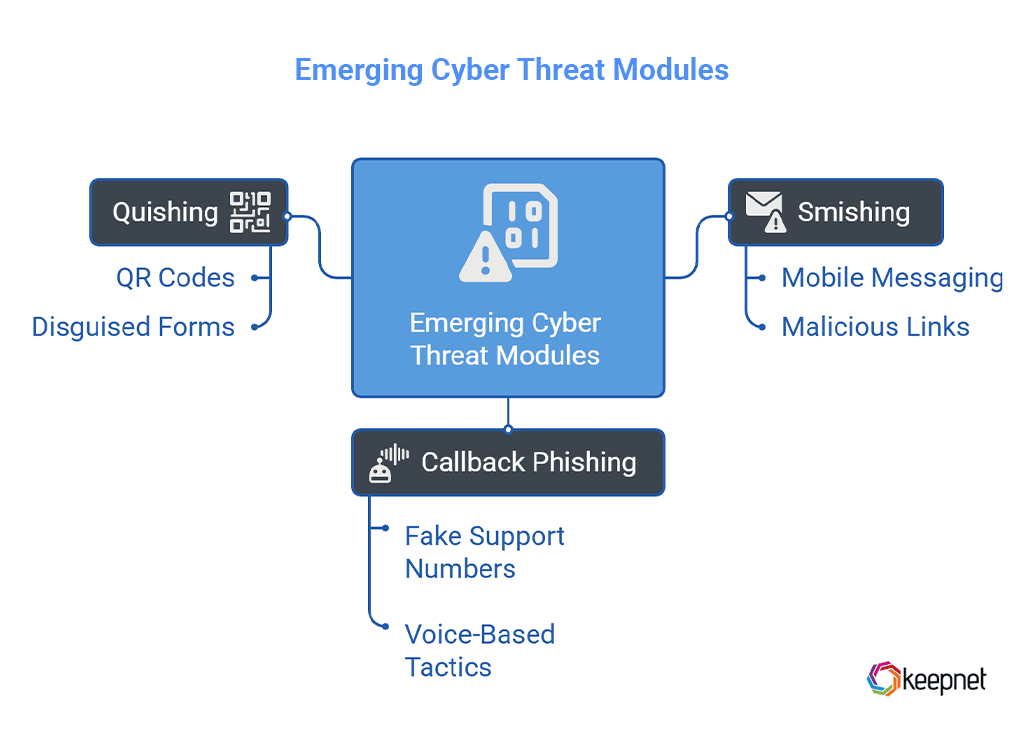
- Smishing – SMS-based phishing that exploits trust in mobile messaging to trick users into clicking malicious links or sharing credentials.
- Callback Phishing – A hybrid attack where users are lured into calling fake support numbers, leading to voice-based social engineering.
- Quishing (QR Code Phishing) – Phishing attacks delivered via QR codes, often disguised as business forms, menus, or login prompts.
These threat types bypass traditional email filters and rely on user behavior. That’s why training must include realistic, scenario-driven phishing simulations that mimic how these attacks appear in daily routines—whether on a smartphone, through a phone call, or in a printed document.
2. Compliance-Integrated Training
Security awareness training must do more than educate—it must also help your organization stay compliant. A strong playbook should align training content with key regulatory frameworks such as:
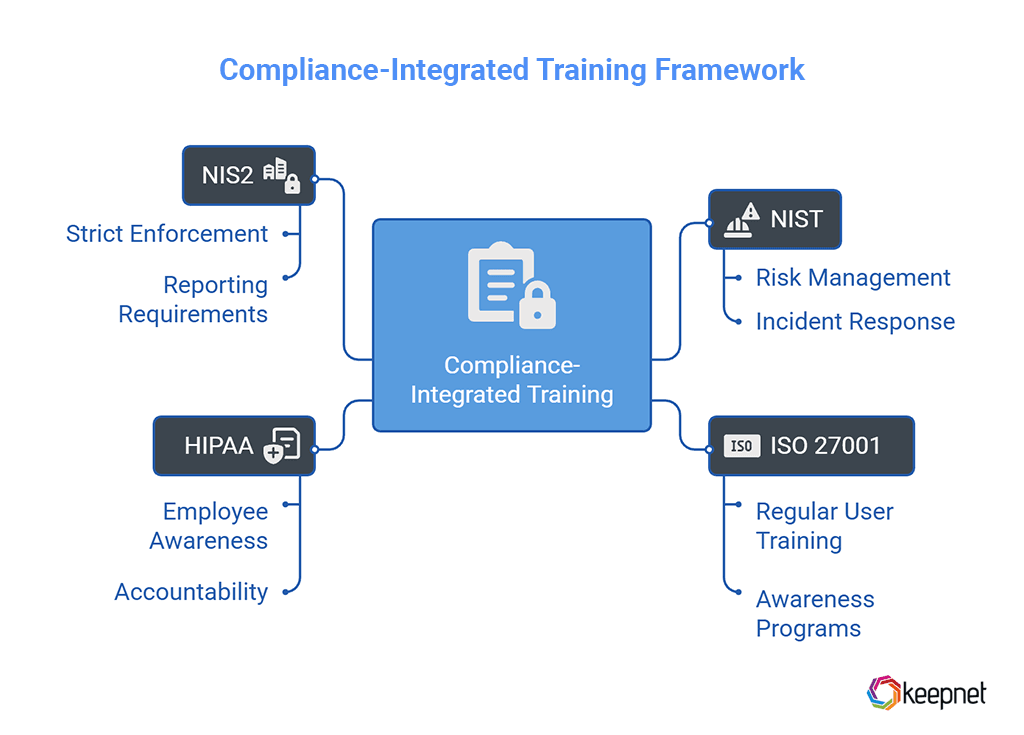
- NIST (National Institute of Standards and Technology) – focusing on risk management and incident response practices.
