What is Phishing? How to Protect Yourself from It?
Phishing is a deceptive practice that cybercriminals use to steal sensitive information. This guide provides important tips on recognizing phishing attempts and outlines robust strategies to shield yourself and your organization from these malicious attacks.
In 2025, phishing attacks accounted for over 36% of all cyberattacks, according to the Verizon Data Breach Investigations Report. With losses exceeding $17 billion globally, phishing remains one of the most common and effective cyberattack methods. It’s not just about tricking individuals into clicking links—it’s about exploiting human trust. One notable case involved a UK energy company in 2023, where a phishing attack led to $250,000 being stolen within minutes, severely damaging their reputation.
So, what exactly is phishing? Phishing is a cybercrime tactic where attackers impersonate trusted entities—such as banks, colleagues, or government agencies—to steal sensitive information like login credentials, credit card numbers, or personal identification details. These attacks typically occur via email, but they’ve expanded to include phone calls (vishing), text messages (smishing), and even QR codes (quishing).
In this blog, we’ll explore:
- The definition of phishing.
- The different types of phishing attacks.
- Real-world examples of phishing incidents.
- Steps to protect yourself and your organization.
Definition of Phishing
Phishing is a cyberattack where scammers impersonate trusted entities—like banks, colleagues, or popular brands—to trick you into revealing sensitive data such as passwords, credit-card numbers, or personal information. By sending realistic-looking emails, text messages, or links, phishers exploit human trust and urgency, often prompting victims to click before they think. Understanding “what is phishing” and learning to spot misspellings, strange URLs, and unsolicited requests is your first line of defense against data breaches and identity theft.
Phishing attacks exploit human trust and urgency, making them one of the most common and effective methods used by cybercriminals to compromise systems, steal data, or execute financial fraud.
The Evolution and Impact of Phishing Attacks
The history of phishing traces back to the 1990s, when internet usage began to skyrocket. The term 'phishing' was coined around 1996 by hackers stealing AOL accounts and passwords. The early phishing attacks were relatively simple, often leveraging fear and curiosity to deceive victims into giving up their details.
With the evolution of technology and increased online activity, phishing scams have evolved significantly. Phishers have become more sophisticated in their approach, crafting believable scams that often mirror the communications of trusted entities such as banks, service providers, and even coworkers. It is this constant evolution that makes phishing an ever-present and growing threat.
Learn what is phishing and how phishing attacks works from the below YouTube video.
The Anatomy of a Typical Phishing Email
To understand how to combat phishing, it's significant to recognize the anatomy of a typical phishing email. These elements often include:
Sender Information
Phishing emails often appear to come from a legitimate source. The 'From' line may display a name you recognize, such as a financial institution, service provider, or even a person you know. However, a closer look might reveal discrepancies, such as a misspelled domain name or a foreign email extension.
Message Content
The body of a phishing email often instills a sense of urgency, fear, or curiosity in the recipient. The message might claim that your account has been compromised, you've won a prize, or an invoice is due. Grammar and spelling errors can also be a sign of a phishing email, as these messages often originate from non-native English speakers.
Links and Attachments
Phishing emails frequently contain malicious links or attachments that lead to fake websites or download malware. These links often appear legitimate but may contain subtle misspellings or a different domain when hovered over with the cursor.
