250+ Phishing Statistics and Trends You Must Know in 2026
Phishing is evolving, with billions of emails sent daily and businesses increasingly targeted by AI-powered attacks. Discover the top 2026 phishing statistics and trends to protect your organization from data breaches, spear-phishing, and ransomware.
Phishing statistics in 2026 show that phishing is still one of the most successful cyber-attack methods against businesses and individuals.
With phishing emails driving a large share of modern data breaches, security teams need clear, up-to-date numbers to understand how big the problem really is.
In this guide, we break down the latest phishing statistics and phishing trends for 2026, so you can see how attackers are evolving and what your organization should do to stay ahead.
Key Phishing Trends in 2026
- AI's Impact: AI is dramatically increasing success rates, with click rates up to 4x higher than traditional methods. A 2025 report noted a 400% rise in successful phishing scams due to AI tools.
- Training Reduces Success: Organizations with ongoing training see click rates drop to as low as 1.5%, and reporting rates increase (e.g., 21% report suspicious emails with recent training vs. 5% without).
- Average Costs: Successful phishing breaches cost ~$4.8 million on average and take 254 days to detect/contain.
- Trends for 2026: Expect higher rates due to multi-channel attacks (e.g., SMS, QR codes) and AI, with phishing in 57% of social engineering incidents.
Free Deepfake Phishing Simulation
One-time, zero-cost deepfake simulation
Key Phishing Statistics in 2026

Phishing remains a primary attack method, as most cyberattacks begin with a phishing email.
57% of organizations face phishing scams weekly or daily. Nearly 1.2% of all emails sent are malicious, accounting for 3.4 billion phishing emails daily.
Human error continues to play a significant role, contributing to 60% of security breaches, according to the Verizon Data Breach Investigations Report (DBIR) 2025.
Meanwhile, CSO Online reports that 80% of security incidents are attributed to phishing, with losses totaling $17,700 every minute due to these attacks.
Phishing Trends in 2026
As phishing tactics become more sophisticated, several key phishing trends have emerged in 2025:
- Targeting Financial Institutions: APWG reports that 23% of phishing attacks in Q2 2023 were aimed at financial institutions, with social media platforms and SaaS companies accounting for 22.3% each.
- Deceptive Links Dominate: Cloudflare reports that deceptive links were the most common phishing method, making up 36% of phishing threats from their analysis of 13 billion emails.
- Brand Impersonation: Attackers frequently impersonate popular brands like Microsoft, Google, and Amazon. According to Cloudflare’s phishing stats, 51.7% of malicious emails were disguised as communications from these companies.
- AI-Driven Phishing: AI-powered phishing attacks are harder to detect as attackers use AI to craft human-like messages. Zscaler ThreatLabs indicates that this trend is on the rise, making it harder for conventional security measures to block these attacks.
- Ransomware via Phishing: 35% of ransomware attacks are initiated through phishing emails, showing how critical email security has become in mitigating ransomware attacks.
- AI-Powered Email Scams: Attackers now use AI chatbots to generate typo-free and convincing phishing emails, mimicking legitimate messages almost perfectly (Source).
- Abuse of Cloudflare Services: Hackers are misusing Cloudflare Workers and Pages to host phishing payloads, making the phishing emails appear more legitimate (Source).
- Smishing by Organized Groups: The “Smishing Triad” and similar threat actors have escalated global SMS phishing, using over 200,000 fraudulent domains (Source).
- Phishing as the Leading Ransomware Vector: 45% of ransomware infections now originate from phishing emails (Source).
- Hyper-Personalized AI Phishing: AI-driven scams now use publicly available personal data to craft emails that impersonate friends or family, deceiving even cautious users (Source).
- Quishing (QR Code Phishing) Proliferation: Malicious QR codes in emails, attachments, or physical spaces have risen by 25%, directing users to fake sites or malware downloads, with dynamic codes that evade static scans.
- Multi-Channel Phishing Expansion: Attacks now span beyond email to platforms like Slack, Teams, social media, and even phone/video calls, with 40% of campaigns using these to build trust and urgency. (Note: This builds on your Smishing but adds non-SMS channels.)
- Targeted Sector-Specific Scams: Education sees a 224% surge in attacks exploiting academic timelines, while engineering roles (64% of hiring-related phishing) and cryptocurrency users face fake wallets and job scams. (Note: Expands beyond your financial/SaaS focus.)
