Insights from Magic Quadrant for Email Security 2025
This guide unpacks Magic Quadrant for Email Security 2025, explains what the report covers, and shows how to use its findings to choose the right email security platform and human risk programme.
Email is still the easiest way attackers get into organisations. In 2025, phishing, business email compromise (BEC), account takeover and data loss are all evolving with AI-generated content, deepfake-enhanced social engineering and multi-channel campaigns that blend email, SMS, voice and collaboration apps.
Analyst research like the Email security Gartner Magic Quadrant helps security leaders understand which vendors are serious players in this fast-moving market and how their strategies compare.
The Gartner Magic Quadrant for Email security 2025 is especially important because it reflects this new reality: cloud-first infrastructure, API-driven integrations, AI-enabled detection, and the need to keep total cost of ownership under control.
In this article, we’ll discuss following
- A clear explanation of what the report actually is
- Why it matters in 2025
- How Gartner evaluates vendors, key trends, how to read the chart, and how to use it in your own decision-making
What is the Magic quadrant for email security?
The Magic quadrant for email security is Gartner’s visual way of mapping email security vendors based on two axes: ability to execute and completeness of vision. Each vendor is a dot on the chart, and the chart is divided into four quadrants:
- Leaders – strong execution and strong vision
- Challengers – strong execution but a more limited or focused vision
- Visionaries – innovative vision but still building execution strength
- Niche Players – focused solutions that may excel in certain segments or regions
To be included, a platform must primarily protect organisational email infrastructure against threats such as phishing, malware, spam and business email compromise.
Most of the evaluated products also include related capabilities like data loss prevention (DLP), encryption, account takeover detection, threat intelligence, and sometimes optional awareness training or phishing simulation.
The report itself usually contains:
- A narrative description of the market
- A methodology explaining how vendors are assessed
- A one-page quadrant graphic
- Detailed strengths and cautions for each vendor
Think of it as a structured market map, not a “best product” list.
Why MagicQuadrant for Email Security matters in 2025
In 2025, the email security landscape is more complex than ever:
- Attackers use AI to generate highly convincing messages that are hard to spot with traditional rules or signatures.
- Organisations rely heavily on cloud suites like Microsoft 365 and Google Workspace, which already include some native email protection.
- Collaboration platforms (Teams, Slack, SharePoint, OneDrive, Dropbox, Salesforce) are now part of the attack surface.
- Security teams are under pressure to do more with less, so automation and integration really matter.
Against this backdrop, the MagicQuadrant for Email Security matters because it:
1. Shows which vendors can scale
It highlights who has the operational maturity, customer base and global reach to support mid-market and enterprise customers.
2. Reveals strategic direction
The positions and write-ups show which vendors are leading on AI detection, collaboration security, automation and data protection – and which are following.
3. Helps you build a realistic shortlist
Instead of starting from a random Google search or a cold sales email, you can start with a set of vendors that have been evaluated against the same criteria.
4. Frames internal discussions
CISOs, Heads of IT and procurement teams can use the report as a common reference point when discussing budget, roadmap and ri
Used properly, the report becomes a decision-support tool rather than just a marketing logo.
How Gartner evaluates email security vendors in the 2025 report
The 2025 report doesn’t only look at features. It evaluates vendors across two broad dimensions:
Ability to execute
This includes:
- Quality and reliability of the product
- Customer experience and support
- Sales and marketing execution
- Operational performance and financial stability
A vendor with strong execution is one you can expect to deliver consistently, scale with you, and provide reliable support.
Completeness of vision
This covers:
- Understanding of customer needs and market direction
- Innovation in areas like AI, behavioural detection and collaboration security
- Quality of the product roadmap
- Business model and go-to-market strategy
A vendor with strong vision is looking ahead: not just solving today’s spam problem, but preparing for tomorrow’s AI-driven cyber attacks.
By combining these two dimensions, Gartner positions vendors where their current strength and future plans intersect.
When you compare this with your own roadmap – for example, your move to fully cloud-native, or your plan to tighten integration with identity and XDR – you can see which strategies line up with yours.
Key themes and trends in the 2025 email security report
While the exact wording is analyst-specific, several themes consistently stand out in the 2025 email security landscape:
1. Convergence of SEG and ICES
The old divide between secure email gateways (SEG) and integrated cloud email security (ICES) is disappearing.
Gateway vendors now often support API-based deployment, while API-first vendors provide pre-delivery controls via mail-flow rules or MX records.
The real question becomes: how well can a platform protect you before, during and after delivery, regardless of where it sits in the flow.
2. Expansion into collaboration and SaaS
The report emphasises that email is no longer an isolated channel. Leading vendors protect:
- Collaboration tools (Teams, Slack, etc.)