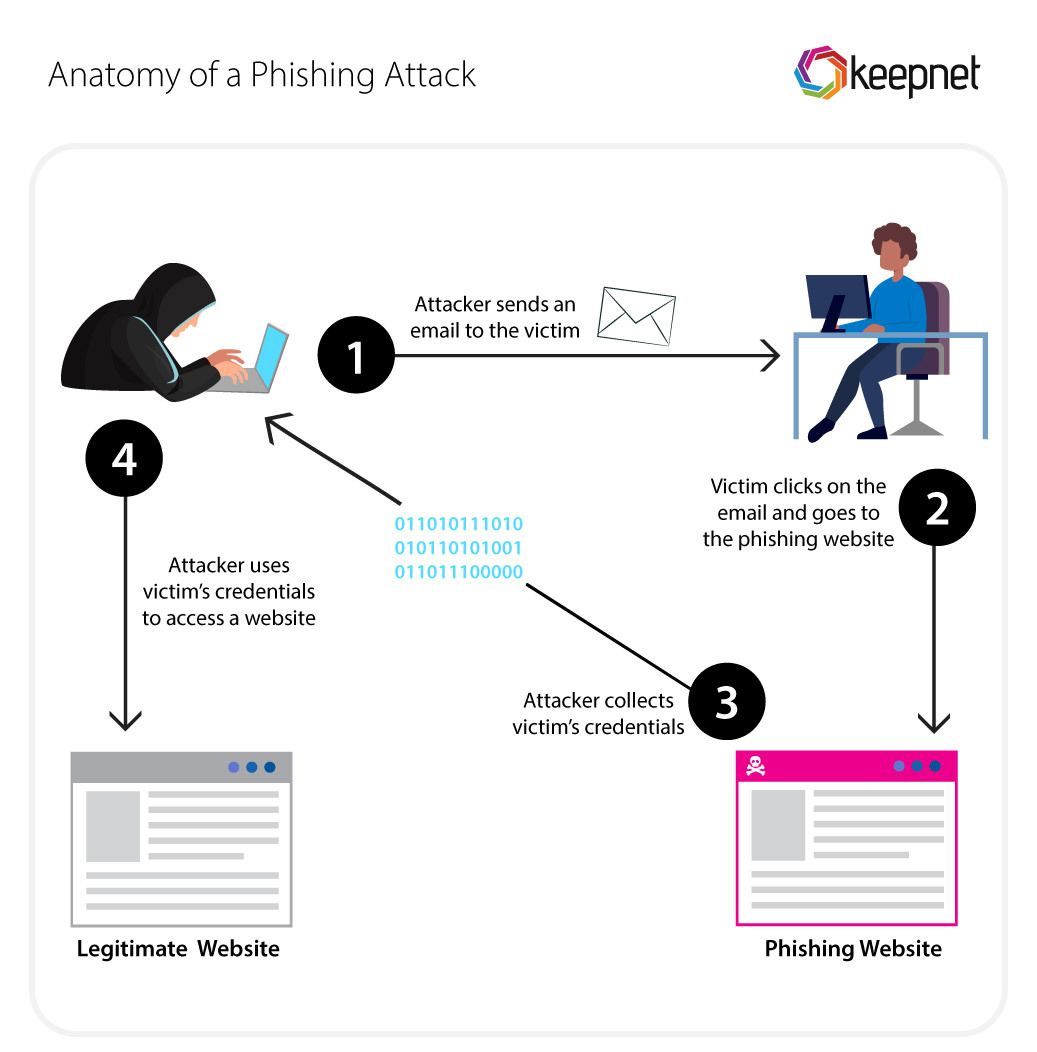
Types of Phishing Scams
Phishing forms are in various, each with its unique approach:
Email Phishing
The most common type, deceptive phishing, involves emails impersonating legitimate companies to steal user data. The emails trick recipients into entering their credentials on a counterfeit website.
Spear Phishing
Spear phishing is a targeted form of phishing where the attackers customize their approach for each victim, using personal information to make the email seem more authentic.
Whaling
Whaling attacks target high-profile individuals like CEOs or CFOs. Attackers usually do thorough research and impersonate senior management to trick the recipient into revealing sensitive information or transferring funds.
MFA Phishing
Multi-Factor Authentication (MFA) phishing attacks deceive users into revealing their MFA credentials on a fake site, which attackers promptly use on the real site to gain unauthorized access. This real time, time-sensitive attack mimics the MFA process to trick the user, despite MFA being a well-regarded security measure. The FBI has issued warnings about the increase in such scams, emphasizing the importance of user education, hardware-based authentication devices, and more sophisticated security measures like biometric authentication or behavioral pattern recognition.
Clone Phishing
In clone phishing, a legitimate email with an attachment or link is replicated with changed content or replaced link, making it appear it came from the original sender.