- Credential Harvesting Dominance: About 80% of campaigns focus on stealing logins for cloud services like Microsoft 365, using realistic fake pages and multi-channel tactics like password recovery lures.
- Use of Compromised Accounts: A 57.9% rise in attacks originating from hijacked legitimate accounts, including supply chain sources, to bypass filters and enhance credibility.
- Voice Phishing (Vishing) and Deepfakes: Vishing incidents affect 30% of organizations, amplified by AI deepfakes and voice cloning for impersonating executives or officials, up 15%.
- Evasion of Security Controls: 80% of phishing sites use HTTPS, combined with AI obfuscation like invisible characters and redirects, leading to a 47.3% increase in bypassing email gateways.
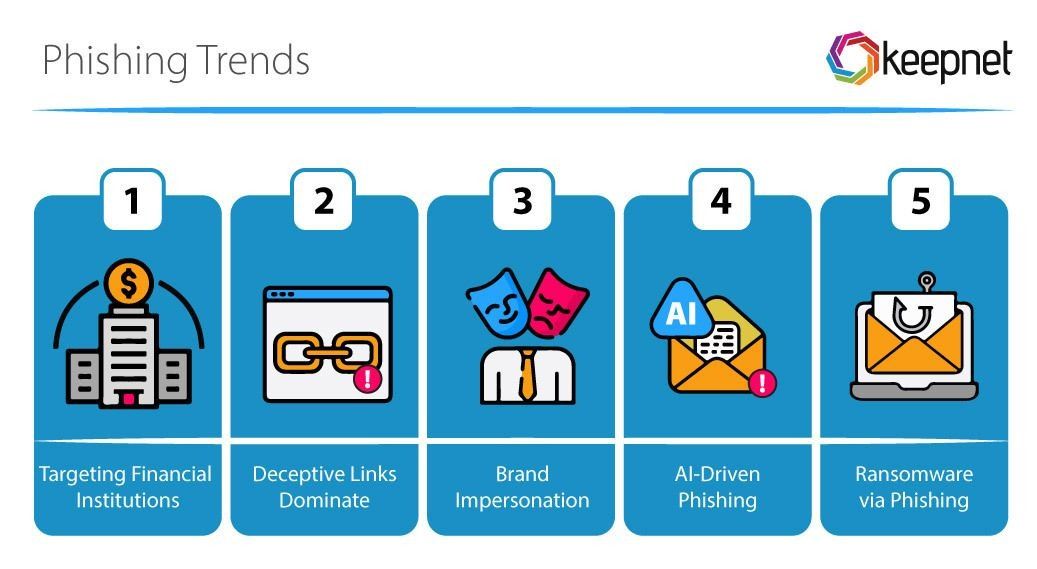
The 2026 phishing trends reveal attackers are more sophisticated, leveraging AI, multi-channel tactics, and real-time personalization. Current phishing facts and phishing statistics show deceptive links, brand impersonation, and ransomware-triggered phishing are on the rise, with threats expanding beyond email to SMS, voice, and collaboration tools. By tracking key phishing stats and implementing adaptive, multi-layered defenses, organizations can stay ahead of these evolving threats.
Current Phishing Statistics Insights [Updated January 2026]
![Current Phishing Statistics Insights [Updated November 2025]](https://timely-benefit-e63d540317.media.strapiapp.com/Current_Phishing_Statistics_Insights_Updated_November_2025_35a721b3c4.png)
In 2026, phishing remains one of the most dangerous and widespread cyber threats. Many of the biggest cyber attacks in history involved phishing as a key entry point. From traditional email-based attacks to more sophisticated methods like voice phishing (vishing) and SMS phishing (smishing), organizations across all industries are struggling to defend against these constantly evolving tactics.
Phishing Attack Statistics by Volume and Frequency

Phishing isn’t slowing down. Attackers now mix email, SMS, voice, and QR to hit more people, more often. If you’re planning training and response capacity, it helps to know how many attempts typically happen and how frequently they spike.
Here are phishing attack statistics by volume and frequency:
- An estimated 3.4 billion phishing emails are sent daily, accounting for 1.2% of global email traffic.
- The Anti-Phishing Working Group (APWG) recorded 1,003,924 phishing attacks in Q1 2025, the highest since late 2023.
- Phishing attacks increased by 150% year-over-year from 2019 to 2022, with continued growth into 2025.
- In 2024, global phishing volume dropped by 20%, but targeted attacks rose, continuing into 2025.