- File-sharing platforms (SharePoint, OneDrive, Dropbox)
- Potentially CRM and other SaaS applications
Attackers follow people, not just email. So your email security platform increasingly needs to see and control what happens around the inbox too.
3. AI, language and behaviour-aware detection
Because phishing campaigns are now often AI-assisted, detection has to be smarter than simple URL reputation and attachment scanning. The report pays close attention to:
- Use of language models and semantic analysis
- Behavioural baselines and social-graph analysis
- Detection of “no-payload” social-engineering attacks, like invoice fraud or payroll redirection
- Automated triage, enrichment and remediation
This is where a lot of innovation is happening – and where differences between vendors really stand out.
4. Focus on misdirected mail and data protection
Many incidents aren’t caused by attackers at all, but by human error: sending sensitive data to the wrong person, attaching the wrong file, or forwarding information outside the company. Modern platforms increasingly build in:
Misdirected recipient detection
DLP policies and templates
Easy encryption and secure sharing options
These capabilities sit alongside traditional inbound threat protection.
How to read the quadrant chart without being misled
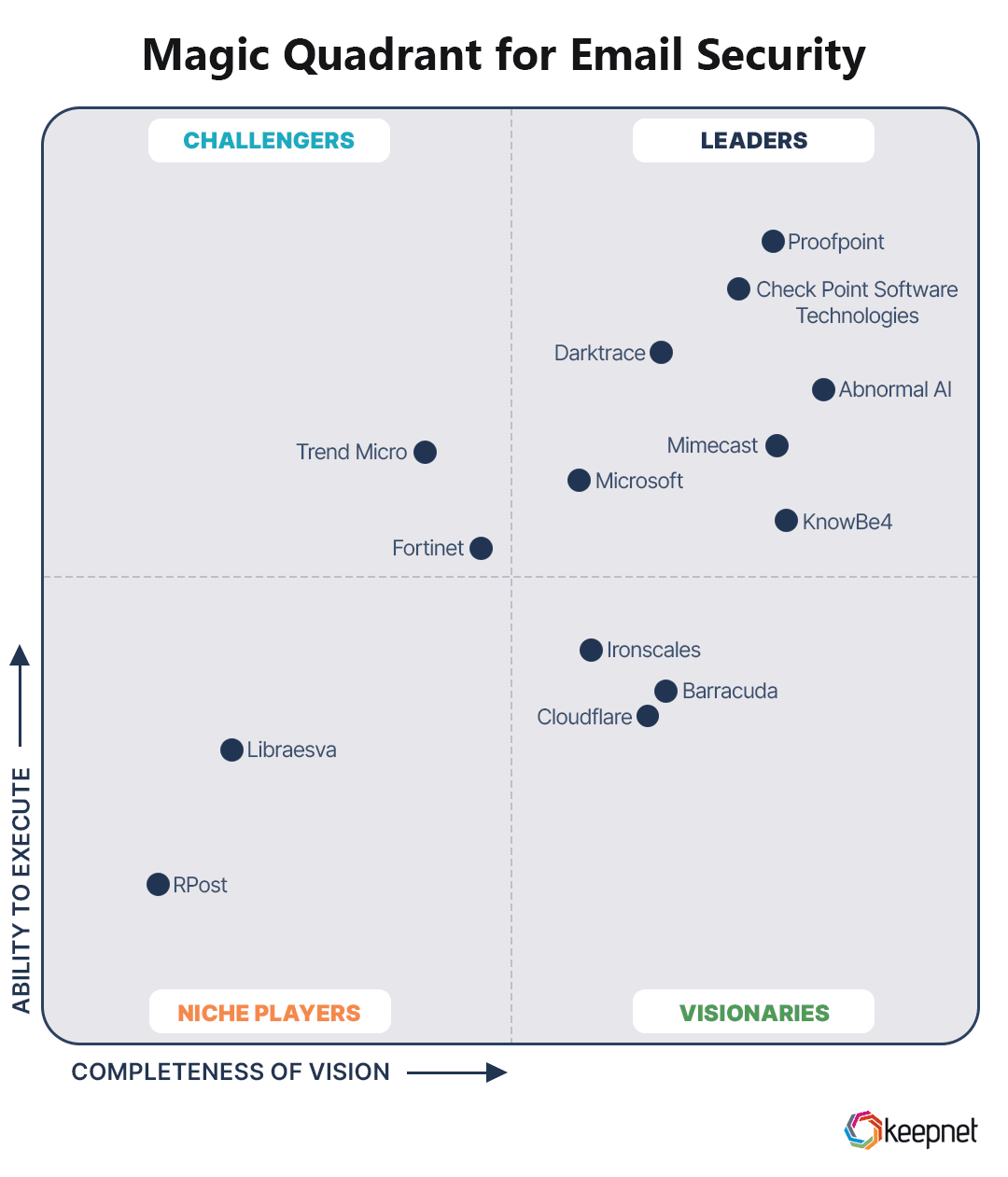
The famous graphic is powerful but easy to misinterpret. Here’s how to read it.