CEO Fraud
CEO fraud is a form of spear phishing where attackers pose as the CEO or another high-level executive and send an email to an employee with the authority to transfer money or send sensitive information.
Vishing
Vishing (voice phishing) involves attackers impersonating trusted entities over phone calls to trick victims into revealing sensitive information, such as passwords or financial details.
Quishing
Quishing uses malicious QR codes to redirect victims to phishing websites or initiate malware downloads, exploiting the growing reliance on QR code technology.
Smishing
Smishing (SMS phishing) involves sending fraudulent text messages to victims, often containing malicious links or requests for sensitive information under false pretenses.
Callback Phishing
Callback Phishing is a sophisticated phishing technique where attackers lure victims into calling a fake customer service number. Once the victim makes the call, the attacker impersonates a legitimate organization to extract sensitive information or install malware.
Check our guide to learn more on phishing types.
Impact and Risks Associated with Phishing
The impacts of phishing are far-reaching, affecting individuals, businesses, and even governments. Phishing attacks can lead to devastating consequences, from financial losses to reputational harm. Let’s examine the real-world impacts of phishing through actual cases:
For Individuals: Identity Theft and Financial Loss
Phishing attacks on individuals often result in stolen credentials, financial losses, or identity theft. In 2023, a widespread smishing campaign targeted consumers by impersonating major banks, tricking them into sharing their online banking credentials. According to the FBI, one victim lost over $80,000 in a single attack after transferring money to a "secure account" that belonged to the attackers.
For Businesses: Data Breaches and Reputational Damage
Businesses face even greater risks. A 2022 phishing attack on Australian telecom company Optus exposed sensitive data of nearly 10 million customers, including passport and driver’s license details. The breach not only resulted in legal penalties but also severely damaged customer trust, costing the company millions in recovery and compensation efforts.
Similarly, Twitter faced a massive phishing attack in 2020 when employees were targeted with a spear phishing email. Hackers gained access to internal systems and took over high-profile accounts, including those of Barack Obama and Elon Musk, to promote a cryptocurrency scam. The attack exposed the platform’s vulnerabilities, resulting in global criticism and regulatory scrutiny.
For Governments: National Security Risks
Phishing has even targeted governments, threatening national security. In 2021, a phishing attack targeted employees of the US Department of Defense, leading to a breach that exposed sensitive data and disrupted critical operations. Such incidents highlight how phishing can have far-reaching consequences beyond financial loss, impacting public safety and security.
Detecting Phishing Attempts
Navigating the cyber world requires a careful and discerning eye, especially when it comes to the threats posed by phishing attacks. The key to staying safe online is the ability to recognize phishing attempts when they occur.
Common Signs of Phishing Emails
Knowing the common signs of phishing emails can significantly improve your defense against cyber threats.
Here are some red flags to look out for:
- Urgency: Phishing emails often use scare tactics and create a sense of urgency to prompt immediate action. Phrases like "your account will be closed," or "your payment is overdue" are common.
- Generic greetings: Phishing emails often use generic greetings such as "Dear Customer" instead of personalized greetings.
- Suspicious email addresses: Even if the name appears familiar, check the email address. Look out for random strings of characters or slight misspellings in the domain name.
- Poor grammar and spelling: While not always the case, many phishing emails contain grammatical errors and spelling mistakes.
- Request for personal information: Legitimate companies typically don't ask for sensitive information over email.
- Mismatched URLs: Hover over any links without clicking to see if the actual URL matches the one in the email.
Add to what you're learning here by watching our video. Watch our YouTube video below and learn how to analyze Discord phishing emails in real life.
Real-Life Phishing Incidents
To better understand the dynamics of a phishing scam, let's dissect some real-life phishing examples that occurred:
SRP Federal Credit Union Data Breach (December 2024):
SRP Federal Credit Union, based in South Carolina, experienced a substantial data breach affecting over 240,000 individuals. The breach, occurring between September 5 and November 4, was part of a two-month cyberattack during which hackers accessed sensitive personal data, including Social Security numbers, driver's license numbers, dates of birth, and financial information.