- Google blocks approximately 100 million phishing emails daily.
- In Q1 2022, 45.56% of all emails sent globally were spam, a trend persisting into 2025.
- The Internet Crime Complaint Center (IC3) received 300,487 phishing reports in 2024, down from prior years but up 10x since 2018 (26,379 reports).
- Phishing sites increased from 110,554 in October 2019 to 1,023,579 in September 2024, an 11% rise from 2023.
- An estimated 1 in every 412 emails globally is a phishing attempt, based on analysis of 500 million emails.
- In 2021, 323,972 internet users fell victim to phishing attacks globally, a figure likely higher in 2025 due to increased digital reliance.
- In Q4 2022, APWG logged 1,350,037 phishing attacks, contributing to 4.7 million total attacks for the year.
- Phishing attacks doubled in frequency since the COVID-19 pandemic, per IMF data.
- In 2024, 1 in 5 emails globally (20%) contained some form of phishing or spam content.
- Over 1 billion emails were exposed in breaches in 2021, fueling phishing campaigns into 2025.
- In Q2 2022, 54% of phishing URLs used the ‘.com’ domain, a trend continuing into 2025.
- June 2021 saw the highest spam email rate at 48.03%, with November 2021 at 43.7%, patterns persisting in 2025.
- In 2024, phishing emails accounted for 1.2% of all global email traffic, equating to 4 billion daily phishing emails.
- The average click rate for phishing campaigns in 2021 was 17.8%, with targeted campaigns reaching 53.2%.
- In 2021, 16.5 leaked emails per 100 internet users fueled phishing databases, a trend ongoing in 2025.
- Phishing attacks targeting mobile devices increased by 25-40% compared to desktops in 2024, continuing into 2025.
Phishing Statistics by Financial and Economic Impact

Budgets feel the hit when phishing succeeds, lost funds, downtime, recovery costs, and long-tail expenses like higher cyber insurance and compliance penalties. Understanding the money side helps you justify investments in controls, training, and response.
Here are phishing statistics by financial and economic impact:
- The average cost of a phishing breach in 2024 was $4.88 million, up 9.7% from 2023.
- Phishing attacks cost businesses $200,000 on average in 2021, with larger enterprises losing millions.
- Individual victims in the U.S. reported $245 million in phishing losses in 2021, likely higher in 2025.
- In the U.K., phishing scams cost individuals £15.3 million between August 2021 and March 2022, up 24%.
- Business email compromise (BEC) attacks resulted in $1.8 billion in losses in 2020, with 2025 losses projected higher.
- A single whaling attack costs businesses $47 million on average.
- The global cost of phishing could reach $250 billion in 2024, up from $147 billion in 2021.
- Ransomware attacks, often initiated by phishing, cost $4.54 million on average to recover from.
- Phishing-related data breaches with 10 million exposed records cost $50 million on average.
- Breaches compromising 50 million records can cost up to $392 million.
- Phishing losses in 2024 totaled $53 million, per IC3 data.
- The average financial loss per phishing attack in 2021 was $136, with total losses of $44.2 million.
- Phishing breaches identified after 200 days cost $1.2 million more than those contained earlier.
- Social engineering breaches, including phishing, cost $4.77 million on average in 2024.
- BEC attacks averaged $150,000 in losses per incident in 2024.
- Phishing attacks result in $17,700 in losses every minute, per CSO Online.
- Small businesses lose $200,000 on average per successful phishing attack.
- The global cost of cybercrime, including phishing, is projected at $23 trillion by 2027.
- Organizations with extensive AI and automation save $2.22 million on average in breach costs.
- A fintech CFO lost $1.2M in 2024 due to a deepfake audio phishing attack.
Phishing Statistics by Industry-Specific Targeting

Different sectors attract different lures. Finance faces credential theft and wire fraud, healthcare gets data-exfiltration schemes, and retail sees payment and help-desk scams—because attackers mirror the workflows and vendors each industry relies on. Segmenting your risk and training by industry patterns makes defenses stick.
Here are phishing statistics by industry-specific targeting:
- Financial institutions faced 27.7% of phishing attacks globally in 2024.
- Software-as-a-Service (SaaS) industries saw 17.7% of phishing attacks in 2024.
- Social media platforms were targeted in 10.4% of phishing attacks in 2024.
- Logistics and shipping industries faced 9% of phishing attacks in 2024.
