Military Cyber Security Training Guide
Discover how modern military cyber security training uses AI simulations, human risk scoring, and real-time threat intelligence to defend against evolving cyber threats.
Cyberattacks targeting military systems are evolving rapidly, threatening communications, mission-critical infrastructure, and classified data across armed forces. Sophisticated threats like phishing, ransomware, insider breaches, and AI-driven cyberattacks increasingly bypass traditional defenses, creating serious operational risks.
Here are 5 key statistics highlighting the importance of military cyber security awareness training in preventing breaches, reducing risks, and protecting national security:
- Approximately 95% of cybersecurity breaches are caused by human error, such as phishing or misconfigurations, making targeted awareness training essential for military personnel to mitigate these vulnerabilities and safeguard sensitive operations.
- Organizations implementing effective security awareness training experience up to a 70% reduction in security-related risks, which is critical in military contexts where breaches can compromise missions and lead to catastrophic consequences.
- 93% of cybersecurity experts emphasize that combining human-focused training with technology is vital for detecting and responding to threats, underscoring the need for ongoing education in the military to address evolving cyber adversaries.
- Just 90 days of consistent awareness training can reduce phishing susceptibility by over 40%, a key benefit for military forces where social engineering attacks often target personnel handling classified information.
Despite rising investments, outdated training approaches—centered around passive learning and annual checklists—fail to prepare personnel for modern cyber threats. Effective military cyber security training must prioritize real-world attack simulations, human risk management, and proactive incident response.
In this blog, we will explore the essential components of building resilient cyber security capabilities within military organizations using cybersecurity training and how Keepnet’s human risk management solutions enable defense teams to stay ahead of evolving threats.
What is Military Cyber Security Awareness Training?
Military Cyber Security Awareness Training is all about making sure everyone in uniform—or working around classified systems—knows how to spot and stop cyber threats before they cause real damage. It’s not just IT teams or intelligence officers who need it—every soldier, civilian, and contractor with access to military networks has a role to play.
This kind of training goes way beyond typical office cybersecurity videos. It’s designed for real-world threats—things like phishing emails that look like they’re from your commanding officer, social engineering aimed at gathering troop movements, or malware hidden in a fake logistics document.
The Rising Cyber Threats Targeting Military Forces
Military forces are now prime targets for cyberattacks designed to disrupt operations, steal classified information, and weaken national security. These threats are faster, more targeted, and often state-sponsored.
AI-driven phishing, deepfake impersonations, and quantum computing risks are reshaping military cyber defense. These methods bypass traditional security, exploiting both human and technical vulnerabilities.
Cyberattacks have become a serious and growing risk to the military’s ability to stay prepared and execute missions. They can shut down supply chains, disrupt communications, and cut off critical resources like fuel and power.
As John Garstka, Director for Cyber Warfare at the Pentagon, explained, adversaries are increasingly targeting the defense industrial base — the factories and companies building military equipment. Disrupting production lines could leave forces without the tools needed for missions, putting national security at serious risk (Source).
To counter these threats, military organizations must move beyond static defenses with simulation-based training, proactive strategies, and full-system risk assessments.
To understand how improving cyber awareness strengthens defenses and reduces operational risks, explore Keepnet’s article on How Security Awareness Training Reduces the Risk of Data Breaches and Security Incidents.
Why Traditional Cyber Security Training Fails
Traditional cyber security training often relies on outdated methods such as annual presentations, passive e-learning, and checklist-based compliance exercises. While these approaches may meet regulatory requirements, they fail to build the real-world skills needed to face today’s complex cyber threats.
Modern threats like AI-driven phishing, ransomware, and social engineering no longer follow predictable patterns. These attacks force quick decisions under pressure, exploiting human behavior as much as technical weaknesses. Traditional training, focused mainly on technical threats, leaves military personnel unprepared to respond effectively during real-world cyber incidents.
Another major flaw is the lack of ongoing risk assessment. Traditional programs treat all users the same, ignoring individual risk profiles and evolving threat landscapes. Without adaptive, role-specific training and continuous testing, critical gaps in awareness and readiness persist. Adversaries increasingly exploit both technical and human vulnerabilities, making static training models ineffective. Military organizations must adopt dynamic, simulation-based programs focused on real-world attack scenarios, individual risk management, and continuous skill development.
To dive deeper into why traditional security awareness approaches fall short, also review Keepnet’s article on Why Traditional Security Awareness Training Is Inadequate.