The ransomware group Nitrogen has claimed responsibility, allegedly stealing 650 GB of customer data. Following the breach, SRP informed law enforcement and is now being investigated for potential legal challenges. The credit union is offering identity theft protection services to those impacted.
GCash Unauthorized Transactions (2023)
In May 2023, GCash, a widely used mobile wallet in the Philippines, suffered a major phishing attack. Hackers exploited users by luring them through fake online gambling websites. This led to unauthorized fund transfers affecting a large number of users and dented customer trust in the company. The incident showcased how phishing could exploit digital payment platforms.
Twilio and Cloudflare Breach (2022)
In August 2022, phishing attacks targeted employees at Twilio and Cloudflare by sending fake text messages claiming to come from their IT teams. Twilio confirmed that the breach exposed customer data, while Cloudflare managed to fend off the attack due to their use of hardware-based MFA keys. This attack highlighted how even large tech companies are vulnerable to well-crafted phishing campaigns.
SolarWinds-Related Phishing Attacks (2022)
Following the infamous SolarWinds supply chain attack, phishing campaigns in 2022 targeted government agencies and private companies using similar tactics. Hackers impersonated trusted vendors to compromise employee credentials and gain access to sensitive systems. This led to data breaches for several high-profile businesses.
Uber Data Breach (2022)
In September 2022, a hacker breached Uber’s internal systems using a phishing attack. By posing as an IT administrator, the attacker tricked an employee into granting access to Uber’s internal systems. This breach compromised sensitive employee and customer data, damaging the company’s reputation significantly.
Revolut Phishing Attack (2022)
In 2022, Revolut, a digital banking platform, confirmed a phishing attack that affected a small percentage of customers. The breach exposed personal data, including partial payment card details, email addresses, and phone numbers. The attack served as a reminder of the vulnerabilities digital banking platforms face against phishing campaigns.
Norwegian Parliament (Stortinget) Email Breach (2021)
In March 2021, Norway’s national assembly was hit by a phishing email campaign that allowed attackers to access email accounts of elected officials and employees. While the exact financial losses remain unclear, the geopolitical implications and reputational harm were significant.
Facebook Scam Targeting Palestinian Users (2021)
In 2021, a phishing campaign targeted Facebook users in Palestine. Attackers distributed malicious Android apps through phishing messages, leading to substantial data theft. Though not quantified in financial terms, this incident had severe implications for personal privacy and data security.
Australian Securities and Investments Commission (ASIC) Email Breach (2021)
The Australian corporate regulator faced a data breach in January 2021 when attackers compromised a file transfer application through phishing. Sensitive information, including credit license applications, was exposed. The breach highlighted the vulnerability of even government institutions to phishing schemes.
Hafnium’s Microsoft Exchange Server Attacks (2021)
State-sponsored attackers from Hafnium exploited vulnerabilities in Microsoft Exchange Servers in early 2021. They used phishing to gain admin credentials and deployed malware, compromising over 30,000 organizations in the United States. Businesses lost millions due to data theft and operational disruptions.
Watch a real-life phishing incident unfold: A victim received a call from someone pretending to be from Amazon customer service, claiming there were suspicious purchases on their account. The scam escalated when the victim was transferred to an individual posing as an FTC official, who manipulated them into withdrawing a large sum of money and handing it over to a stranger. Learn from this story and discover essential precautions to safeguard yourself from similar scams.
Check our guide to learn current phishing trends and statistics.
Understanding the Technology/Methodology Behind Phishing
As we delve deeper into the world of phishing, it's important to understand the technology and techniques that enable these deceptive practices. This knowledge will help empower you to better defend against phishing attempts and minimize their potential impact.
Creating Phishing Emails
Phishers use various techniques to forge emails and make them appear as though they're from legitimate sources. The two primary methods are email spoofing and website cloning.
- Email spoofing: This involves altering the email header so the message appears to come from somewhere other than the actual source. While email systems typically verify if a message is from the server it claims to be, phishers can get around these checks through a technique called SMTP (Simple Mail Transfer Protocol) relay, tricking the system into delivering the email.