- Payment services were targeted in 6% of phishing attacks in 2024.
- eCommerce and retail saw 5.6% of phishing attacks in 2024.
- Telecom industries faced 3.1% of phishing attacks in 2024.
- Cryptocurrency platforms accounted for 2.3% of phishing attacks in 2024.
- In 2021, 40% of cyberattacks in manufacturing involved phishing.
- The finance industry saw 46% of cyberattacks involving phishing in 2021.
- Healthcare phishing attacks led to $10 million in recovery costs per ransomware incident in 2025.
- Over 68% of phishing breaches in small businesses (under 100 employees) started with a single untrained staff member.
- Government agencies faced spoofed inter-agency requests, with phishing affecting 42% of European organizations in 2021.
- In North America, 47% of cyberattacks in 2021 involved phishing.
- Latin American organizations saw 47% of cyberattacks involving phishing in 2021.
- Asian organizations reported phishing in 43% of attacks in 2021.
- In 2025, multiple U.S. hospital networks faced shutdowns due to phishing-triggered ransomware.
- Financial sector phishing often targets account managers with fake compliance alerts.
- Small businesses lack DMARC policies in 68% of cases, increasing phishing vulnerability.
- Enterprises face tailored phishing using stolen internal data from prior breaches.
Phishing Stats by Attack Methods and Tactics

Attackers constantly tweak the “how”: from credential-harvesting links and spoofed login pages to payload-less BEC, QR lures, MFA fatigue prompts, and even deepfake voice. Knowing which techniques dominate helps you prioritize controls, detections, and scenario-based training.
Here are phishing stats by attack methods and tactics:
- In 2021, 90% of phishing attacks via messaging apps used WhatsApp.
- Telegram accounted for 5.04% of messaging app phishing attacks in 2021.
- In Q1 2022, LinkedIn was the most imitated brand for phishing, at 52% of attacks.
- DHL was impersonated in 14% of phishing attacks in Q1 2022.
- Google was spoofed in 7% of phishing attacks in Q1 2022.
- Microsoft was targeted in 6% of phishing attacks in Q1 2022.
- FedEx was impersonated in 6% of phishing attacks in Q1 2022.
- Of credential phishing emails, 45% purported to be from Microsoft in 2021.
- Finance-themed phishing emails made up 17% of credential phishing in 2021.
- 9.3% of reported phishing messages in 2021 were malicious.
- Of malicious phishing messages, 38% contained only a URL, while 36% had attachments.
- Microsoft Office docs were used in 52% of phishing emails with malicious files.
- Compressed files accounted for 29% of malicious phishing attachments.
- Executable files were used in 12% of phishing emails with attachments.
- PDFs accounted for 7% of malicious phishing attachments.
- In 2021, 469 unique phishing kits were detected by Kaspersky.
- Kaspersky blocked 1.2 million phishing pages in 2021, a number likely higher in 2025.
- Spear phishing was used by 65% of known cybercriminal groups in 2019, a trend continuing.
- 96% of spear phishing attacks in 2019 aimed at intelligence gathering.
- In 2022, 33% of organizations reported a significant increase in phishing email volume.
- 92% of organizations in 2022 had at least one business email compromised.
- 93% of organizations in 2022 experienced data leaks due to phishing-related errors.
- In Q2 2022, Adobe was a top impersonated ‘.com’ domain in phishing URLs.
- Myportfolio was among the top spoofed ‘.com’ domains in Q2 2022.
- Backblazeb2 was a common spoofed domain in Q2 2022 phishing URLs.
- Weebly was frequently impersonated in Q2 2022 phishing campaigns.
- In 2021, ‘Agensla’ Trojans were the most prevalent malware in phishing emails.
- 68% of phishing websites in 2021 used typosquatting or compromised brand domains.
- In 2024, 159 million tech support and job scam phishing hits were recorded.
- Phishing emails mimicking IRS or tax agencies increased by 35% in 2024.
- Over 44,750 phishing attacks in 2024 targeted Facebook via domain spoofing.
- In 2022, ‘Payment invoice’ was a top phishing email subject line.
- ‘Update your invoice’ was a common phishing subject line in 2022.
- ‘Outstanding payment’ was frequently used in phishing email subjects in 2022.
- In 2021, 12% of phishing emails delivered malware directly.
- 6% of phishing emails in 2021 were BEC or CEO fraud attempts.