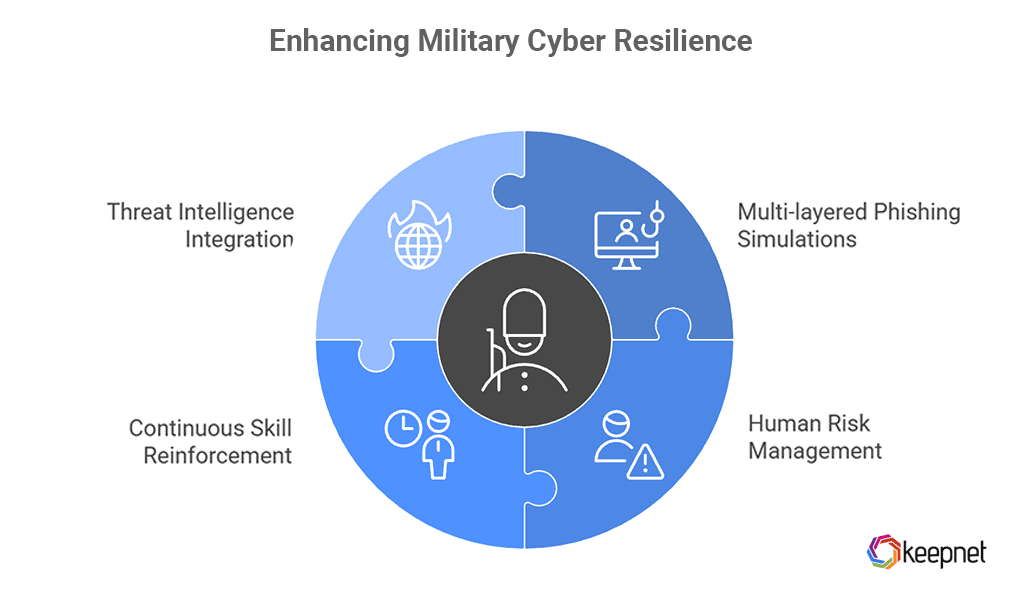
Core Elements of Effective Military Cyber Security Training
Building strong cyber resilience within military forces requires training that develops the practical skills needed to recognize, respond to, and recover from real-world cyberattacks. Programs must replicate the speed, unpredictability, and pressure of modern threats, strengthening decision-making under stress, addressing human vulnerabilities, and reinforcing operational readiness through continuous, adaptive learning.
Multi-layered Phishing Simulations
Training must include hands-on simulations of phishing, vishing, smishing, quishing, and ransomware attacks. By exposing personnel to real-world tactics in a controlled environment, simulations build practical recognition and response skills essential for high-pressure situations.
To experience how simulation-based learning strengthens defense capabilities, military teams can try Keepnet’s Free Phishing Simulation Test.
Human Risk Management
Effective cyber security training must move beyond general awareness and address individual risk levels within military units. Human risk scoring helps identify personnel who are more susceptible to cyber threats based on behavior patterns, past actions, and role-specific vulnerabilities. By analyzing these risk profiles, training programs can tailor content, frequency, and intensity to focus on the highest-risk individuals, turning potential weak points into strong defenders.
To learn more about how human risk scoring strengthens cyber resilience, explore Keepnet’s article on What is Human Risk Score and How Does It Help Prevent Cybersecurity Incidents?.
Continuous Skill Reinforcement
Effective cyber training must mirror the pace and pressure of real-world threats. It requires ongoing, hands-on exercises that test decision-making under stress, expose gaps in knowledge, and adapt to evolving attack methods. Regular phishing simulations, targeted awareness training, and incident response drills ensure that military personnel build not just knowledge, but readiness and resilience. Training must evolve continuously, matching both the sophistication of adversaries and the specific risk profiles within the organization.
In addition to structured exercises, behavior-based nudges — small, timely prompts delivered at critical moments — are essential for reinforcing secure habits without overwhelming users. When customized to specific roles and risk levels, nudges help integrate cybersecurity best practices into daily operations, strengthening long-term behavior change.
For more insights into how nudges can enhance military cyber resilience, explore Keepnet’s guide on Customizing Nudges for Specific Roles in Security Behavior and Culture Programs.
Threat Intelligence Integration
Effective military cyber training must be based on real, up-to-date threat intelligence, not outdated attack scenarios. Integrating live data into exercises keeps personnel alert to evolving adversary tactics, techniques, and procedures, ensuring that training remains relevant and operationally effective.
Keepnet’s Threat Intelligence platform helps organizations quickly identify if employee data has been exposed in breaches, providing critical details such as breach timelines, compromised email addresses, and affected data types.
Alongside this, Threat Sharing enables military teams to securely exchange intelligence about new email threats, vulnerabilities, and threat actors within trusted communities, strengthening collective defense and accelerating response efforts.
Addressing the Human Factor in Military Cyber Security
Technology alone cannot secure military operations against cyber threats. Human behavior remains a critical vulnerability, as attackers increasingly exploit mistakes, misjudgments, and lapses in security awareness to breach sensitive systems. In the 2025 Verizon Data Breach Investigations Report (DBIR), 60% of breaches were attributed to human error, including misconfigurations, misuse, and social engineering — highlighting the urgent need to strengthen the human element in cybersecurity.