- Website cloning: Phishers often clone legitimate websites to fool victims into entering their credentials. The cloned sites look virtually identical to the real ones but are hosted on different servers. Any information entered on these clone sites is directly captured by the phishers.
Using Malware in Phishing Attacks
Phishing isn't just about deceptive emails; it often involves malicious software, or malware, designed to infiltrate and damage computers without the user's consent. There are various types of malware used in phishing attacks:
- Keyloggers: These record every keystroke you make on your keyboard, including usernames, passwords, and credit card numbers, which are then sent back to the phisher.
- Trojans: These appear as legitimate software but perform hidden functions, such as compromising your system's security or transmitting your data to the phisher.
- Ransomware: This malware encrypts the victim's files and demands a ransom to decrypt them. The initial infection often occurs via a phishing email.
Tracking and Capturing Data During Phishing Attacks
The principal aim of phishing scams is to illicitly procure sensitive data to derive profits. To this end, phishers adopt numerous data tracking and capturing methodologies:
- Cloned Site Data Capturing: As previously delineated, phishers mirror authentic websites to hoodwink victims into revealing their login details. Once these credentials are keyed in, the scammers capture this data and redirect it to themselves.
- Deployment of Spyware: This category of malware camouflages itself on a user's computer, monitoring their activity and capturing data such as browsing patterns, keystrokes, and private information. This gathered data is then transmitted back to the phisher.
- Data Trafficking: Frequently, the filched data, especially personal information, is sold in the dark web's underground markets, rendering the venture lucrative for phishers.
- Financial Fraud: Often, phishers' ultimate objective is monetary gain. This is achieved through fraudulent transactions leveraging purloined credit card data or manipulating victims into effecting direct payments, as evidenced by CEO fraud and ransomware attacks.
- Ransomware Attacks: In this sinister scheme, malware is used to encrypt a victim's data or block access to their system. The attackers then demand a ransom, typically in cryptocurrency, to restore access. The encryption is typically robust, leaving victims with few options but to pay, often resulting in significant financial losses. It's worth noting that even after payment, there's no guarantee that the attackers will honor their word and decrypt the data. Ransomware has been particularly prevalent in attacks against businesses and public institutions, causing not just financial losses, but significant disruption to operations and services.
Protecting Yourself and Your Organization from Phishing
Information alone isn't enough to shield us from the insidious threat of phishing. We must encourage active participation and instill strong security behavior. So, what do we recommend for fortifying your defenses against these cyber attacks? Let's explore the proactive measures you can take to substantially diminish the odds of becoming a victim.
Build a Security Culture
Building a strong security culture is important in defending against phishing attacks and other cyber threats. A security culture goes beyond implementing tools and policies—it’s about embedding cybersecurity awareness into every employee's behavior and decision-making processes.
Key elements of a robust security culture include:
- Leadership Commitment: Leaders must champion cybersecurity initiatives, setting an example for employees and emphasizing its importance.
- Comprehensive Training Programs: Regular, engaging, and targeted training helps employees stay updated on the latest phishing tactics and best practices for prevention.
- Engaging Awareness Campaigns: Interactive and creative campaigns make cybersecurity awareness an ongoing and memorable experience for employees.
- Encouraging a Reporting Culture: Employees should feel empowered and confident to report suspicious activities without fear of repercussions.
- Simulated Phishing Exercises: Testing employees with realistic phishing scenarios allows organizations to assess vulnerabilities and strengthen defenses.
- Continuous Evaluation and Improvement: Regular assessments of cybersecurity practices ensure the organization is ready to handle emerging threats effectively.
Create Security Behavior and Culture Programs
A well-designed Security Behavior and Culture Program (SBCP) is critical for addressing the human element of cybersecurity risks. Many phishing attacks succeed because of human error rather than technical weaknesses, making behavioral transformation a cornerstone of modern security strategies.
By implementing an SBCP, organizations can:
- Reduce Human Risk: These programs educate employees on recognizing and avoiding phishing threats, significantly reducing the likelihood of human error.