- In 2024, 64% of businesses reported facing BEC attacks.
- Wire transfer BEC attacks increased by 33% in Q1 2025 compared to Q4 2024.
- In Q1 2021, LinkedIn phishing emails had a 42% click rate, ahead of Facebook (20%) and Twitter (9%).
- In 2022, 96% of organizations reported at least one phishing attack.
Phishing Statistics by Victim Profiles and Susceptibility

Who gets phished—and why—often comes down to role, access level, and context in the moment. Clear patterns show up by department, seniority, workload, training recency, and even device/channel used. Use these signals to target controls, coaching, and just-in-time nudges where they’ll cut the most risk.
Here are phishing statistics by victim profiles and susceptibility:
- Millennials and Gen-Z (18-40) are most likely to fall for phishing, with a 23% victim rate.
- Generation X (41-55) has a 19% phishing victim rate.
- Ages 18-24 have a 12% phishing success rate due to overconfidence.
- Ages 25-44 face a 20% phishing success rate, the largest attack surface.
- Ages 45-64 have an 18% phishing success rate, less familiar with modern tactics.
- Ages 65+ have a 22% phishing success rate, the highest due to trust in authority.
- New hires are 44% more likely to fall for phishing in their first 90 days.
- Senior executives are 23% more likely to fall for AI-personalized attacks.
- Employees under tight deadlines are 3x more likely to click phishing emails.
- Mobile device users face 25-40% higher phishing success rates than desktop users.
- In 2024, a senior marketing executive’s credentials were stolen via a fake mobile Zoom invite.
- New starters on LinkedIn are key targets for impersonation scams.
- Employees in HR, payroll, and finance are high-value targets for BEC attacks.
- 80% of organizations in 2022 believed they were likely to face an email-based attack.
- In 2024, 52% of organizations reported phishing attacks as more sophisticated.
- Busy mid-career professionals (25-44) are prone to BEC and HR scams.
- Overconfident digital natives (18-24) trust pop-up notifications, increasing risk.
- 35% of remote workers clicked on COVID-19-themed phishing emails in 2021.
- In 2021, 50% of cybercrime victims were phishing targets.
- The median number of users compromised per week in 2021 phishing simulations was 15, up from 9 in 2020.
Phishing Statistics by Defense and Mitigation Strategies

Great defenses mix people, process, and tech. Programs that pair phishing-resistant MFA with DMARC enforcement, tuned email/security gateways, role-based training, and one-click reporting consistently see higher report rates, faster time-to-report, lower click-through, and fewer account takeovers.
Here are phishing statistics by defense and mitigation strategies:
- Phishing simulations reduced real phishing email clicks by 76%, per a 2022 Meta study.
- Organizations with regular phishing training see 46 times fewer malware infections.
- DMARC email authentication reduced spoofing by 96% in tested organizations.
- AI and machine learning detect 95% of phishing threats, per Barracuda Networks.
- Multi-factor authentication (MFA) blocks 99% of phishing-related account compromises.
- Companies with monthly phishing training reduced click rates from 34% to 4.6% in 12 months.
- A mid-sized bank reduced phishing click rates from 18% to 4% with gamified simulations.
- The same bank improved phishing reporting dwell time from 3.5 hours to 24 minutes.
- Real phishing threat detection increased by 150% with gamified training.
- Phishing reporting rates should target 55% or higher for effective defense.
- Average reporting dwell time should be under 5 minutes for optimal response.
- Post-training click rates should be driven below 3% for resilience.
- Simulation engagement rates should be maintained at 65% or higher.
- Behavior-based training reduced phishing incidents by 86% in leading organizations.
- Google’s cybersecurity measures block 99.9% of phishing attempts from reaching users.
- Organizations using mobile-first phishing simulations reduced click rates by 38% in 90 days.
- Desktop-only training groups saw only a 17% reduction in click rates.
- AI-powered segmentation in reduces lateral movement in phishing breaches.
- Targeted Human Risk Management strategies reduces new hire phishing risk by up to 30%.
Phishing Statistics by Regional and Global Trends

Threat patterns aren’t uniform worldwide. Regulations, language, dominant apps, and local criminal markets all shape how lures look and when they surge, think tax seasons, elections, and major holidays. Cross-border crews also recycle infrastructure, so outbreaks in one region often ripple across time zones within hours.
Here are phishing statistics by regional and global trends:
- Russia originated 24.77% of spam emails in 2021, a trend continuing into 2025.