Effective cyber defense must go beyond technical measures. Military personnel need the skills to detect social engineering tactics, respond decisively under pressure, and instinctively apply security protocols during critical situations. This requires ongoing, role-specific training that adapts to individual risk profiles and evolves with the threat landscape.
Programs that combine realistic threat simulations, continuous behavioral reinforcement, and personalized risk assessments are essential to minimizing human error. Building cyber resilience within military teams means transforming personnel from potential vulnerabilities into proactive defenders of mission-critical operations.
The Role of AI in Military Cyber Security Training
Artificial intelligence (AI) is reshaping military cyber security training. AI-driven tools create adaptive attack simulations that adjust based on user behavior, making exercises more realistic and challenging than static programs.
AI also personalizes training by analyzing individual performance, identifying weaknesses, and delivering targeted content to improve skills and reduce training fatigue.
By simulating unexpected attack behaviors and real-time threat changes, AI trains personnel to recognize patterns quickly, assess risks under pressure, and respond decisively during live cyber incidents.
Integrating AI into cyber training keeps military teams agile, threat-ready, and aligned with evolving adversary tactics.
For more insights, explore Keepnet’s article on Leading GenAI Security: What CISOs Need to Know.
Key Topics of Military Cyber Security Awareness Training
Military cyber awareness programs are designed to build a strong human firewall across all ranks and roles. These trainings combine real-world threat scenarios with operational protocols to help personnel recognize and respond to digital risks that could compromise missions or national defense. Below are the core topics typically covered.
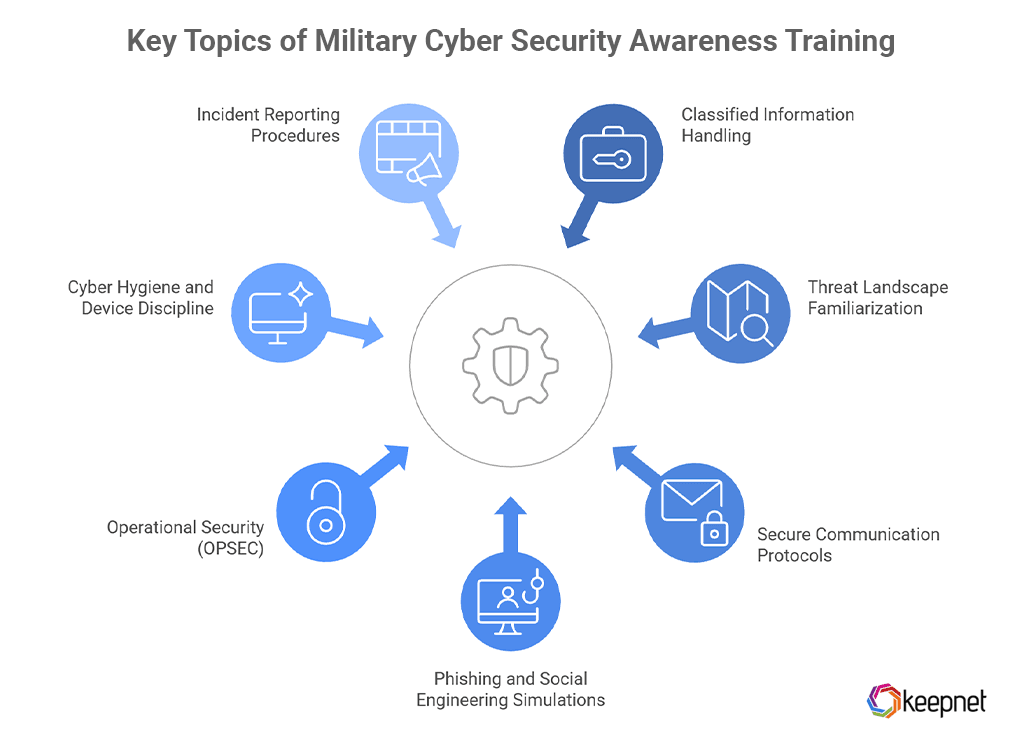
1. Classified Information Handling
Personnel are trained on handling, transmitting, and disposing of classified and sensitive data (e.g., SIPRNet, JWICS) in line with military-specific regulations like DoD 5220.22-M and NIST SP 800-171.
2. Threat Landscape Familiarization
The training focuses on advanced persistent threats (APTs), insider threats, foreign intelligence services, and tactics used by nation-state actors targeting military assets.
3. Secure Communication Protocols
Service members are instructed on how to use encrypted messaging systems, secure voice channels, and official networks—and the consequences of unauthorized apps or shadow IT.