- Foster Proactive Responses: Employees are empowered to take ownership of their role in cybersecurity, actively identifying and mitigating potential threats.
- Integrate Security into Daily Operations: SBCPs align cybersecurity with organizational goals, embedding a culture of vigilance across teams and departments.
To explore more, read our blog on a Security Behavior and Culture Program.
Set Protection Level Agreements (PLAs) in Building Security Culture
Another key component of fostering a security culture is implementing Protection Level Agreements (PLAs) in your Security Awareness Training programs. A PLA is a measurable framework that defines the desired outcomes and expectations from security awareness initiatives. It ensures accountability and effectiveness by linking security goals to outcome driven metrics.
Why PLAs Are Crucial:
- Clear Objectives: PLAs set clear benchmarks for what security awareness training should achieve, such as reduced phishing susceptibility rates or faster reporting of suspicious activity.
- Measurable Outcomes: By quantifying performance, PLAs allow organizations to track progress and make data-driven improvements.
- Alignment with Business Goals: PLAs ensure that security awareness efforts are not just educational but also contribute directly to the organization’s overall risk management strategy.
For a deeper dive into how PLAs can enhance your security awareness training, read our blog on PLA guide.
Steps to Take When You Receive a Potential Phishing Email
If you suspect an email might be a phishing attempt, follow these steps:
- Don't panic: Phishers often rely on inducing fear or a sense of urgency. Stay calm and think clearly.
- Don't click on links or download attachments: They could lead to harmful sites or contain malware.
- Check the sender's details: Look for inconsistencies in the email address.
- Report the email: Notify your IT department if you're at work, or report it to your email provider if you're at home.
Steps to Take if You've Fallen for a Phishing Scam
If you've fallen for a phishing scam:
- Change your passwords: Do this immediately, starting with your email and any accounts that share the same password.
- Monitor your accounts: Keep an eye on your financial accounts for unusual activity.
- Contact the right people: Report the incident to your IT department if at work, or to your bank and credit card companies if personal information was involved.
Reporting Phishing Attempts
If you've identified a phishing attempt, it's important to report it. Here are some ways to do so:
- Your workplace: If you're part of an organization and you received the phishing email at work, report it to your IT department.
- Email provider:Most email providers have a 'report phishing' option.
- Anti-Phishing Working Group (APWG): You can report phishing to the APWG by emailing reportphishing@apwg.org.
- Federal Trade Commission (FTC): In the U.S., you can report phishing to the FTC at ftc.gov/complaint.
- Phishing Reporter Add-in: Keepnet offers organizations Phishing Reporter add-in to report suspicious emails to your IT team or Incident Responder product to analyze the Sender IP, Links, Attachments in the email within a minute with integrated security solutions.
- Mobile Reporting Apps: Some cybersecurity platforms offer mobile apps for employees to report phishing attacks on the go. These apps streamline the reporting process by allowing users to submit screenshots, suspicious URLs, or email headers.
- QR Code for Reporting: Organizations can provide a dedicated QR code that employees can scan to report phishing attacks. This QR code could direct them to a secure webpage or form where they can submit the details of the suspected attack.
- Phishing Incident Reporting Portal: A centralized, web-based portal allows employees to report phishing attempts by uploading suspicious emails, links, or text messages for evaluation. These systems provide immediate feedback on whether the reported message is legitimate or malicious, helping organizations respond quickly. With tools like Keepnet's Free Phishing Email Analysis Service, employees can easily analyze suspected phishing emails, identify threats, and enhance overall cybersecurity awareness.
- SMS Reporting for Smishing Attacks: For text message phishing (smishing), organizations or telecom providers can offer an SMS number where users can forward suspicious messages. For example, many telecom providers use "7726" (SPAM) to report such messages. To learn further, read our blog on how to report SMS phishing attacks.
- Voice Hotline for Vishing Incidents: Organizations can set up a dedicated vishing reporting hotline, allowing employees to report suspicious calls where attackers pose as trusted entities to extract sensitive information.