1. Don’t treat Leaders as automatically “the best”
Leaders often have broad platforms and strong execution, but they may be tuned for very large enterprises or specific verticals.
2. Pay attention to the narrative
The vendor write-ups explain why each dot is where it is. That context is more important than the dot alone.
3. Look for alignment, not hype
A vendor in the Visionary or Challenger quadrant may align better with your architecture, region or budget than a big-name Leader.
4. Separate report facts from vendor marketing
When you search for terms like Proofpoint Gartner Magic Quadrant, you’ll mostly land on vendor-run landing pages and campaigns. Those can be useful, but they are marketing narratives built on top of the independent research.
5. Remember your own requirements
The report doesn’t know your identity stack, your ticketing system, your local regulations, or your internal skills. You do.
The quadrant is most helpful when you see it as a map you overlay on your own environment, not a ranking to follow blindly.
How search behaviour and “Top lists” intersect with the report
Many buyers still start their journey in a very human way: they type something like Best email security solutions Gartner into Google, or look for articles promising the Top 10 email security solutions.
These list-style pieces can be a handy starting point, but they usually serve as high-level overviews or lead-generation content.
Here’s how to use them wisely:
- Take note of vendor names that appear repeatedly across lists and the quadrant.
- Use them as input to your shortlist, not the shortlist itself.
- Prioritise official research and hands-on testing when it’s time to make a final decision.
You’ll also find that Gartner publishes many quadrants across different domains – from access management to SIEM and more.
Collectively, these Gartner email Magic Quadrant and related reports help you design an overall architecture where email security, endpoint, identity and analytics reinforce each other.
Using the 2025 report in your vendor shortlist and evaluation
Here’s a practical way to turn the report into an actionable evaluation process:
Step 1 – Define your baseline
Document your needs clearly:
- Cloud provider (Microsoft 365, Google Workspace, hybrid)
- Regions and data residency constraints
- Regulatory obligations (GDPR, sector-specific rules, etc.)
- Collaboration tools and SaaS you must protect
- Integration points (SIEM, SOAR, XDR, ticketing, identity)
- Budget and internal skill level
Step 2 – Cross-reference with the report
Use the quadrant to pick vendors that:
- Match your scale and industry
- Support your cloud platform and collaboration stack
- Have a roadmap that aligns with AI and behavioural detection
Also keep an eye on older references like email security gartner magic quadrant, which may still appear in search and give historical context about the move from appliance/gateway-centric models to fully cloud-native platforms.
Step 3 – Run structured proof-of-concept tests
Invite 2–4 vendors from your shortlist and run side-by-side evaluations. Measure:
- Detection of real phishing, BEC and supplier fraud attempts hitting your mailboxes
- False positives, time-to-detect and time-to-remediate
- Analyst workload (how much manual triage is needed)
- End-user experience and user-reporting workflows
Step 4 – Combine platform and human risk management
No matter which platform you choose, people remain your last line of defence. This is where a Human Risk Management Platform, along with Security Awareness Training and a multi-channel Phishing Simulator, becomes essential. For example:
- Use simulations (email phishing simulation, vishing simulation, SMS phishing simulation, QR phishing simulation, MFA phishing simulation and Deepfake simulation) to mirror real attacker behaviour.
- Provide short, role-specific training to high-risk groups like finance or executives.
- Feed real incident data into your training programme so employees see relevant examples.
Keepnet’s Human Risk Management capabilities are built to fit this layer: tightly integrated training, behaviour analytics and simulations designed to sit alongside whichever email security platform you choose.
Limitations of relying only on the MagicQuadrant for Email Security
Finally, it’s important to be honest about what the report can’t do:
- It can’t see your internal politics, budget battles or change-management challenges.
- It can’t evaluate how well a vendor’s UI fits your team’s workflow.
- It can’t predict how responsive a support team will be to your particular tickets.
- It can’t replace real-world testing and user feedback.
Treat the report as a powerful, but partial, lens. Combine it with:
- Independent tests or benchmarks
- Peer reviews and reference calls
- Your own proof-of-concept results
- A clear vision for human risk and culture change
That’s how you turn “quadrant reading” into real-world risk reduction.