- Germany sent 14.12% of spam emails in 2021.
- The USA accounted for 10.46% of spam emails in 2021.
- China originated 8.73% of spam emails in 2021.
- The Netherlands sent 4.75% of spam emails in 2021.
- Phishing in the U.S. dropped 31.8% in 2024 due to stronger email authentication.
- Google’s sender verification blocked 265 billion unauthenticated emails in 2024.
- In the UK, 83% of businesses reporting cyberattacks in 2022 cited phishing.
- UK scammers impersonated Ofgem to harvest financial data in 2022.
- Cryptojacking phishing attacks increased by 409% in India in 2024.
Phishing Stasts by Historical Context and Emerging Patterns

Phishing has evolved from spray-and-pray email scams to multi-channel, low-signal attacks powered by automation and AI. Waves often track big shifts, new collaboration apps, global events, or authentication changes, while playbooks converge as criminals copy what works. Looking across years highlights faster campaign cycles, more impersonation/BEC, and blended tactics (QR, MFA fatigue, voice) that bypass legacy filters.
Here are phishing stasts by historical context and emerging patterns:
- Phishing attacks surged by 667% in Q1 2020 due to COVID-19 themes.
- COVID-19 vaccine phishing attacks increased by 110% from December 2020 to January 2021.
- Over 450 COVID-19 financial assistance scams were reported in 2021.
- 36% of organizations saw increased BEC attacks tied to COVID-19 relief in 2021.
- Phishing kits on the dark web increased by 50% in 2024.
- In 2022, 84% of organizations faced at least one phishing attempt.
- Social engineering was used in 17% of data breaches in 2023.
- Negligence caused 98% of data breaches in 2023, often linked to phishing.
- Stolen credentials were involved in 86% of data breaches in 2023.
- Misdelivery errors contributed to 43% of data breaches in 2023.
- The human element was involved in 68% of breaches in 2024, per Verizon DBIR.
- 80-95% of breaches involve phishing, per Comcast Business Cybersecurity Report.
- Phishing attacks skyrocketed by 4,151% since ChatGPT’s advent in 2022.
- Only 0.7-4.7% of 386,000 analyzed phishing emails in 2024 were AI-crafted.
- Threat reporting rates by trained users increased by 28% in 2022.
- Threat reporting rates grew by 13% in 2023, leveling off at 3% in 2024.
- In 2023, 26% of organizations saw a significant increase in email threats.
- 88% of those organizations were victimized by ransomware via phishing.
- REvil ransomware in 2021 often started with QakBot phishing emails.
- In 2024, 183,000 customers were affected by supply chain phishing attacks, up 33%.
Phishing Statistics by Miscellaneous Categories

Not every useful datapoint fits neatly into a box. This catch-all bucket covers edge cases and practical signals—seasonal spikes, device quirks, third-party app abuse, reporting latency, and other “misc” patterns that still move risk up or down.
Here are phishing statistics by miscellaneous categories:
- The average time to identify and contain a phishing breach is 277 days.
- Breaches involving stolen credentials take 328 days to identify and contain.
- 60% of supply chain organizations use cybersecurity risks as evaluation criteria in 2024.
- Encrypted phishing threats increased by 92% in 2024.
- Malware in phishing emails increased by 30% in the first half of 2024.
- 15% of malware in 2024 used software packing as a primary evasion tactic.
- Globally, cryptojacking phishing attacks decreased by 60% in 2024, except in India.
- The average number of cyberattacks per organization rose from 3 to 4 in 2024.
- 75% of large organizations with revenues over $5.5 billion have cyber insurance.
- Only 25% of organizations with revenues under $250 million have cyber insurance.
- Hoxhunt analyzed 2.5 million user clicks across 50 million phishing simulations in 2024.
- In 2023, only 4% of organizations considered their internet-connected devices secure.
- The FBI shut down 13 DDoS-for-hire marketplaces in 2023, some linked to phishing.
- In 2024, cloud intrusions, often phishing-related, increased by 75%.
- 23% of cloud security incidents in 2023 were due to misconfiguration.
- 27% of businesses encountered cloud security breaches in 2023.
- Over half of cloud credential thefts in 2023 involved phishing.
- 70% of ransomware attacks in 2024 targeted small and medium businesses.
- Ransomware attacks increased by 15% in North America in 2024.
- Ransomware declined by 49% in EMEA in 2024.