- Chatbot Integration for Real-Time Reporting: Using chatbots integrated into workplace communication tools like Microsoft Teams or Slack can allow employees to quickly report phishing attempts. Employees can drop suspicious messages or URLs into the chatbot for immediate analysis and feedback.
- API-Based Reporting: Organizations can integrate APIs into their IT systems to automatically flag and forward suspicious emails to cybersecurity teams or external reporting platforms for real-time analysis.
Popular Phishing Scams in 2025
Here are a few emerging phishing in the world of phishing:
- AI-powered phishing: Cybercriminals are starting to use artificial intelligence to create more convincing phishing attempts. For example, machine learning can be used to study the patterns in a person's writing style and mimic it convincingly.
- Deepfake phishing: Deepfake phishing is an advanced cyberattack that uses deepfake technology—AI-generated audio, video, or images—to impersonate trusted individuals or organizations. Attackers use convincing fake content, such as a CEO’s voice or a video message, to manipulate victims into sharing sensitive information or transferring funds.
- Social media phishing: Phishing isn't limited to emails anymore. Cybercriminals are using social media platforms to launch phishing attacks, often disguised as messages from friends or familiar brands.
- Smishing (SMS Phishing): This is another form of phishing where cybercriminals send deceptive text messages. The message often appears to come from a reputable source and encourages the recipient to share sensitive information or click on a link that leads to a malicious website. As the usage of smartphones continues to grow, the prevalence of smishing is expected to increase.
- Voice Phishing: Voice phishing, also known as vishing, is a deceptive technique where cybercriminals make phone calls to extract sensitive information. Impersonating trusted entities, such as financial institutions or government agencies, attackers manipulate victims into revealing confidential data. These calls exploit social engineering tactics, leveraging voice manipulation techniques and playing on the victim's trust and compliance with perceived authority figures. To protect against voice phishing, individuals and organizations must educate themselves about warning signs during phone conversations. They should be cautious about unsolicited calls, verify caller identities independently, and refrain from sharing sensitive information unless absolutely necessary.
- Toad (Telephone-Oriented Attack Delivery): Toad, or Telephone-Oriented Attack Delivery, or some times called callback phishing refers to a social engineering attack that specifically targets individuals or organizations over the phone. In a Toad attack, the perpetrator poses as a legitimate representative, exploiting vulnerabilities and employing persuasive tactics to deceive victims. By impersonating trusted sources like banks or service providers, they manipulate victims into revealing sensitive information or performing actions that serve the attacker's interests. To protect against Toad attacks, individuals and organizations should adopt a skeptical mindset during phone conversations. They should question the caller's authenticity, avoid sharing sensitive information without verifying the purpose of the call, and educate themselves regularly to recognize and thwart these manipulative tactics.
- Quishing: Quishing combines the tactics of voice communication with phishing, targeting individuals and organizations through deceptive phone calls. Attackers impersonate trusted sources, exploiting trust to manipulate victims into divulging sensitive information. Being cautious is important when sharing information over the phone, verifying the caller's identity independently, and recognizing that reputable organizations seldom request sensitive details via unsolicited calls. By staying cautious and informed, the risk of falling victim to quishing attacks can be significantly reduced.
How Keepnet Human Risk Management Can Help You Prevent Phishing Attacks
Phishing attacks are one of the most persistent threats organizations face today. Keepnet offers a comprehensive suite of tools designed to help you take a proactive approach to these evolving challenges. Keepnet Phishing, Smishing, and Vishing Simulators provide a practical, controlled environment to test your organization's resilience against email, SMS, and voice-based phishing attacks, helping you identify vulnerabilities before they become costly issues.
Alongside phishing simulators, Keepnet Security Awareness Training delivers ongoing, interactive training to ensure your employees are equipped to recognize and respond to these threats. By integrating simulations with consistent training, you foster a security-conscious culture that actively safeguards your organization.