4. Phishing and Social Engineering Simulations
Interactive exercises simulate phishing attacks, credential harvesting, and voice impersonation scenarios tailored to military contexts—such as fake chain-of-command emails or base-specific alerts.
5. Operational Security (OPSEC)
OPSEC training emphasizes minimizing digital footprints, securing social media use, and not disclosing unit locations, movements, or deployments, even unintentionally.
6. Cyber Hygiene and Device Discipline
This includes multi-factor authentication (MFA), USB restrictions, software patching, and the use of approved devices under military endpoint protection policies.
7. Incident Reporting Procedures
Service members are taught how and when to escalate suspicious activity using DoD-specific reporting channels like AR 25-2, DISA reporting, or the Cyber Command Watch Floor.
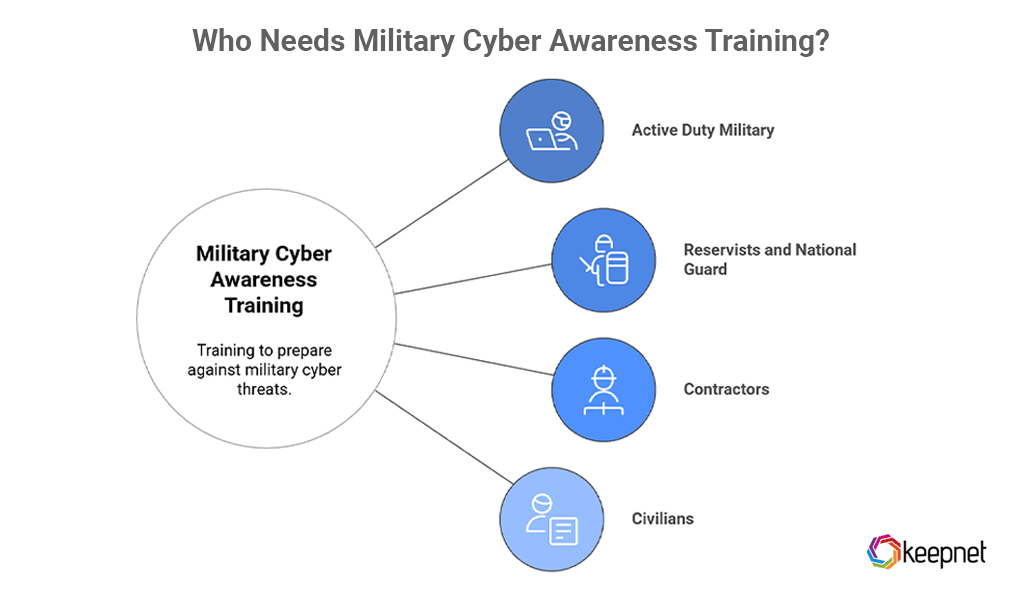
Who Needs Military Cyber Awareness Training?
Cyber threats don’t discriminate by rank or role. Whether you’re on active duty, part of a reserve unit, supporting operations as a contractor, or working in a civilian capacity with access to military networks, you’re a potential target—and a critical line of defense. This training ensures everyone is prepared to spot and stop cyber threats before they cause harm.
- Active duty military
- Reservists and National Guard
- Contractors working on DoD systems
- Civilians with access to defense networks or data
How Keepnet Enhances Military Cyber Security Training
Strengthening cyber resilience in military forces requires a targeted, adaptable approach. Keepnet’s Extended Human Risk Management platform combines personalized education, realistic attack simulations, and rapid threat response to close human and technical security gaps.
Through Role-Based Security Awareness Training, military teams access over 2,100 training materials from 15+ providers in 36+ languages, tailored by role, risk level, and operational need. This ensures personnel build the skills most relevant to their missions, across diverse and multilingual units.
Keepnet’s AI-powered Phishing Simulator delivers realistic, behavior-specific phishing campaigns using over 6,000 templates. It mirrors real-world tactics, filters out false clicks from sandbox tools, and provides accurate reporting—giving leadership a clear view of cyber readiness across all units.
The Incident Responder tool enables military cybersecurity teams to analyze, investigate, and neutralize email threats 48.6 times faster than traditional methods. Automated detection and containment workflows minimize risks before they impact operations.
Securing the Future of Military Operations with Keepnet Extended Human Risk Management
As cyber threats grow in speed, complexity, and precision, military organizations must rethink their approach to cyber security training.
Investing in advanced human risk management strategies, real-time threat intelligence, and AI-powered training tools is no longer optional—it is essential for protecting mission-critical operations and maintaining operational readiness. Organizations that strengthen both their technology and their workforce will be best positioned to counter evolving adversary tactics.
To start building a stronger cyber defense culture within your organization, explore Keepnet’s Security Awareness Training software— designed to help teams recognize threats faster, reduce risk, and improve overall resilience.
Editor's note: This article was updated January 9, 2026.