- ISO 27001 – requiring regular user training and awareness as part of a certified Information Security Management System (ISMS).
- HIPAA – mandating protection of sensitive health information through employee awareness and accountability.
- NIS2 – expanding cybersecurity obligations across critical sectors in the EU and UK, with strict enforcement and reporting requirements.
By integrating these standards into training, organizations can ensure regulatory alignment, reduce audit gaps, and demonstrate proactive risk management. This also reinforces a culture of accountability, where employees understand the compliance impact of their daily actions.
3. Microlearning and Gamification
Traditional, hour-long training sessions are no longer effective in keeping users engaged. Microlearning breaks down complex cybersecurity topics into short, focused lessons that employees can absorb quickly—often in just 3–5 minutes.
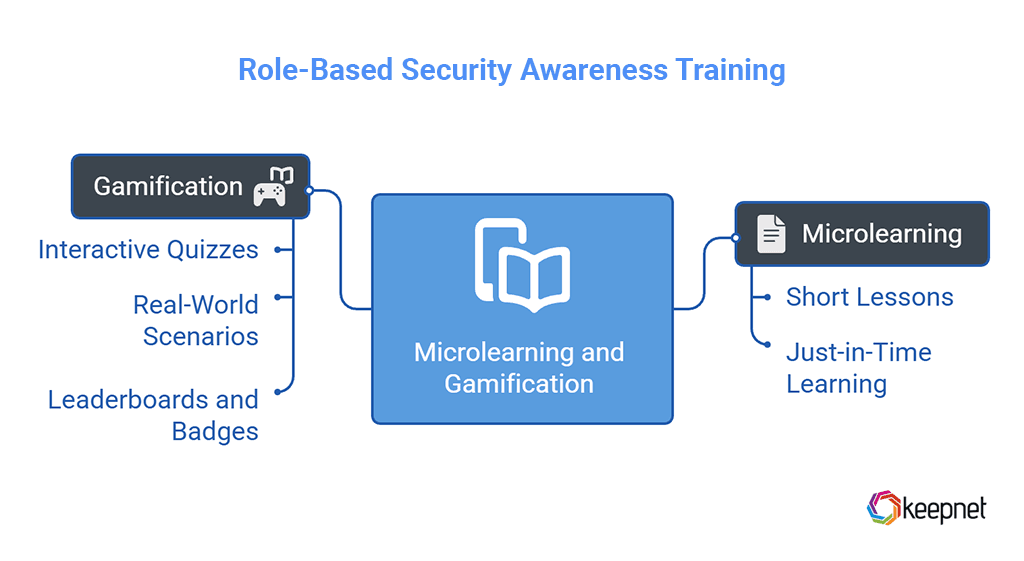
This approach supports just-in-time learning, allowing users to retain critical information without being overwhelmed. To enhance retention and motivation, these lessons should be paired with gamified elements such as:
- Interactive quizzes that reinforce key concepts immediately.
- Real-world scenarios that let users practice decision-making in safe environments.
- Leaderboards and achievement badges to encourage healthy competition and recognize progress.
Together, microlearning and gamification turn security training from a chore into an engaging, ongoing experience—boosting participation and reinforcing long-term behavioral change.
4. Scheduled Simulation Refreshes
Attackers constantly change their tactics—training must do the same. Scheduled simulation refreshes ensure that phishing tests and awareness content stay aligned with the latest threat trends. Whether it’s a new quishing technique or a trending callback scam, simulations should be updated quarterly or monthly to stay relevant.
This not only helps employees recognize current attack patterns, but also prevents training fatigue by keeping content fresh and challenging. Regular updates also provide security teams with a more accurate view of evolving user behavior.
5. Role-Based and Contextual Paths
Effective security awareness training must reflect the real threats faced by specific job roles. In 2026, attackers often tailor their methods based on departmental responsibilities—so training must do the same.