To enhance your incident response capabilities, Keepnet's Incident Responder streamlines the process of reporting, analyzing, and containing phishing threats. With real-time alerts and in-depth analytics, your team can track incidents, detect patterns, and take preventive measures to minimize risks.
| Feature | Description | Benefit |
|---|---|---|
| Cybersecurity Awareness Training | Offers 500+ courses in 30+ languages with diverse content styles, including micro-videos, game-based learning, and regulatory training. | Builds a security-oriented culture and equips employees with knowledge to defend against phishing and other threats. |
| Behavior-Based Security Training | Delivers targeted training automatically in response to employees' incorrect actions during simulations. | Helps reinforce correct behaviors and improve overall employee security performance. |
| Gamification and Leaderboards | Encourages participation in training programs by using leaderboards and rewarding employees for engagement. | Makes security training more engaging, increasing employee participation and retention. |
| Security Behavior and Culture Program (SBCP) | A program designed to influence and improve employee behavior towards cybersecurity through targeted training and cultural shifts. | Reduces human error by fostering a security-conscious work culture and aligning cybersecurity with organizational goals. |
| Protection Level Agreement (PLA) | Sets measurable benchmarks and outcomes for security awareness training initiatives to track their effectiveness. | Ensures training programs are aligned with organizational goals and deliver measurable results, improving accountability. |
| Phishing Simulation | Simulate realistic email-based phishing attacks to train employees in identifying and responding to deceptive emails. | Enhances employee readiness and significantly reduces the risk of falling victim to phishing. |
| Voice Phishing Simulation | Simulates phone-based phishing (vishing) attacks to train employees in identifying and handling malicious calls. | Builds employee confidence in recognizing and avoiding voice-based phishing scams. |
| SMS Phishing Simulation | Mimics SMS-based phishing (smishing) to teach employees how to identify and respond to malicious text messages. | Helps employees become vigilant against smishing threats, especially in mobile-dependent environments. |
| QR Code Phishing Simulation | Simulates phishing attacks using malicious QR codes to test employee awareness of QR-based risks. | Raises awareness about QR phishing (quishing) and promotes safe practices when scanning codes. |
| MFA Phishing Simulation | Tests employee responses to simulated attempts to bypass multi-factor authentication (MFA). | Reinforces the importance of secure MFA practices and reduces vulnerabilities in authentication systems. |
| Phishing Forensic Analysis | Automatically analyzes reported phishing emails based on headers, links, attachments, and sender IP. | Quickly identifies malicious emails and provides detailed threat insights for faster responses. |
| Phishing Incident Response | Find and quarantine malicious emails in Google Workspace, Microsoft Office 365, or Exchange EWS via native integration. | Prevents further spread of phishing emails within the organization by quickly isolating threats. |
| AI Threat Analysis Services | Built-in analysis using tools like VirusTotal, IBM X-Force, Forti Sandbox, and more for comprehensive email threat detection. | Provides advanced threat detection, ensuring accurate identification of phishing attempts. |
| SOAR Integration | Integrates with top SOAR solutions to automate email incident response processes. | Streamlines threat response and improves the efficiency of incident management. |
| Automated Email Response Rules | Create custom playbook rules to automate the analysis and response to suspicious emails. | Speeds up email threat management and reduces manual intervention. |
| Threat Intelligence Sharing | Join sector-based ISACs or verified communities for sector-specific threat intelligence and collaboration. | Enables proactive defense with access to over 1 million global threat hunters and shared intelligence. |
| Outlook Phishing Reporter Add-In | Allows employees to report suspicious emails directly from their Outlook Desktop App. | Improves reporting efficiency and enables faster threat detection and mitigation. |
| Archive Scanning | Scans archived emails in services like Enterprise Vault to detect and mitigate phishing risks. | Ensures complete email protection, even for archived messages, minimizing long-term risks. |
Table 1: How Keepnet Human Risk Management Can Help You Prevent Phishing Attacks
Keepnet Human Risk Management Solution is designed to help you build a resilient defense against phishing attacks—without disrupting your workflow. If you're looking to strengthen your organization’s cybersecurity posture, we’re here to support you with tools and insights you can trust.
Watch the video below to learn more about Keepnet Human Risk Management Platform.
Editor's Note: This article was updated on June 25, 2025.