- In 2023, 35% of all cyberattacks were ransomware, often delivered via phishing.
- The cybersecurity workforce grew by 12.6% in 2023, yet shortages persist.
- A shortage of 4 million cybersecurity professionals existed in 2024.
- By 2030, the cybersecurity skills gap could reach 85 million.
- 52% of organizations cite lack of resources as a barrier to cyber resilience.
- 50% of executives believe GenAI will advance phishing capabilities by 2028.
- GenAI could reduce employee-driven incidents by 40% by 2026.
- 45% of organizations faced third-party-related disruptions in the last two years.
- Over 2.6 billion personal records were compromised globally between 2021 and 2023.
- A new vulnerability is identified every 17 minutes, fueling phishing exploits.
Phishing Statistics by Keepnet Research

Keepnet’s anonymized telemetry across multi-channel simulations (voice, SMS, QR, MFA) and real-world incident data offers a high-resolution view of what actually lands—who’s targeted, which lures work, and which defenses cut risk. These insights power benchmarks like click-through, report rates, time-to-report, and training effect sizes by industry and region.
Here are phishing statistics from Keepnet research:
- According to Keepnet, new hires are 44% more likely to fall victim to phishing and social engineering attacks during their first 90 days.
- 70% of organizations unknowingly share sensitive information during vishing (voice phishing) simulations, according to Keepnet 2024 Vishing Response Report.
- On average, vishing attacks cost organizations $14 million annually, highlighting the financial toll of phone-based fraud.
- Customer support departments were identified as the most vulnerable to vishing attacks, with their high volume of external communications making them primary targets.
- 6.5% of users were deceived by simulated vishing calls, indicating the need for enhanced security training.
- 40.3% of users did not answer vishing calls, which could either show caution or lead to potential security risks due to missed warnings.
- Companies with the lowest vishing rates typically use advanced vishing simulation software, demonstrating the effectiveness of proactive training.
- Vishing attacks have increased by 30% in the last year, showing the growing use of phone-based social engineering.
- 76% of businesses were hit by smishing (SMS phishing) or scam text messages in the past year, resulting in a 328% increase in incidents and average losses of $800 per incident globally (Keepnet).
- Phone scams caused $39.5 billion in losses last year, with vishing emerging as one of the most damaging forms of fraud.
- Senior citizens were disproportionately targeted by vishing, with a 40% increase in attacks in the last two years, making them a key demographic for scammers.
- 91% of security managers doubt the effectiveness of traditional security training against phishing.
- 89% of malicious emails bypassed email authentication methods like SPF, DKIM, and DMARC.
- 55% of CISOs polled (2024) see deepfakes as a moderate-to-significant threat.
- The dark web trade in deepfake tools rose 223% between Q1 2023 and Q1 2024.
- Cyber scam farms have stolen more in the last 12 months than in any prior year.
- Ransomware was involved in 44% of breaches, with a median payout of $115K and 64% refusing to pay.
- 30% of breaches were caused by third-party compromise.
- 22% of breaches started with stolen credentials, and 20% from exploited vulnerabilities.
- Edge and VPN vulnerabilities grew eightfold, with only 54% patched, and a median fix time of 32 days.
- Human error contributed to 60% of breaches, while user reporting increased 4x post-training.
- Espionage-related breaches rose by 163%, now 17% of all incidents.
- Infostealers hit 30% of corporate and 46% of unmanaged devices storing credentials.
- 15% of staff accessed generative AI tools, 72% through personal email accounts.
- Business Email Compromise (BEC) losses totaled $6.3 billion, with a $50K median loss per incident.
- The use of AI-generated phishing emails has skyrocketed by over 4,000% since 2022, as attackers increasingly deploy large language models to mimic natural communication and evade detection systems.
- As of 2024, Google's AI-driven email security systems block approximately 15 billion unwanted emails daily, effectively preventing over 99.9% of spam, phishing attempts, and malware from reaching users' inboxes, demonstrating the escalating volume of email-based threats and the need for layered security defenses.
- Business Email Compromise (BEC) schemes are responsible for 28% of all phishing-related financial losses, with each successful incident costing organizations an average of $187,000.
- Corporate executives are being specifically targeted by AI-powered phishing campaigns, which now use advanced personalization to create high-trust email messages that bypass traditional filters.
- In 2024 alone, victims reported $16.6 billion in cyber fraud losses, marking a 33% rise from 2023, with phishing continuing to dominate as the most reported scam tactic.