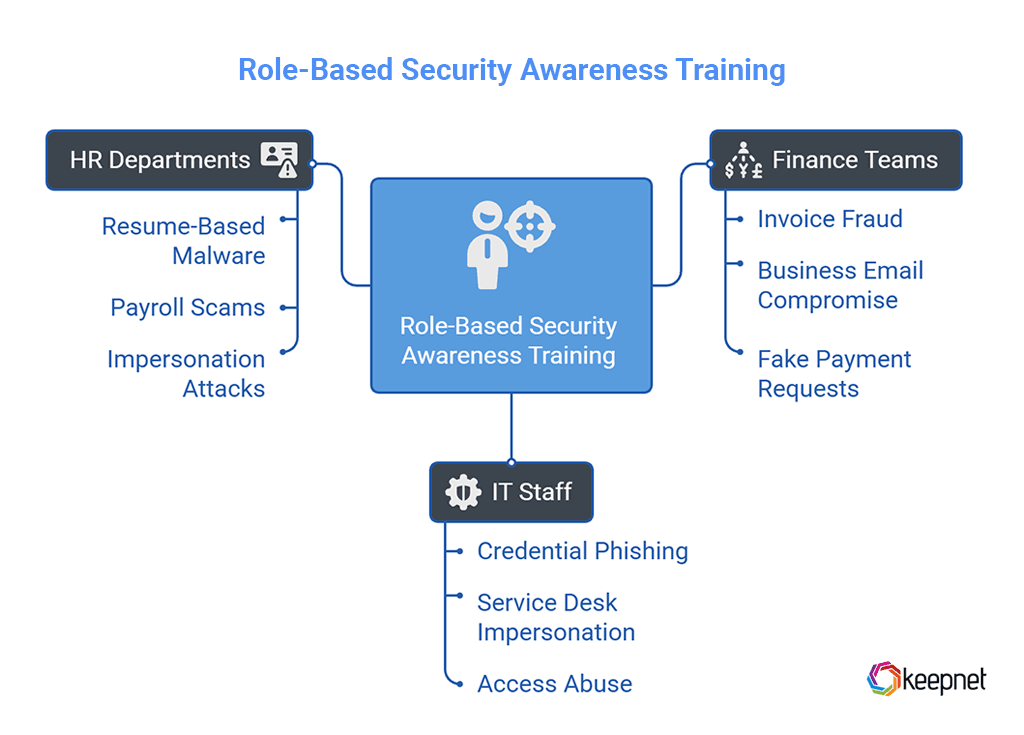
Role-based security awareness training provides users with simulations and scenarios directly relevant to their daily tasks and responsibilities. For example:
- Finance teams need simulations focused on invoice fraud, business email compromise (BEC), and fake payment requests.
- IT staff should train against credential phishing, service desk impersonation, and access abuse.
- HR departments must be prepared for resume-based malware, payroll scams, and impersonation attacks.
By aligning content with departmental risk profiles, employees are more likely to recognize and respond to threats that genuinely target their workflows. This targeted approach increases engagement, retention, and ultimately reduces the organization’s overall attack surface.
6. Behavior-Driven Insights
The goal isn’t just awareness—it’s measurable behavior change. By integrating behavioral analytics into training, organizations can monitor how users respond and adapt over time. Key elements include:
- Human Risk Scores based on real user interactions.
- Tracking repeat offenders who consistently fail simulations.
- Personalized learning paths that target specific weaknesses.
This data-driven approach helps security teams identify high-risk users, tailor interventions, and continuously optimize training effectiveness—ensuring the program evolves with the workforce.
Keepnet Security Awareness Training: Scalable, Intelligent, Proven
Keepnet’s security awareness training is built around real-life breach examples and role-based learning, ensuring every employee gets relevant, impactful education tailored to their risks.
Key features include:
- Real Breach Stories: 90-second videos based on actual incidents, helping employees understand how attacks really happen.
- Role-Based Training: Customized learning paths for departments like Finance, HR, and IT, reflecting their unique threat exposures.
- Personalized Learning Paths: Training adapts to user behavior, targeting specific weaknesses and reducing risk over time.
- Nudges for Retention: Engaging posters, screensavers, and infographics highlight key security practices, making it easier for employees to remember and apply them consistently.
- Gamified Elements: Quizzes, badges, and leaderboards that drive participation and make learning more interactive.
- Behavioral Science Methods: Built-in learning techniques proven to improve retention and support long-term behavior change.
Explore Keepnet Security Awareness Training to operationalize breach-based, role-specific campaigns with measurable behavior change.
Further Reading (Recommended Next Steps)
- How to choose a security awareness training tool (evaluation checklist)
- How to measure whether training is working (metrics that prove behavior change)
- Why behavior-change programs outperform “annual compliance” (behavioral science approach)
- Benchmarks to set expectations and justify budget (latest training statistics)
Editor's note: This blog was updated on January 2, 2026.