- A global workforce survey in 2024 found that 45% of professionals had fallen victim to a cyberattack or online scam, many of which stemmed from email-based phishing.
- In Q1 2024, the Anti-Phishing Working Group (APWG) recorded 963,994 phishing attacks, marking a significant decrease from the record high of 1,624,144 attacks observed in Q1 2023.
These phishing stats show just how widespread and damaging phishing attacks have become. From email-based phishing to advanced methods like vishing and smishing, or deepfake phishing attacks, organizations must remain vigilant and proactive. Implementing phishing simulations, vishing simulations, and security awareness training can drastically reduce the risks associated with these cyber threats. Keepnet Human Risk Management offers businesses the tools they need to stay protected and avoid costly data breaches and financial losses.
Phishing Attacks Caused Serious Harm in 2026

Here are 6 examples of significant phishing attacks from 2026:
- Twilio Phishing Attack: Twilio’s systems were breached through a sophisticated spear-phishing campaign, compromising sensitive customer data.
- SOVA Android Malware via Phishing: This malware was distributed through phishing emails, leading to ransomware demands and file encryption on victims' devices.
- Petya Ransomware Resurgence: Petya ransomware re-emerged in 2024, targeting businesses via phishing emails and encrypting entire networks.
- AI-Powered Phishing Campaigns Targeting Email Users: In early 2025, phishing scams using AI to generate convincing emails targeted Gmail, Outlook, and Apple Mail users, leading to a spike in identity theft and financial fraud. These AI-crafted messages mimicked legitimate communication, making detection extremely difficult. (Source)
- Blob URI Phishing Technique Bypassing Security: In 2025, researchers discovered phishing attacks using browser-based blob URIs to steal encrypted login credentials. These phishing pages bypass traditional security and AI filters, making them nearly invisible to detection tools. (Source)
- WhatsApp 'Funny Meme' Scam: In 2025, a WhatsApp scam used seemingly harmless memes to spread malware. Once downloaded, these images gave hackers access to victims’ personal data and bank details. (Source)
Further Reading
Phishing continues to be a major cyber security threat in 2026, with the sophistication and frequency of attacks rising. As phishing accounts for a large portion of data breaches, organizations must invest in phishing simulations and awareness training to reduce the risks. The evolution of AI-driven phishing and multi-channel attacks makes it imperative to adopt advanced security measures.
Train your employees and secure your business with Keepnet's phishing simulation software, increasing awareness by up to 90%. Protect your organization with Keepnet's incident response and threat intelligence solutions to stay ahead of the latest phishing threats.
For more resources and insights into phishing and cybersecurity, check out the following blogs:
1. Cybersecurity Awareness Training for Employees
Learn how to equip your team with the knowledge and skills to identify and avoid phishing attacks, improving your overall security posture and get free cybersecurity awareness training contents.
2. What Are Vishing Statistics in 2026?
Examine the growing threat of voice phishing (vishing) and how it is impacting businesses today.
3. 2026 QR Code Phishing Trends: In-Depth Analysis of Rising Quishing Statistics
Learn how quishing—phishing via QR codes—is becoming a more prevalent attack method in today’s digital world.
4. 2026 Security Awareness Training Statistics
Understand the latest trends and statistics around security awareness training and its effectiveness in preventing cyber incidents.
5. Smishing Statistics: The Growing Threat of SMS Phishing
Dive into the alarming rise of smishing (SMS phishing) and what businesses need to do to protect their employees from this attack vector.
6. Understanding MFA Phishing: Protection Measures and Key Statistics
Explore how multi-factor authentication is being targeted by threat actors and what steps you can take to bolster your defenses.
7. Understanding MFA Phishing: Protection Measures and Key Statistics
Explore how attackers exploit multi-factor authentication and what can be done to enhance your defenses.
8. Top 10 Effective Vishing Awareness Training Strategies for Your Team
Learn practical strategies for training your team to recognize and prevent vishing attacks.
9. Email Security: The 7 Biggest Threats
Discover the most common email security threats and how to strengthen your organization’s email defenses.
10. How to Protect Your Business Against Ransomware
Explore key steps for safeguarding your company from ransomware, a threat often initiated by phishing emails.
By staying proactive and informed, your organization can significantly reduce its exposure to phishing scams and build a robust cybersecurity strategy.
Editor's Note: This article was updated on January 12, 2026.